Your computer is a very sensitive place for your privacy. It's where many of us keep vital information like payment details, phone numbers, sensitive files, email addresses, and so much more. For this reason, a compromised Mac is a considerable digital and physical security risk.
There are various ways hackers or malicious people can steal information from your Mac. But few are as effective as spyware and keyloggers. Here, we will show you what to do if you suspect you are a target of such nefarious practices. But before that, let's look at some signs you should look out for.
What Are the Signs Someone Is Spying on Your Mac?
Just like with diseases or infections in the human body, you can diagnose your Mac with spyware through certain signs.
Your Mac Is Using More Bandwidth
Spyware getting on your computer is just the first half of its journey. The second half is sending real-time data to whoever is trying to steal your information. Most times, your computer needs to use the internet to do this.
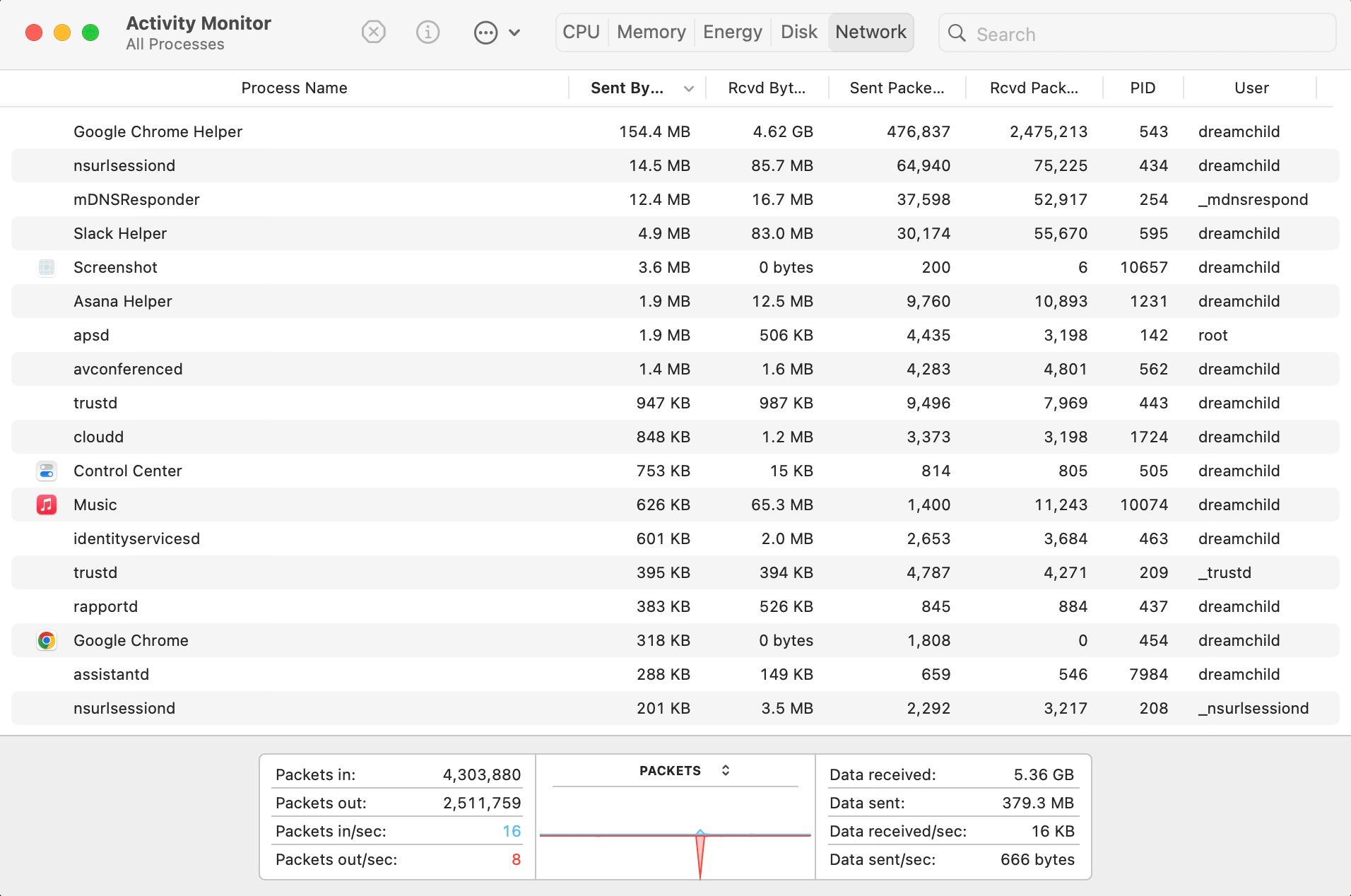
Luckily, you can detect when this is happening if your computer uses more internet than usual, and there's no apparent justification for this abnormal upload.
You can catch software using your internet by opening Activity Monitor with a Spotlight search. From there, click Network and toggle sorting by Sent Bytes. Here, you should see if any unsolicited apps are using your network.
Your Mac Becomes Slower, Apps Crash More, and Exhibits Odd GUI Behavior
Kind of like a parasite, spyware needs your computer's resources to be effective. If someone is watching you, they'll need demanding software. Because of this, other bonafide apps are more likely to crash since your computer is straining under the load.
Consequently, you may also experience perpetual lag. Since your CPU, memory, and GPU could be overworked, your processors could overheat and cause lag. If you just booted up your computer and you're experiencing lag too soon, there is most likely a resource-heavy program running in the background. And this program can be malicious.
Like checking the network, you can open the Activity Monitor to see what is draining your Mac's other resources.
Also, some malicious software can control your Mac and cause it to act strange. So, if you notice erratic GUI movements like your cursor shifting without input, it might be time to raise the alarm.
Your Webcam Light Is On
While some spyware might be watching your screen or tracking your keyboard buttons, others could watch you through your camera. Yes, we know it sounds scary, but a webcam is an important part of most modern computers.
Unfortunately, it can also be a tool for hackers to spy on you. On a Mac, if your camera light is on, then your camera is also on because they've been engineered that way, according to Apple.
As tempting as it sounds, don't cover your camera because this can possibly damage your screen. Instead, you should check your privacy settings and ensure that no suspicious software has been granted access.
Follow these steps to check which applications have access to your camera:
- Launch System Settings from the Apple logo on the menu bar.
- Mouse over to the left pane and select Privacy & Security.
- Click Camera to see what has access to your camera.
Check for Privacy Icons in Your Menu Bar
Apart from your camera, other ways a person can monitor you include screen-recording applications, remote access software (like Apple Remote Desktop), and your microphone.
You can check what has access to screen recording and your microphone permissions from Privacy & Security in System Settings, just like with the camera permissions.
What's more, these permissions also have signs for when something is actively using them. Screen recording pops up in the menu bar as a rectangle in a rectangle, while the microphone shows as an orange or yellow dot at the corner of your screen.
That said, if you open Control Center in the menu bar, you can easily see exactly what app is using your microphone.
There Might Be a New User on Your Mac
User accounts are how Apple manages permissions in macOS. A user with all the applicable permissions has an admin tag, and they can make key changes to the computer.
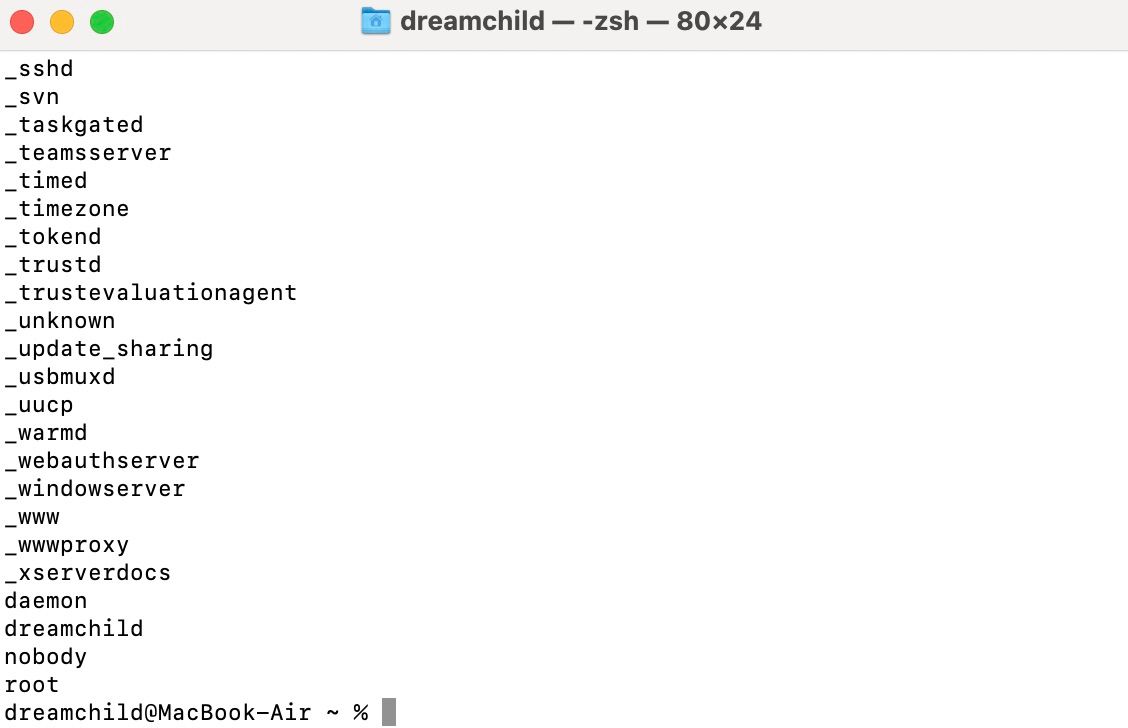
While you can see users in System Settings > Users & Groups, a foolproof way of seeing everyone on your computer is to use the Terminal app.
Follow these steps to check for users with Terminal:
- Open Spotlight with Command + Space.
- Type in Terminal and hit Return.
-
Copy and paste the following command line into Terminal.
dscl . list /Users - Press Return.
Don't be worried if you see a long list of users. The ones with underscores or named "daemon," "root," and "nobody" are important for your computer to function. However, anything else that isn't authorized is a cause for alarm.
How to Stop Spyware on Your Mac
The best way to stop spyware is to prevent it. Avoid taking steps that will get your computer infected in the first place. But should some slip through the cracks, here are some things we suggest you do.
Download and Install Security Software
Everyone should have an antivirus installed. And you don't need to be rich to have one; we have a list of free but effective antiviruses.
Antivirus software can protect your Mac in real-time and scan your entire system for malware. When it finds something suspicious, it quarantines the process or the app and prompts you to delete it.
Inspect Your Mac Yourself and Delete Odd Apps
As stated earlier, you can use the Activity Monitor to find anything draining your Mac's resources. If you find apps you don't remember installing or odd new apps, you should delete them.
You can also check to see if any suspicious apps boot on startup. Launch System Settings and go to General. Click Login Items and look through to see if there's anything you don't want there.
There are various ways to delete apps, some more effective than others. For more details, we've listed the multiple ways to delete apps on a Mac.
Check Your Hardware
Hackers with physical access to your Mac can attach keylogging hardware that can record what you type. If you aren't confident in your ability to find them, you should take your Mac to an expert to have it looked at.
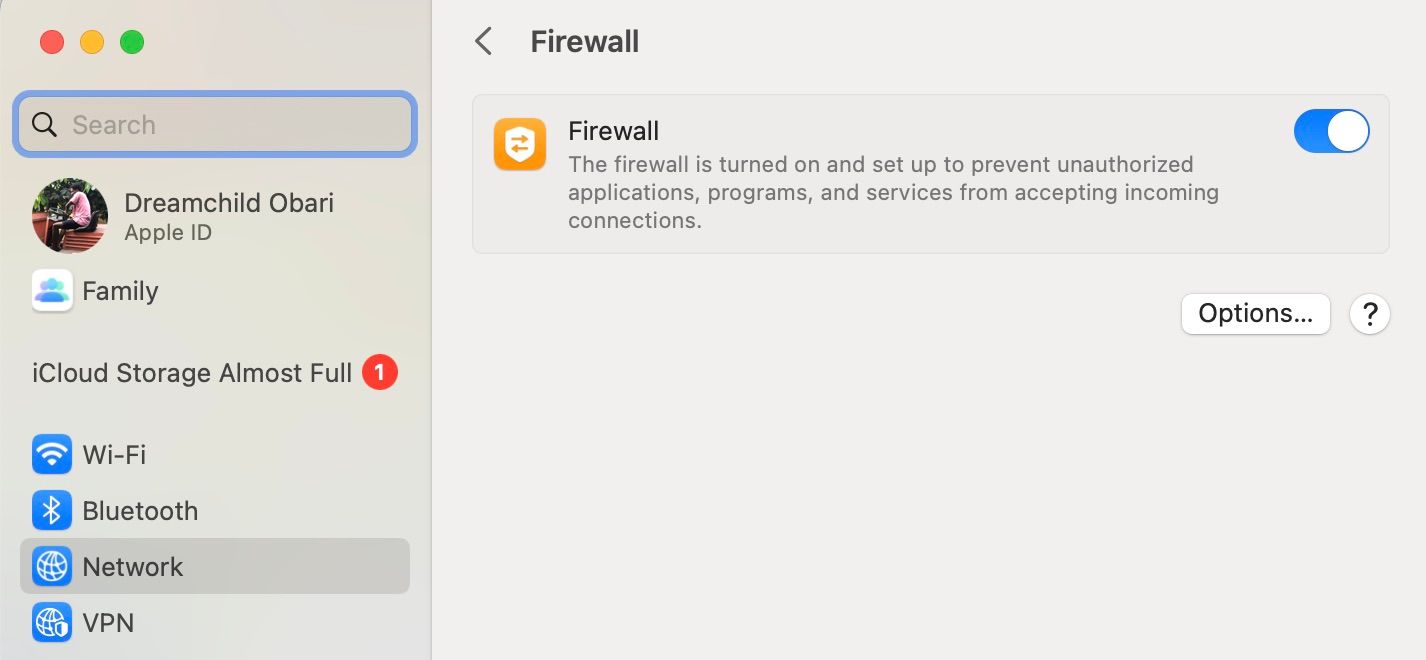
Activate a Firewall
Firewalls shield your computer from harm by checking if the data coming in follows certain rules. There are different kinds of firewalls, from built-in ones to third-party apps.
Follow these steps to turn on the default firewall in macOS:
- Click the Apple logo on the menu bar and select System Settings.
- Now, choose Network from the left pane.
- Next, click on Firewall on the right and turn the toggle on.
- You can click on Options if you want finer controls.
For more information on firewalls (including third-party ones), feel free to check our guide explaining whether or not your Mac needs a firewall.
Prevent Spyware Rather Than Cure It
Most times, before people discover they are being spied on and act on it, the perpetrator may already have collected vital information. This is why we highly recommend you approach your Mac's security with proactivity and prevention.
And when you do discover suspicious activity, be swift and decisive, taking all measures to ensure your precious computer is safe again.


.jpeg)