Virtualization-Based Security has been a feature on Windows 10 for years. It flew under the radar for many people because Microsoft wasn’t enforcing it; however, this is going to change with Windows 11.
Let’s take a closer look at VBS, see what it is, and how to enable and disable it.
What Is Virtualization-Based Security (VBS)?
Virtualization-Based Security (VBS) uses Windows Hypervisor to virtually isolate a segment of main memory from the rest of the operating system. Windows uses this isolated, secure region of memory to store important security solutions like log-in credentials and code responsible for Windows security, among other things.
The reason to host security solutions inside an isolated part of memory is to protect the solutions from exploits that aim to defeat these protections. Malware often targets Windows’ built-in security mechanisms to gain access to critical system resources. For instance, malicious code can gain access to kernel-level resources by defeating Windows’ code authentication methods.
VBS solves this problem by separating Windows security solutions from the rest of the OS. This makes Windows more secure since vulnerabilities can’t bypass the OS protections because they don’t have access to these protections. One of these protections is Hypervisor-Enforced Code Integrity (HVCI) or Memory Integrity.
HVCI leverages VBS to implement enhanced code integrity checks. These checks authenticate kernel-mode drivers and programs to make sure they come from trusted sources. So, HVCI ensures that only trusted code is loaded into memory.
In short, VBS is a mechanism by which Windows keeps critical security solutions separate from everything else. In case of a system breach, solutions and information protected by VBS will remain active since malicious code can’t infiltrate and disable/bypass them.
The Need for Virtualization-Based Security in Windows
To understand Windows 11’s need for VBS, we have to understand the threats that VBS is intended to eliminate. VBS is mainly a mechanism to protect against malicious code that traditional security mechanisms can’t handle.
In other words, VBS aims to defeat kernel-mode malware.
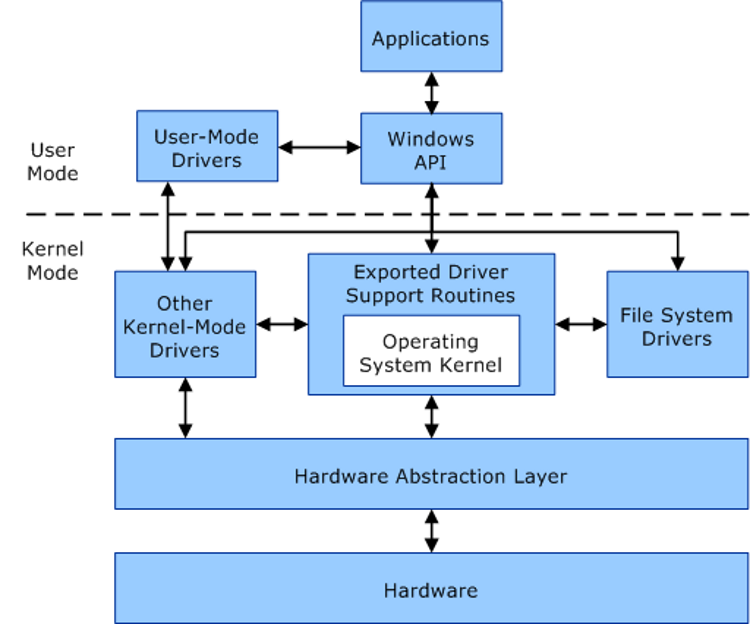
The kernel is the core of any OS. It is the code that manages everything and allows different hardware components to work together. Generally, user programs don’t run in kernel-mode. They run in user-mode. User-mode programs have limited capabilities as they don’t have elevated permissions. For instance, a user-mode program can’t overwrite another program’s virtual address space and mess with its operation.
Kernel-mode programs, as the name suggests, have full access to Windows kernel and in turn full access to Windows’ resources. They can make system calls, access critical data, and connect to remote servers without any hindrances.
In short, kernel-mode programs have elevated permissions than even anti-virus programs. So, they can bypass firewalls and other protections set up by Windows and third-party apps.
In many cases, Windows won’t even know there is malicious code with kernel-level access. This makes detecting kernel-mode malware extremely hard or, in some cases, even impossible.
VBS aims to change this.
As mentioned in the previous section, VBS creates a secure region of memory using Windows Hypervisor. Windows Hypervisor has the highest level of permissions in the system. It can check and enforce restrictions on system memory.
So, if a kernel-mode malware has altered pages in system memory, code integrity checks powered by the hypervisor examine memory pages for potential integrity violations inside the secure memory region. Only when a piece of code receives a green signal from these integrity checks is it made executable outside of this memory region.
Long story short, Windows needs VBS to minimize the risk of kernel-mode malware in addition to dealing with user-mode malicious code.
How Does Windows 11 Use VBS?
If we take a close look at the hardware requirements of Windows 11, we can see that most of the things Microsoft is mandating for a Windows 11 PC are needed for VBS to work. Microsoft details the hardware needed for VBS to work on its website, including:
- A 64-bit CPU with hardware acceleration features such as Intel VT-X and AMD-V
- Trusted Platform Module (TPM) 2.0
- UEFI
- Hypervisor-Enforced Code Integrity (HVCI) compatible drivers
From this list, it is quite clear that Windows 11’s major hardware requirements, including Intel 8th gen or above CPUs, are there to facilitate VBS and the features it enables. One such feature is Hypervisor-Enforced Code Integrity (HVCI).
Recall that VBS uses Windows Hypervisor to build a virtual memory environment separate from the rest of the OS. This environment acts as the OS's root of trust. In other words, only the code and security mechanisms residing inside this virtual environment are trusted. Programs and solutions residing outside including any kernel-mode code are not trusted until they are authenticated. HVCI is a key component that strengthens the virtual environment that VBS creates.
Inside the virtual memory region, HVCI checks kernel-mode code for integrity violations. The kernel-mode code under question can only allocate the memory if the code is from a trusted source and if the allocations don’t pose any threat to system security.
As you can see, HVCI is a big deal. Therefore, Windows 11 turns the feature on by default on every compatible system.
How to See if VBS Is Enabled on Your Computer
Microsoft enables VBS on compatible pre-built and OEM Windows 11 machines by default. Unfortunately, VBS can tank performance by as much as 25%. So, if you are running Windows 11 and don’t need cutting-edge security, make sure to turn VBS off.
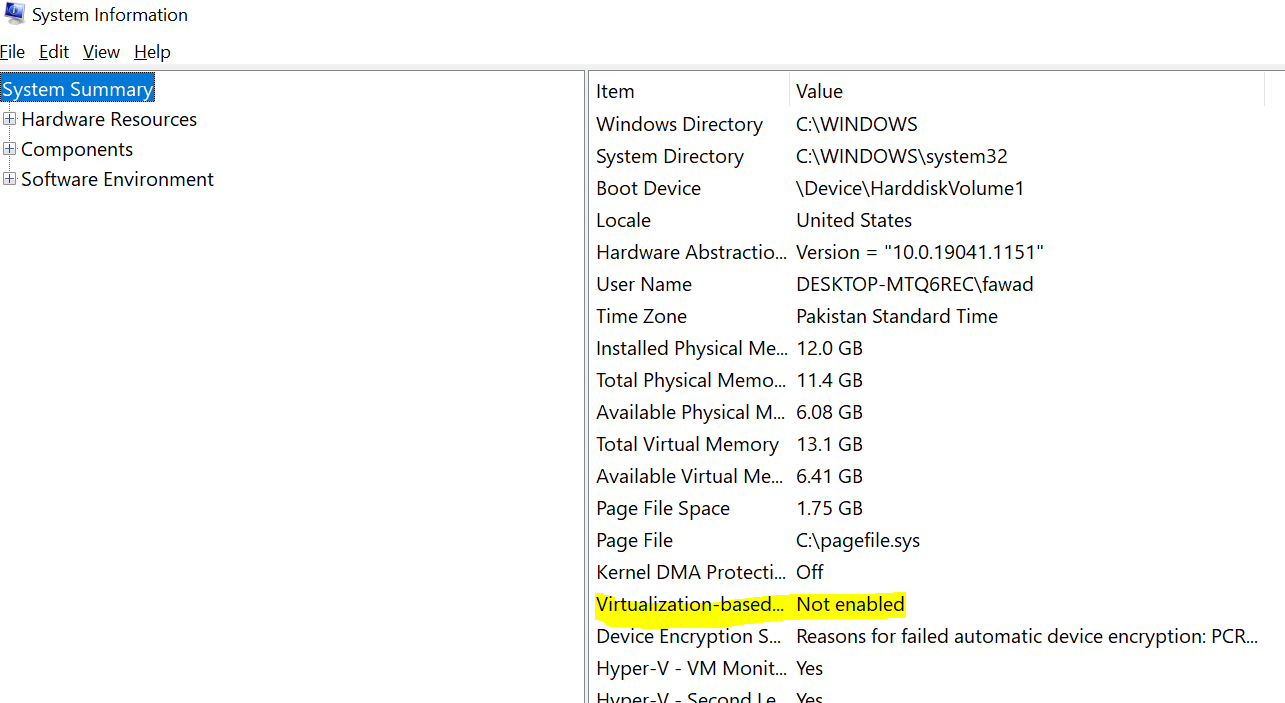
To check VBS is enabled on your computer, hit the Windows key, type “system information”, and choose the relevant result. Once the app opens up, scroll down to Virtualization-based security and see if it is enabled.
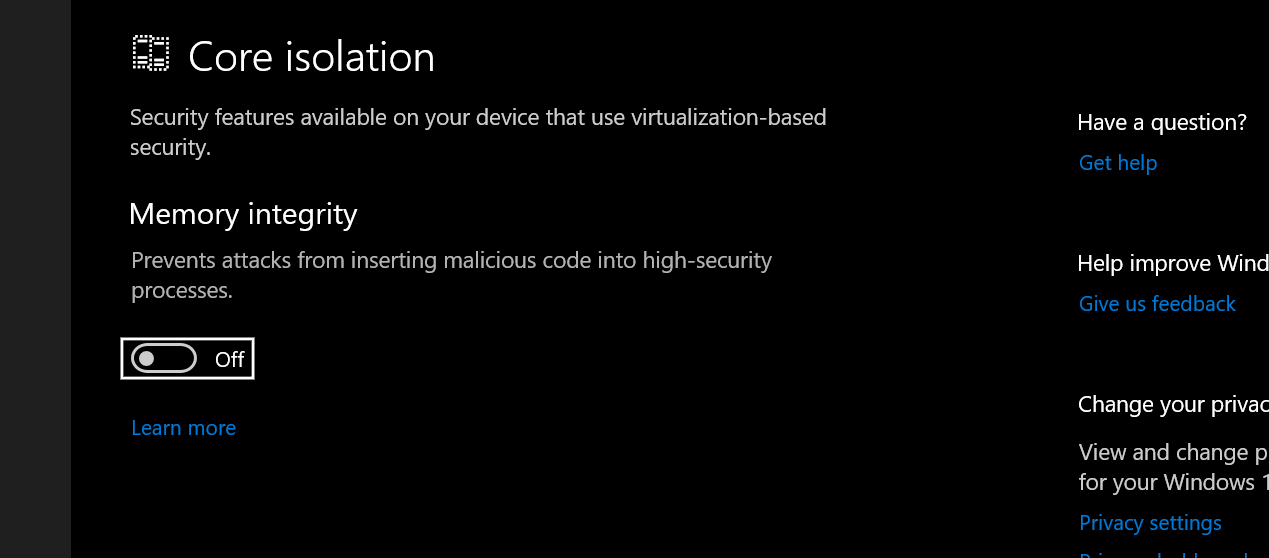
To enable/disable VBS, press the Windows key, type “core isolation”, and pick the relevant result. In the Core Isolation section, toggle Memory integrity On/Off.
Finally, restart your PC.
VBS Can Make Windows 11 Much More Secure... but There Are Drawbacks
Windows 11’s big security features like HVCI rely heavily on VBS, for good reason. VBS is an effective way to defeat malicious code and protect the OS from security breaches. But because VBS relies on virtualization, it can eat a fair chunk of your system performance.
For Microsoft’s enterprise customers, this security bump, even when it comes at the cost of performance, is a no-brainer. But for average folks who want a speedy Windows experience, especially during gaming, VBS’s performance cost can be hard to swallow.
Thankfully, Microsoft allows you to disable VBS on your machine. But don't worry about disabling VBS. Windows 11 is way more secure than Windows 10 even without VBS.