Secure Shell (SSH) is a cryptographic network protocol that enables secure communication over an insecure network. The protocol was developed to replace old insecure protocols, increasing security and privacy across all operating systems.
So, what is SSH?
What Is SSH?
SSH stands for Secure Shell and is also known as Secure Socket Shell.
SSH is a secure network communication protocol. The protocol is primarily used by network administrators to connect to remote devices securely, but SSH has a whole host of common functionality.
Prior to SSH's development, users and administrators used insecure network protocols, such as Telnet, to communicate with remote devices. These now-outdated protocols send critical information such as passwords and login information in plaintext, making them an easy target for an attacker.
SSH typically communicates over port 22.
SSH1 vs. SSH2: What's the Difference?
There are "two" versions of SSH. We say "two" because between those two versions, there were many implementations and updates leading from SSH1 to SSH2.
As you might expect, SSH2 is the more secure protocol. It provides better protection against attackers and eavesdroppers, supports stronger encryption algorithms, and makes heaps of general improvements over the original SSH protocol.
What Is OpenSSH?
OpenSSH is a widely-used open-source implementation of SSH. The original free version of SSH was developed by Tatu Ylönen. Later versions of Ylönen's work were proprietary, meaning they cost money to license and use, and you couldn't make unauthorized changes to the protocol.
Thus, a team of developers forked the original free version of SSH and named it OpenSSH, which is now developed as part of OpenBSD (an open-source operating system). All major operating systems, such as Windows, macOS, and the numerous Linux distributions, support OpenSSH.
How Does SSH Work?
To understand how SSH works, you need to understand two things.
First, what is a shell? Second, how does public-key cryptography work? Let's figure out what a shell actually is before considering the details of an SSH connection.
What Is a Shell?
A shell is a piece of software that enables you to communicate with the operating system it is hosted on. Typically, you use commands to interact with the shell, although graphical user interfaces (GUIs) do exist.
One important thing to know is that you don't have to be sitting at the computer to use a shell. You can operate a shell remotely over a network connection using—you guessed it—SSH.
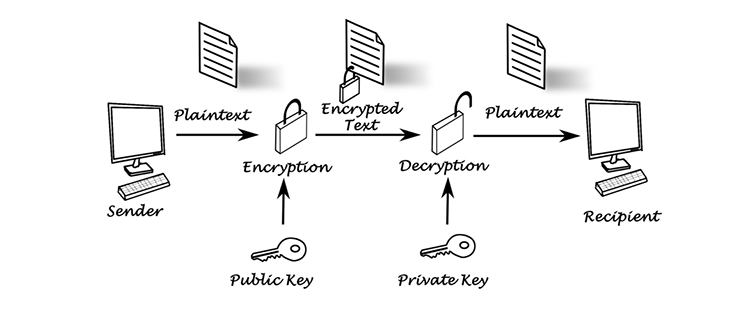
What Is Public-Key Encryption?
In modern computing, there are two primary encryption types:
- Symmetric algorithm: Uses the same key for both encryption and decryption. Both parties must agree on the algorithm key before commencing communication.
- Asymmetric algorithm: Uses two different keys: a public key and a private key. This enables secure encryption while communicating without previously establishing a mutual algorithm.
SSH is a type of public-key cryptography, using both of the above encryption types to create a secure connection.
SSH uses both above encryption types to create a secure connection in a client-server model. When the client attempts to create a connection with the server, each party communicates their encryption protocols.
After settling on a matching encryption protocol, the client and server use the Diffie-Hellman Key Exchange Algorithm to arrive at a shared encryption key as part of a symmetric algorithm. This encryption key remains a secret throughout the entire connection and is used to encrypt all communications between the two parties.
So, where does the asymmetric encryption feature?
In public-key cryptography, you have two keys: a public key and a private key. You can send the public key to other people, while the owner only knows the private key. Together, they form a pair.
Before the symmetric key exchange takes place and the secure communication channel establishes, SSH uses asymmetric encryption to create a temporary key pair. The client and server exchange public keys, validating each other before the symmetric key creation process begins.
What Encryption Algorithm Does SSH Use?
As SSH uses symmetric encryption to secure your connection, you can configure SSH to use a wide range of symmetric encryption algorithms, including AES, Blowfish, Twofish, Salsa20/ChaCha20, 3DES, IDEA, and more.
Related: Common Encryption Types and Why You Shouldn't Make Your Own
Is SSH the Same as SSL/TLS?
While both SSH and SSL/TLS provide security for a previously insecure network protocol, SSH and SSL/TLS are not the same.
The Secure Sockets Layer (SSL) and its successor, Transport Layer Security (TLS), provide an encrypted communication tunnel. You use TLS every day when sending emails or browsing the web. SSL and TLS are application layer protocols. In internet communication networks, the application layer standardizes communications for end-user services.
While both SSL/TLS and SSH provide encryption, the network protocols themselves are designed for different things. SSL/TLS is designed to protect your data connection, whereas SSH is designed to allow secure remote access and command execution.
However, you can use SSH in conjunction with SSL to transfer files, using the SSH File Transfer Protocol (SFTP) or the Secure Copy Protocol (SCP). Incidentally, using the SCP is just one way you can copy data from your PC to a Raspberry Pi.
Is SSH the Same as a VPN?
Like the above question, a Virtual Private Network (VPN) also provides an encrypted tunnel for your communication. But where SSH provides a secure connection in a client-server configuration to a specific computer, a VPN provides a secure connection between your computer and the VPN server.
You're not executing remote commands on the VPN server. Rather, when you switch your VPN on, data transmissions to and from your computer travel through the encrypted tunnel through to the VPN server before "re-joining" the wider internet.
So, SSH enables a secure connection to a single computer to execute remote commands, while a VPN enables an encrypted tunnel between your computer and the VPN server.
This process can obscure your computer's location and provide some additional security while using an internet connection. Want to know more? Here's how a VPN can protect your privacy.
Which Platforms Is SSH Available On?
So long as your chosen operating system has an SSH client or integrated SSH functionality, the secure network protocol is available to you.
For example, you can follow our beginners guide to SSH on Linux or check out how easy it is to use SSH in Windows 10.
SSH Is Here to Stay
Secure Shell isn't going anywhere. SSH provides a secure and easy to use network protocol that is freely available to any user. It works on every platform and is found globally. Now you've read this short guide to SSH, you're much better prepared to use it in the future.