SMB is a protocol that allows computers to share files and hardware (such as printers and external hard drives) when connected to the same network.
As the popularity of the SMB protocol increases, so has the number of malicious attacks. SMB protocol is vulnerable to cyberattacks because its old versions do not use encryption, which means that any hacker who knows how to exploit it can gain access to your files and data.
And there are other risks associated with SMB, which make it essential to understand how the protocol works, its different types, and how to stay protected.
What Is the SMB Protocol?
SMB stands for Server Message Block. It is a network protocol used to share data between computers and devices on a local or wide area network. The protocol allows local network computers to share resources such as files, printers, and other devices.
SMB was developed in the mid-1980s by IBM for file sharing in DOS, but it has since been adopted by many other operating systems, including Microsoft's Windows, Linux, and macOS.
The SMB protocol is an integral part of many day-to-day operations for businesses and organizations, as it makes it easy to access files and resources from other computers on the network.
Imagine you are working with a team in which members work remotely from different locations. In such cases, the SMB protocol is a great way to share files quickly and easily. It will allow each team member to access the same data and collaborate on projects. Multiple people can view or edit the same file remotely as if it is present on their own computer.
How Does the SMB Protocol Work?
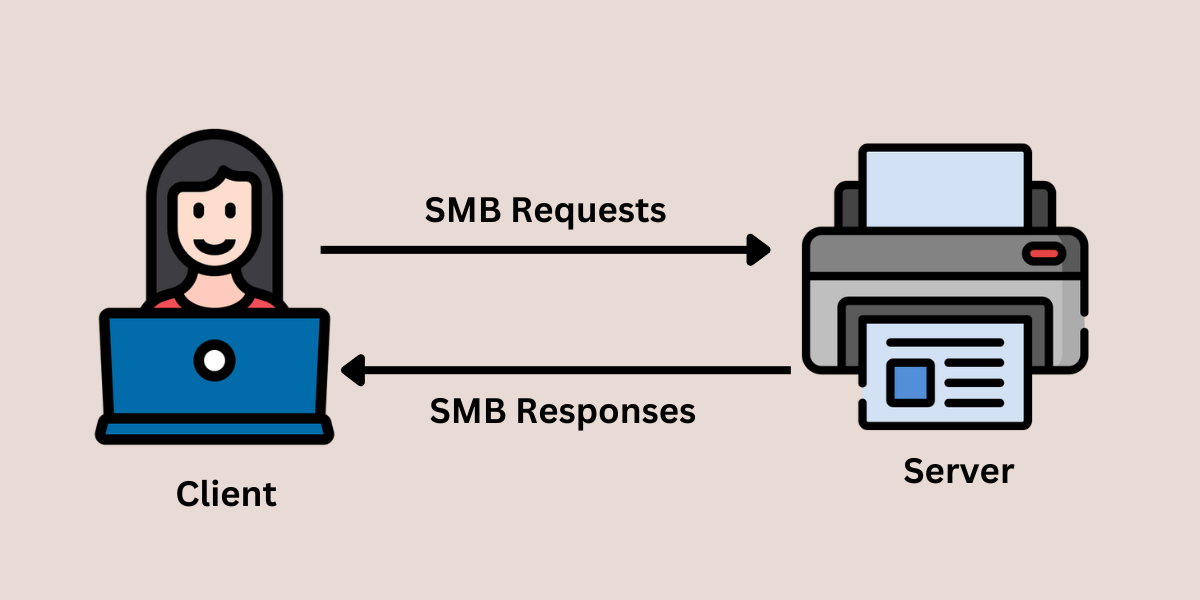
The SMB protocol follows the request and response method to create a connection between the client and server. Here are the steps in which it works:
Step 1. Request from client: The client (the device making the request) sends a request to the server using SMB packets. The packet contains the full path of the requested file or resource.
Step 2. Response from server: The server (the device with access to the requested file or resource) evaluates the request and, if successful, responds back with an SMB packet containing more information on how to access the data.
Step 3. Process by Client: The client receives the response and then processes the data or resource accordingly.
Let us understand this with an example. Say you want to print a document from your cabin, and the printer is in another room or area of the office. Once you command to print the document, your computer (the client) will send the request using the SMB packets to the printer (the server) to print it. The printer will evaluate the request and then respond back using the SMB packets about the status, such as whether the document is printing, queued for printing, or cannot be printed due to printer error.
Types of SMB Protocol
With the advancement in technology, the SMB protocol has also seen a few upgrades. The various types of SMB protocols that are available today are:
- SMB Version 1: This is the original version of the SMB protocol released in 1984 by IBM for exchanging files on DOS. Microsoft later modified it for using on Windows.
- CIFS: Common Internet File System (CIFS) is a modified version of SMBv1, which was primarily developed to support the sharing of larger files. It was first released with Windows 95.
- SMB Version 2: Microsoft released SMB v2 in 2006 with Windows Vista as a more secure and efficient alternative to the older versions. This protocol introduced features such as improved authentication, larger packet size, fewer commands, and better efficiency.
- SMB Version 3: Microsoft released SMB v3 with Windows 8. It was designed to improve performance and introduce support for end-to-end encryption and improved authentication methods.
- SMB Version 3.1.1: The latest version of the SMB protocol was released in 2015 with Windows 10 and is fully compatible with all previous versions. It introduces more security features, such as AES-128 encryption and extended security features for tackling malicious attacks.
What Are the Dangers of the SMB Protocol?
Although the SMB protocol has been a great asset for many businesses, it is also associated with some security risks. Hackers have targeted this protocol to gain access to corporate systems and networks. It has become one of the most common attack vectors used by cyber criminals to breach corporate networks and systems.
What's worse is despite the upgraded versions of SMB available, many Windows devices are still running on the older, less secured version 1 or 2. This increases the chances of malicious actors exploiting these devices and gaining access to sensitive data.
Here are the most common SMB exploits.
Brute Force Attacks
The most common attack vectors used by hackers against SMB protocol include brute force attacks. In such attacks, hackers use automated tools to guess the correct username and password combinations. Once they gain access to the network, they can steal sensitive data or plant malicious software on the system.
Man-in-the-Middle Attacks
Another attack vector used against SMB protocol is man-in-the-middle attacks. Here, a hacker injects malicious code into the network, which allows them to intercept the communication between two systems. They can then view and alter the data being exchanged.
Buffer Overflow Attacks
Hackers also use buffer overflow attacks against the SMB protocol. In such attacks, hackers send an enormous amount of data to fill up a system’s memory with junk, thus crashing it. This technique is often used to plant malicious software in the system, which can be used to gain access to confidential data or launch a denial-of-service attack.
Ransomware Attacks
Ransomware attacks are also a major threat to SMB protocol. In this type of attack, hackers encrypt the data stored on a system and then demand ransom in exchange for encryption keys. If the ransom is not paid, they can delete all the encrypted data permanently.
Remote Code Execution
Remote code execution is another attack vector used against the SMB protocol. In such attacks, hackers inject malicious code into the system, which allows them to take control of it remotely. Once they have accessed the system, they can steal confidential data or exploit other vulnerabilities in the network.
Stay Protected While Using the SMB Protocol
Although there are a number of risks associated with the SMB protocol, it is still an important part of Windows. Therefore, it is vital to ensure that all business systems and networks are secured against malicious attacks.
To stay protected, you should only use the latest version of the SMB protocol, regularly update your security software, and monitor your network for suspicious activities. It is also important to train your staff on best practices for cybersecurity and ensure that all users are using strong passwords. By following these measures, you can ensure that your business remains secure from malicious attacks.