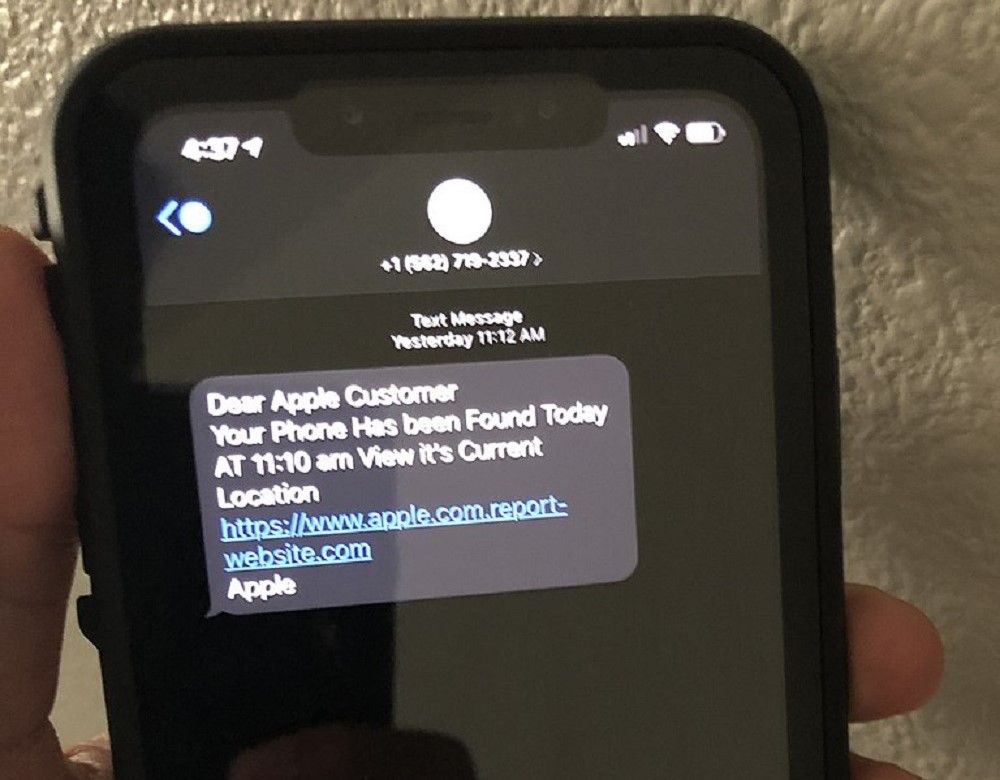
Anyone who has a phone and can receive calls is susceptible to a pretexting attack. Pretexting attackers can call you under false pretenses, like pretending to be from a company’s technical department or another team with access to passwords, to manipulate you and obtain information. These attackers can sell or misuse this data, so you should actively safeguard your information.
So what is pretecting? How can you protect yourself?
What Is Pretexting?
Pretexting, a form of social engineering, occurs when a hacker uses deceptive means to try and gain access to a system, network, or any information. The attacker conjures up a false scenario, known as the pretext, pretending to be someone experienced, like an IT personnel, HR manager, or even a government agent. This attack can occur online and in person.
Pretexting started in the UK in the early 2000s when journalists looking for juicy scoops on celebrities used extreme measures to spy on them. The competition between news brands was fierce, leading journalists to invent new ways of getting private information.
First, it was as simple as snooping on the target celebrity’s voicemail. Voicemails came with a default PIN that many users didn’t bother to change, and the journalists exploited this. If the default PIN had been changed, some went as far as calling their targets and pretending to be technicians from the phone company. They would obtain the voicemail PINs and gain access to information hidden there.
Generally, pretexting scenarios usually feel like they require a great deal of urgency or sympathy from the would-be victim. The attackers may use emails, phone calls, or text messages to get in contact with their targets.
Elements of a Pretexting Attack
In a pretexting scenario, there are two main elements: the "character" played by the scammer and the "plausible situation" meant to fool the target into believing the character has a right to the information they are after.
Imagine that you try to process a transaction, and it doesn’t go through. You don’t get the pizza you ordered, and the online store is closed. What a bummer! But that’s not all. A few minutes later, by some inexplicable error, you find out that your account was debited.
Soon after, the attacker calls and gets in character, pretending to be a customer care agent from your bank. Because you’re expecting a call, you fall for this plausible situation and give out your credit card information.
How Does Pretexting Work?
Pretexting takes advantage of weaknesses in identity verification. During voice transactions, physical identification is near to impossible, so institutions resort to other methods to identify their customers.
These methods include requesting verification of date of birth, next of kin, number of offspring, contact address, mother’s maiden name, or account number. Most of this information can be obtained online from the target’s social media accounts. Pretexters use this information to "prove" the authenticity of their character.
The scammers use your personal information to get you to reveal more sensitive information that they can use. Getting this personal information requires careful research because the more specific the data obtained is, the more compelled you will be to give up even more valuable information.
Scammers also have direct sources of information other than social media. They can spoof the phone number or email domain name of the organization they are impersonating to add more credibility to the plausible situation being sold to the target.
3 Notable Pretexting Techniques
There are various pretexting techniques scammers and hackers use to gain access to sensitive information.
1. Vishing and Smishing
These techniques are very similar. Vishing attacks involve using voice calls to persuade a victim to give up the information needed by the scammer. Smishing scams, on the other hand, use SMS or text messages.
Vishing has a higher chance of success because targets are more likely to ignore text messages than direct calls from seemingly essential personnel.
2. Baiting
Baiting involves using a large reward to collect information and could also include faking a trusted source.
The scammer could pretend to be a lawyer claiming you have an inheritance from a distant relative and would need your financial details to process the transaction. High-ranking personnel of a target organization could be victims too.
Another common maneuver is dropping off an envelope containing a flash drive with the company’s logo and a message to work on an urgent project. The flash drive would be laden with malware that the hackers would use to gain access to the company’s servers.
3. Scareware
In this method, the hackers use fear as a tactic. A notable example is a pop-up on an insecure site, telling you that there is a virus on your device and then asking you to download an antivirus program that’s actually malware. The scareware can also be distributed using emails and links in text messages.
How to Protect Yourself from Pretexting Attacks
Pretexting attacks are so prevalent that there’s almost no way to stop them completely. However, steps can be taken to curb them significantly.
One step is email analysis. Looking at the domain name of an email can give an insight into whether it is spoofed or genuine. However, pretexting attacks can spoof email domains so look almost identical to the original, making it extremely difficult to spot these pretexts.
But with the advancement of complex AI tech, email analysis has become more accessible. AI can now spot phishing patterns and look for signs of pretexting. It can identify anomalies in traffic and spoofed email display names, as well as phrases and text common with pretexting attacks.
User education is, of course, essential. No one should ask for your bank password, credit card pin, or serial number. You should immediately report a request for any of these to the appropriate authorities. Furthermore, reminding your family, friends, and employees not to click on unknown links and to avoid visiting insecure websites could be enough to prevent the entry of malware into your company’s servers.
Don't Fall for Pretexting Scams
Fishing out a pretexting operation might not be easy, but there are simple steps you can take to avoid falling victim. Don’t click on links on insecure websites, and don't reveal your login details to anyone. There are verified customer service care lines on your bank’s online platform. When any customer care agent contacts you, ensure the numbers correspond with the official line.