Windows Active Directory is a service created by Microsoft that is still used today in numerous organizations around the world. It connects and stores information about multiple devices and services on the same network together. But if a company's Active Directory is not properly and securely configured, it could lead to a series of vulnerabilities and attacks.
One of the more popular Active Directory attacks is the LLMNR Poisoning attack. If successful, an LLMNR poisoning attack can give a hacker admin access and privileges to the Active Directory service.
Read on to discover how the LLMNR poisoning attack works and how to prevent it from happening to you.
What Is LLMNR?
LLMNR stands for Link-Local Multicast Name Resolution. It is a name resolution service or protocol used on Windows to resolve the IP address of a host on the same local network when the DNS server is not available.
LLMNR works by sending a query to all devices across a network requesting a specific hostname. It does this using a Name Resolution Request (NRR) packet that it broadcasts to all devices on that network. If there is a device with that hostname, it will respond with a Name Resolution Response (NRP) packet containing its IP address and establish a connection with the requesting device.
Unfortunately, LLMNR is far from being a secure mode of hostname resolution. Its main weakness is that it uses one's username alongside the corresponding password when communicating.
What Is LLMNR Poisoning?
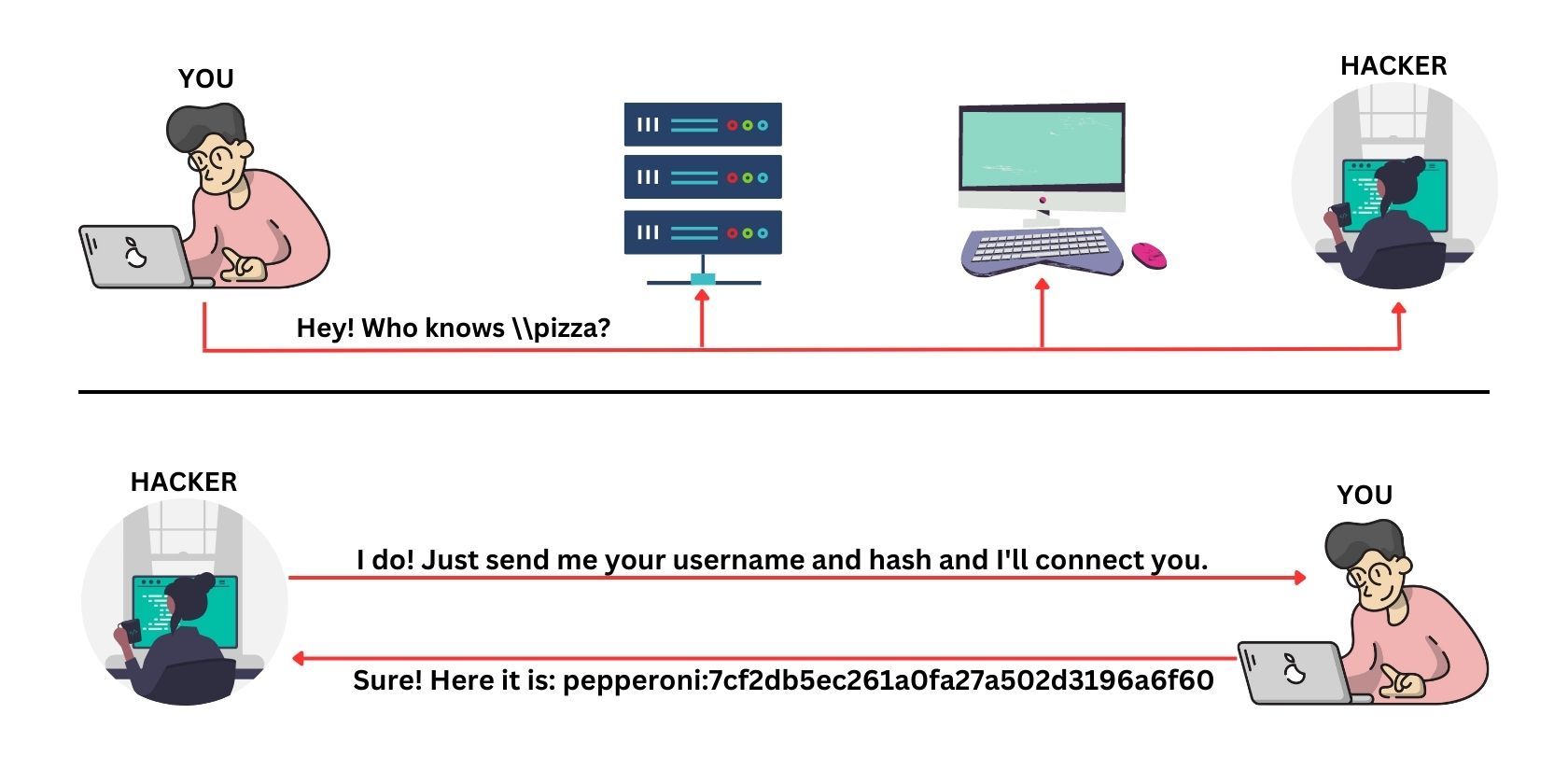
LLMNR Poisoning is a type of man-in-the-middle attack that exploits the LLMNR (Link-Local Multicast Name Resolution) protocol in Windows systems. In LLMNR Poisoning, an attacker listens and waits to intercept a request from the target. If successful, this person can then send a malicious LLMNR response to a target computer, tricking it into sending sensitive information (username and password hash) to them instead of the intended network resource. This attack can be used to steal credentials, perform network reconnaissance, or launch further attacks on the target system or network.
How Does LLMNR Poisoning Work?
In most cases, LLMNR is achieved using a tool called Responder. It is a popular open-source script usually written in python and used for LLMNR, NBT-NS, and MDNS poisoning. It sets up multiple servers like SMB, LDAP, Auth, WDAP, etc. When run on a network, the Responder script listens to LLMNR queries made by other devices on that network and performs man-in-the-middle attacks on them. The tool can be used to capture authentication credentials, gain access to systems, and perform other malicious activities.
When an attacker executes the responder script, the script listens quietly for events and LLMNR queries. When one occurs, it sends poisoned responses to them. If these spoofing attacks are successful, the responder displays the target's username and password hash.
The attacker can then try to crack the password hash using various password-cracking tools. The password hash is usually an NTLMv1 hash. If the target's password is weak it would be brute forced and cracked in little to no time. And when this happens, the attacker would be able to log into the user's account, impersonate the victim, install malware, or perform other activities like network reconnaissance and data exfiltration.
Pass the Hash Attacks
The frightening thing about this attack is that sometimes the password hash need not be cracked. The hash itself can be used in a pass the hash attack. A pass the hash attack is one where the cybercriminal uses the uncracked password hash to gain access to the user's account and authenticate himself.
In a normal authentication process, you enter your password in plain text. The password is then hashed with a cryptographic algorithm (such as MD5 or SHA1) and compared to the hashed version stored in the system's database. If the hashes match, you become authenticated. But, in a pass the hash attack, the attacker intercepts the password hash during authentication and reuses it to authenticate without knowing the plain text password.
How to Prevent LLMNR Poisoning?
LLMNR Poisoning might be a popular cyberattack, this also means that there are tested and trusted measures to mitigate it and secure you and your assets. Some of these measures include the use of firewalls, multifactor authentication, IPSec, strong passwords, and disabling LLMNR altogether.
1. Disable LLMNR
The best way to avoid an LLMNR poisoning attack from happening to you is to disable the LLMNR protocol on your network. If you aren't using the service, there's no need to have the added security risk.
If you do need such functionality, the better and more secure alternative is the Domain Name System (DNS) protocol.
2. Require Network Access Control
Network Access Control prevents LLMNR poisoning attacks by enforcing strong security policies and access control measures on all network devices. It can detect and block unauthorized devices from accessing the network and provide real-time monitoring and alerts
Network Access Control can also prevent LLMNR poisoning attacks by enforcing network segmentation, which limits the attack surface of the network and restricts unauthorized access to sensitive data or critical systems.
3. Implement Network Segmentation
You can limit the scope of LLMNR Poisoning attacks by dividing your network into smaller subnets. This can be done through the use of VLANs, firewalls, and other network security measures.
4. Use Strong Passwords
In the event that an LLMNR Poisoning Attack takes place, it is advisable to use strong passwords that cannot be easily cracked. Weak passwords, such as those based on your name or a sequence of numbers, can be easily guessed or already exist in a dictionary table or a password list.
Maintain a Strong Security Posture
Maintaining a good security posture is a critical aspect of protecting your systems and data against cyber threats like LLMNR Poisoning. Doing so requires a combination of proactive measures, like implementing strong passwords, regularly updating software and systems, and educating employees on security best practices.
By continuously assessing and improving security measures, your organization can stay ahead of breaches and threats and protect your assets from attacks.