Internet Control Message Protocol (ICMP) is a third layer (network layer) protocol in the OSI seven-layer model. The protocol diagnoses network connectivity or data transmission issues between devices. It helps by sending, receiving, and processing ICMP messages to report connectivity issues to the source network device.
Hence, the primary purpose of the ICMP protocol is to report errors at the network layer. However, malicious actors can manipulate its functionality to launch attacks like Distributed Denial of Service (DDoS) and Ping of Death attacks. Here, you'll learn about the ICMP protocol, its use case, and the parameters that are important to understand ICMP messages.
How Does ICMP Work?
Routers use ICMP protocol to perform network management and issues diagnosis. It generates and sends error messages to the sender device when the network disables the delivery of packets to the destination device. These error messages include time exceeded, parameter problem, destination unreachable, network congestion, etc.
For instance, when a sender sends data from one device to the destination device in the form of an IP datagram, it travels through multiple routers or intermediary devices. On occasion, there can be an error in forwarding that IPV4 datagram. Hence, ICMP messages are divided into two broad categories: error messages, and query messages.
Error-Reporting Messages
These are the messages that the router or intermediary host may face in datagram processing:
- Time Exceeded: The ICMP packet has a time-to-live parameter that when it reaches 0, the router or host discards the datagram and sends a time exceeded error message. The message is also sent when the destination does not receive all data fragments.
- Destination Unreachable: The connection initiating device receives an unreachable destination error message when the router or intermediary host fails to deliver it. Consequently, the devices discard the datagram.
- Source Quench: When the devices fail to deliver the datagram due to network congestion, they send an ICMP "source quench message" to the message sender. The error reporting message adds flow control in the network layer by informing the source device about congestion in the path and slowing down the data sending process.
- Redirection: A router in a non-optimal path redirects the packet to a router with an optimal path between the source and destination. As such, it updates the source about the change in its route.
- Parameter Problem: The source device receives this message when there is any missing value in the datagram header. For instance, the difference in calculated checksum at the destination from the source generates this ICMP error message.
Query Messages
The query messages occur in pairs and provide specific information from the intermediate devices to the source device.
- Echo-Request and Echo-Reply Message: These messages help resolve network diagnostic issues.
- Timestamp Request and Reply: These time stamp requests and reply messages help determine the round trip time between the devices.
Understanding ICMP Parameters
The ICMP messages data is encapsulated under the IP header, which means the ICMP datagram header comes after IPv4/v6 information. The first part of the ICMP packet header contains the parameters that help network devices determine the error or query message.
Among the first 32 bits, the first 8 bits determine the message type, the next 8 bits determine the code of the message, and the remaining bits contain information related to the data integrity. Hence, the three informational fields are: ICMP types, ICMP code, and Checksum.
ICMP Types
The type determines the purpose of the ICMP packet. As it briefly explains why the source device is receiving that message. There are 0-255 types of ICMP messages such that each type provides different information. Some important ICMP types are:
0: Echo Request
3: Destination Unreachable
4: Source Quench
5: Redirect
8: Echo Reply
11: Time Exceeded
12: Parameter Problem
30: Traceroute
ICMP Code
The ICMP code provides additional information about the messages. For instance, ICMP type 3 with code 0-15 specifies why the destination is unreachable; that is, if the code is 0, then it's because the network is unavailable. Similarly, for type 3 code 1, the message specifies that the host is unreachable.
Moreover, type 8 code 0 and type 0 code 0 represent echo-request and echo reply messages. Hence, each message type with the same code value gives different network information.
Checksum
The checksum is an error detections mechanism that determines data integrity. The checksum value represents the bits in the transmission message. The sender calculates and includes the data checksum, and the receiver recalculates the value and compares it with the original one to determine any changes to the original message during transmission.
The second part of the header points to the byte value that is the cause of the problem in the original message. Lastly, the end part of the ICMP packet is the actual datagram.
Examples of ICMP in Use
Here are some working examples of ICMP protocol in various network management and administrative utilities.
Ping
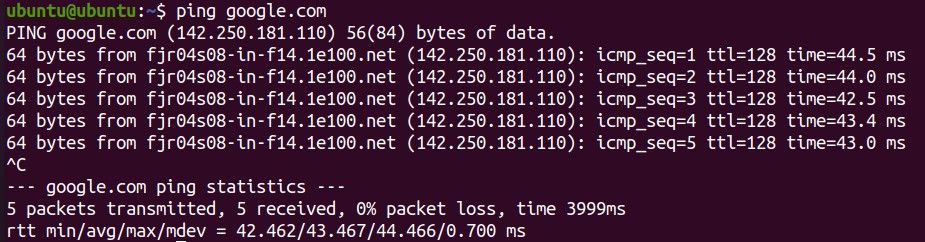
Ping is a command-line utility that relies on ICMP echo-request and echo-reply messages to test network availability and latency between devices. The utility simply determines the availability of the destination server by estimating the total packet sent or received and the percentage of packet loss. It also helps determine the total maximum transmission unit (MTU) size.
Use ping <ip_address> to determine google.com availability:
Traceroute
Traceroute is another command-line utility that uses echo-request and echo-reply messages with a TTL variable to map the path between source and destination devices. It is also useful in determining the response delays and assures accuracy by querying each hop multiple times.
How Does ICMP Work Without a Port?
From the above explanation, ICMP is a connectionless protocol that sends data independently as a datagram, and its header appears after IPv4 details. However, you can also notice the absence of a port number which raises the question of how devices receive the ICMP data or become aware of any connection?
The answer is pretty simple. The ICMP protocol was designed to work at the network layer of the OSI Model and communicate between routers and hosts to share information. Port numbers are a part of the Transport Layer, and ICMP is neither a TCP nor a UDP protocol. Lastly, the ICMP type and code combination help devices determine the message and get all the information about the network.
Error and Flow Control With ICMP
The above details about the ICMP protocol show how it ensures flow control and error control of data at layer three of an OSI model. The protocol messages and parameters in the first part of the ICMP packet header cover all the aspects of network management and diagnosis issues.
It's important to know that improper firewall settings can allow attackers to ping sweep through the organization's network and make it prone to DDOS, ping of death, and ICMP flood attacks. You can use Wireshark to capture packets from the internet and perform a detailed analysis of the ICMP packets for better understanding.