When developers need to extend the functionality of a program they don't have the source code for, they often turn to DLL hooking. This is an unorthodox way of making a program do something it isn't intended to do.
Thing is, hackers also use this technique for all the wrong reasons, like weaponizing harmless applications or cracking software. So what is DLL hooking, and how does it actually work?
What Is a DLL?
Every application depends on some files outside its base code to run. These external files contain code and data a program needs to function properly. When any of these external files go missing, the program may have stability issues or outright refuse to run.
In the Windows operating system, these external files are called DLL or dynamic link libraries. Dynamic link libraries are essential components of the Windows operating system, providing reusable code and resources that can be shared across multiple applications.
External files on Windows are known as libraries. There are two types of libraries: dynamic and static. Dynamic libraries are loaded at run-time and static libraries are loaded at compile time. DLL is a dynamic library.
What Is DLL Hooking?
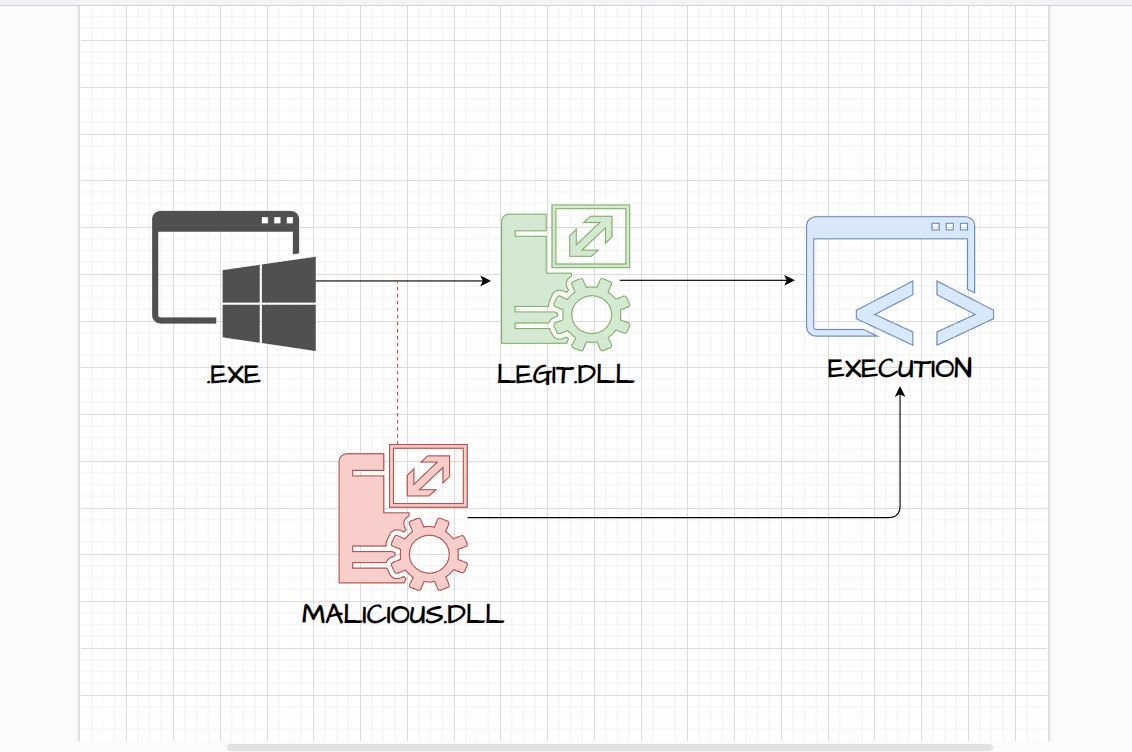
DLL hooking is a technique that includes intercepting and altering function calls programs or processes make to a DLL. Essentially a Man-in-The-Middle setup is established where a hook sits in between a program and the DLLs it calls. All or targeted function calls are then traced and altered.
Here's an example of a DLL hooking attack workflow:
- The attacker analyzes the function calls made by the program and the DLL files it depends on.
- The attacker creates a hook using one of the many implementation techniques like IAT hooking, inline hooking, COM hooking, etc.
- Arbitrary code execution happens.
- Original function call execution may or may not happen.
- The attacker covers up their tracks by deleting the hook and reverting all alterations made.
DLL hooking is a sophisticated technique that can be employed for both good (such as extending program functionality, debugging, and logging) or for bad (such as bypassing security measures, stealing sensitive data, executing arbitrary code, and writing video game hacks).
How Does DLL Hooking Work?
Before diving into implementing DLL hooking, it's important to clear up the basics. Let's take a step back and understand what happens when a function call is made to a DLL by a program.
When a program calls a function in a DLL, the operating system first looks up the function's name in the program's Import Address Table and gets the function's address from the DLL's Export Address Table.
Once the address to the function is resolved, the program can jump to the address of the function to access and execute it. DLL hooking revolves around intercepting this process and redirecting the function call to a different function. There are several ways to implement DLL hooking. Let's look at the most commonly used techniques for implementing it.
This can get pretty technical, so it may help if you are a Windows power user or otherwise have a strong understanding of Windows internals.
IAT Hooking
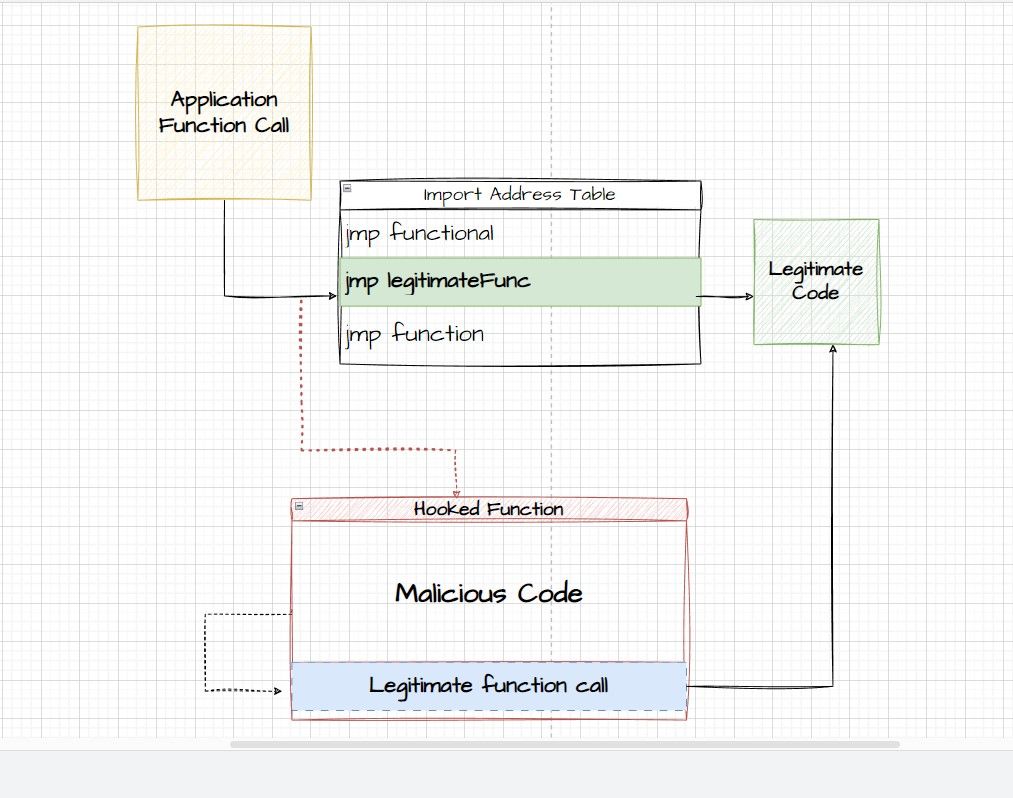
IAT hooking is an effective technique widely employed by malware authors to circumvent security measures and evade detection. The Import Address Table (IAT) is a data structure that is loaded onto the memory whenever a new process is created. IAT contains the names of all the imported function calls and their memory addresses.
When a program calls a function in the DLL, the function name is first searched for in the IAT and if the memory address of the said function is not found in the IAT then it is established from the DLL's Export Address Table.
It is a data structure where all the functions exported by the DLL are mapped to their memory addresses. In IAT hooking, an adversary can modify the IAT of a process and replace legitimate function mappings with malicious ones thus disrupting the intended operation and making the program execute arbitrary code.
Here's what the general attack flow in IAT hooking looks like:
- A program makes a function call.
- The function address is located in the IAT.
- Since the IAT has been hooked; the function address has been altered, and the memory location of a malicious function is loaded.
- The program jumps to the location of the malicious function and arbitrary code is executed.
- Finally, the original function call is executed.
Inline Hooking
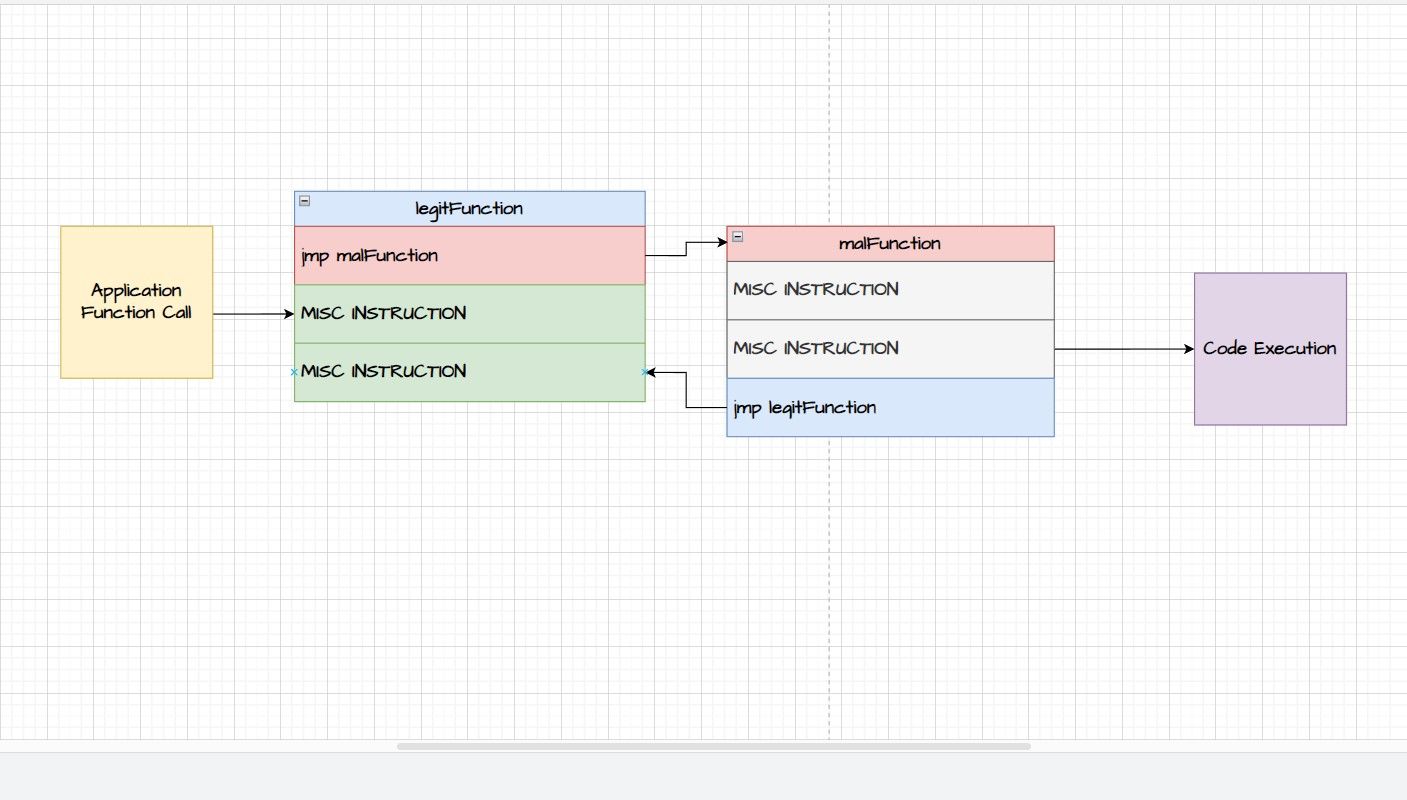
Inline hooking is a DLL hooking technique that involves altering a target function's source code in order to direct its execution to a special function. Inline Hooking, as opposed to IAT hooking, alters the target function's code directly, giving the attacker more precise control over how the target function behaves.
In the diagram above, observe how the legitimate function has been tampered with to point to a malicious function. Once all the instructions in the malicious function are executed, a jump instruction is made to return to the legitimate function for it to finish executing.
Adversaries employ inline hooking to make lasting changes to a program such as changing the parameters or the return value of a function.
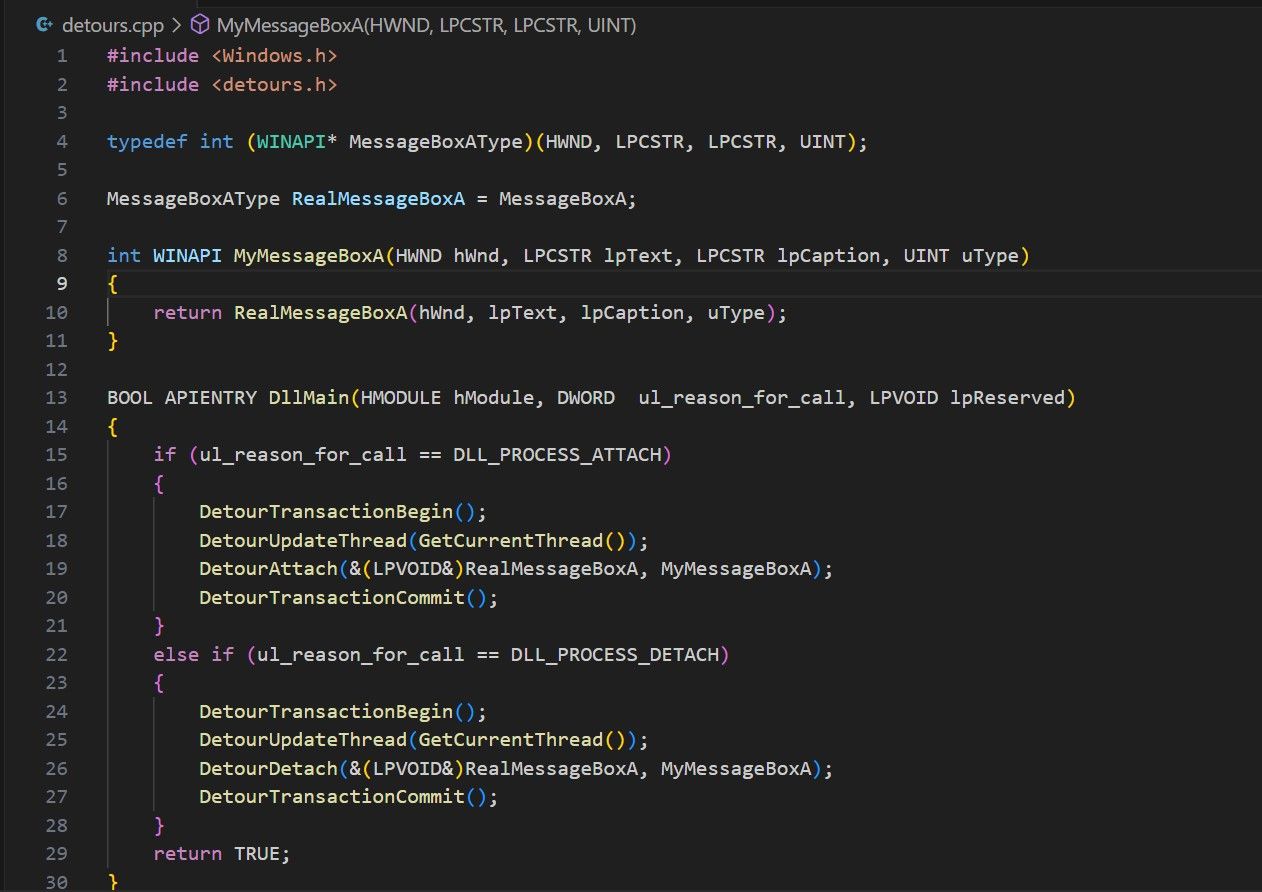
Microsoft Detours
Microsoft Research has developed an in-house DLL hooking package, Detours. It enables programmers to track and alter function calls made by a program. Detours can be used for a variety of tasks, including but not limited to: instrumentation, testing, and bug fixing.
Adversaries utilize Detours to carry out DLL injection and hooking attacks, and developers frequently use it to extend the functionality of their apps. You can learn more about the Detours package on the official GitHub repository.
Now You Know How DLL Hooking Works
DLL hooking is a sophisticated technique that, when used for the right reasons, can boost the capabilities of your application or help you debug and optimize software. Unfortunately, hooking is more commonly seen in use as an adversarial technique rather than a development one. So, it's important that you adopt and adhere to the security best practices ensuring that your applications are safe and free from attacks like hooking and injection.