Since its inception, Babuk Locker’s ransomware code has proven to be highly effective. And despite the group recently announcing its retirement from ransomware-focused attacks, its growth as a cybercrime gang is far from over.
What Is Ransomware?
Understanding the Babuk Locker gang requires an understanding of what ransomware is.
Ransomware is a type of malware that targets the data of victims. It is leveraged by cyber attackers to deny victims access to their network data via encryption processes. After an attacker successfully leverages ransomware, the attacker uses the promise of a decryptor key to get victims to pay a ransom. Decryptor keys allow a victim’s encrypted files to become accessible. As a result, when ransomware denies a victim access to critical data, they are often willing to pay a ransom.
Since many targets of ransomware are willing to make payments to attackers, the frequency of ransomware attacks has exploded. According to statista.com, in 2020 alone, ransomware attacks were up 62 percent from the previous year.
Babuk’s Targets
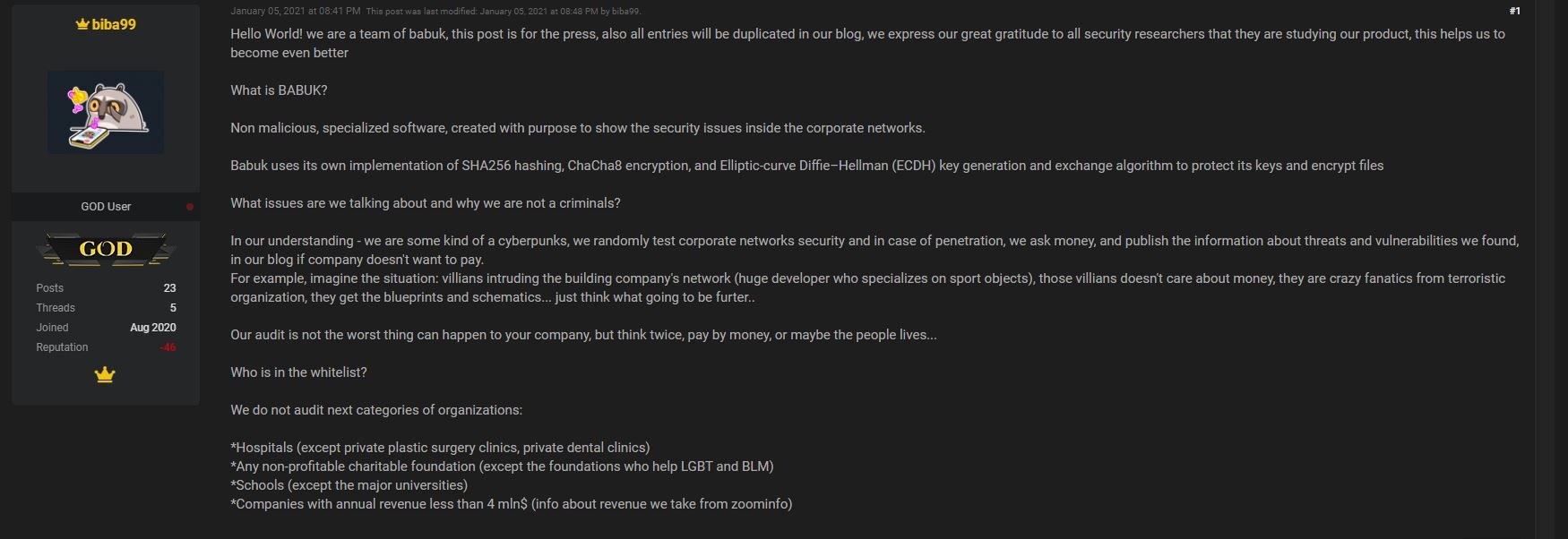
According to a self-published post from Babuk Locker at raidforum.com (username biba99), Babuk does not target hospitals, non-profits, small universities/colleges, or companies whose annual revenue is less than $4 million.
Although this policy offers some assurance for small business owners and organizations, it implies that the group is willing to target large enterprises and governmental organizations. So far, the organization has proven its willingness to attack governmental organizations. In April of 2021, they claimed responsibility for an attack on the Washington D.C. Police network.
In addition to targeting large enterprises, Babuk Locker favors companies with ransomware insurance. After a successful attack is performed, the group will ask targets if they have ransomware insurance. Presumably, the presence of ransomware insurance allows the group to command a higher ransom price.
How Does Babuk Locker Ransomware Spread?
Babuk Locker makes its entrance into networks via internet-facing hosts that have accounts with high administrative privileges. After the initial entrance to a network, it is evident that Babuk does not immediately encrypt a target’s files.
Babuk often releases sensitive file information from its targets. This means that before an encryption payload, Babuk Locker sorts through a target’s files to extract valuable information for later use.
Executing the Payload
When the Babuk Locker ransomware payload is executed, it starts by suspending the services and processes that would hinder the code’s ability to encrypt data. Services and processes associated with backup programs, virus scanning programs, etc., are terminated before data encryption begins.
After necessary services and processes are terminated, the code then determines the disk type of the host target. Determining a host’s disk type allows the location of data sources to be discovered and increases the reach of the ransomware code.
When the location of data has been determined on a target host, the files within a host’s directories are queried. To ensure that a target will retain internet and network access, certain files are excluded from encryption while others are appended with a .babyk extension.
Once all necessary files in a directory have been encrypted, a text (.txt) file is created that contains a note for the target. The file also includes directions for the target to make contact with the group. After a target makes contact with the organization, Babuk Locker proves good faith by preemptively decrypting a few of the target’s files. Then the group outlines its payment demands, often requiring payment in the form of Bitcoin.
Ransomware as a Service
The Babuk Locker gang utilizes Ransomware as a Service (RaaS) attack strategies. RaaS products operate similarly to SaaS (Software as a Service) products. With SaaS products, a company leases access to a legitimate software product.
The company is then able to use the software without the responsibility of managing it. The profitability and ease of the SaaS model have led to its appropriation by ransomware gangs. In exchange for access to ransomware developers’ code, affiliate attackers pay an initial access fee and a percentage of their ransom profits to ransomware gangs.
The financial and safety benefits of a RaaS model helps to explain why threat actors, such as Babuk Locker, initiate attack campaigns. When Babuk Locker performs a successful attack, affiliate attackers are willing to purchase Babuk’s ransomware kits. In addition, when the purchasers of Babuk’s ransomware kits perform successful attacks, Babuk receives a percentage of the profits without having to be responsible for the dirty work.
A Change in Babuk Locker’s RaaS Model
Still, Babuk Locker may lack the ability to profit from a RaaS model. According to Emisoft, Babuk’s decryptor key damages files in a VMware ESXi environment. Babuk’s decryptor does not contain a mechanism to detect if a file is encrypted. This results in unencrypted files being decrypted, causing total file loss.
Without an effective decryptor for Babuk’s ransomware code, organizations would not be willing to pay a ransom fee. In other words, Babuk Locker’s decryptor bug would make it ineffective for affiliate attackers to use.
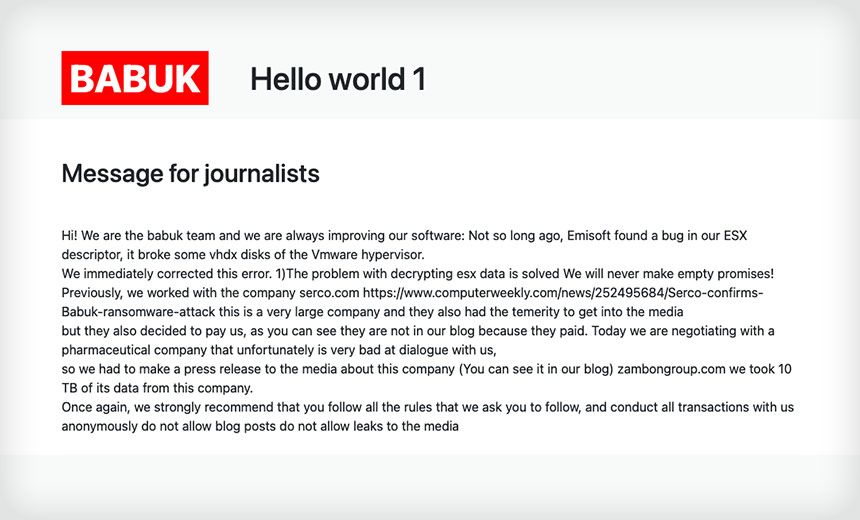
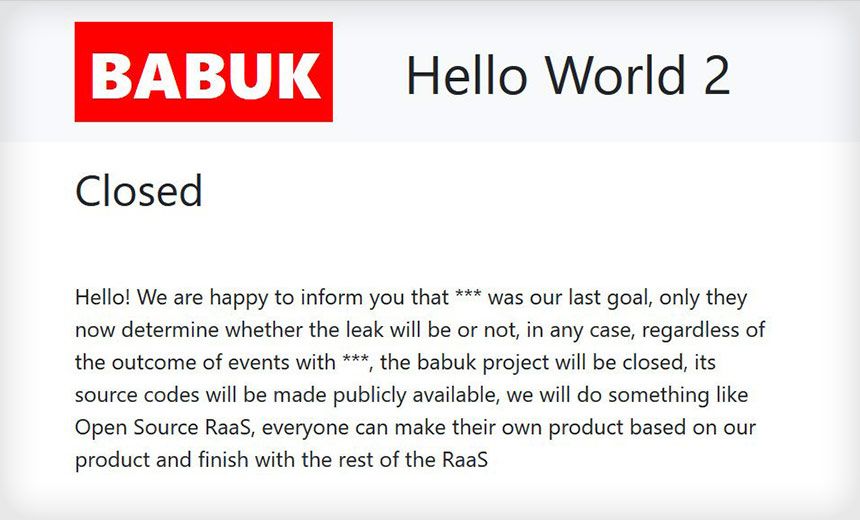
In addition to a failed decryptor, Babuk’s decision to use its code to attack a high-profile target, the Washington, D.C. Police Department, has brought heavy attention to its code and organization. This may explain why the group has recently announced its intention to move away from a RaaS model.
On the group’s Tor site, it announced its intention to end the group’s affiliate attacker program and make its ransomware openly available. The group will move its business model to a new form of data extortion. Instead of encrypting organizations’ files, the group will steal data and force companies to pay for the data to not be released.
Preventing a Babuk Locker Attack
Preventing a Babuk Locker attack requires organizations to align with general ransomware prevention best practices. Some best practices are: limiting the likelihood of account compromises, encrypting sensitive data, network segmentation, and robust patching. In addition, when able, organizations should avoid paying ransomware gangs.
Even when a ransom payment is made, there is no guarantee that the decryptors provided by an attacker will restore an organization’s files.