As a Linux novice user, you learn about the permissions and ownership associated with the file and directories. Linux/Unix-like operating systems allow you to set a combination of nine bits permissions to prevent other users from unnecessary files/directory access. Similar to these are special permissions for executable files known as set UID, set GID, and sticky bits.
Understanding special permissions can be a bit overwhelming for aspiring Linux administrators. Here you'll learn a little background on the regular file permissions and explains how they differ from special permissions. We also demonstrate SetID, GetID, and sticky bits functionality with examples for a comprehensive understanding.
Regular Linux File Permissions
Linux uses the chmod command to assign/change read (r=4), write (w=2), and execute (x=1) permissions on files and folders. That is to say, the nine bits mentioned above apply to the three main categories of permission groups. The first three are for the user who owns the file, the second set is for the group assigned to the file/directory, and the last three represent all other users.
For instance, a regular file will all types of permissions for all categories of users will appear as -rwxrwxrwx. While - in replace of letters represent the absence of that permission. Now chmod command uses numbers and letters to change permissions as follows:
sudo chmod 755 file #for rwxr-xr-x
sudo chmod 644 file #for rw-r--r--
sudo chmod a-w file #for r-xr-xr-x
sudo chmod a+x file #for --x--x--x
Special Linux File Permissions
The setuid bit represents permission on an executable file that can be run by other users with the owner's authorization. For instance, when the user max runs the vi command as the user john, you will have the read/write permissions of john.
To identify files with setuid, use the ls command and look for the s bit in place of the executable bit x, as follows.
Set UID Bit
The setuid bit represents permission on an executable file that can be run by other users with the owner's authorization. For instance, when the user max runs the vi command as the root, he will have the read/write permissions of the root. To identify files with setuid, use the ls command and look for the s bit in place of the execute bit x, as follows:
ls -la /etc/passwd
-rwsr-xr-x 1 root root 88464 Dec 14 12:46 passwd
Some other examples are:
ls -la /bin/gpasswd
-rwsr-xr-x 1 root root 88464 Jul 14 15:08 gpasswd
ls -la /bin/su
-rwsr-xr-x 1 root root 67816 Jul 21 2020 su
ls -la /newgrp
-rwsr-xr-x 1 root root 44784 Jul 14 15:08 newgrp
ls -la /bin/sudo
-rwsr-xr-x 1 root root 166056 Jan 19 2021 sudo
To set the setuid bit for executable files, use the chmod command as follows:
chmod u+s /etc/passwd
To remove the permission to execute the files from non-root users or owners:
chmod u-s /etc/passwd
Set GID Bit
As discussed, the set uid bit controls file access to other users, while the setgid (GID) bit creates collaborative directories. That means any file created inside that directory is accessible to the directory's group. Hence, it allows all group members to run executable files without the owner's privileges and protects them from other users.
Follow these steps to create a collaborative directory in your Linux system:
Create a group using the groupadd command with group id 415 for collaboration:
groupadd -g 415 admins
Use the usermod command to add john to the group for file access/execution.
usermod -aG admins john
Use the mkdir command to create a directory:
mkdir /tmp/collaborative_dir
Use the chgrp command to assign the directory to the admins group:
chgrp admins /tmp/collaborative_dir
Use the chmod command to change directory permission to 2775. The 2 bit turns on the set gid, 7 to assign full rwx to the user and group, while 5 (r-w) for others.
chmod 2775 /tmp/collaborative_dir
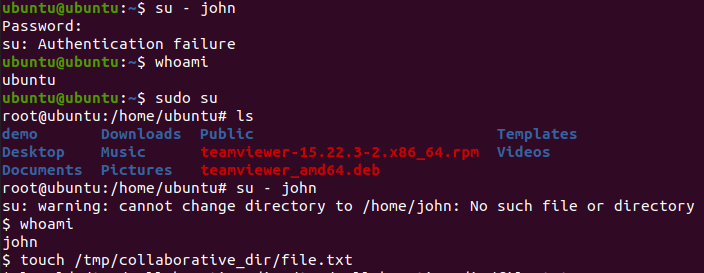
Lastly, change your user account to john and create a file in the collaborative directory to check file permissions.
su - john
touch /tmp/collaborative_dir/file.txt
The su command may give you an authentication error. In this case, type the sudo su command to switch to the root and rerun su - john to change the user account
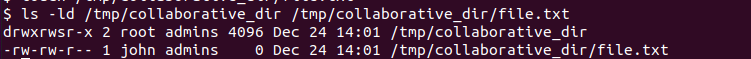
Now list the permissions to check the GID bit (s )set for the directory and newly created file.
ls -ld /tmp/collaborative_dir /tmp/collaborative_dir/file.txt
In a typical scenario, a file created by john will have a group john assigned to it. Since you create the file inside a set GID bit directory, it assigns permissions to the admins group, such that anyone who belongs to the group, like the user chris, will have access to it.
Sticky Bits
Unlike SID and GID bits, sticky bits differ in functionality as it protects files and directories from renaming and deletion by other users. Regular file permission allows any user with the write access to delete or rename the file. Whereas with the sticky bit set, it is not possible unless you are the root user or owner of the file.
The ideal case scenario for using sticky bits is the directory accessible to all users for file creation. For instance, use the ls -ld command to check the \tmp directory permissions, as follows:
You can notice that the sticky bit t replaces the execute bit x. Follow the given set of instructions to create a restricted deletion directory:
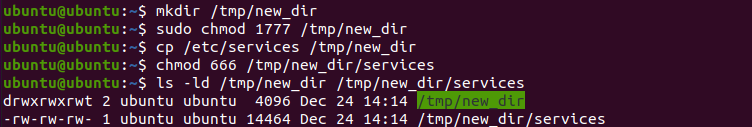
Now create another directory in the /tmp folder:
mkdir /tmp/new_dir
Change the file permissions to 1777 to set the sticky bit (t) and full directory access:
chmod 1777 /tmp/new_dir
Now copy any file from the /etc folder to /tmp/new_dir and change its permissions to 666:
cp /etc/ /tmp/new_dir
chmod 666 /tmp/new_dir/services
List the directory and all its content to view permissions:
ls -ld /tmp/new_dir /tmp/new_dir/services
You can notice the sticky bit instead of the execute bit, which means only the root or the user john can delete the file, as the file is inside the sticky bit directory.
Understanding Special File Permissions in Linux
The article demonstrates how to set these bits to improve collaboration over shared files and directories and protect them from unauthorized access, execution, and deletion. Even if you don't create files/directories with these bits, understanding special file permissions is helpful in many situations, especially in troubleshooting or as a system admin. Whereas, unwise usage of these bits can cause various security vulnerabilities.