CPU protection rings are structural layers that limit interaction between installed applications on a computer and core processes. They typically range from the outermost layer, which is Ring 3, to the innermost layer, which is Ring 0, also referred to as the kernel.
Ring 0 is at the core of all system processes. Anyone who can control the kernel can basically control all aspects of a computer. To prevent abuse of this core, computer system architects limit interaction to this zone. As such, most processes that can be accessed by a computer user are limited to Ring 3. So how do privilege rings work?
How the Privilege Rings Interact
Ring 0 processes operate in supervisor mode and so do not require any user input. Interfering with them could cause major system errors and unresolvable security issues. This is why they are deliberately designed to be inaccessible to computer users.
Let's take Windows as an example: access to Ring 0 by Ring 3 processes is restricted to a few data instructions. To access the kernel, applications in Ring 3 have to make a connection that is handled by virtualized memory. Even then, very few applications are allowed to do this.
They include browsers that require network access and cameras that need to make a network connection. Additionally, these data calls are insulated to prevent them from directly interfering with vital system processes.
Some earlier Windows versions (like Windows 95/98) had less shielding between privilege Rings. This is among the main reasons why they were so unstable and prone to errors. In modern systems, kernel memory security is reinforced by specialized hardware chips.
Current Windows Kernel Memory Protections Against Intrusions
Microsoft introduced formidable protections to kernel memory starting from Windows 10 version 1803.
Among the most notable was Kernel DMA Protection; the holistic feature was designed to protect personal computers against Direct Memory Access (DMA) attacks, particularly those implemented via PCI hot plugs. Protection coverage was expanded in build 1903 to cover internal PCIe ports such as M.2 slots.
One of the main reasons Microsoft chose to provide additional protections to these sectors is because PCI devices are already DMA-capable out of the box. This capability allows them to read and write onto system memory without requiring system processor permissions. This property is among the main reasons why PCI devices have a high performance.
The Nuances of DMA Protection Processes
Windows utilizes Input/Output Memory Management Unit (IOMMU) protocols to block unauthorized peripherals from performing DMA operations. There are, however, exceptions to the rule if their drivers support memory isolation executed using DMA Remapping.
That said, additional permissions are still required. Typically, the OS administrator will be prompted to provide DMA authorization. To further modify and automate related processes, DmaGuard MDM policies can be changed by IT specialists to determine how incompatible DMA Remapping drivers will be handled.
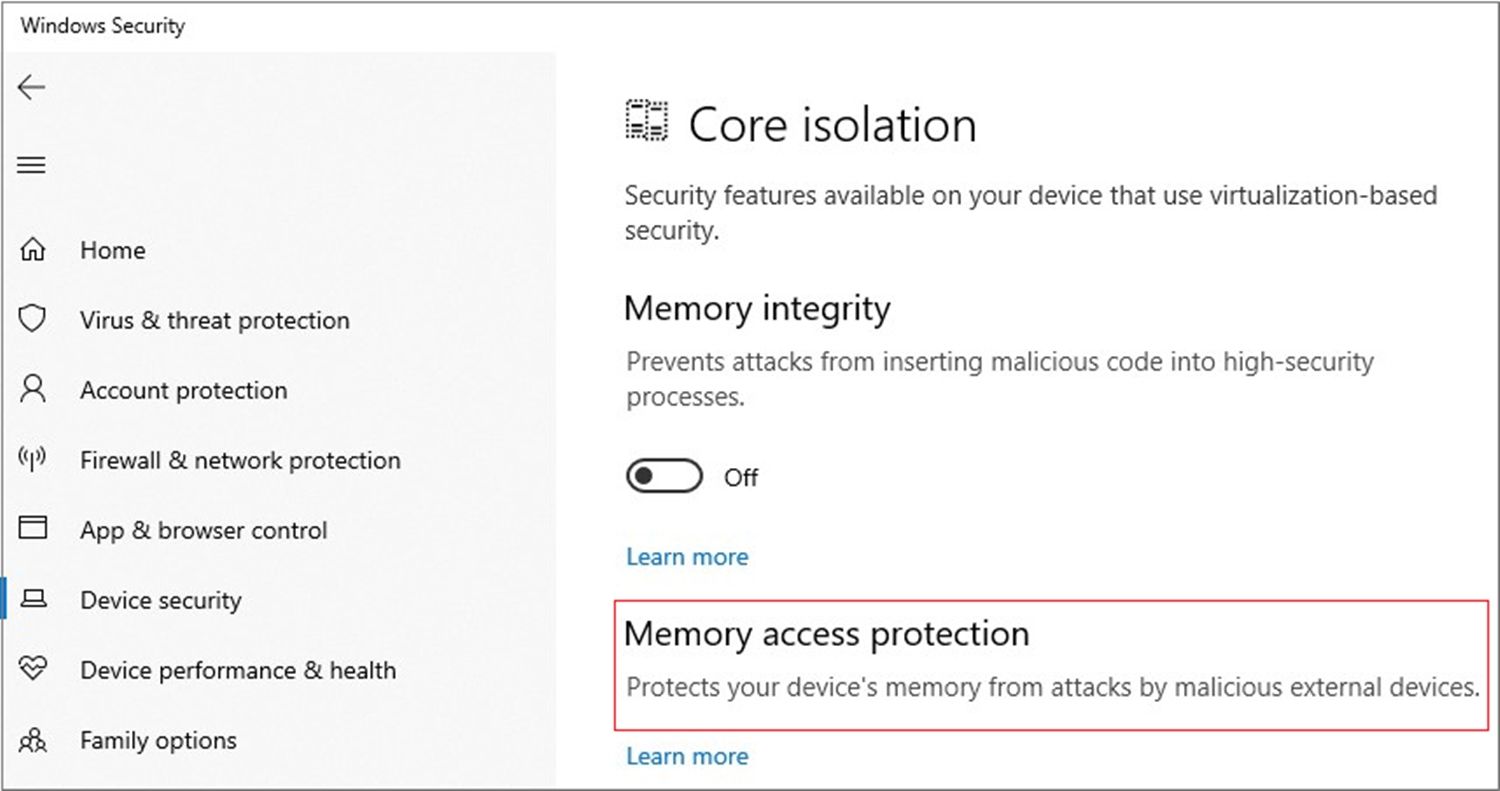
To check if your system has Kernel DMA Protection in place, use Security Center and view the settings in Core Isolation Details under Memory Access Protection. It is important to note that only operating systems released later than Windows 10 version 1803 have this feature.
Why CPUs Rarely Rely on Ring 1 and 2 Privileges
Rings 1 and 2 are largely used by drivers and guest operating systems. Most of the code in these privilege levels have also been semi-repurposed. As such, the majority of contemporary Windows programs operate as if the system has only two levels—the kernel and user levels.
That said, virtualization applications such as VirtualBox and Virtual Machine utilize Ring 1 to operate.
A Last Word on Privileges
The multiple privilege rings design came about due to x86 system architecture. It is, however, inconvenient to use all Ring privilege levels all the time. This would lead to increased latency and compatibility issues.