Scammers and cybercriminals are constantly searching for ways to compromise your security, hack into your accounts, and drain your hard-earned savings into their own coffers. You need to take every precaution to protect your personal information—both online, and in the digital world. This includes your email address, with which ne'er-do-wells can accomplish an awful lot.
So what can a cybercriminal do with just your email address?
Are Scammers Really After My Email Address?
Yes, they are. On August 16th 2022, cloud storage provider DigitalOcean was forced to disclose a data breach and contact all of its customers with the news that, "a number of DigitalOcean customer email addresses may have been viewed by an unauthorized individual."
Email data breaches are a fairly common occurrence. Sometimes, physical addresses and passwords or hashes of passwords are leaked alongside the email address. Even if no other information is disclosed, a valid email address can provide multiple opportunities for scammers to take advantage of you. Here's how...
1. Leaks Show Email Addresses Are in Use
There is a practically unlimited number of possible email addresses. If Gmail were the only email provider in the world, its 30 character username limit means that there are 30 ^ 36 or 30 undecillion possible combinations. Other providers have much higher limits, and the total number of email providers worldwide is unknown.
When scammers are looking for potential victims, sending out emails to random addresses isn't going to cut it. Most potential email addresses are unused, have never been used, and will never be used. They can improve the odds a little by including common words, phrases, and numbers in their efforts.
Verifying that an email address is actively being used saves scammers a lot of effort and money (sending bulk emails is not always cheap), which is why email addresses databases are bought and sold openly online. If your email address is exposed, you can, at the very least, expect to receive a significant increase in junk mail, spam, and phishing attempts.
2. Your Email Can Make You a Target for Spear Phishing
Spear Phishing is a term for a phishing attempt when the scammer tailors a phishing email for a specific recipient. The more the scammer knows about the target, the more successful the attempt is likely to be.
The DigitalOcean breach disclosure came as part of an attempt by scammers to target cryptocurrency users, according to Mailchimp. This, by itself, gives phony email users an angle of attack for spear phishing, and an incentive to try.
Further information about the target can be gleaned from the email address itself. Many people use their full names and year of birth as part of their email address, allowing an attacker even more insight which can be used against the victim.
Lastly, if your email address—or part of your email address—is a username for social media accounts (if your username is "yeezydave1992@420blaze.it" and your Twitter handle is "yeezydave1992", for instance), they will be able to look over all aspects of your life, your relationships, hobbies, musical tastes, and then sculpt an email to trap you.
3. Your Email Address Can Help Scammers Target Your Contacts
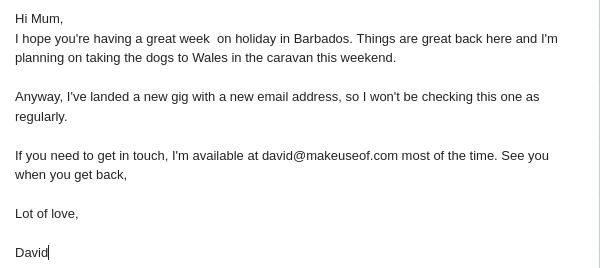
A little bit of research can reveal other people you may know: your mum, your boss, your clients. These are the people who might expect to receive an email from you and would not be unduly alarmed to find a message from your address in their inbox.
For example, one might say that you now consider the address "yeezydave1992@gmail.com" to be immature, and ask them to please contact you on the far more respectable "mrdavidyeezy@business.business". Or perhaps they could email a client stating that your banking details have changed and further asking them to send the next payment to a different account.
Spoofing an email is astonishingly easy and can be accomplished in about five minutes with Telnet. In our experience, each email sent this way has about a 20 percent chance of making it through Gmail's first level spam filters. The efficacy of other providers' defenses will vary.
4. Your Email Address Is Half Your Login
To gain access to your many and varied online accounts, in many cases an attacker will only need two pieces of information: an email address and a password. If they already have your email address, that means the only thing they need to know is your password.
When creating an account online, there are certain minimum requirements for password strength. These may include a minimum length, the use of capital and lower case letters, numbers, and symbols.
But passwords are difficult to remember—especially when you need to remember different ones for different services. The most common password in use today is "123456", with second place going to "123456789", and there are lists of common passwords circulating on the web, let alone the dark web.
All an attacker needs to do is match a common password with an already known email address. While we're not suggesting that your own password is weak, it may be worthwhile choosing a new, strong password to protect your account.
5. An Attacker Can Fake Your Email Address With Unicode
Spoofing an email address to fool acquaintances of the target is quick and easy to do, but has a low success rate, and emails replies will be seen by the person being impersonated. It is far better (from a criminal point of view) to create an email address which seems identical, but which is invisibly different. Not just subtly different but invisibly.
Consider the following two characters: "а" and "a". Do they look different to you? One is the Cyrillic character, "а", which is completely different to the Latin character, "a".
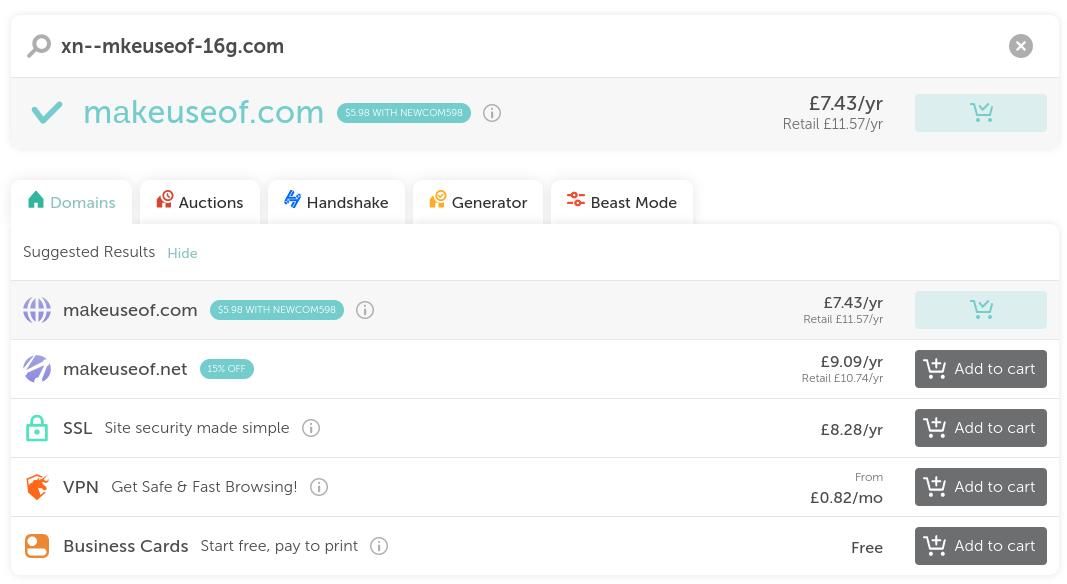
Unicode spoofing allows attackers—or other interested parties—to create a domain name which looks identical to a legitimate domain. Receiving an email from "david@makeuseof.com" is completely different to one from "david@mаkeuseof.com". Other easily spoofed characters include к, о, р, с, у, х.
An attacker who purchases that domain name will be able to send emails which appear to be from a legitimate source, and for which they can receive replies and correspond as if they were really a makeuseof.com staffer.
You shouldn't feel safe just because your email address is with a major provider, either. While some of the more obviously spoofable domains are no longer available, there are plenty of alternative top level domains for sale.
Yes, your email can be spoofed to successfully fool people, and it will cost an attacker less than $10.
Keep Your Email Address Hidden
You can't avoid giving out your email completely—it's there to be used, after all. But you should take care of your main email address, i.e. the one you use in conjunction with your bank and PayPal accounts is different from the ones you use for sign-ups and digital services.
Ideally, you should have a different email address to give out to every person or organization you have contact with. This will limit the damage if your email address is ever disclosed. If you don't have time for that, consider using aliases.