Optional alternative title: How to Use VeraCrypt’s Advanced Features to Protect Sensitive Data
Many security experts recommend using VeraCrypt to secure sensitive files. It's not hard to see why: VeraCrypt provides users with "military-grade" file encryption abilities. It's free, open-source, and available on all major desktop operating systems. Anyone can use VeraCrypt's basic functions for files that need safekeeping. But if you're looking to take file security to another level, then VeraCrypt can keep you covered with its many advanced features.
How to Encrypt External Drives or Partitions
Users typically create encrypted file containers with VeraCrypt. But the program also has the ability to encrypt entire drives and partitions. Windows users can encrypt their system drives and partitions.
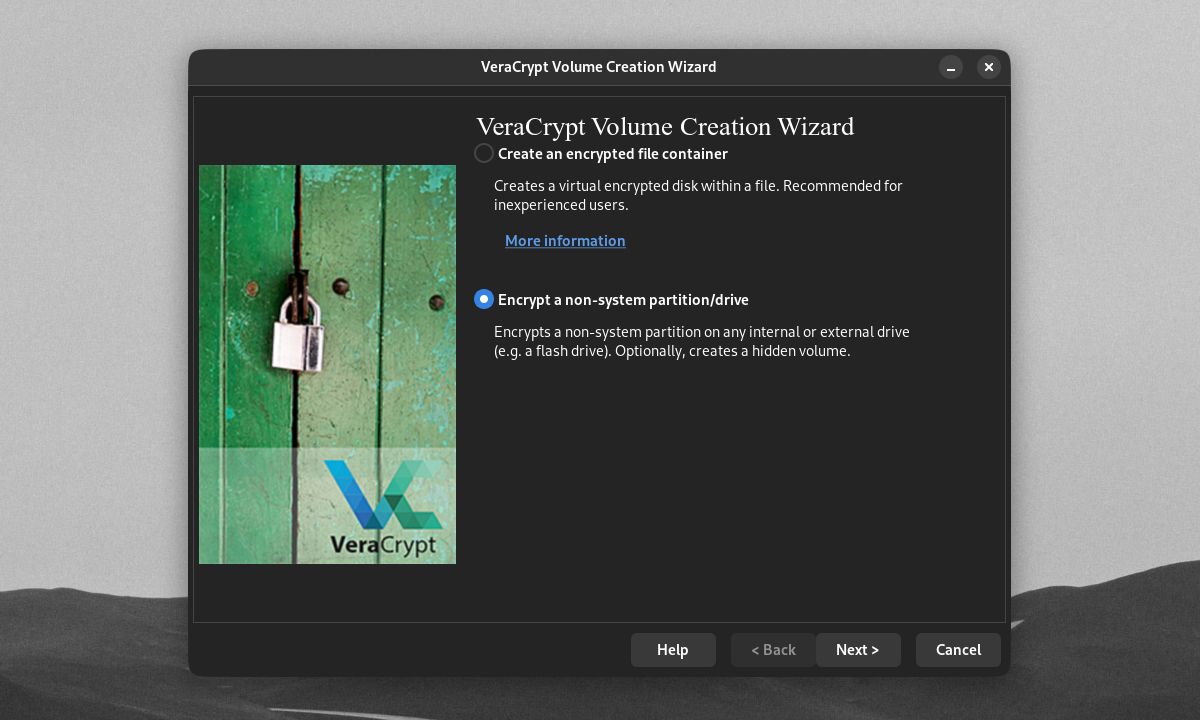
VeraCrypt users across all platforms can encrypt flash drives and other kinds of external drives too. In fact, it's one of the best programs for encrypting USB drives. To begin this process, open the VeraCrypt Volume Creation Wizard. Select Encrypt a non-system partition/drive and click Next.
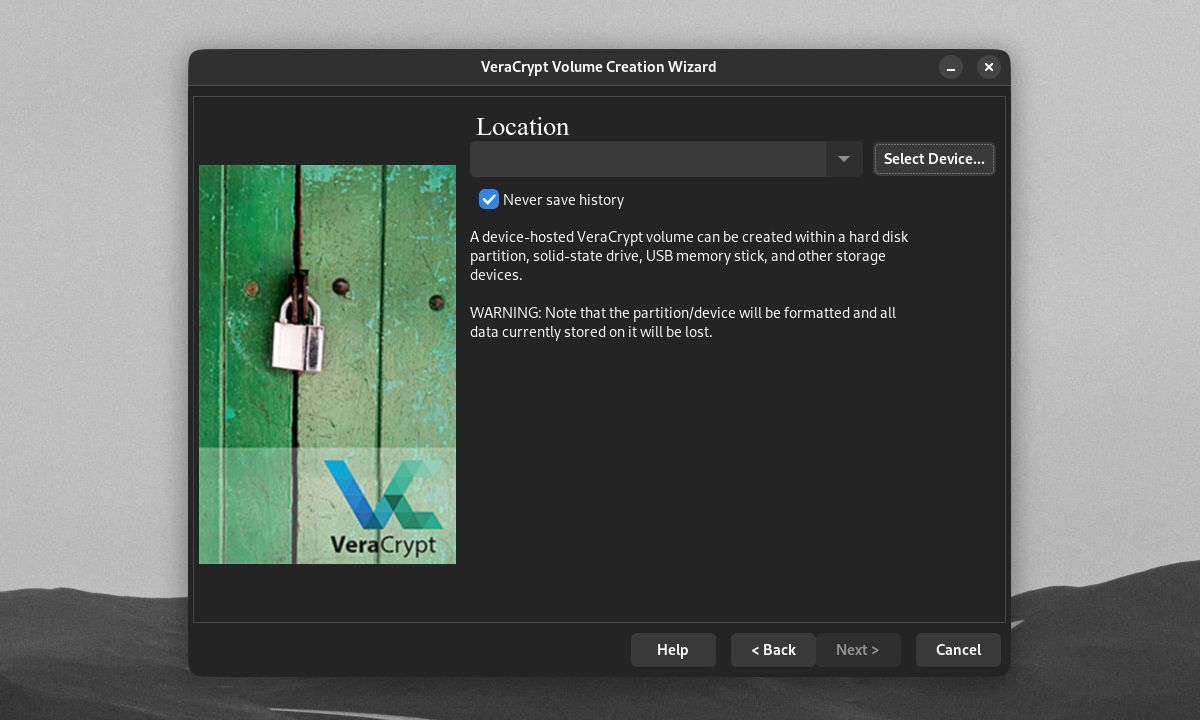
When choosing a location for your encrypted drive, VeraCrypt will prompt you to choose a device drive or partition. Click Select Device.
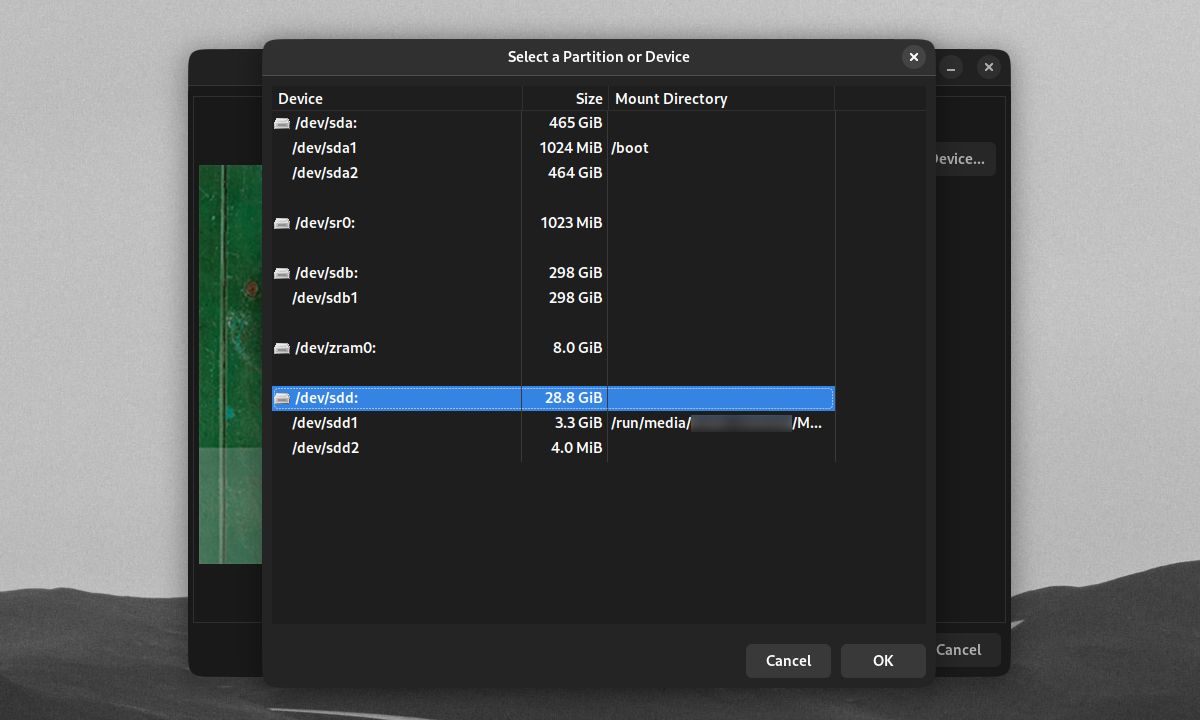
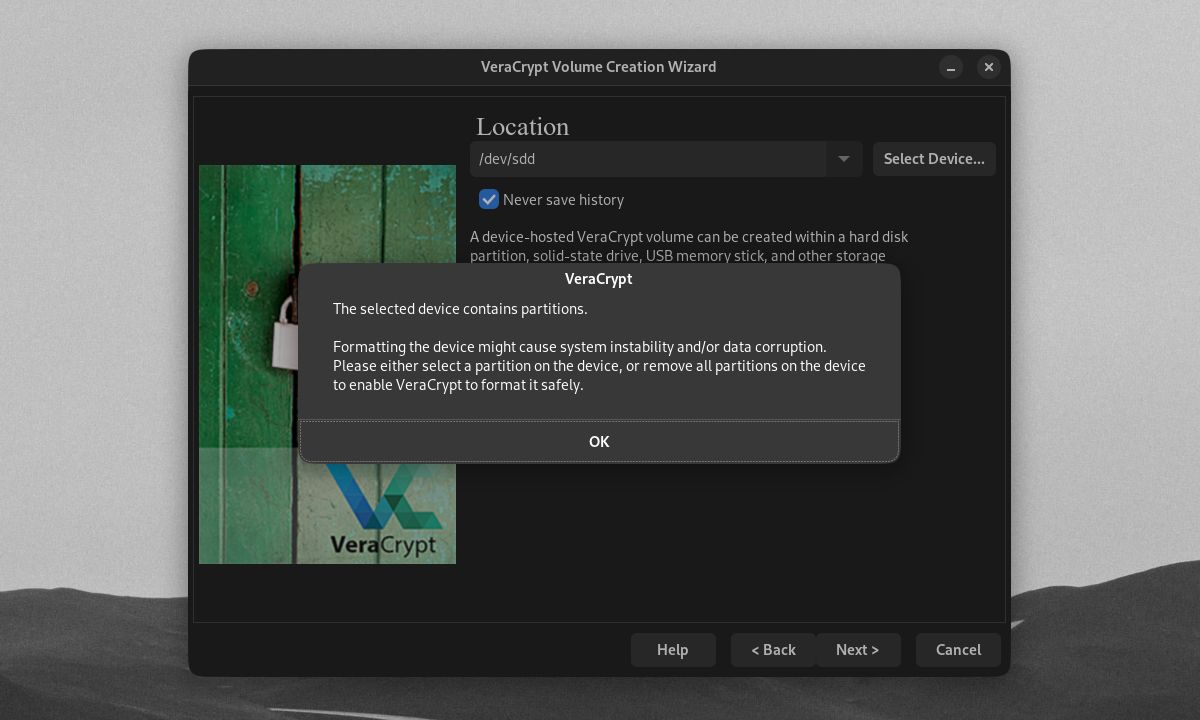
You have the option to select an entire non-system drive or a partition within the drive for encryption. You can opt to create multiple partitions in any external drive. Then, you can encrypt one partition while leaving the rest of the drive unencrypted. Click OK once you've selected a drive or partition to encrypt.
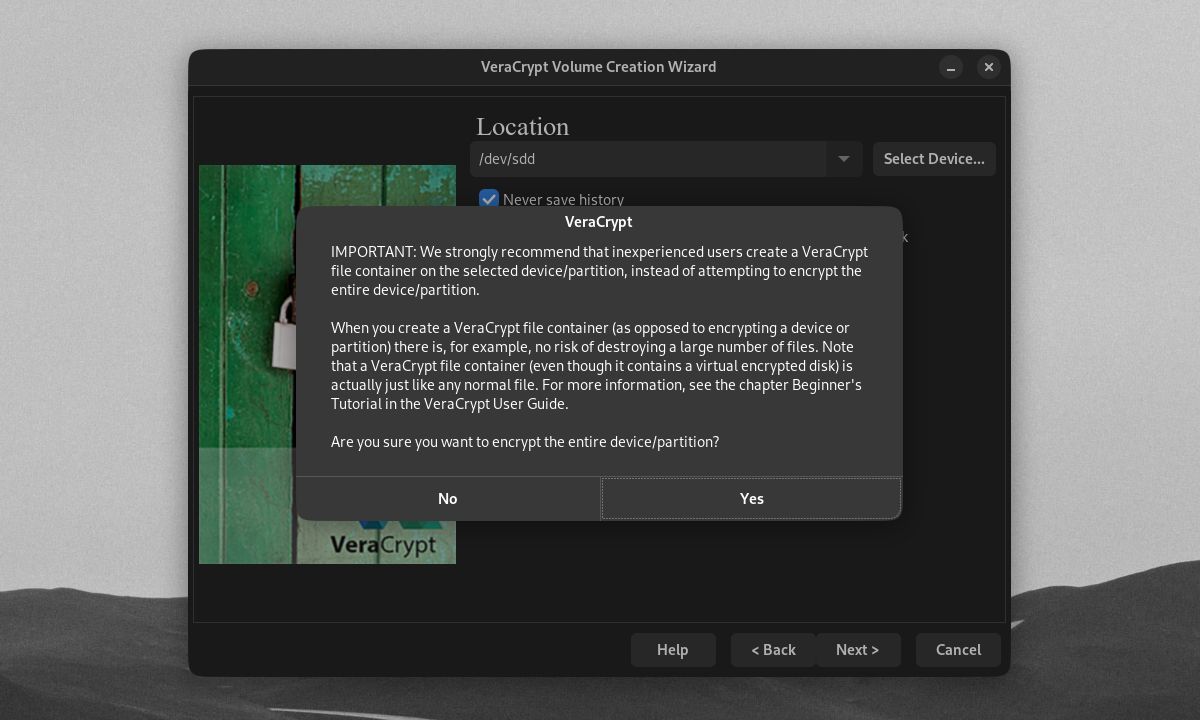
Be aware that any drive or partition you choose will have its data formatted, and its files destroyed.
Like any other files or drives, VeraCrypt is also vulnerable to unwanted data deletion or corruption. This is why you should always keep backups of your files.
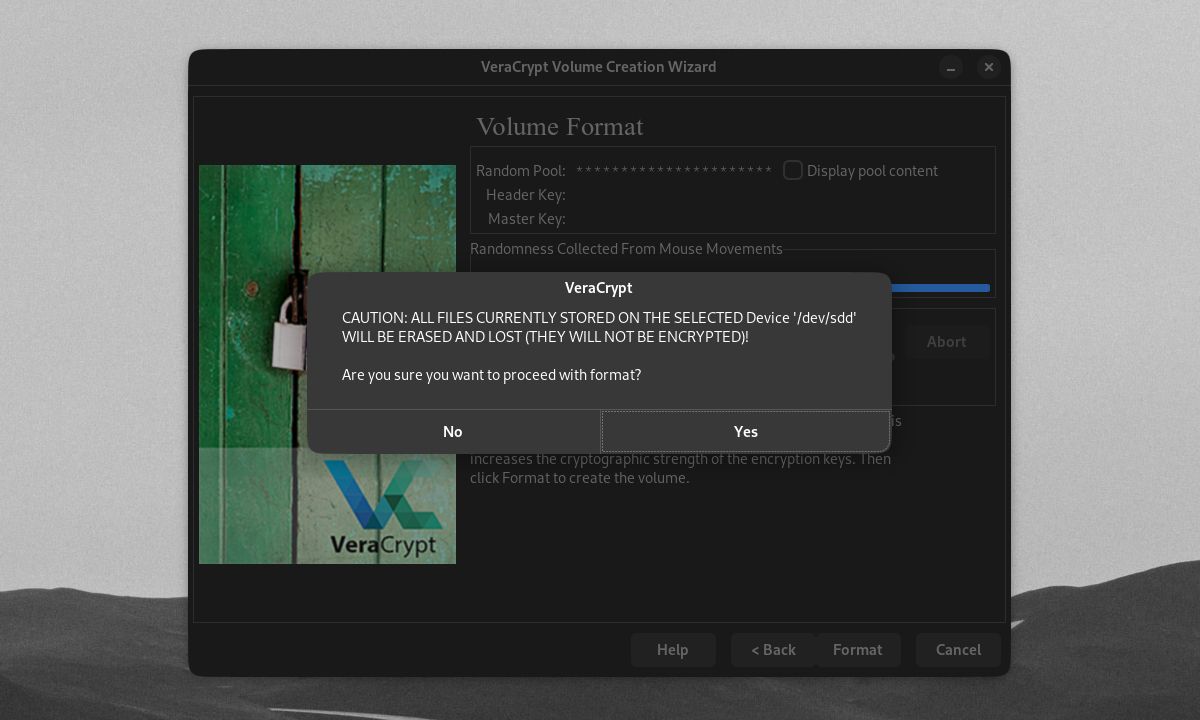
Only click Yes on the warning pop up if you're sure about encrypting your selected drive/encryption.
If you plan on encrypting a non-system drive with multiple partitions, make sure you format it to remove the partitions first. Click Next on the wizard.
As usual, VeraCrypt will prompt you to select the drive's encryption options, password, and file format. Click Format, then click Yes once you're ready to create your encrypted external drive.
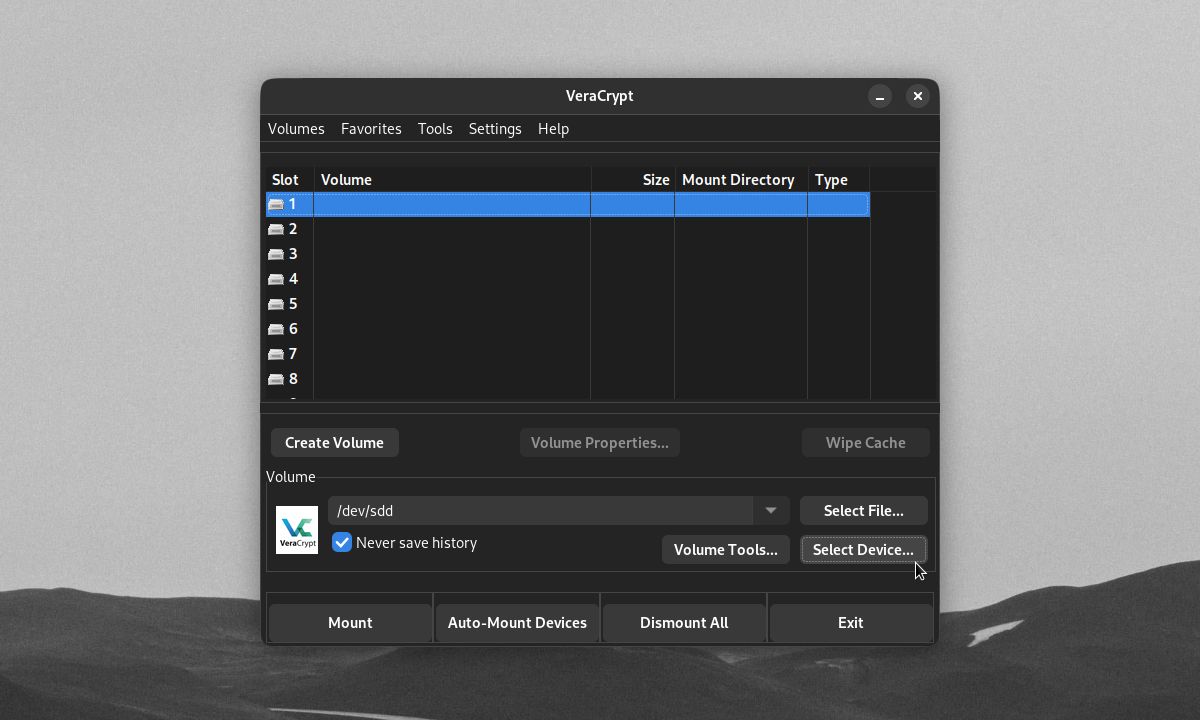
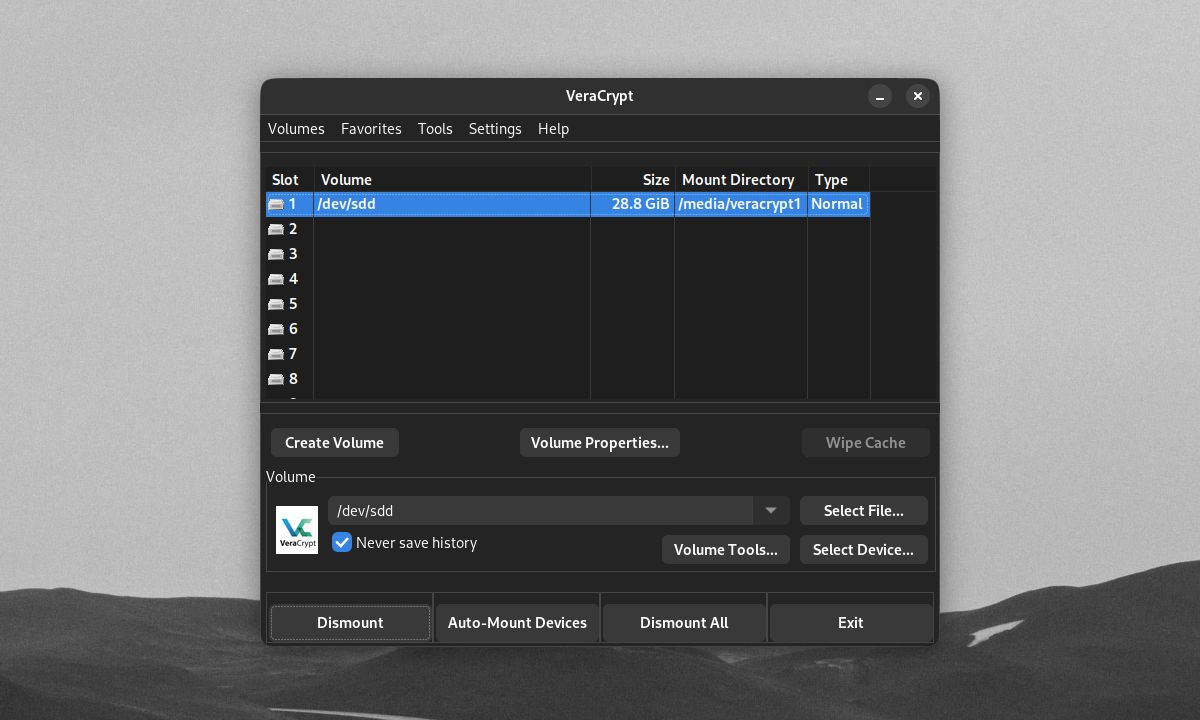
Once you've finished formatting your encrypted device, it will no longer be accessible outside VeraCrypt. To mount your encrypted device, select it with Select Device, click Mount, and enter your password.
You can use the encrypted device like any other VeraCrypt volume and dismount it as usual. To decrypt your device, format the drive/partition with your desktop's built-in disk management software.
How to Use More Safeguards for VeraCrypt Volumes
VeraCrypt's default volume setups paired with a strong password provide plenty of security for most users. But they may not be enough if you or your group or business is more vulnerable to certain threat actors. To make sure that your precious data is safe, VeraCrypt has even more features to render encrypted volumes impractical to crack.
Familiarize yourself with common encryption terms as we go through VeraCrypt's extra features.
Using Encryption and Hash Algorithms
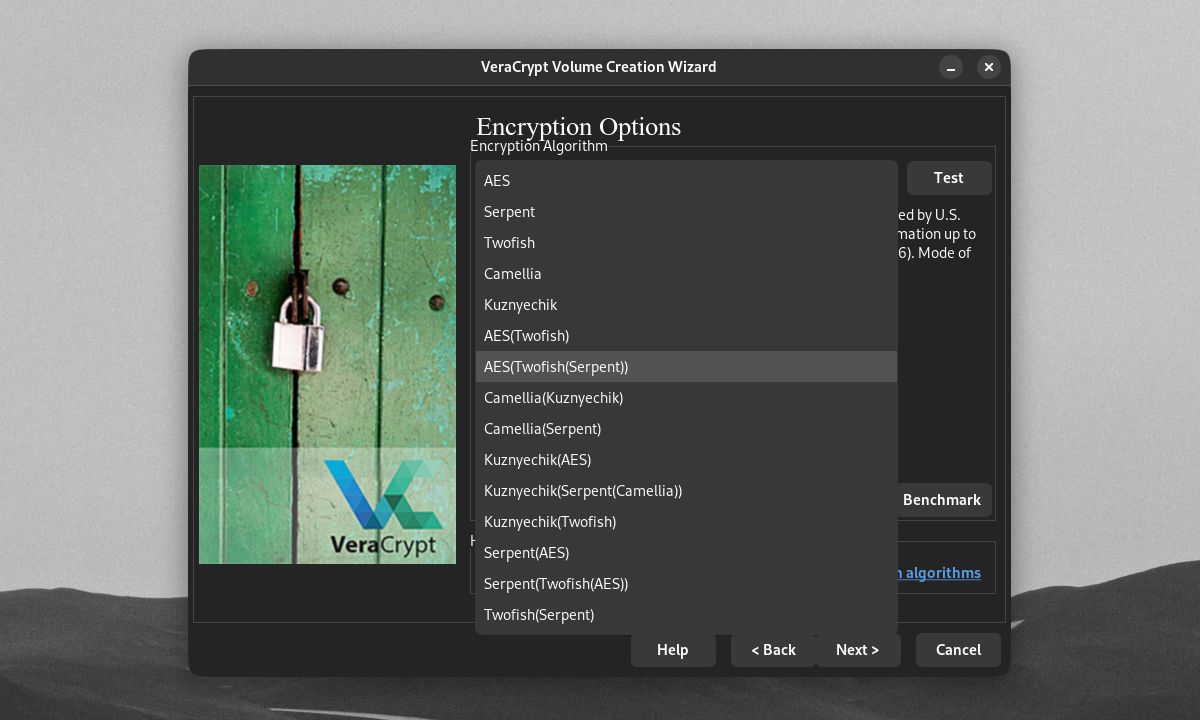
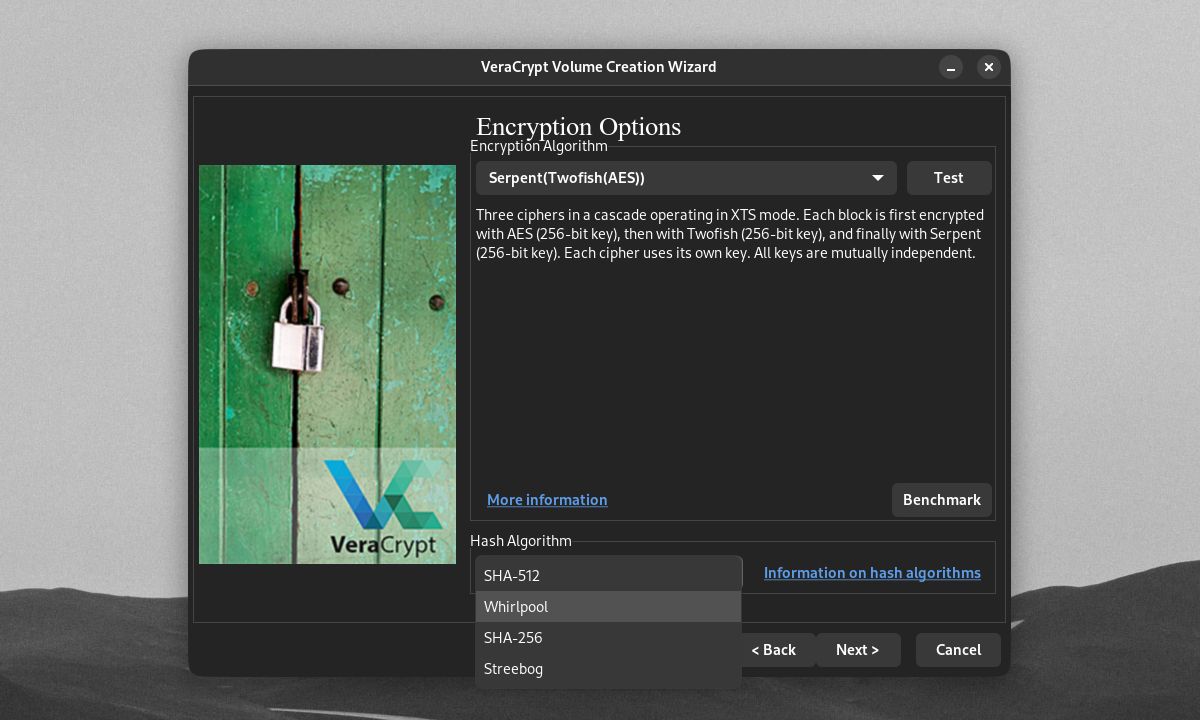
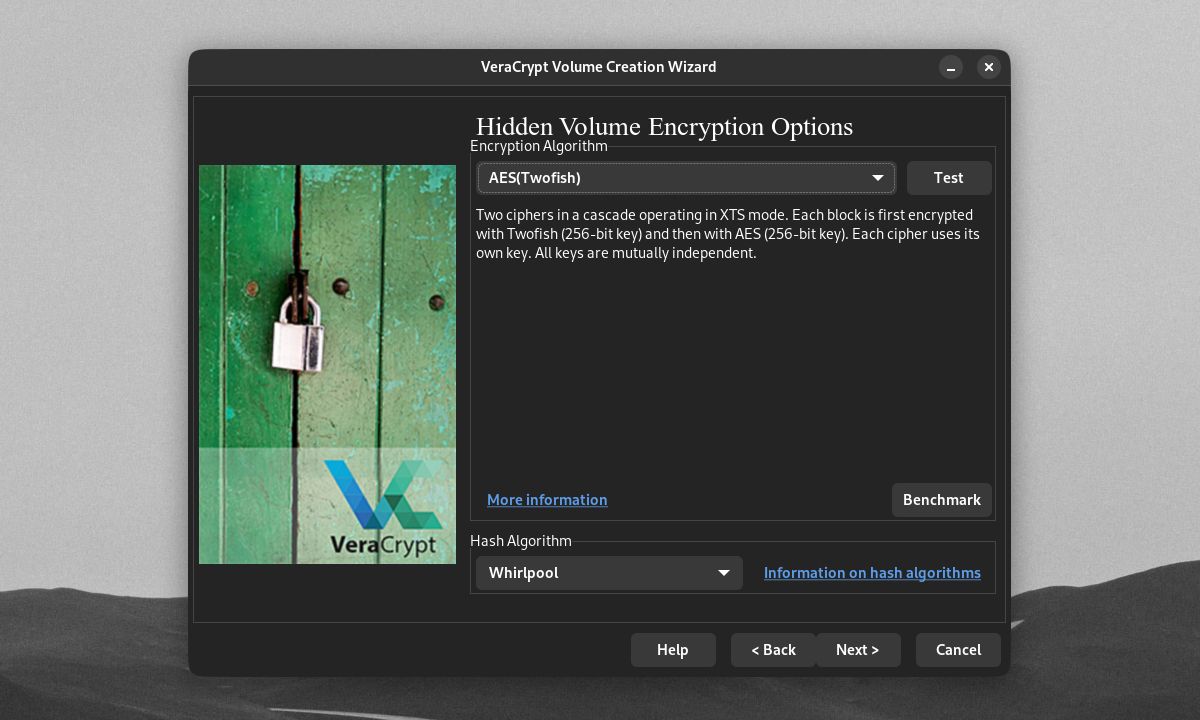
On the Volume Creation Wizard, you can choose between numerous options for encrypting and hashing your volume. The default AES algorithm is a common but secure type of encryption. But you're free to use other ciphers like Twofish and Serpent. You can even stack multiple algorithms on top of each other.
You can further choose the algorithm or method of hashing your password. The hash algorithm determines the way your password is converted into a hash that VeraCrypt can use to decrypt your volume. Using a strong hash method like SHA-512 or Whirlpool, together with a high PIM number, will slow down any brute-force attack on your volumes.
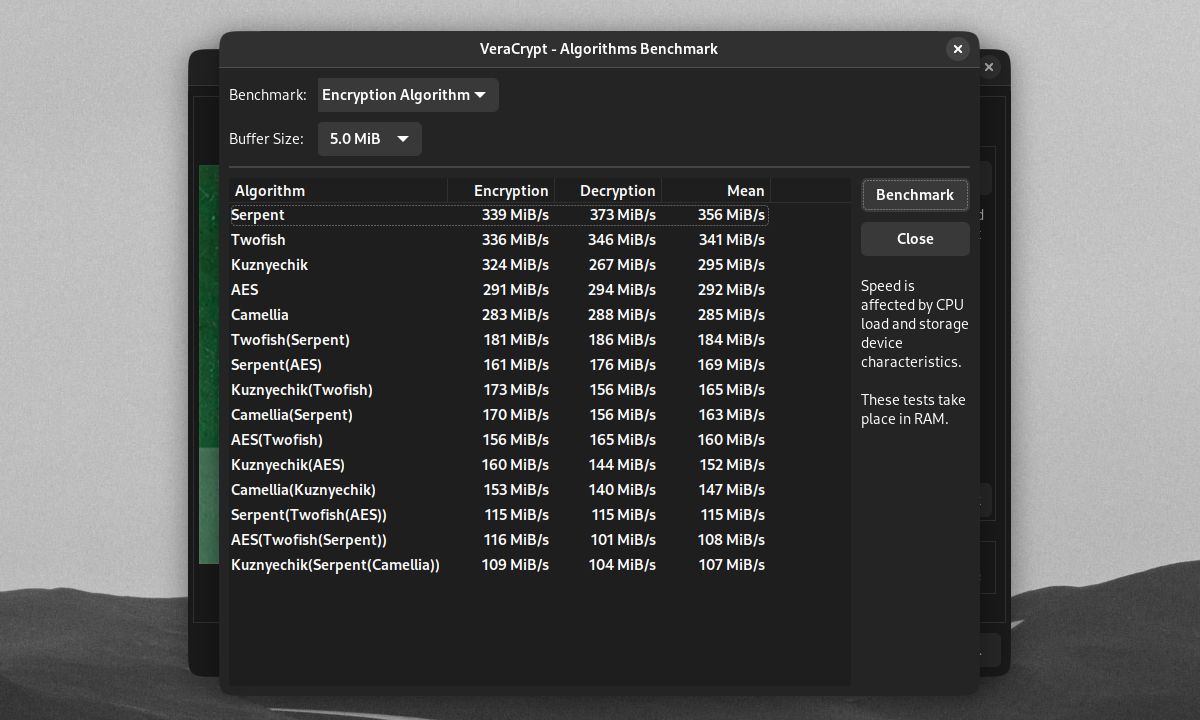
You can test the speed of the hash and encryption ciphers on your machine by clicking Benchmark. Faster encryption and hash times mean faster load times for your volume, but slower hash times mean better protection from brute-force attacks.
Using PIM Numbers
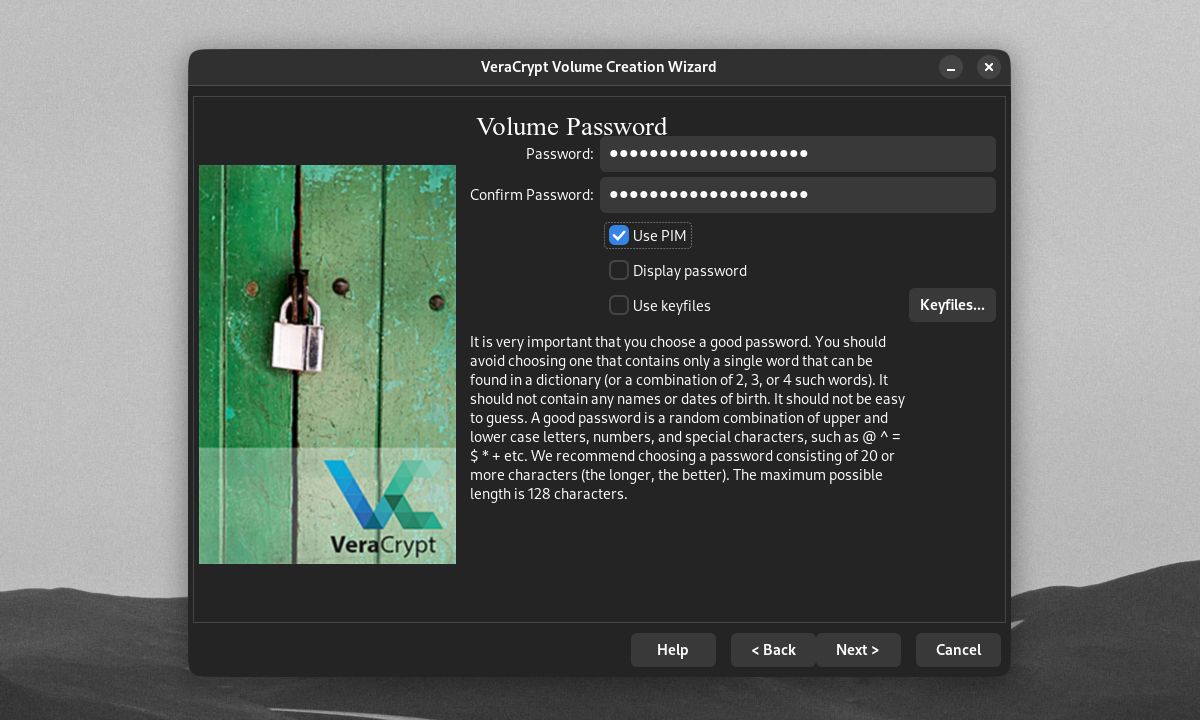
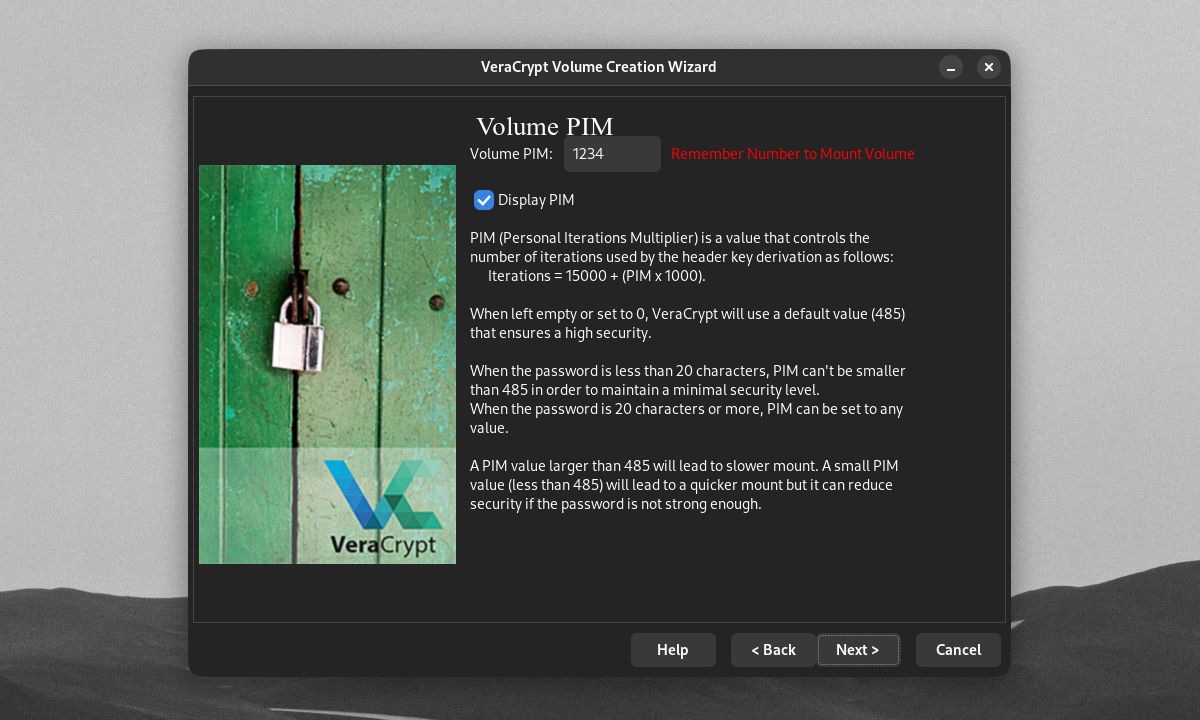
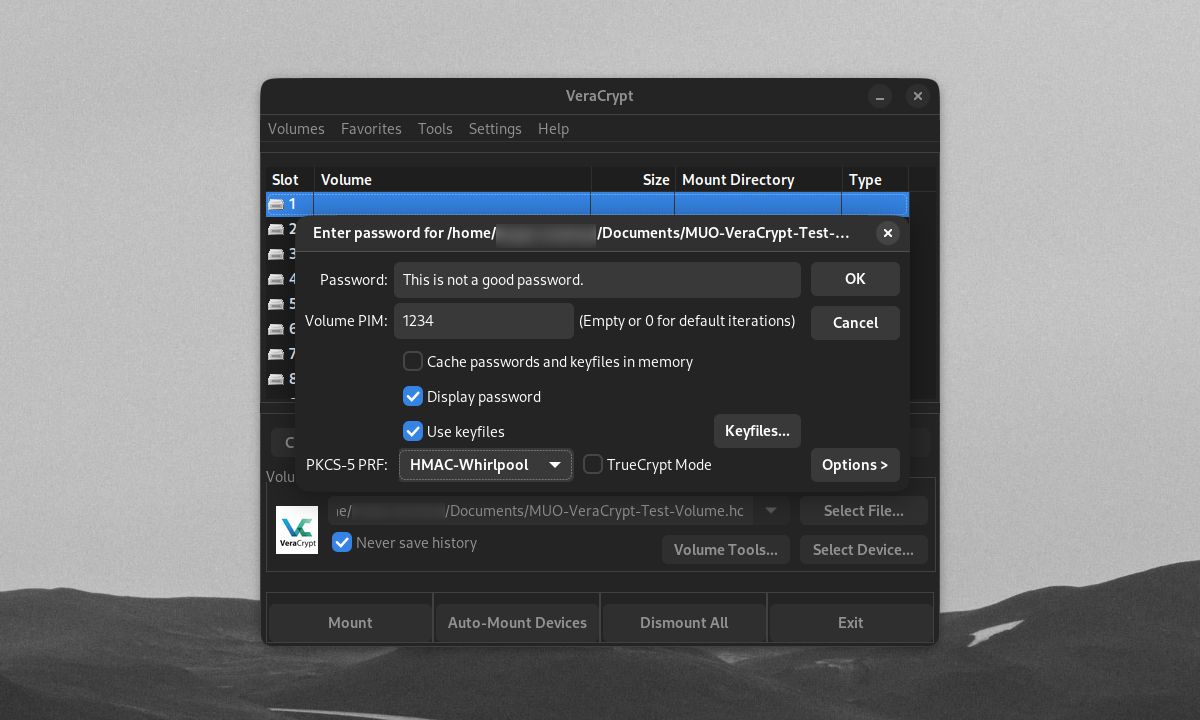
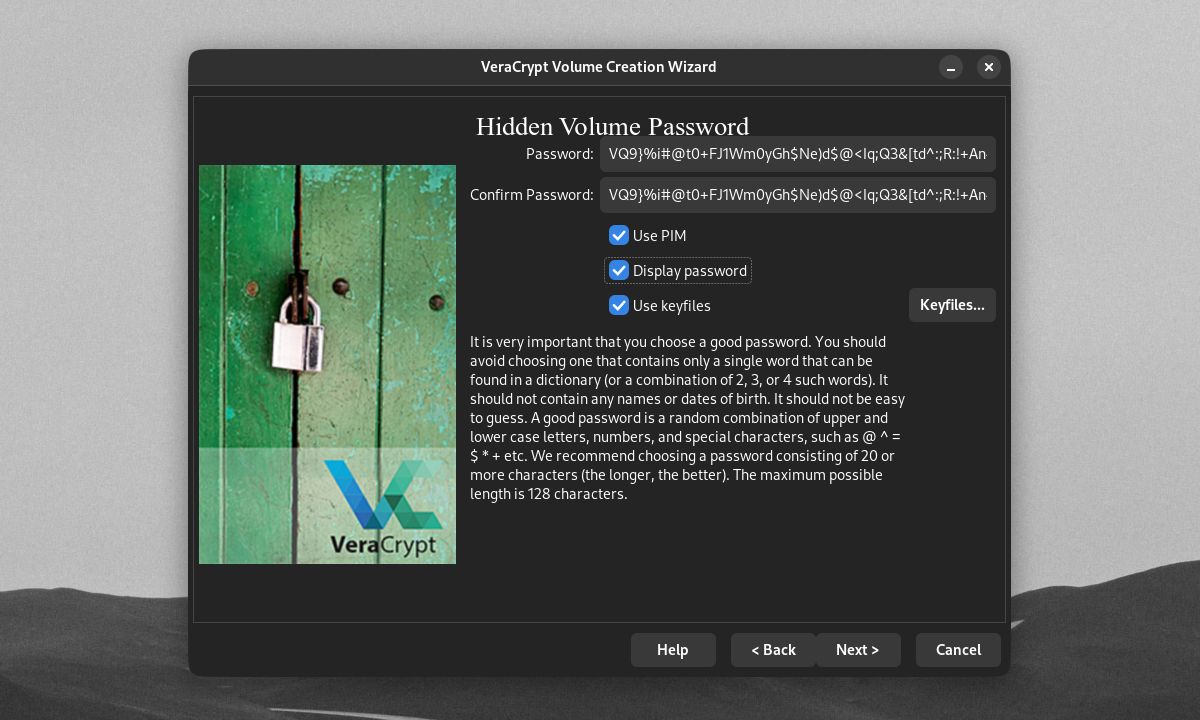
To set a Personal Iterations Multiplier (PIM) Number on your volume, tick the Use PIM checkbox on the Volume Password window. Clicking Next will bring you to the window where you can set your volume's PIM.
Your volume's PIM determines how many times VeraCrypt will need to hash your password from plain text. A default (SHA-512) VeraCrypt volume's password will be hashed 500,000 times. You can set an even higher volume PIM for better security.
Make sure you remember your volumes' PIM numbers if they aren't set to the default. Entering the wrong PIM number will lead to the wrong hash. VeraCrypt can't decrypt your volume with the wrong hash, even if your password is correct.
Using Keyfiles
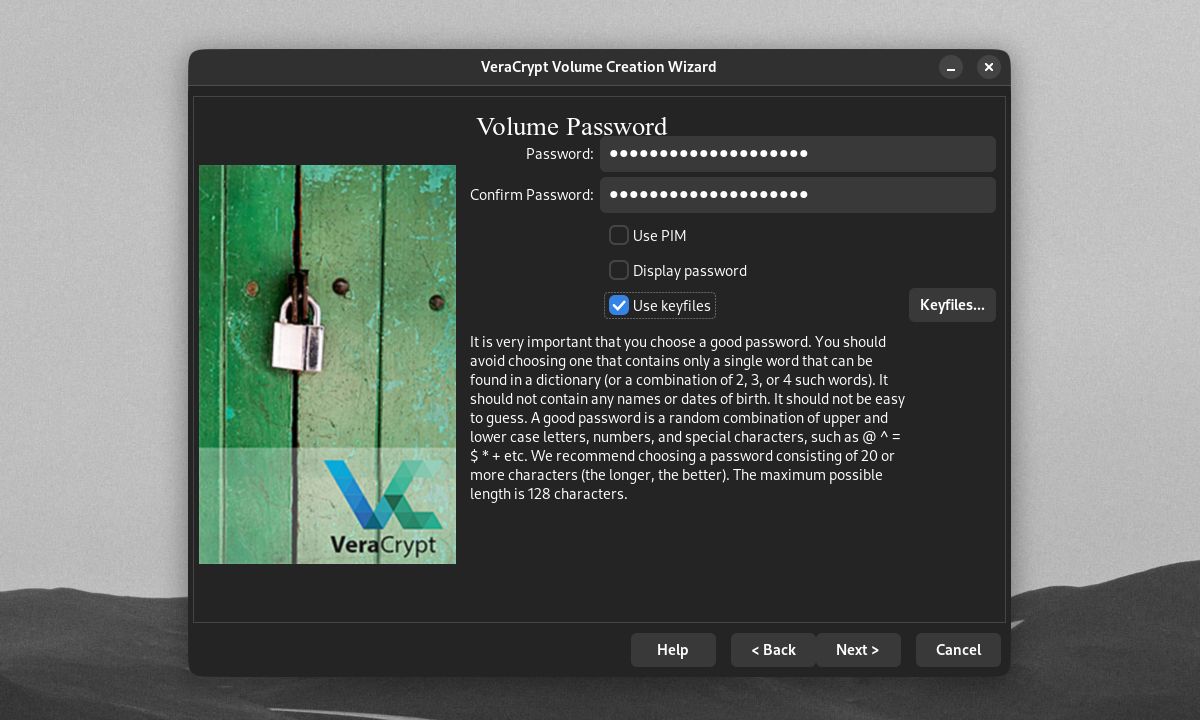
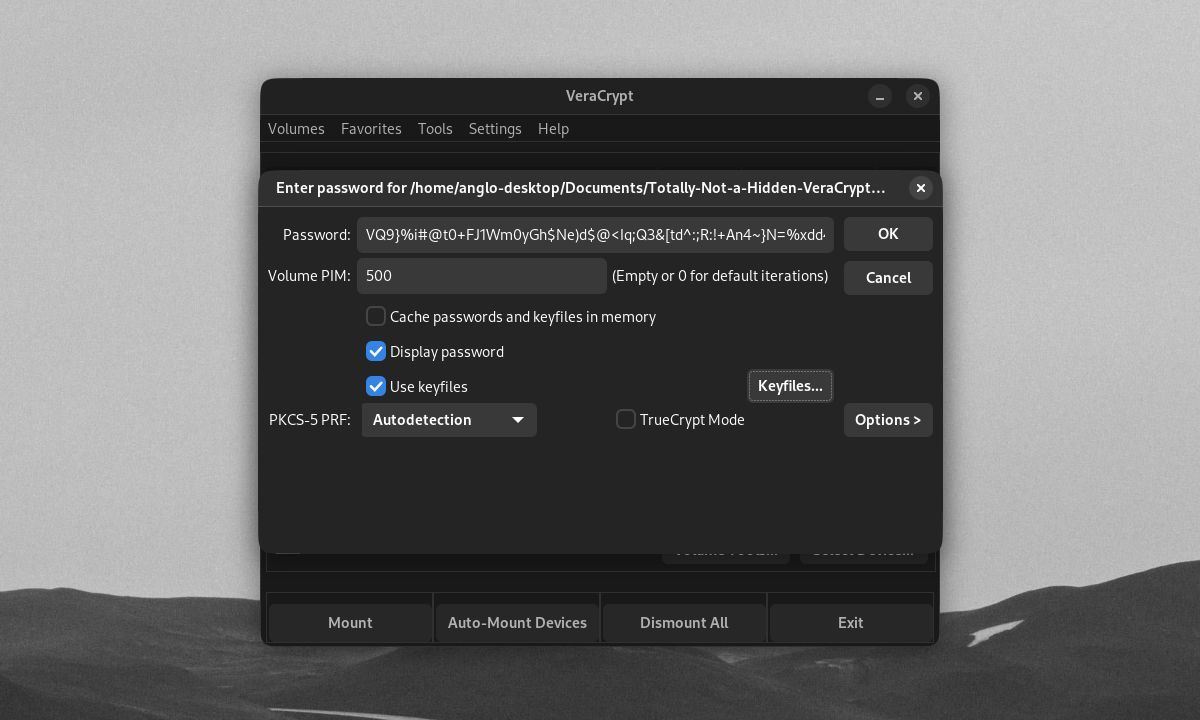
You can get even better security by using files that act as keys to your encrypted volumes. To add a keyfile for your volume, tick the Use keyfiles checkbox on the Volume Password window, then click Keyfiles.
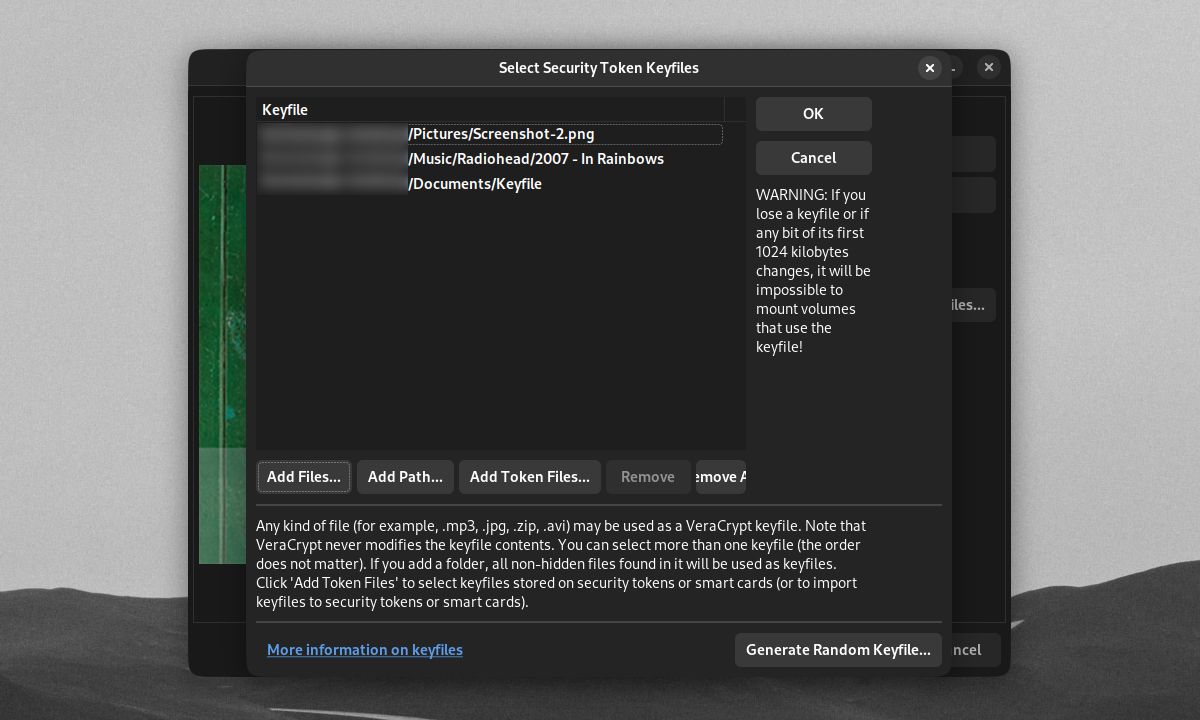
On the Select Security Token Keyfiles screen, you can set any file or folder path to serve as a volume keyfile. You could use Add Token Files to set a hardware security key as your keyfile. If you keep your keyfile in a USB outside your volume's drive, your USB can also act as a physical security key. If you need VeraCrypt to make a new keyfile, click Generate Random Keyfile.
When mounting a volume with a custom Volume PIM and keyfiles, you need to tick the Use PIM and Use keyfiles checkboxes and click the Keyfiles button. This will allow you to input the correct PIM and keyfiles, along with your password, to open your encrypted volume.
Making Changes to Existing VeraCrypt Volumes
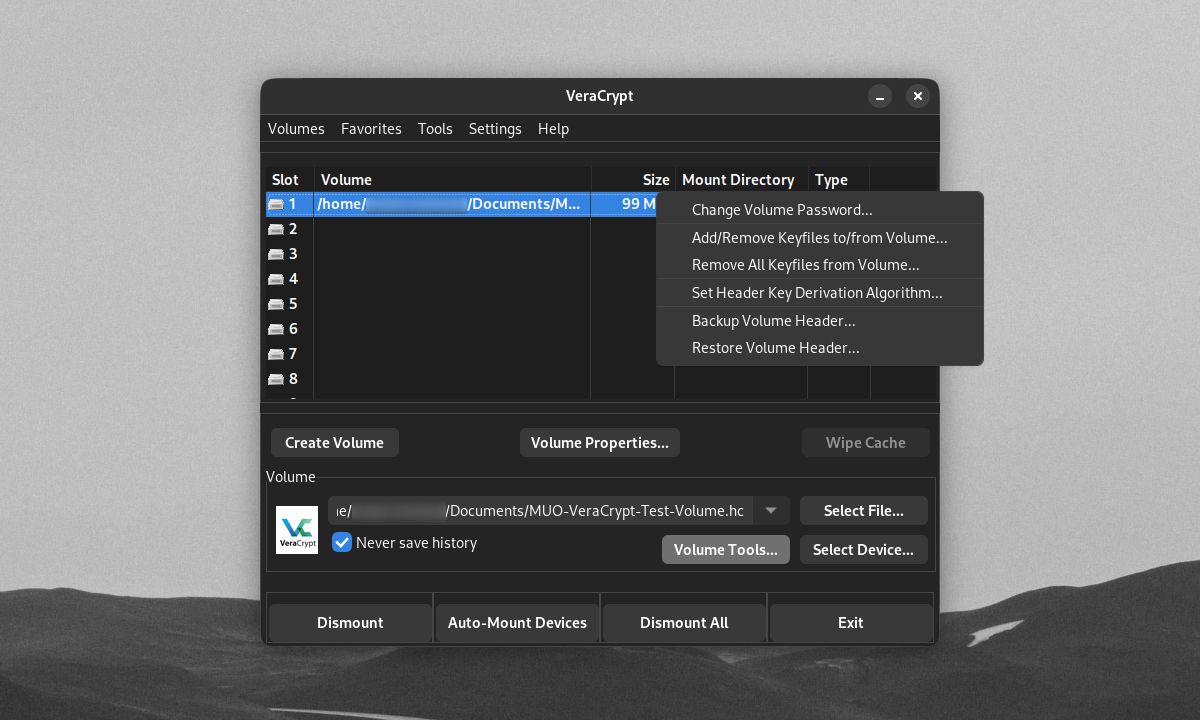
Once you create an encrypted volume, you can still make changes to how you decrypt it. To do this, click on Volume Tools on the VeraCrypt main window. You'll have the option to change or remove your volume's password, PIM, and keyfiles. You can do this if you need to change your passwords regularly.
How to Create Hidden VeraCrypt Volumes
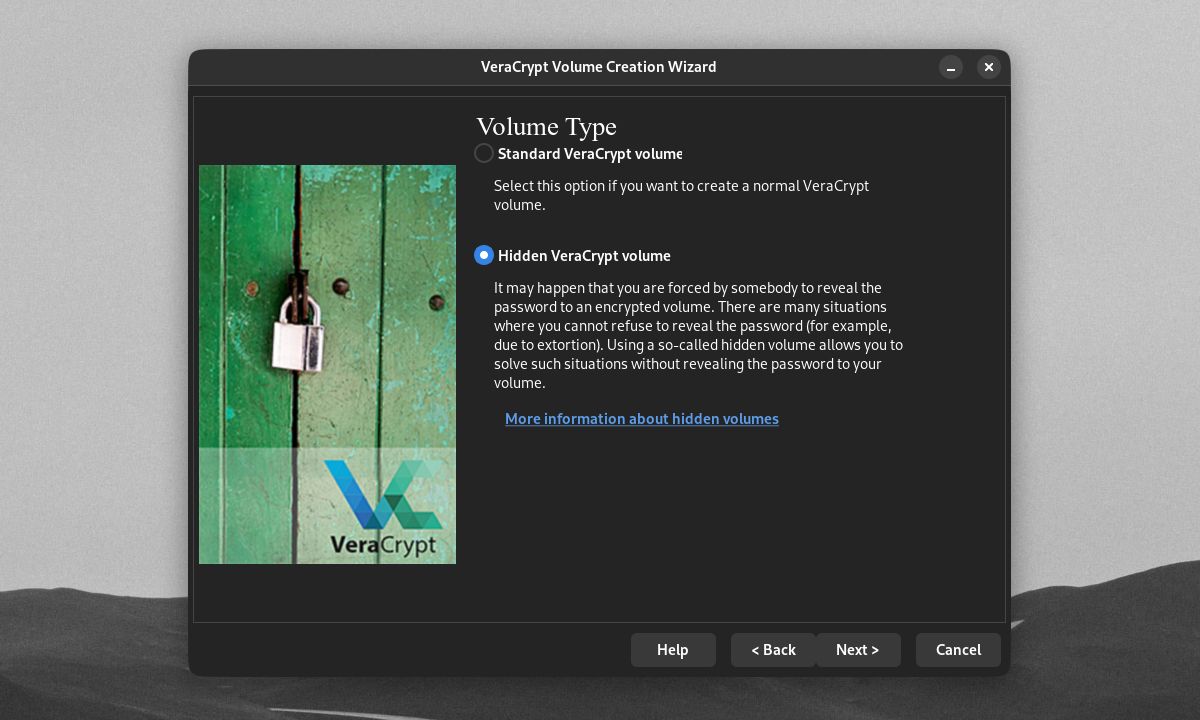
One of VeraCrypt's most useful advanced features is its ability to create hidden encrypted volumes. These are real encrypted volumes hidden inside an outer VeraCrypt volume.
Hidden volumes can come in handy if you're forced to give your password up to a cyber extortion attacker, for example. You can instead give up the password to the outer VeraCrypt volume, which will not expose your hidden volume to any threats.
To start creating a hidden volume, click Hidden VeraCrypt volume on the Volume Type window of the Creation Wizard. Click Next.
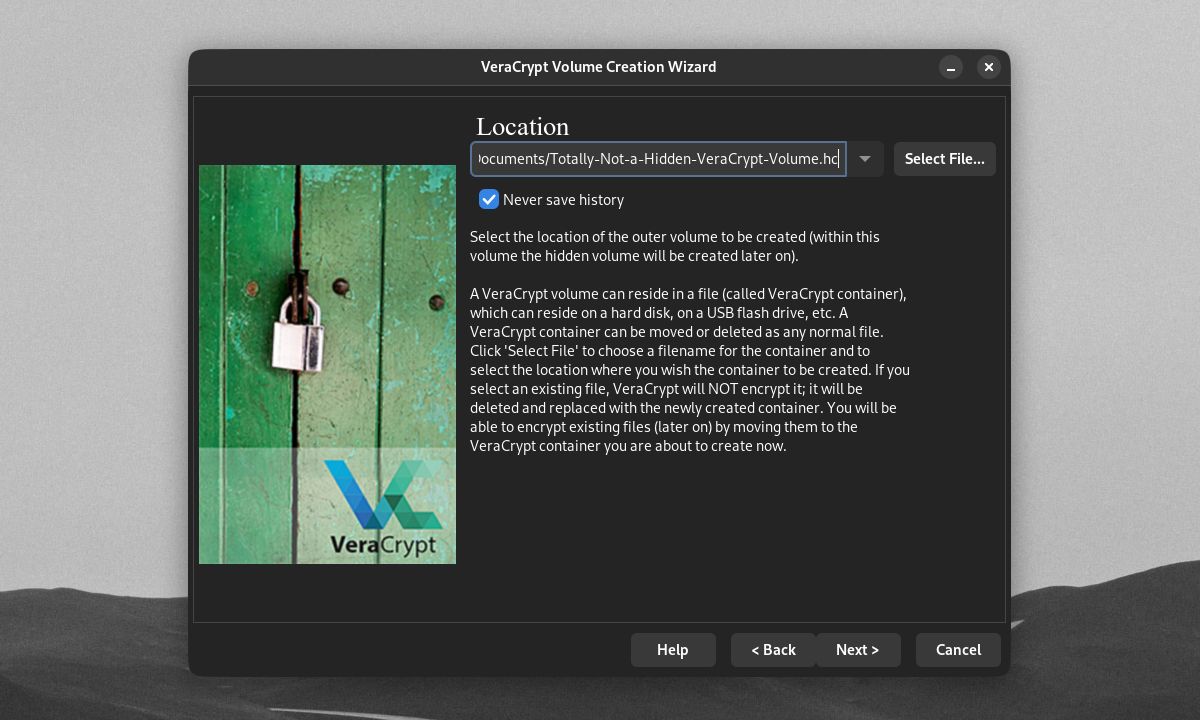
First, VeraCrypt will prompt you to select a device/file location for your hidden volume. Click Next once you're done.
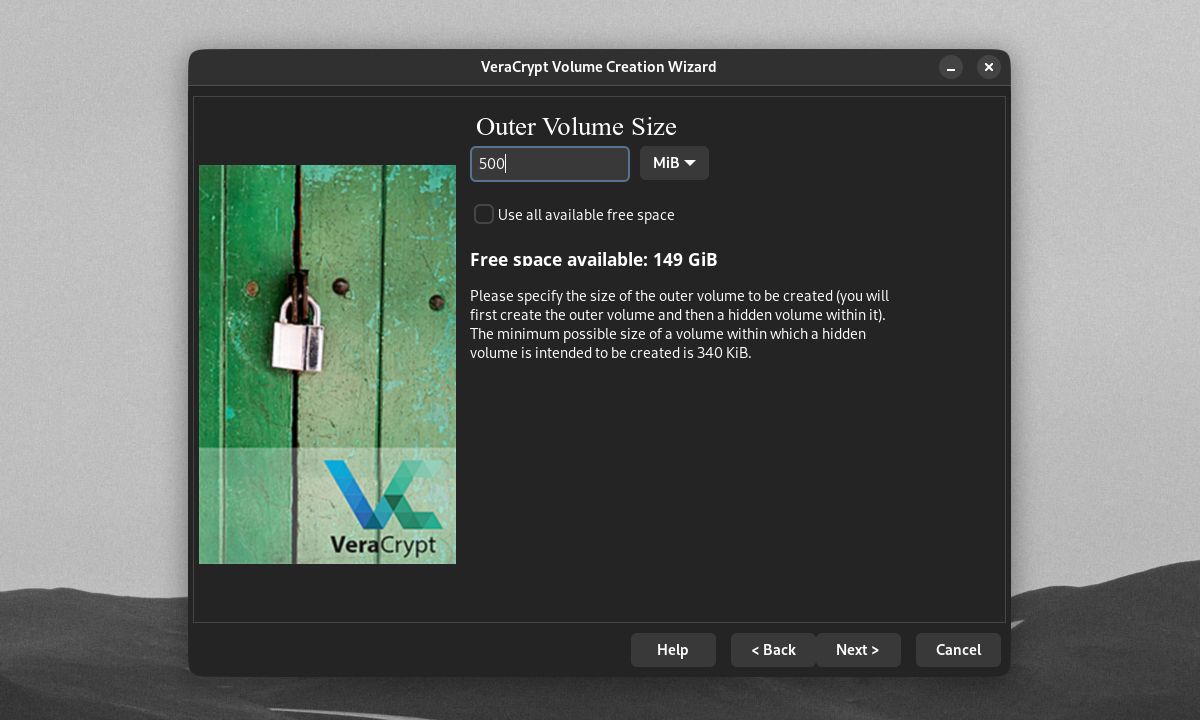
From here, you'll need to create an encrypted outer volume. If you're creating a hidden encrypted drive/partition, VeraCrypt will set the entire device as the outer volume. But if you're creating a hidden encrypted file container, you will need to set the size of the outer volume.
You'll also need to set the outer volume's encryption options, password, and file format.
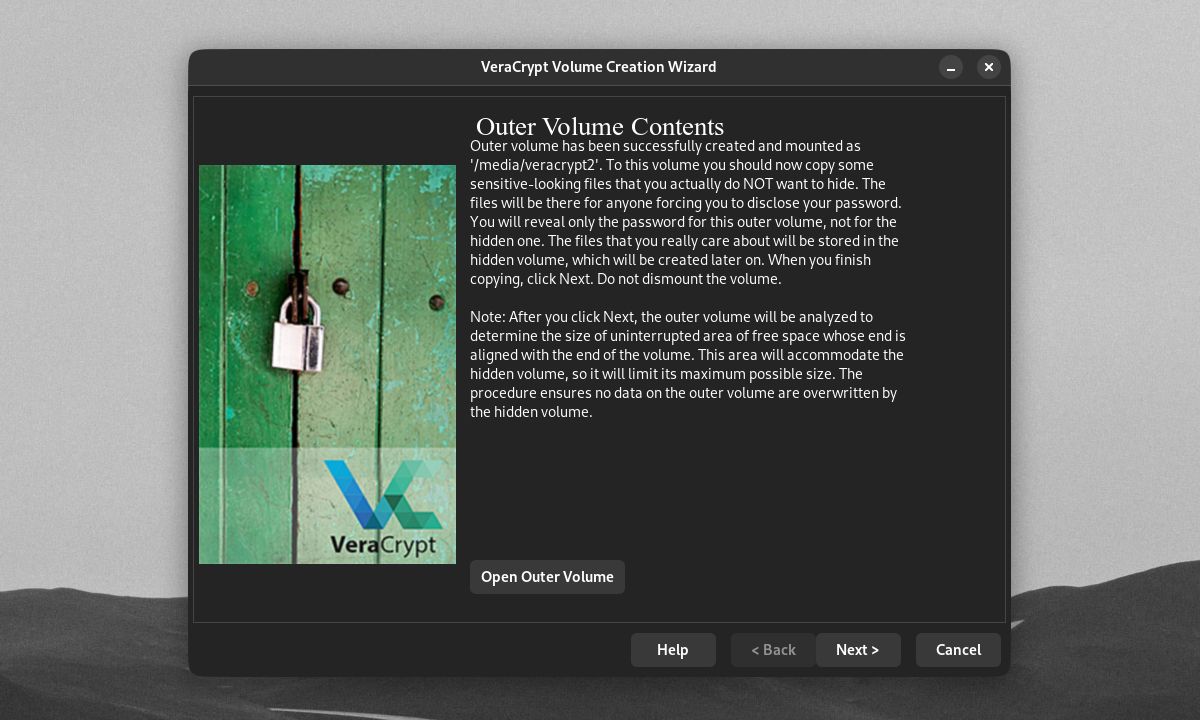
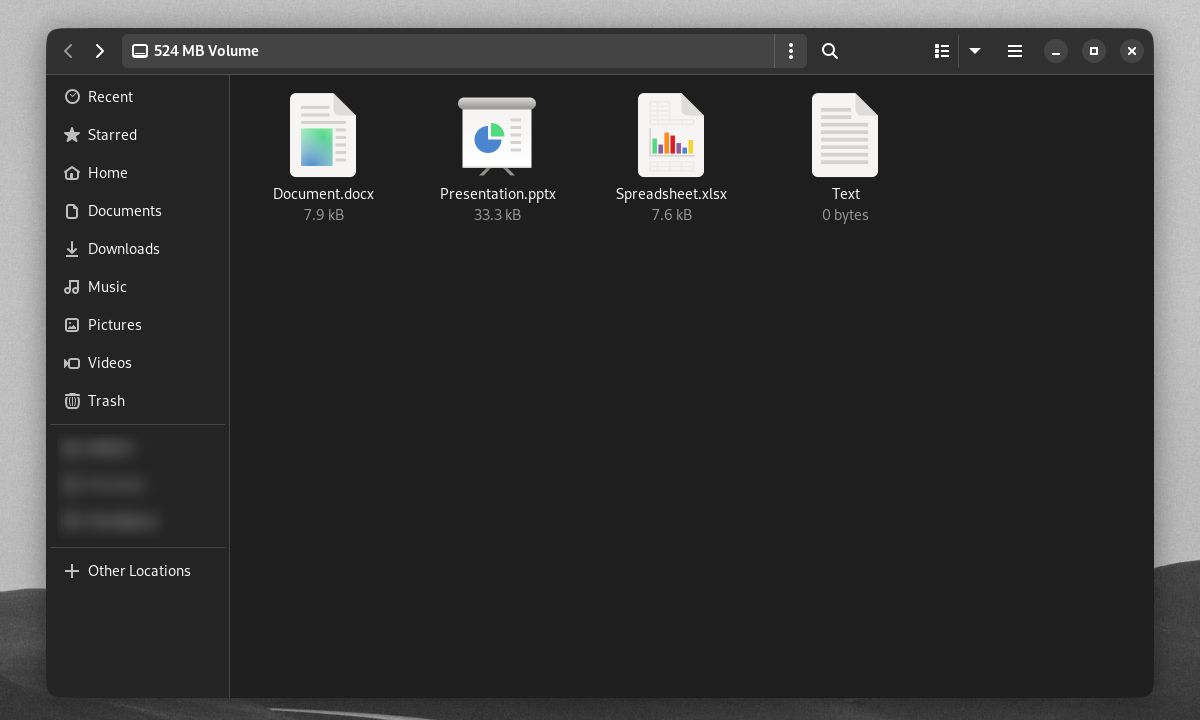
Once VeraCrypt formats the outer volume, you'll be prompted to copy "sensitive-looking" files to the outer volume. These files show up instead of the hidden volume's contents if you're forced to give up your outer volume password. Do this by clicking Open Outer Volume.
Here's an example of an open outer volume. Note that the hidden volume and its contents will appear as free space on an open outer volume.
Once you've created a convincing outer volume, it's time to create your hidden encrypted volume. You can give your hidden volume encryption options that are different from your outer volume.
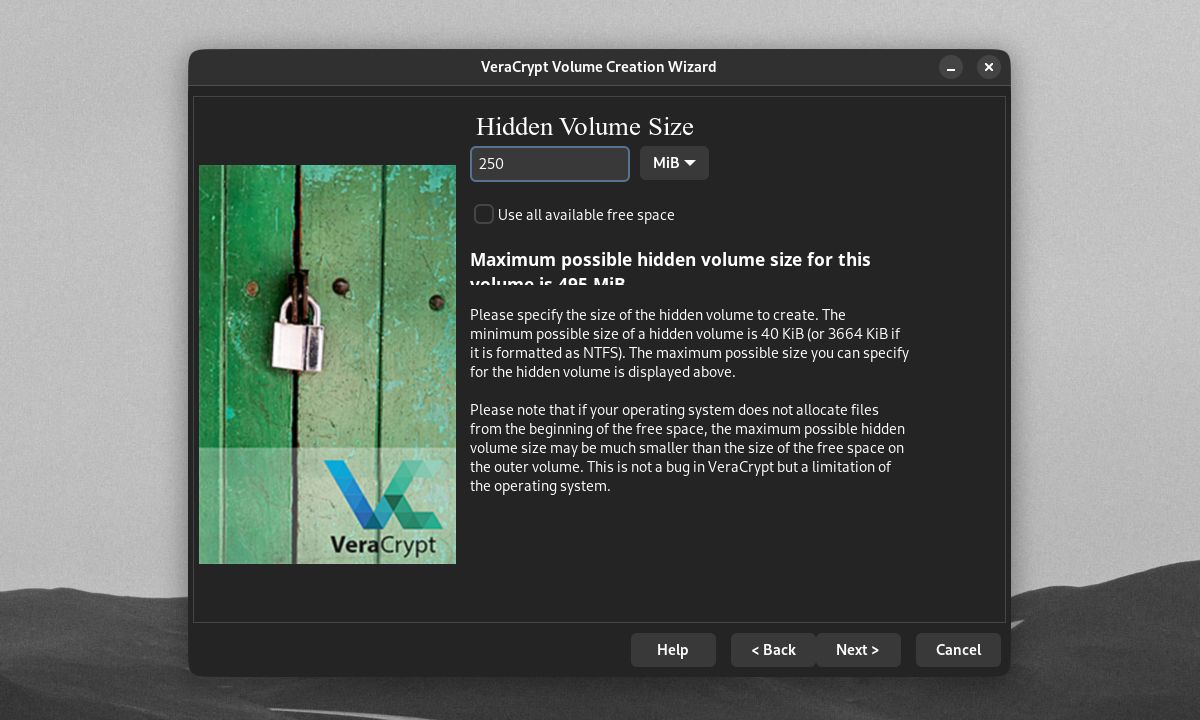
You'll also need to set your hidden volume's size. It should be much smaller than the outer volume to prevent any future hidden volume damage.
Your real volume's password should also be very different from the outer volume password. You can also opt to give your hidden volume a separate volume PIM and keyfiles, and file format.
Once you've finished creating your hidden volume, you can mount it like any other VeraCrypt volume.
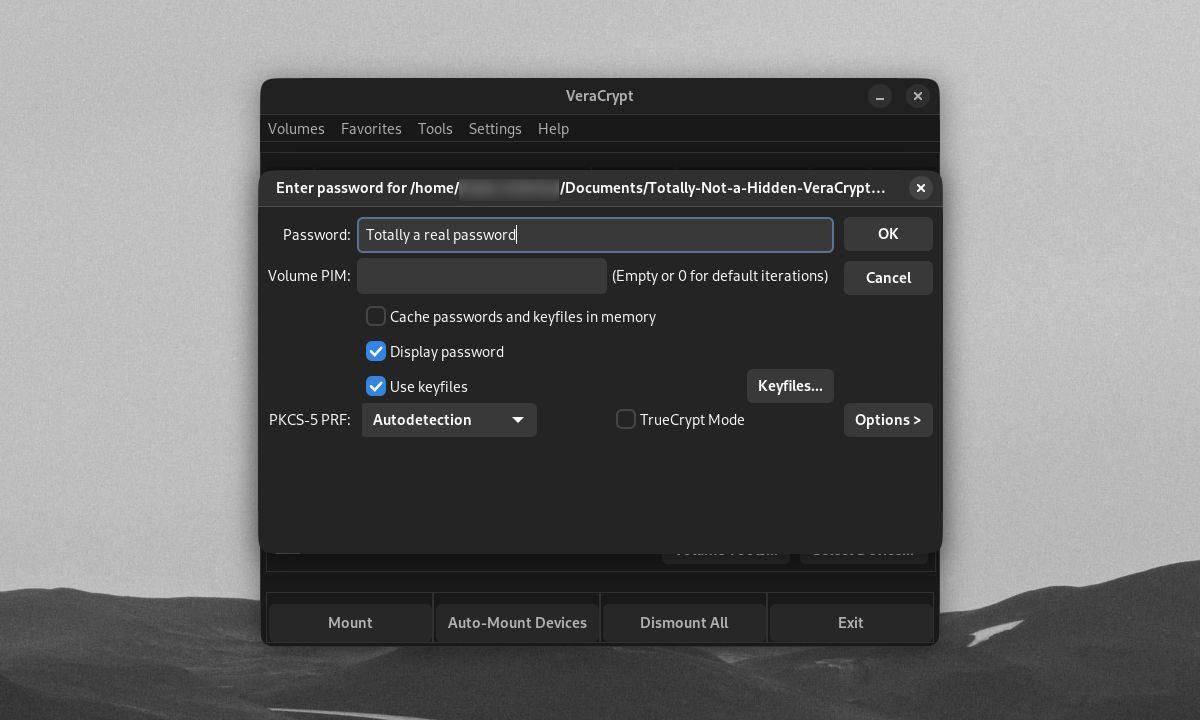
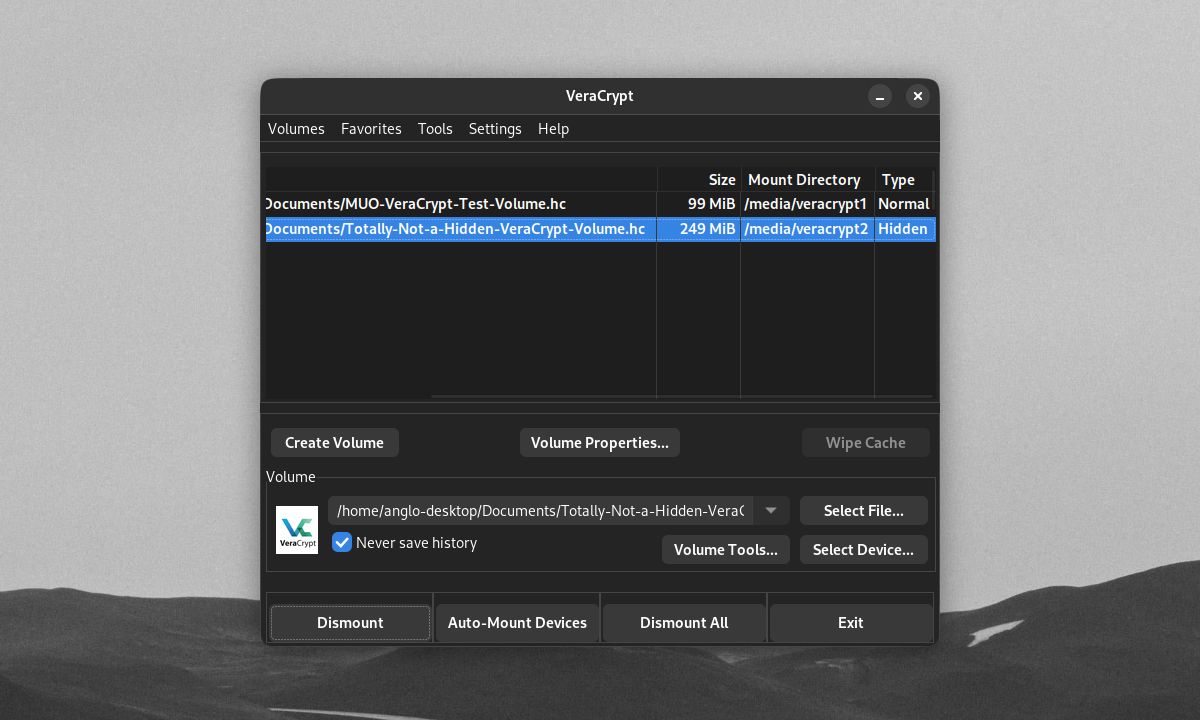
Mounting the volume using the outer volume password will not open your hidden volume. It will instead lead to the outer volume, with VeraCrypt marking the volume as "Normal".
You'll need to remember the passwords, PIM numbers, and keyfiles of your outer and hidden volumes. This is why maintaining a hidden volume can be more difficult than using a regular VeraCrypt volume.
If you mount the volume using your hidden volume password, VeraCrypt will detect and open the hidden volume.
Do You Need to Use VeraCrypt’s Advanced Features?
Creating an encrypted file container with AES, SHA-512, and a strong password should be more than enough to secure most users' files. But if you need extra layers of file protection, you'll be better safe than sorry with VeraCrypt. With keyfiles, a high PIM number, and strong ciphers like Twofish, you can create a VeraCrypt volume that the best hackers can only dream to crack.