Bluetooth is now a widely-used technology, thanks to its inclusion in devices like smartphones and tablets. And while we've grown accustomed to using it to connect devices to our earphones, cars, and other software, Bluetooth nonetheless has its fair share of vulnerabilities.
So is it safe to use Bluetooth? How can hackers attack using Bluetooth?
How Does Bluetooth Work?
In 1989, the telecommunications company, Ericsson, started to work on a wireless alternative to RS-232 serial communication. In 1996, Nokia and similar companies began to look for short-distance protocols such as Bluetooth. All these organizations formed the Bluetooth Special Interest Group (SIG).
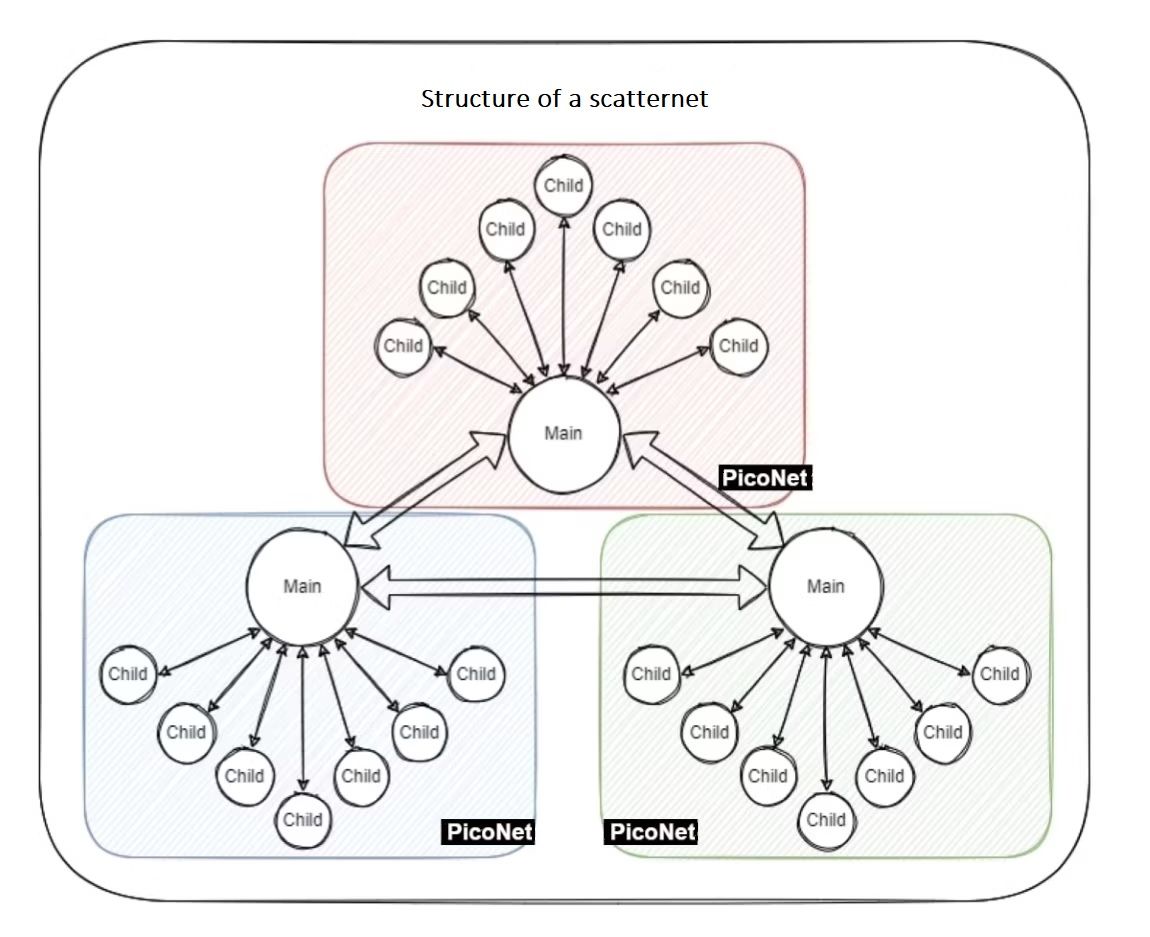
Generally, Bluetooth technology consists of the parent device and child devices connected to it. That's a piconet. Child devices are within 10 meters of the parent device. Piconets unite, and create scatternets. The parent device here communicates with the child devices.
However, it is not possible to talk directly to child devices.
How Bluetooth Security Works
There are three basic security models in the Bluetooth protocol:
- Non-secure mode: There are no security applications in this mode. Steps such as authentication, encryption, and communication security are not available.
- Service level security mode: In this mode, security is only at the service level. In other words, even if an application using the secure service is relatively secure when communicating, there is no extra protection.
- Link-level security mode: This mode works at the connection level, unlike the others. The purpose here is to prevent unauthorized access and to try to fully protect the system.
Each Bluetooth service has a security mode based on it, and provides security with three levels. Some services may use authorization and authentication, while others may only use authentication. There are two different security models for devices using this protocol.
In addition, different security levels are defined for both devices and services in the Bluetooth security architecture. There are two security levels for devices:
- Secure: These are devices that you've previously established any persistent connection to. They have unlimited access to all services as long as there are no limitations at the application layer.
- Unsafe: Devices you have not had any connection to or communication with before are in this category. In addition, these devices are sometimes described as risky and unsafe for other reasons, even if you connect to them.
It is possible to exchange many files during the day with Bluetooth technology. However, if you consider the above security services and modes, you'll realize that you have to give a lot of permissions to the devices you allow to exchange files.
It is a big security problem for another device to have so many privileges over yours just because it is sending a few files. But of course, there are some precautions you can take.
How to Increase Your Bluetooth Security
Keep your Bluetooth setting in “not discoverable” (transmission disabled) and switch to “discoverable” mode only when you are using it. Leaving your smartphone or any Bluetooth device you use in discoverable mode exposes the device to Bluetooth issues. When you're out for a stroll, driving, or even walking around your office, any Bluetooth user in close range could pick up your signal and use it to access your device.
Avoid storing your critical information—such as social security numbers, identity information, serial numbers, passwords, and credit card information—on your Bluetooth-enabled devices. If you do this anyway, at least make sure those are stored on sandboxed services using complex passwords and extra layers of verification like Two-Factor Authentication (2FA).
If you are going to connect with a device via Bluetooth, make this connection in a safe place. This will limit the number of potential intruders in your vicinity.
How Do Hackers Attack Bluetooth?
There is a large pool of attack vectors when it comes to Bluetooth. By exploiting vulnerabilities in Bluetooth, the attacker gains unauthorized access to the victim device.
Once the attacker gains access, they use privilege escalation, i.e. using a smaller exploit to get access to the wider system and leverage control. As a result, it becomes possible to destroy evidence, attack other devices, or even take over the entire device.
Bluetooth devices are typically thought of as safe from long distances. However, this is wrong. It is possible to attack from a distance of 1500 meters with high-gain antennas, and even further, thanks to Bluetooth 5, the latest version of the technology, and developing network structures.
The general method of attackers is to generate unexpected results by transferring erroneous files. When a system receives an unexpected file and the specified security level is insufficient, it either falls into an unstable state or the system crashes. Attackers who take advantage of these situations can perform a lot of attacks on vulnerable devices. The list of what can be achieved as a result of these attacks is extensive and includes:
- Making calls or texts.
- Viewing, modifying, or updating files.
- Interfering with media that may contain sensitive content such as photos, videos, or audio.
- Data theft or theft of material value.
- Displaying something offensive on the device.
In short, attackers can obtain access rights to all operations you can perform at root privilege level. This situation usually occurs because Bluetooth and similar chips are directly connected to the main chip and there is no authority limitation on the main chip. At least by limiting permissions, you can restrict the root privileges during an attack.
What Is the Blueborne Vulnerability?
The vulnerability, named Blueborne, published in September 2017, once again revealed how frightening Bluetooth technology can be. Thanks to this attack, it became possible to run code remotely on many devices (although remote access can be made more secure).
Blueborne had significant differences from other attacks. The aforementioned vectors require user permission. In other words, the end-user was approving things like a file transfer request, connection requests, and device trust requests. In Blueborne, however, the user did not need to give any permissions. It was possible to use it remotely.
The Logic of Remotely Exploitable Vulnerabilities
One of the most crucial points about vulnerabilities that enable remote attacks is that they do not need any user approval. There are three main fundamental rules to this:
- It shouldn't need any human interaction to exploit.
- It should not make complex assumptions about the active state of the system.
- Once exploited, it should leave the system in a stable state.
In other words, a hacker can carry out attacks using the vulnerability without the knowledge of the victim. The best example of this would undoubtedly be the Blueborne attack. Using Bluetooth technology, an attacker can reach the devices of an individual or even the masses, and manipulate them.
Don’t Underestimate Bluetooth Attacks
Don't leave your Bluetooth connection open, and never accept Bluetooth connections you do not trust. Keep your software up to date and remove unused Bluetooth devices from the list of trusted devices. These methods will protect you from most attacks over Bluetooth.
Of course, perfect security does not exist, and attack vectors will continue to evolve as technology does.