A firewall refers to a computer security system that prevents unauthorized access to your LAN (local area network) by placing a virtual wall on connections that are not authorized to send traffic back to you.
Firewalls tend to be adequate for restricted traffic, but they do not protect against any computer attack. And that is why it is crucial to know what type of firewall is suitable for you so that you can pick the right one.
What You Should Know Before Getting a Firewall
We want to clarify that firewalls don't protect traffic that does not pass through them because they cannot control it. This means that our devices can be easily infected through flash drives or any other type of external storage. That is why a firewall is not a replacement for antivirus but rather something you should use alongside.
An antivirus will protect against those viruses that the firewall cannot detect, making firewalls and antiviruses a perfect complement. That is why it is imperative to pick the right firewall for you.
The 5 Basic Types of Firewalls
Depending on how they operate to protect your network and their feature set, firewalls fall into one of the five types below:
1. Packet-Filtering Firewall
Packet filtering firewalls are the most basic type of firewalls, and although they are considered outdated, they still play a crucial role in cybersecurity. A packet filtering firewall is the equivalent of a security guard with a wanted list who compares the list with all who pass by. A man with a gun could walk by, but the guard would not stop him if he were not on the wanted list.
A packet-filtering firewall operates by inspecting packets at junction points. They examine these packets by comparing them with a set of already established criteria, so when they receive a packet that does not fulfill the checklist, they drop it or filter it, hence the name. Packet filtering firewalls have several advantages, such as price and efficiency in scanning traffic.
Packet filtering firewalls have some downfalls; they can be easily spoofed and are not very user-friendly for you to access the pre-establish controls to make amendments. They are ideal for individuals and small organizations that don't have too much sensitive data on their servers. Ideally, they serve as a basic level of security alongside other software or as part of a layered defense strategy.
2. Circuit-Level Gateway Firewall
A circuit-level gateway firewall is similar to a packet filtering firewall. Its main difference is that it can process requested transactions while filtering all other traffic. They are also straightforward to set up and are reasonably priced. They have some downfalls, like not offering protection against data leakage from within the devices. Also, they require frequent updates to keep current with all the threats.
Ideally, they are used alongside other firewalls and as part of a layered defense. Back to the analogy, in simple terms, this firewall would also be a security guard with a wanted list, who compares the list with everyone who passes by. The main difference is that this guard will get a new wanted list more often, or upon request, to update the old one.
3. Application-Level Gateway Firewalls/Proxy Firewall
A proxy firewall works similarly to a cloud secure web gateway (SWG) because it builds a gate that all traffic must go through, making it the only entry point for the network. Unlike the last two firewalls, proxy firewalls will filter and scan all packets according to their intended service, destination port, and attached characteristics, making it easier to detect suspicious packages.
Proxy firewalls inhibit network performance and can become challenging to program and manage due to their advanced capabilities. They are also more expensive than the last two firewalls and don't work with all network protocols; this is why they are used mainly by larger organizations needing to block access to more threats while preventing data leaks of sensitive information.
This firewall would be the equivalent of a security guard located at the only entry point with a wanted list, who additionally asks passengers what they do for work, where they are heading, and where they are coming from to see if anything is suspicious. They do this for passengers exiting and entering the terminal.
4. Stateful Inspection Firewall
Stateful inspection firewalls conduct an in-depth analysis of payloads and packets, giving users a more robust security lawyer. For these firewalls to work correctly, there must be a high degree of control over the content that's let in and out of the network. Like proxy firewalls, stateful inspection firewalls will be very expensive and interfere with network and communication speed.
This type of firewall would be the equivalent of a security guard with a wanted list who asks passengers the same questions as the last security guard and takes a good look at each passenger for any prohibited items or suspicious behavior.
5. Next-Generation Firewall
A next-generation firewall represents the highest level of security in terms of firewalls. Unlike other firewalls, an NGFW can understand the different applications that generate traffic that passes through them. This is done by automatic updates and by integrating several security techniques, which in the past were usually done by different software.
Naturally, due to its complexity, there are some downfalls to an NGFW. For example, they need to be appropriately integrated with other security systems in the organization so that they can work with all other security measures rather than alongside them. This is a very complex process and must be done by a tech-savvy individual or a company's IT department.
NGFWs are also among the most expensive ones in the market and are heavily used in the cloud. Due to their price and complexity, NGFWs are mostly preferred by organizations looking to keep a lot of their data private; these include law firms, hospitals, or finance firms.
This type of firewall would be the equivalent of a three security guard team using an x-ray machine. One guard has a wanted list, one guard looks at the x-ray, and one guard checks the boarding pass and passport while asking a lot of questions. Additionally, these guards constantly communicate with the CCTV security center and all other guards in the airport; pretty impressive, right?
The 3 Types of Firewall Delivery Methods
Firewalls are deployed in three different ways, depending on the organization's needs. So, let's take a look at them, shall we?
1. Hardware-Based Firewalls
A hardware-installed firewall is located in routers and used to access the internet safely. Most routers come with the firewall already installed. It will essentially act as a gateway inside your network perimeter and thus, not consume processing power on your device, making it ideal for individuals or small organizations with many devices.
The main disadvantage of this type of firewall is that it will only protect devices behind the router. Hardware-based firewalls also require some skill to update and install.
2. Software-Based Firewalls
A software-based firewall is installed as virtual appliances, meaning you will need to install them on every device you want to protect. This could take some staffing and time and will likely consume significant CPU and RAM resources.
These firewalls are great to help keep your electronic device protected in public places. They are also the most popular and can be either free or paid for; TinyWall is a great example of a free software-based firewall.
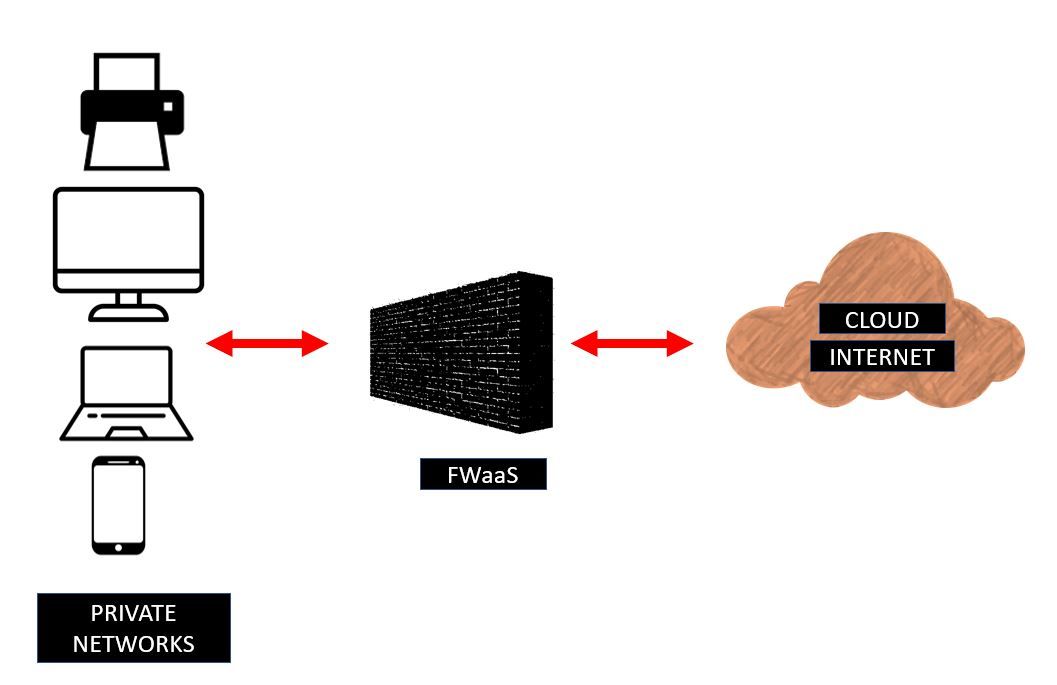
3. Cloud-Based Firewalls
Cloud-based firewalls are sometimes referred to as cloud firewalls and firewall-as-a-service (FWaaS). A cloud-based firewall works the same way as the last two but serves to create a barrier between your cloud and all systems and networks connected to it.
Choose the Right Firewall for Your Needs
Whether you are an individual looking to complete your antivirus, or a larger organization looking to protect your data from leaks or theft in the cloud, there is a firewall for you. Just remember what each type of firewall is better suited for and the hosting advantages and disadvantages before ultimately deciding on one.