Transferring data between two devices is often a time consuming mess. Cables, unreliable Bluetooth connections, and significant patience are all part of our collective suffering.
Fortunately, an alternative exists in the form of Wi-Fi Direct. Developed by the Wi-Fi Alliance, Wi-Fi Direct promises to deliver the speed of a traditional Wi-Fi network. Two devices are able to communicate directly, without the need of an internet connection.
Of course, no new technology is without downsides. According to research presented at Black Hat Europe 2017, Wi-Fi Direct may be compromising our security. In doing so, it unwittingly grants hackers an easy way into our digital lives---all in the pursuit of convenience.
How exactly does Wi-Fi direct make us vulnerable, and what can we do about it?
What Is Wi-Fi Direct?
Bluetooth has been around since 1994, and it was once considered the easiest, fastest solution for wireless file transfer. However, it wasn't the best: speeds were slow and reliability was poor.
In the almost quarter of a century since, we've been propelled into the digital age, creating, consuming, and transferring files far larger than existed in 1994. The Wi-Fi Alliance thought they could help, and created Wi-Fi Direct---combining the ease of Bluetooth and the speed of Wi-Fi.
Although we associate Wi-Fi with the internet, it is actually a way to create a local wireless network. It just so happens that most of the time the Wi-Fi Access Point (AP) is connected to the internet. Wi-Fi Direct is not constrained by an internet connection. Instead it allows two devices to set up a peer-to-peer (P2P) Wi-Fi network, without the need for a wireless router.
Although it uses different technology, the reality is that Wi-Fi Direct is a lot like Bluetooth---except with speeds up to 250Mbps (ten times the speed offered by Bluetooth 4.0) and AES 256-bit encryption.
How Does Wi-Fi Direct Work?
Wi-Fi Direct is a fairly confusing name. In fact, it sounds strangely like a service used to easily connect to a Wi-Fi network. Although, that already exists as Wi-Fi Protected Setup (WPS).
During development, Wi-Fi Direct had an alternative name (Wi-Fi P2P) which better summarizes the protocol. Instead of connecting to a central Access Point (AP), two devices are able to connect directly to each other.
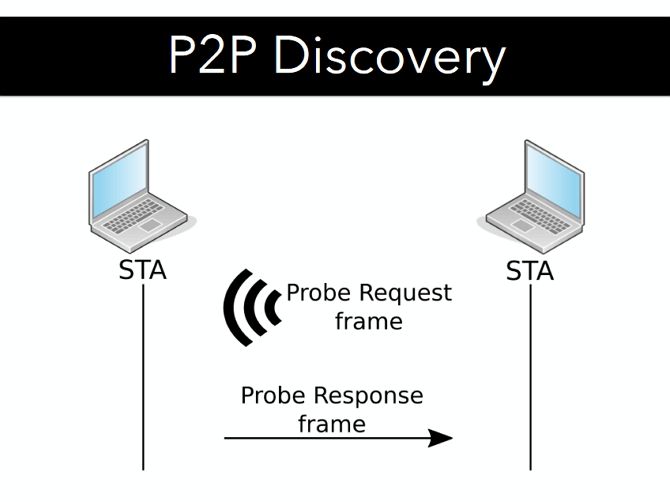
The Discovery Procedure, which allows for the creation of the Wi-Fi Direct connection, consists of two device states: listen, and search. When in a listening state, the device waits to receive a probe request which it can answer, known as passive scanning.
The search state, or active scanning, sends out requests, waiting for responses from devices in a listening state. To create the P2P network, both devices need to actively switch between both states.
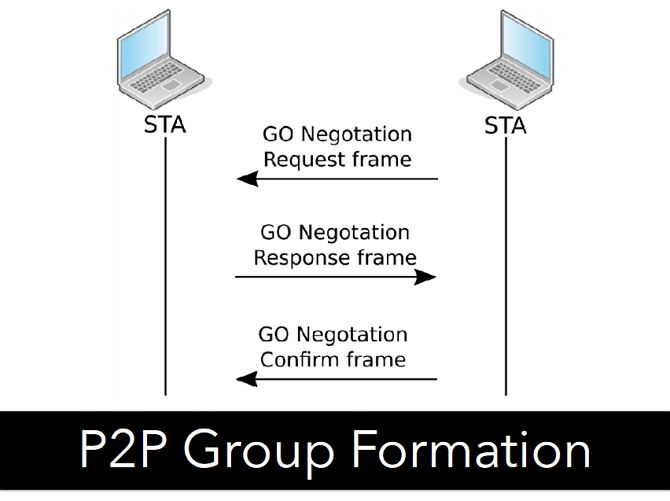
Once two devices have located each other, they enter negotiations as to which device will act as the P2P Group Owner (P2P GO). The P2P GO closely resembles the AP in a traditional network, allowing the other device to connect to it.
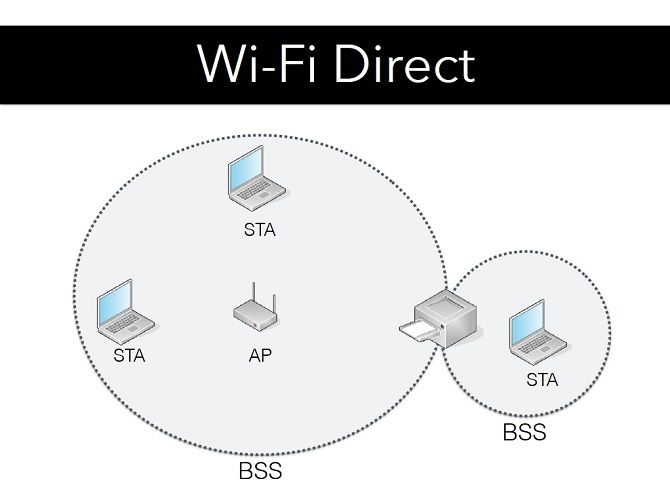
Printers, Smart TVs, and similar Internet of Things (IoT) devices are often designed to act by default P2P GOs. They emit beacon frames, so that other devices can find them, and determine if they are suitable to connect to. This means there is no need for the GO negotiation, with the end result that the Wi-Fi Direct and Wi-Fi connections seem functionally similar.
A Problem With Wi-Fi Direct's Implementation
In practice, none of these technologies works in isolation. Many devices that support Wi-Fi Direct are also connected to a standard Wi-Fi network at the same time. Your home printer, for example, may be able to accept photos directly from your smartphone via Wi-Fi Direct, but it is also probably connected to your home network.
The ability for a device to connect to multiple networks concurrently is usually a positive one. It is also one of Wi-Fi Direct's greatest vulnerabilities.
However, Wi-Fi Direct as a specification isn't to blame. Instead, it is the implementation and poor security practices of the many device manufacturers that put you at risk.
This problem isn't unique to Wi-Fi Direct. Indeed, it is a common weakness in IoT devices. Among the many examples presented by Andrés Blanco at Black Hat Europe, were printers from HP and Samsung, and a media streaming device from Western Digital.
The Point of Entry
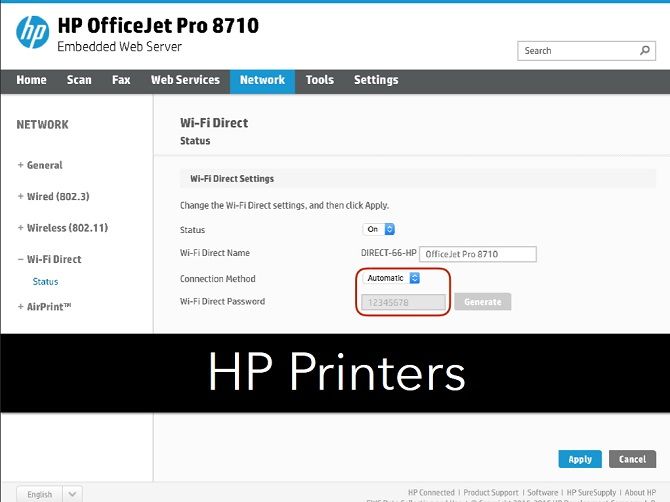
Blanco used HP's OfficeJet Pro 8710 as a case study. The printer supports Wi-Fi Direct, and is also able to accept concurrent connections to standard Wi-Fi networks. The printer's security management includes; HTTPS, WPA2, 802.1x wireless authentication, PSK, and a firewall amongst other things.
After reading the specification sheet, you might be left thinking you've invested in a bulletproof device. The printer is setup as a P2P GO, so that it broadcasts its existence and allows other devices to connect to it.
The Wi-Fi Direct standard mandates that once a connection is requested, the devices then use the WPS connection protocol to establish the connection. The WPS pin is a numerical eight digit code, which is easily subjected to brute force attack. HP's implementation of the WPS protocol is to automatically allow Wi-Fi Direct connections, using the default WPS password of '12345678'.
In effect, this allows anyone to establish a Wi-Fi connection to the printer, without any authentication or notification. The attacker then has full access to the printer---potentially including its print memory and history---as well as an entry point to the wider Wi-Fi network that the printer is connected to.
Another example of poor implementation can be found in the Western Digital TV Live Media Player. The device supported Wi-Fi Direct as standard, and it was automatically enabled, allowing anyone within range to connect.
The connected device then had full access to the remote control features, as well as the web server, and read/write access to the media server and all connected devices. All of these permissions were granted with no authentication or notification. Perhaps unsurprisingly, the WD TV Live was discontinued in 2016.
Is Wi-Fi Direct Really an Issue?
Many manufacturers claim that the vulnerabilities around Wi-Fi Direct aren't a concern down to the protocol's distance limitations of around 100m. Standard Wi-Fi networks also have a range of around 100m and this does little to prevent attacks.
The Wi-Fi Direct protocol has flaws. However, as is the case across the tech industry, the main flaws come from hardware manufacturers doing little to secure their devices.
Eager to part you with your hard-earned cash, technological developments are rebranded as features, but with no time invested in securing them. As the vulnerabilities differ by device, the best you can do is be aware of the devices on your network.
When setting up a device change the default settings, disable insecure features, and make your network secure. Until companies are forced to face the cost of their poor security standards, it's left to us as users to prevent the damage they cause.