2017 was the year of ransomware. 2018 was all about cryptojacking. 2019 is shaping up as the year of formjacking.
Drastic decreases in the value of cryptocurrencies such as Bitcoin and Monero mean cybercriminals are looking elsewhere for fraudulent profits. What better place than to steal your banking information straight from the product order form, before you even hit submit. That's right; they're not breaking into your bank. Attackers are lifting your data before it even gets that far.
Here's what you need to know about formjacking.
What Is Formjacking?
A formjacking attack is a way for a cybercriminal to intercept your banking information direct from an e-commerce site.
According to the Symantec Internet Security Threat Report 2019, formjackers compromised 4,818 unique websites every month in 2018. Over the course of the year, Symantec blocked over 3.7 million formjacking attempts.
Furthermore, over 1 million of those formjacking attempts came during the final two months of 2018---ramping up towards the November Black Friday weekend, and onward throughout the December Christmas shopping period.
So, how does a formjacking attack work?
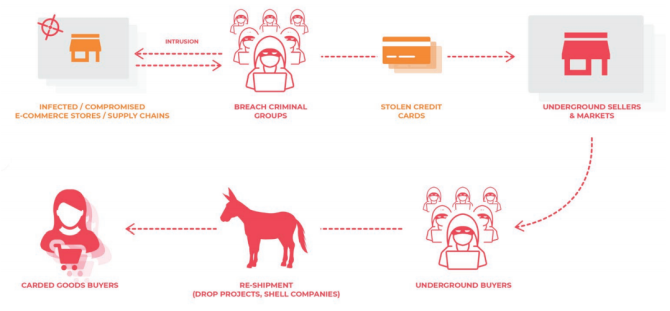
Formjacking involves inserting malicious code into the website of an e-commerce provider. The malicious code steals payment information such as card details, names, and other personal information commonly used while shopping online. The stolen data is sent to a server for reuse or sale, the victim unaware that their payment information is compromised.
All in all, it seems basic. It is far from it. One hacker used 22 lines of code to modify scripts running on the British Airways site. The attacker stole 380,000 credit card details, netting over £13 million in the process.
Therein lies the allure. Recent high-profile attacks on British Airways, TicketMaster UK, Newegg, Home Depot, and Target share a common denominator: formjacking.
Who Is Behind the Formjacking Attacks?
Pinpointing a single attacker when so many unique websites fall victim to a single attack (or at least, style of attack) is always difficult for security researchers. As with other recent cybercrime waves, there is no single perpetrator. Instead, the majority of formjacking stems from Magecart groups.
The name stems from the software the hacking groups use to inject malicious code into vulnerable e-commerce sites. It does cause some confusion, and you often see Magecart used as a singular entity to describe a hacking group. In reality, numerous Magecart hacking groups attack different targets, using different techniques.
Yonathan Klijnsma, a threat researcher at RiskIQ, tracks the various Magecart groups. In a recent report published with risk intelligence firm Flashpoint, Klijnsma details six distinct groups using Magecart, operating under the same moniker to avoid detection.
The Inside Magecart report [PDF] explores what makes each of the leading Magecart groups unique:
- Group 1 & 2: Attack a wide range of targets, use automated tools to breach and skim sites; monetizes stolen data using a sophisticated reshipping scheme.
- Group 3: Very high volume of targets, operates a unique injector and skimmer.
- Group 4: One of the most advanced groups, blends in with victim sites using a range of obfuscation tools.
- Group 5: Targets third-party suppliers to breach multiple targets, links to the Ticketmaster attack.
- Group 6: Selective targeting of extremely high-value websites and services, including the British Airways and Newegg attacks.
As you can see, the groups are shadowy and use different techniques. Furthermore, the Magecart groups are competing to create an effective credential stealing product. The targets are different, as some groups specifically aim for high-value returns. But for the most part, they're swimming in the same pool. (These six are not the only Magecart groups out there.)
Advanced Group 4
The RiskIQ research paper identifies Group 4 as "advanced." What does that mean in the context of formjacking?
Group 4 attempts to blend in with the website it is infiltrating. Instead of creating additional unexpected web traffic that a network administrator or security researcher might spot, Group 4 tries to generate "natural" traffic. It does this by registering domains "mimicking ad providers, analytics providers, victim's domains, and anything else" that helps them hide in plain sight.
In addition, Group 4 regularly alters the appearance of its skimmer, how its URLs appear, the data exfiltration servers, and more. There's more.
The Group 4 formjacking skimmer first validates the checkout URL on which it is functioning. Then, unlike all other groups, the Group 4 skimmer replaces the payment form with one of their own, serving the skimming form directly to the customer (read: victim). Replacing the form "standardizes the data to pull out," making it easier to reuse or sell on.
RiskIQ concludes that "these advanced methods combined with sophisticated infrastructure indicate a likely history in the banking malware ecosystem . . . but they transferred their MO [Modus Operandi] toward card skimming because it is a lot easier than banking fraud."
How Do Formjacking Groups Make Money?
Most of the time, the stolen credentials are sold online. There are numerous international and Russian-language carding forums with long listings of stolen credit card and other banking information. They're not the illicit, seedy type of site you might imagine.
Some of the most popular carding sites present themselves as a professional outfit---perfect English, perfect grammar, customer services; everything you expect from a legitimate e-commerce site.
Magecart groups are also reselling their formjacking packages to other would-be cybercriminals. Analysts for Flashpoint found adverts for customized formjacking skimmer kits on a Russian hacking forum. The kits range from around $250 to $5,000 depending on complexity, with vendors displaying unique pricing models.
For instance, one vendor was offering budget versions of professional tools seen the high-profile formjacking attacks.
Formjacking groups also offer access to compromised websites, with prices starting as low as $0.50, depending on the website ranking, the hosting, and other factors. The same Flashpoint analysts discovered around 3,000 breached websites on sale on the same hacking forum.
Furthermore, there were "more than a dozen sellers and hundreds of buyers" operating on the same forum.
How Can You Stop a Formjacking Attack?
Magecart formjacking skimmers use JavaScript to exploit customer payment forms. Using a browser-based script blocker is usually enough to stop a formjacking attack stealing your data.
- Chrome users should check out ScriptSafe
- Firefox users can use NoScript
- Opera users can use ScriptSafe
- Safari users should check out JSBlocker
Once you add one of the script blocking extensions to your browser, you will have significantly more protection against formjacking attacks. It isn't perfect though.
The RiskIQ report suggests avoiding smaller sites that do not have the same level of protection as a major site. Attacks on British Airways, Newegg, and Ticketmaster suggest that advice isn't entirely sound. Don't discount it though. A mom and pop e-commerce site is more likely to host a Magecart formjacking script.
Another mitigation is Malwarebytes Premium. Malwarebytes Premium offers real-time system scanning and in-browser protection. The Premium version protects against precisely this sort of attack. Unsure about upgrading? Here are five excellent reasons to upgrade to Malwarebytes Premium!