One of my favorite cybersecurity terms is "botnet." It conjures all sorts of imagery: interconnected robots, legions of networked workers simultaneously powering toward a single goal. Funnily enough, the image the word evokes is similar to what a botnet is -- in roundabout terms, at least.
Botnets account for a serious amount of computing power around the world. And that power is regularly (perhaps even consistently) the source of malware, ransomware, spam, and more. But how do botnets come into existence? Who controls them? And how can we stop them?
What Is a Botnet?
The SearchSecurity botnet definition states that "a botnet is a collection of internet-connected devices, which may include PCs, servers, mobile devices and internet of things devices that are infected and controlled by a common type of malware. Users are often unaware of a botnet infecting their system."
The final sentence of the definition is key. Devices within a botnet aren't usually there willingly. Devices infected with certain malware variants are controlled by remote threat actors, aka cybercriminals. The malware hides the malicious botnet activities on the device rendering the owner unaware of their role in the network. You could be sending spam offering appendage enlarging tablets by the thousands -- without an inkling.
As such, we often refer to infected botnet devices to as "zombies."
What Does a Botnet Do?
A botnet has several common functions depending on the desire of the botnet operator:
- Spam: Sending vast volumes of spam around the globe. For instance, the average share of spam in global email traffic between January to September was 56.69 percent. When security research firm FireEye temporarily halted the transition of the notorious Srizbi botnet after the infamous McColo hosting went offline, global spam fell by a huge number (and in fact, when it finally went offline, global spam temporarily dropped by around 50 percent).
- Malware: Delivering malware and spyware to vulnerable machines. Botnet resources are bought and sold by malefactors to further their criminal enterprises.
- Data: Capturing passwords and other private information. This ties into the above.
- Click fraud: An infected device visits websites to generate false web traffic and advertising impressions.
- Bitcoin: Botnet controllers direct infected devices to mine Bitcoin and other cryptocurrencies to generate profit quietly.
- DDoS: Botnet operators direct the power of infected devices at specific targets, taking them offline in distributed-denial-of-service attacks.
Botnet operators usually turn their networks to a number of these functions to generate profit. For instance, botnet operators sending medical spam to U.S. citizens also own the knock-off pharmacies that deliver the goods. (Oh yes, there are actual products at the end of the email. Brian Krebs's Spam Nation is an excellent look into this.)
The major botnets have slightly changed direction in the past few years. Whereas medical and other similar types of spam were extremely profitable for a long time, government crackdowns in several countries eroded profits. As such, the number of emails carrying a malicious attachment rose to one in every 359 emails, according to Symantec's July 2017 Intelligence Report.
What Does a Botnet Look Like?
We know that a botnet is a network of infected computers. However, the core components and actual botnet architecture are interesting to consider.
Architecture
There are two main botnet architectures:
- Client-server model: A client-server botnet typically uses a chat client (formerly IRC, but modern botnets have made use of Telegram and other encrypted messaging services), domain, or website to communicate with the network. The operator sends a message to the server, relaying it to clients, which execute the command. Though the botnet infrastructure differs from basic to very complex, a concentrated effort can disable a client-server botnet.
- Peer-to-Peer: A peer-to-peer (P2P) botnet tries to stop security programs and researchers identifying specific C2 servers by creating a decentralized network. A P2P network is more advanced, in some ways, than a client-server model. Furthermore, their architecture differs from how most envision. Instead of a single network of interconnected infected devices communicating via IP addresses, operators prefer to use zombie devices connected to nodes, in turn, connected to one another and the main communication server. The idea is that there are simply too many interconnected but separate nodes to take down simultaneously.
Command and Control
Command and Control (sometimes written C&C or C2) protocols come in various guises:
- Telnet: Telnet botnets are relatively simple, using a script to scan IP ranges for default telnet and SSH server logins to add vulnerable devices to add bots.
- IRC: IRC networks offer an extremely low bandwidth communication method for the C2 protocol. The ability to rapidly switch channels grants some additional security for botnet operators, but also means infected clients are easily cut off from the botnet if they do not receive updated channel information. IRC traffic is relatively easy to examine and isolate, meaning many operators have moved away from this method.
- Domains: Some large botnets use domains rather than a messaging client for control. Infected devices access a specific domain serving a list of control commands, easily allowing for changes and updates on the fly. The downside is the huge bandwidth requirement for large botnets, as well as the relative ease with which suspected control domains are shut down. Some operators use so-called bulletproof hosting to operate outside the jurisdiction of countries with strict criminal internet law.
- P2P: A P2P protocol usually implements digital signing using asymmetric encryption (one public and one private key). Meaning while the operator holds the private key, it is extremely difficult (essentially impossible) for anyone else to issue different commands to the botnet. Similarly, the lack of a single defined C2 server makes attacking and destroying a P2P botnet more difficult than its counterparts.
- Others: Over the years, we have seen botnet operators use some interesting Command and Control channels. Ones that instantly come to mind are social media channels, such as the Android Twitoor botnet, controlled via Twitter, or the Mac.Backdoor.iWorm that exploited the Minecraft server list subreddit to retrieve IP addresses for its network. Instagram isn't safe, either. In 2017, Turla, a cyber-espionage group with close links to Russian intelligence, was using comments on Britney Spears Instagram photos to store the location of a malware distribution C2 server.
Zombies
The final piece of the botnet puzzle is the infected devices (i.e. the zombies).
Botnet operators purposefully scan for and infect vulnerable devices to expand their operating power. We listed the main botnet uses above. All of these functions require computing power. Furthermore, botnet operators aren't always friendly with one another, turning the power of their infected machines on one another.
The vast majority of the time zombie device owners are unaware of their role in the botnet. At times, however, botnet malware acts as a conduit for other malware variants.
This ESET video gives a nice explanation as to how botnets expand:
Types of Devices
Networked devices are coming online at a startling rate. And botnets aren't only on the hunt for a PC or Mac. As you'll read more of in the following section, Internet of Things devices are just as susceptible (if not more) to botnet malware variants. Especially if they are sought out because of their appalling security.
Smartphones and tablets aren't secure, either. Android has seen several botnets throughout the past few years. Android is an easy target: it is open source, has multiple operating system versions, and numerous vulnerabilities at any one time. Don't rejoice so quickly, iOS users. There have been a couple of malware variants targeting Apple mobile devices, although usually limited to jailbroken iPhones with security vulnerabilities.
Another core botnet device target is a vulnerable router. Routers running old and insecure firmware are easy targets for botnets, and many owners will not realize that their internet portal carries an infection. Similarly, a simply staggering amount of internet users fail to change the default settings on their routers after installation. Like IoT devices, this allows malware to propagate at a staggering rate, with little resistance met in the infection of thousands of devices.
Taking Down a Botnet
Taking down a botnet isn't an easy task, for a number of reasons. Sometimes the botnet architecture allows an operator to rebuild quickly. At other times, the botnet is simply too large to take down in one fell swoop. The majority of botnet takedowns require coordination between security researchers, government agencies, and other hackers, sometimes relying on tips or unexpected backdoors.
A major problem facing security researchers is the relative ease with which copycat operators start operations using the same malware.
GameOver Zeus
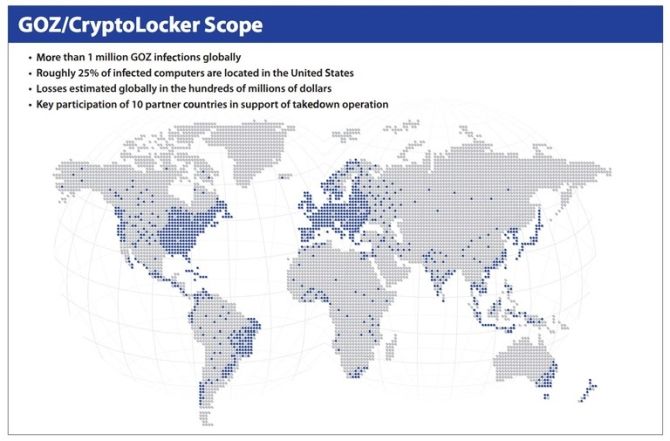
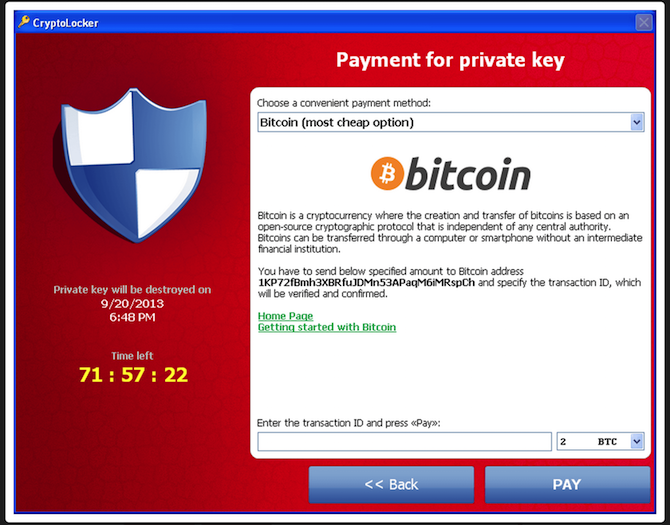
I'm going to use the GameOver Zeus (GOZ) botnet as a takedown example. GOZ was one of the biggest recent botnets, thought to have over one million infected devices at its peak. The botnet's primary use was monetary theft (distributing the CryptoLocker ransomware) and spam mail and, using a sophisticated peer-to-peer domain generating algorithm, appeared to be unstoppable.
A domain generating algorithm allows the botnet to pre-generate long lists of domains for use as a "rendezvous points" for the botnet malware. Multiple rendezvous points make stopping the spread almost impossible, as only the operators know the list of domains.
In 2014, a team of security researchers, working in conjunction with the FBI and other international agencies, finally forced GameOver Zeus offline, in Operation Tovar. It wasn't easy. After noticing domain registration sequences, the team registered some 150,000 domains in the six months leading up to the start of the operation. This was to block any future domain registration from the botnet operators.
Next, several ISPs gave the operation control of GOZ's proxy nodes, used by the botnet operators to communicate between the command and control servers and the actual botnet. Elliot Peterson, the lead FBI investigator on Operation Tovar, said: "We were able to convince the bots that we were good to talk to, but all of the peers and proxies and supernodes controlled by the bad guys were bad to talk to and should be ignored."
Botnet owner Evgeniy Bogachev (online alias Slavik) realized that the takedown was in place after one hour, and attempted to fight back for another four or five hours before "conceding" defeat.
In the aftermath, the researchers were able to crack the notorious CryptoLocker ransomware encryption, creating free decryption tools for victims.
IoT Botnets Are Different
The measures to combat GameOver Zeus were extensive but necessary. It illustrates that the sheer power of a cleverly crafted botnet demands a global approach to mitigation, requiring "innovative legal and technical tactics with traditional law enforcement tools" as well as "strong working relationships with private industry experts and law enforcement counterparts in more than 10 countries around the world."
But not all botnets are the same. As one botnet meets its end, another operator is learning from the destruction.
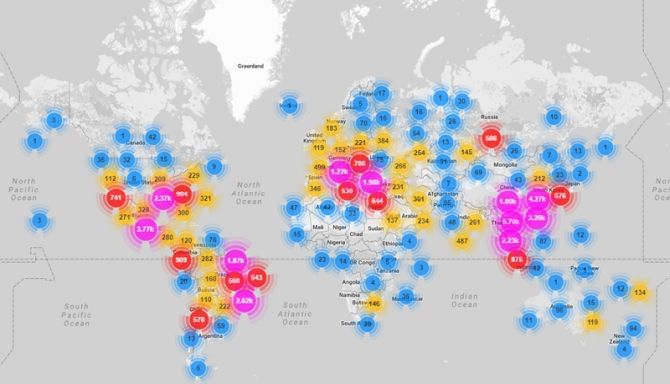
In 2016, the biggest and baddest botnet was Mirai. Before its partial takedown, the Internet of Things-based Mirai botnet hit several prominent targets with staggering DDoS attacks. One such attack hit security researcher Brian Krebs' blog with 620Gbps, eventually forcing Krebs' DDoS protection to drop him as a client. Another attack in the following days hit French cloud-hosting provider OVH with 1.2Tbps in the largest attack ever seen. The below image illustrates how many countries Mirai hit.
Though Mirai wasn't even close to being the largest botnet ever seen, it produced the largest attacks. Mirai made devastating use of the swathes of ridiculously insecure IoT devices, using a list of 62 insecure default passwords to amass devices (admin/admin was top of the list, go figure).
Security researcher Marcus Hutchins (aka MalwareTech) explains that part of the reason for Mirai's massive power is that the majority of IoT devices sit there, doing nothing until requested. That means they are almost always online, and almost always have network resources to share. A traditional botnet operator would analyze their peak power periods and time attacks accordingly. IoT botnets, not so much.
So, as more poorly configured IoT devices come online, the chance for exploitation grows.
Staying Safe
We've learned about what a botnet does, how they grow, and more. But how do you stop your device becoming part of one? Well, the first answer is simple: update your system. Regular updates patch vulnerable holes in your operating system, in turn cutting the avenues for exploitation.
The second is download and update an antivirus program, and an antimalware program, too. There are numerous free antivirus suites out there that offer excellent, low impact protection. Invest in an antimalware program, like Malwarebytes. A Malwarebytes Premium subscription will set you back $24.95 for the year, giving you real-time malware protection. Well worth the investment, in my opinion.
Finally, grab some additional browser security. Drive-by exploit kits are a nuisance, but they are easily avoidable when you use a script-blocking extension like uBlock Origin.
Was your computer part of a botnet? How did you realize? Did you find out which infection was using your device? Let us know your experiences below!