The term DDoS whistles past whenever cyber-activism rears up its head en-masse. These kind of attacks make international headlines because of multiple reasons. The issues that jumpstart those DDoS attacks are often controversial or highly political. Since a large number of regular users are affected by the attacks, it's an issue that plays with the people.
Perhaps most importantly, a lot of people don't know what constitutes a DDoS attack. Despite its rising frequency, looking at the paper's headlines, DDoS attacks can be anything from digital vandalism to fully-fledged cyber-terrorism.
So what does a DDoS, or Distributed Denial of Service attack entail? How does it work, and how does it affect the intended target and its users? These are important questions, and this is what we're going to be focusing on in this instance of MakeUseOf Explains.
Denial Of Service
Before we tackle the issue of DDoS, or Distributed Denial of Service attacks, let's look at the larger group of Denial of Service (DoS) issues.
Denial of Service is a broad issue. Simply put, a website experiences DoS issues when it is no longer able to service its regular users. When too many people flock to Twitter, the Fail Whale pops up, indicating that the website has reached and passed maximum capacity. In essence, Twitter experiences DoS.
Most of the time, these issues are instigated without malicious intent. A large website links to a small website, which isn't built for the same level of traffic.
A Denial of Service Attack, then, indicates malicious intent. The attacker spends effort trying to instigate DoS issues. The techniques used here vary wildly - a DoS attack refers to the intended result of the attack, not the way it is executed. Generally, by hogging the system's resources, it can render the system unavailable to its regular users, ultimately even crashing the system and taking it down entirely.
Distributed (DDoS) Attacks
The difference between Distributed Denial of Service (DDoS) and regular DoS attacks is the scope of the attack. Where a DoS is carried out by a single attacker using a single system, a Distributed attack is carried out across multiple attacking systems.
Voluntarily Participating Agents
Sometimes multiple attackers join up, each willingly participating in the attack. Software that's used to stress-test systems, or software specifically designed to wreck havoc is installed on each system. For the attack to work, it needs to be coordinated. Coordinated through IRC chat rooms, forums, or even Twitter feeds, the attackers throw themselves en-masse on a single target, trying to flood it with activity to disrupt usage, or crash the system.
When PayPal, Visa and MasterCard started boycotting WikiLeaks near the end of 2010, WikiLeaks supporters carried out a coordinated DDoS, temporarily taking down the homepage of multiple websites. Similar attacks have targeted other banks and even national security agencies.
What's important to remember here is that the website storefront is flooded and crashed, whereas the bank's and security agencies' internal networks are usually left untouched, as explained in XKCD comic 932, shown above.
Zombie Systems Or Botnets
A Distributed Denial of Service attack requires multiple attack systems. It doesn't usually require multiple attackers. Often, large-scale attacks are not carried out through the attacker's own computer, but through a large number of infected zombie systems. Attackers can abuse a zero day vulnerability and use a worm or a trojan horse to gain control over a large number of compromised systems. The attacker then uses these infected systems to mount an attack against its target. Infected systems used this way are often called bots or zombie systems. A collection of bots is called a botnet.
Although the website targeted by the DDoS attack is usually portrayed as the sole victim, users with infected systems that are part of the botnet are similarly affected. Not only are their computers used in illicit attacks, their computer's and Internet connection's resources are consumed by the botnet.
Attack Types
As mentioned before, a DDoS attack only states the intent of the attack - robbing a system of its resources and making it unable to perform its intended service. There are several ways to achieve this goal. The attacker can hog the system's resources, or even push the system over the brink and make it crash. In severe cases, a Permanent Denial of Service (PDoS) attack, also known as phlashing, wreaks so much havoc on its target that hardware components need to be entirely replaced before being able to recommence normal operation.
We'll take a look at two important attack methods. This list is by no means comprehensive. A bigger list can be found on Wikipedia's DoS article.
ICMP Flood
The ICMP (or Internet Control Message Protocol, but that's less important) is an integral part of the Internet Protocol. An ICMP flood attack is carried out by bombarding a network with network packages, using up resources and crashing it. One type of attack is a Ping Flood, a simple DoS attack where the attacker effectively overwhelms its target with 'ping' packets. The idea here is that the attacker's bandwidth is larger than its target's.
A Smurf attack is a smarter way of ICMP flooding. Some networks let network clients broadcast messages to all other clients by sending it to a single broadcast address. A Smurf attack targets this broadcast address and makes its packages look as if they came from within the target. The target broadcasts these packages to all network clients, effectively serving as an amplifier for the attack.
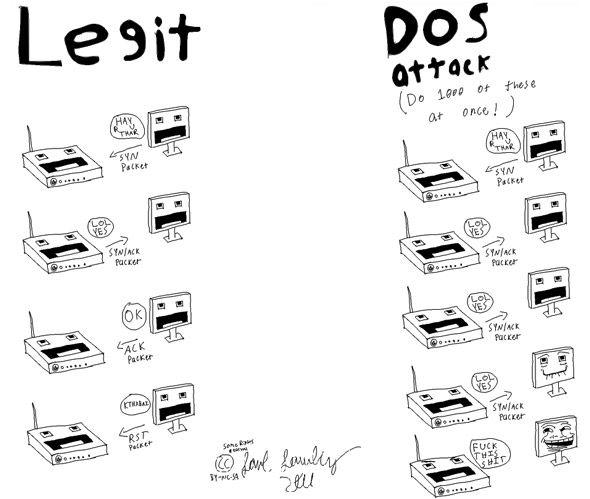
(S)SYN Flood
A (S)SYN Flood relies on the essential operating principles of network communication. During normal operations, a client starts communication by sending the server a TCP/SYN package, essentially telling the server it wishes to communicate. The server, upon receiving the package, creates a connection to communicate with the client and sends back acknowledgement and a reference to the communication channel.
The client sends back an acknowledgement in turn, and starts its communication with the server. However, if the client does not answer with that second acknowledgement, the server asumes it didn't arrive properly (as happens reasonably often) and resends it.
A (S)SYN Flood abuses this mechanic by sending countless of TCP/SYN packages (each with a different, fake origination specified). Each package prompts the server to create a connection and keep sending acknowledgements. Before long, the server has used up its own resources with half-open connections. This principle is illustrated in the comic above, drawn and posted by Redditor verisimilarity.
As explained above, DDoS attacks are varied but have a singular purpose: (temporarily) keeping authentic users from using the target system. Does this agree with your initial ideas on DDoS attacks? Let us know in the comments section.
Image credit: Shutterstock