Did you ever get an email and wondered where it came from, or who really sent it? Surprisingly, a lot of that information can be obtained from the metadata in the email header.
The header is a part of every email that most people never even see. It contains a ton of data that seems like gobbledygook to the average user. Besides, most email clients hide the metadata, often making it difficult to access.
Since there are so many email clients out there, both desktop and web-based, showing how to retrieve email headers could end up being a small book. Hence, we'll focus on how to view the email header in Gmail, and what you can learn from it.
What Is an Email Header?
An email header is a collection of metadata that documents the path by which the email got to you. You may find a deluge of information in the header or just the basics.
There is a standard for what information should be included in a header, but not really a limit to what information an email server might put into the header.
If you're curious about what a standard for an email protocol looks like, check out RFC 5321 - Simple Mail Transfer Protocol. It's a bit hard on the head, especially if you don't need to know this stuff.
How to View the Email Header in Gmail
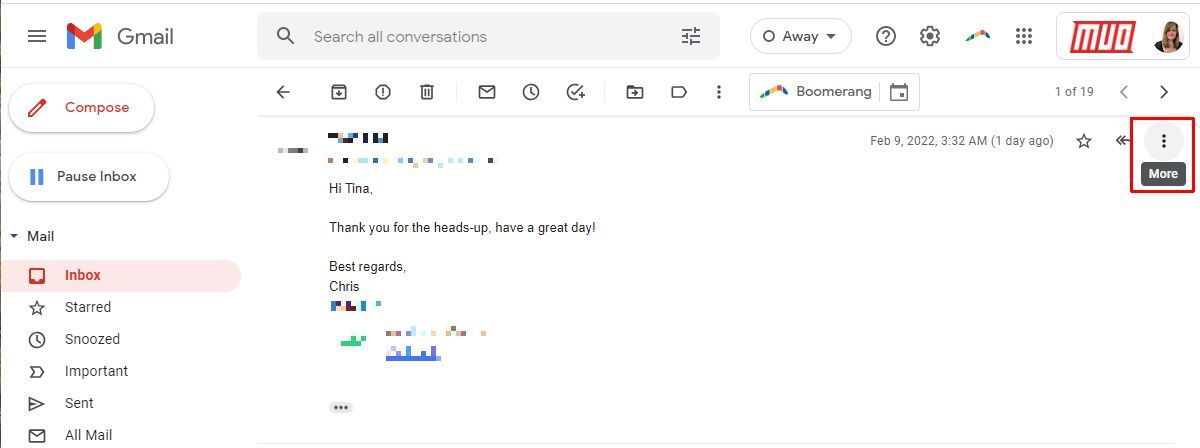
Once you have an email message open in Gmail, click on the three-dot icon in the top-right hand corner of the message to expand the More menu. Click on Show original to see the raw email message with its full contents and header revealed.
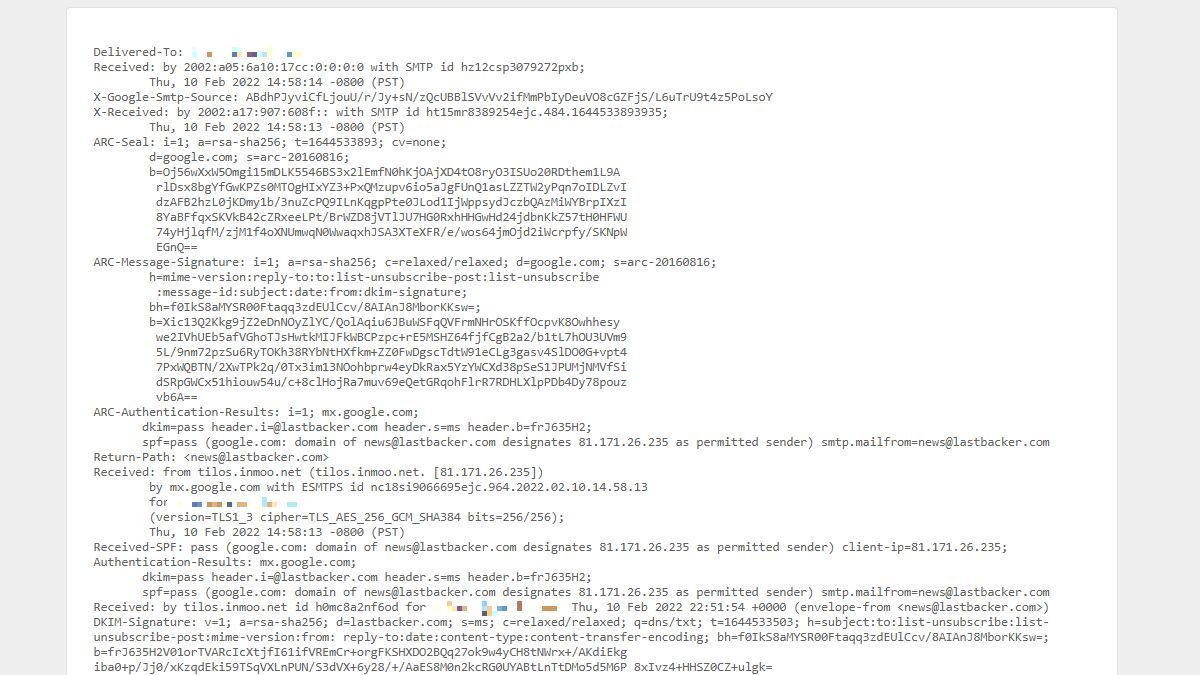
A new window or tab will open, and you'll see a plain text version of your email with the header at the top, of course. The content of the header will look something like this:
That's nice, but what does it mean?
How Is an Email Header Created?
By knowing how the header is created along the path an email travels, you will develop keener insight into what a header's data means. Let's look at the parts as they are added, and what the most important parts mean.
On the Sender's Computer
Part of the header is created when the sender creates the email to send to the recipient. This will include such information as when the email was composed, who composed it, the subject line, and the email's recipient.
This is the part of the header that you are the most familiar to seeing as the Date:, From:, To:, and Subject: lines on the top of your email.
On the Sender's Email Service
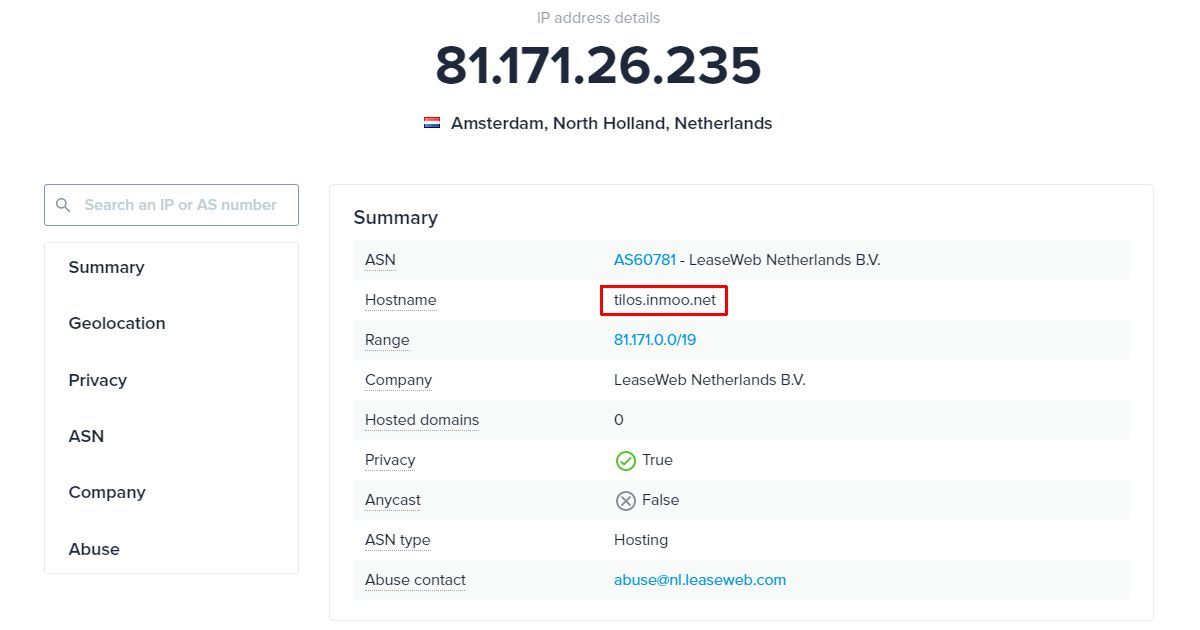
More information is added to the header once the email is actually sent. This is provided by the email service that the sender is using. In this case, the sender is using a hosted email service, so the IP address shown is an address that is internal to the service provider's network.
Performing a WHOIS search on it won't provide any useful information. What we can do is perform a Google search on the server name, in this case tilos.inmoo.net. With a bit of digging, we can find both the server name and IP address on bgp.tools.
Further inspection of the IP address reveals that the sender was using LeaseWeb, a Dutch cloud computing and web services company.
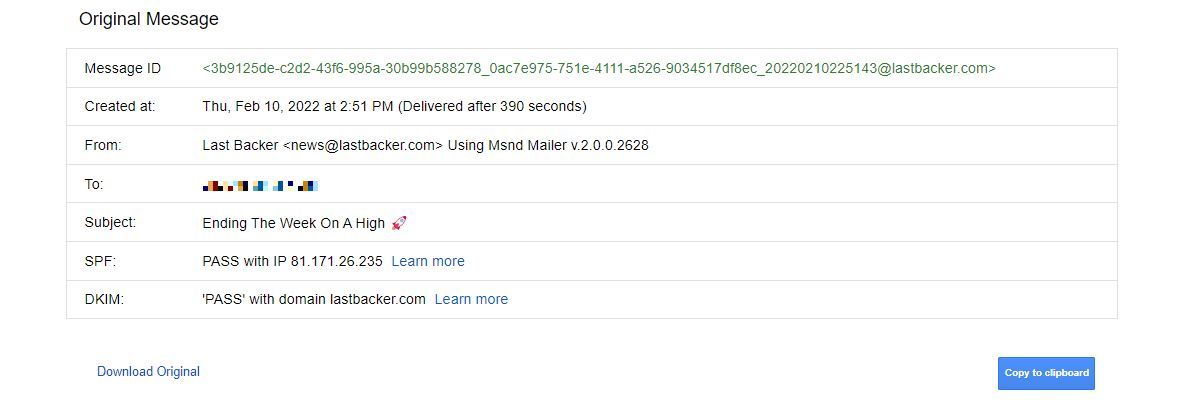
In addition to the sender's IP address, the email header also reveals the time the email was sent by the sender's email service (Thu, 10 Feb 2022 14:58:13 -0800 (PST)), and the Message-ID for that particular message as added by the email service.
Along the Way to the Recipient's Email Service
From there, the email may take any number of routes to end up at the recipient's email service. This can be added to the header to show the "hops" the email had to make to get to you.
These hops start at the server that most recently handled the email and go back to the server that originally handled it, in reverse chronological order. In our example, the first hop takes the email from the sender to Google, from where it takes two more hops until it arrives at its final destination.
Final Hop:
Received: from tilos.inmoo.net (tilos.inmoo.net. [81.171.26.235])
by mx.google.com with ESMTPS id nc18si9066695ejc.964.2022.02.10.14.58.13
for <xxx@gmail.com>
(version=TLS1_3 cipher=TLS_AES_256_GCM_SHA384 bits=256/256);
Thu, 10 Feb 2022 14:58:13 -0800 (PST)
Received-SPF: pass (google.com: domain of news@lastbacker.com designates 81.171.26.235 as permitted sender) client-ip=81.171.26.235;
Authentication-Results: mx.google.com;
dkim=pass header.i=@lastbacker.com header.s=ms header.b=frJ635H2;
spf=pass (google.com: domain of news@lastbacker.com designates 81.171.26.235 as permitted sender) smtp.mailfrom=news@lastbacker.com
This is the hop that takes it from LeaseWeb's server to the recipient's email server. We can tell that it was received by mx.google.com, so the recipient has their email service with Google.
Here, it is good to note the line Received-SPF: SPF, or Sender Policy Framework, is a standard by which a sender's email server can declare itself to be the legitimate sender of the email.
In this case, the qualifier is pass, which means that the IP address was authorized to send from the domain. Had it registered as fail, it would have been rejected by Gmail's servers. If it were softfail, Gmail would have accepted it, but flagged it as possibly not being from whom it says it is from.
Previous Hops:
The final hop can be preceded by one or more hops. The time stamps for each reveal how long it took each server to pass on the message. This won't tell you much, unless you're a network engineer.
In theory, you could calculate roughly how far apart are the two servers.
At the Recipient's Email Server
Once it gets to the recipient's email service, more information is added to the header. This might include the recipient's email services servers received it and when, what email server the message was received from, the intended recipient's email address, and the sender's stated, "reply to" email address.
Back in the Final Hop, we saw that the recipient's email service was with Google. Most importantly, we can tell by the Return-Path: whether the email to reply to and the email of the sender is the same. If it is, it also tells us that there is a good chance this email is legitimate.
Other Information From Other Headers
This particular email header is limited in its information because a hosted email service is being used. If the sender were using their own email server, we might be able to gain a little more information.
We might be able to determine exactly what mail client they are using. Or we could perform a WHOIS on the sender's IP address and get an approximate location of the sender.
We could also perform a simple web search on the sender's domain and see if there is a website for them. Based on that website, we may be able to find out even more information about the sender.
You might conduct a web search on the email address itself, find the person online, and start doxing them. Though, we don't recommend that you do that.
Decoding Email Headers and Metadata
It can be overwhelming to decode email headers based on raw data alone. Fortunately, you can fall back on online tools to do the heavy lifting for you. And Gmail makes it easy to copy the entire header with the click of the button. Once you're viewing the original message (see above) with all its metadata, click the Copy to Clipboard button, then head to one of the sites below.
- Google Admin Toolbox Messageheader: This site will break down the basics and the path the email took from sender to receiver.
- MX Toolbox: This breaks down the header in more detail and reveals delays, authentication issues, and each hop the email made.
- WhatIsMyIP: If you're curious where in the world the email came from, go straight here. This service performs a WHOIS lookup.
- Mail Header: On Mail Header, you'll get a detailed Message Transfer Agent (MTA) analysis, a visual representation of the route your email took across the globe, complete with hop and spam scoring details.
Everything to Learn From an Email Header
All electronic communications leave footprints. Some are larger and easier to follow. Some are obscured by web filters and proxy servers. Either way, what is left behind tells us something about the person that created them.
From that metadata, we might conduct further investigations to learn more about the people involved. Are they hiding something by using a VPN? Are they really from a legitimate business with a legitimate web presence? Is this someone I really want to go on a date with? What can ordinary people learn about me, let alone the NSA?
Take a look at your email headers and see what they say about you. If you find some header lines that don't make much sense, ask Google to help you decode them.