It feels like every time you sign up for a new service, you can choose to pick a username and password or just log in with Facebook or Twitter. Logging in with your Google account is often an option, too. It's fast and it's easy. But should you do it?
How Does It Work?
Logging in using your social account uses a protocol called OAuth, which (in a nutshell) allows one app or service (the requester, or service you're signing up for) to connect to another (the service provider, or existing network you're using to sign up) and act on your behalf. This is done by issuing "tokens" to the requesting app. These tokens function a bit like your username and password, as they give the requesting app access to a password-protected service (e.g., Facebook).
The important thing here is that your actual username and password are never communicated between the apps, and that the requesting app only gets access to a limited part of your password-protected account.
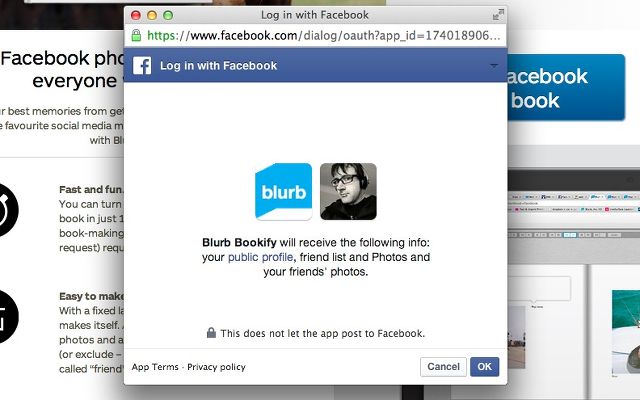
Let's look at a quick example. Say you're using Blurb to turn your Facebook photos into a book. You go to Blurb (the requester) and tell it you want to print photos from Facebook. Blurb directs you back to Facebook (the service provider), where you enter your sign-in credentials (sent directly to Facebook, not Blurb) and tell Facebook that you give Blurb permission to access your photos. Now Blurb can download those photos so they can be printed. If Blurb tries to access your timeline, it will be denied, because the token that it has only gives it access to your photos and public profile.
OAuth never shares your username or password with the requesting app, the idea being that keeping your username and password a secret keeps them secure. And to stop a requesting app or service from accessing your account, all you have to do is click "revoke access," instead of changing your password.
Is It Safe?
Okay, so the process seems pretty straightforward so far. But how safe is it? Should we be worried about the security of OAuth sites?
From a security standpoint, OAuth looks pretty good. A worst-case scenario still doesn't result in the revelation of your social passwords. And the ability to instantly revoke access to any app that has a token means that even if a website gets hacked and some nefarious characters get their hands on all of the token data, you can just hit the revoke access button and they won't have access to your social site.
The fact that you only share access to a specific subset of the data on your social site is also quite appealing—if someone hacks Snapfish and gets access to your Facebook photos, you shouldn't be too worried (you are taking care with the photos you post, right?).
Despite the recent dramatized discovery of a security flaw in OAuth, the system is a pretty good one.
However, there's more to online safety than just encryption and tokens. One of the best ways to make sure that you're safe online is to use good password practices. And OAuth helps a lot with that. How? By being able to sign in using Twitter or Google, you don't have to create yet another password that you have to remember. If you have a very secure Facebook password, you can use that to access a number of things without using the exact same password for more sites.
This is a distinct advantage of OAuth—and the fact that you limit the number of websites that have your passwords is a big plus.
It's also important to mention that sites accessing your social profiles can't take any major actions—they aren't able to delete your account, change your password, or make any other big changes. Which is reassuring.
What risks are you taking?
Unfortunately, nothing is simple when it comes to online security and safety. There are some risks of using OAuth, mostly related to privacy.
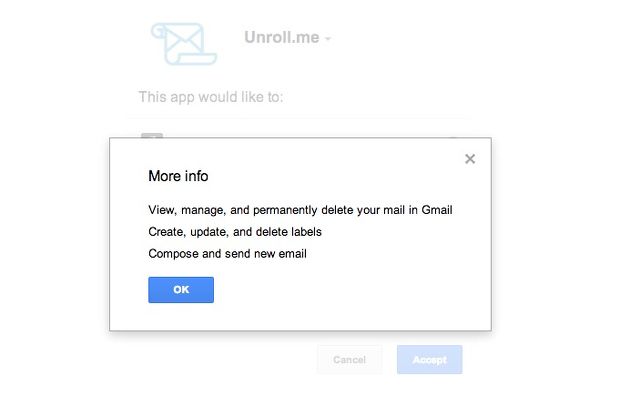
For example, how often do you take the time to really look at the permissions that you're giving when you use Facebook Connect? While apps should only request access to the information that they need to serve you better, they often ask for a lot more—your timeline, your friends' information, and the ability to post, for example.
Sometimes this is a good thing—you might want to integrate Twitter into your contacts app or a news reader. Or you might want to post your workout results from RunKeeper or MapMyFitness. But there's nothing in the permissions that will keep the app or service from posting whatever they want. There's no "post survey results only" option. You just have to trust that the app will only post things you want or tell it to, and not ads.
And you might be giving away more information than you bargained for. Who cares if your favorite store sees what you're posting on Facebook, right? Well, they might be getting more information than you imagined.
For example, at a 2012 conference, a Japanese catalog company talked about how it used information on a user's Facebook profile to infer things "about a customer's "life stage" (whether they're married or unmarried, pregnant, dieting, planning a party, etc.) "household" (if they have a child, an aging parent, a pet, a condo, etc.) and "personality" (are they into volunteering, fortune-telling, food, traveling, sports, running, etc?)."
A member of the marketing team stated that the team "can learn the life background of our customers—their lifestyle and psychology. We can then target our catalogs accordingly. And we can predict when someone needs a product based on what they say on social media."
Didn't think you were giving away that much information, did you?
Of course, you have full control over what you're sharing with a company using social logins and how much they can post for you—but only if you take the time to read the permissions that they're asking for. And not give access to things that you'd rather keep private. But that's not always easy, because some apps and services are now employing Facebook-or-Twitter-only sign-in, meaning that if you don't agree to their permissions, you don't get to use the service.
Takeaway Lessons: What Should You Do?
As with most things, there are two sides to the story of logging in using social accounts. It's generally quite safe, and you actually do have quite a bit of control over how much information you share.
On the other hand, you might be giving away a lot of control if you're not careful. So what should you do about it?
- Read permission requests before granting them.
This is an important one, and it's only going to get more important as web services become more integrated. If you don't want an app harvesting data about your Facebook friends, don't allow it access to Facebook.
- Review your app permissions frequently.
On Facebook, go to the Apps tab on the Settings screen. On Twitter, go to the Apps tab in Settings, too. Google's a bit trickier: go to accounts.google.com, then click on Security, then View All under Account Permissions. Look at which apps have access to your data, and revoke access for any that you don't use anymore. And if you see an app that has more permissions than it should, consider revoking access and seeing if you can log into that service with a traditional username and password.
To speed up the process, you can use MyPermissions, which helps you manage your permissions across Facebook, Twitter, Google, Yahoo, LinkedIn, Foursquare, Instagram, Dropbox, and more.
- Skip permissions and set allowable audiences for sharing.
If an app asks permission to share on your behalf via a social service, you might have the opportunity to not give that permission (you'll see this on Facebook when you see a "Skip" button). If that's an option, use it! You can also set the audience for the allowable sharing—for example, you can share to all of your friends, a custom audience, or only yourself.
- Treat permissions requests differently based on accounts.
What do you post on Instagram? What do you post on Twitter? A request to read your Foursquare posts might be a lot less scary than granting "Compose and send new mail" privileges to your Gmail account.
- Change your passwords on a regular basis.
When you change your passwords, a number of OAuth tokens will be immediately invalidated, requiring you to re-sign in and re-approve the tokens. As far as I've been able to figure out, Gmail and Facebook invalidate tokens when you change your password, but Twitter and Google+ don't. For these other services, you'll need to revoke access and then re-issue the permissions.
Conclusion: Convenience For A Price
Logging into sites and services with your social credentials adds a lot of convenience, and even a bit of security. But it can be risky, both from a privacy and—to a lesser degree—security standpoint. But if you practice the five safety tips above, you should only be giving the permissions you intend to.
How often do you use your social login information on another site? Do you feel safe doing it? Do you read and re-check permissions on a regular basis? Share your thoughts below!
Image credits: Marc Falardeau via Flickr, Rob Pongsajapan via Flickr, Iván Melenchón Serrano via MorgueFile