When do people not like a puppy? When they know it's not a puppy, but a browser exploit aimed at stealing their vital information. The POODLE (Padding Oracle On Downgraded Legacy Encryption) we're talking about is a serious security attack.
As a security exploit, it can affect all web browsers, and therefore any one of us. Let's find out what POODLE is, what it does, and what you can do to prevent it from biting you.
Background Info
To understand POODLE, you need to know a bit about SSL and TLS. They are two cryptographic protocols that were developed to help protect your important web communications. When you go to a website and you see HTTPS:// before the web address, you're using SSL/TLS. SSL (Secure Socket Layer) and TLS (Transport Security Layer) are two very different protocols, but most people just lump them together and call them SSL. SSL was actually replaced by the TLS protocol around ten years ago as the de facto standard for cryptography, yet SSL is still in wide use. That's what makes POODLE dangerous.
When you visit a website, the computer that serves you the page (web server) is capable of several levels of cryptography security, anywhere from TLSv1.2, the most recent and secure protocol, to SSLv3, the older and less secure protocol. This allows your browser and the web server to be able to connect with the same protocol so they can talk securely. This is the fundamental way that web browsers and servers try to prevent man-in-the-middle attacks, like POODLE.
What Does POODLE Do?
POODLE tries to force the connection between your web browser and the server to downgrade to SSLv3. If it does that, the attacker can get the plain text information from the communication. That means that they can access cookies which are often used to store information, some of which could be personal and sensitive in nature. What the attacker does with that information is anybody's guess, but it is never anything good.
On the upside, the POODLE attack is not the easiest way for an attacker to get your info. It may take hundreds, even thousands, of tries to get the POODLE attack to work on someone. So it is something to be concerned about, however it isn't necessarily as bad as the recent Heartbleed issue.
How Can I Protect Myself from POODLE?
Fortunately, it's a fairly easy thing to do. First things first, let's see if you are POODLE vulnerable. Simply go to the POODLETest.com website. If you see a poodle, you have some cleaning up to do. If you see the Springfield Terrier, your browser is good to go. For those that are more tech savvy, check out Qualys SSL Labs' SSL Client Test. It provides more in-depth details.
The underlying principle is to disable SSLv3 support in your web browser. If it's disabled, POODLE can NOT downgrade your browser to it. Let's look at how to do this in Chrome, Internet Explorer, and Firefox.
Be aware, many web sites still want to use SSLv3. If you disable it, those sites might not work as well for you as they once did. It wouldn't hurt to send that company a nice e-mail with a link to this article so they are aware of the issue. Hopefully, they will upgrade to TLS and all will be good again.
Chrome
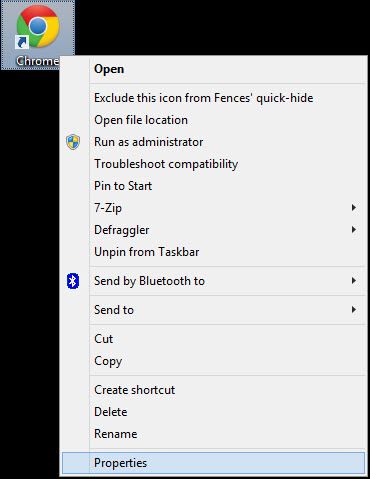
Find the shortcut that you use to launch Chrome. Right-click on it and then click on Properties.
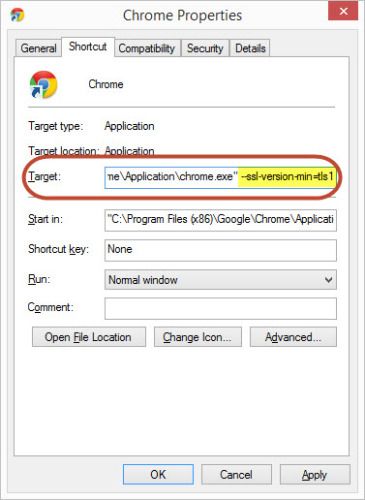
When the Properties window opens, find the field named Target. There should be a long path to where the Chrome file is located. It should look like: "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" or "C:\Program Files\Google\Chrome\Application\chrome.exe".
Click just after the last quotation mark and hit your space bar to create a space. Now type in the following:
––ssl-version-min=tls1
You could copy and paste that from here, too. What that tells Chrome to do is to use TLSv1 as the lowest version of security for your Chrome browser. Click on the Apply button at the bottom of the window, and the next time you open Chrome, it will be POODLE proofed.
Internet Explorer
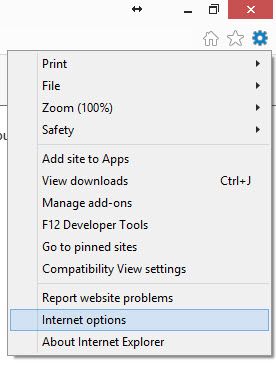
Open your Internet Explorer browser and click on the Settings icon. It's the one that looks like a gear. Now click on Internet options. A new window will open.
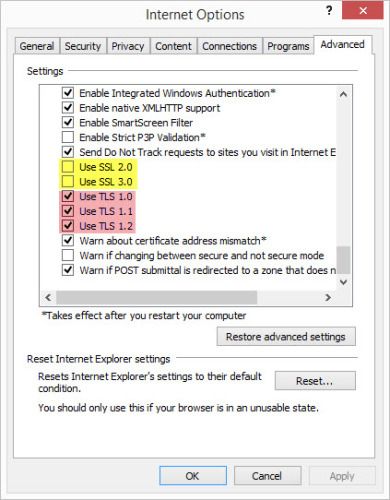
On the far right side, you will see a tab labelled Advanced - click on it. In the Settings area, scroll down until you see the options Use SSL 2.0 and Use SSL 3.0.
If there is a checkmark in those two boxes, uncheck them by clicking on them. Make sure that the boxes labelled Use TLS 1.o, Use TLS 1.1 and Use TLS 1.2 are checked. (If you don't have all three of these TLS boxes, you should update your Internet Explorer.) Then click on the Apply button, and the OK button. Your Internet Explorer is now POODLE proofed.
Firefox
If you're a fan of Firefox, here's how to help the fox outsmart the POODLE. Simply go to Firefox's SSL Version Control 0.2 Add-On page, then download and install the SSL Version Control 0.2 add-on. It's that easy.
Firefox has also announced that it's next version, Firefox 34, will disable support for SSLv3. However, that version won't be released until sometime in November, according to their website.
POODLE Will Be Pooched
Once the majority of people POODLE-proof their browsers and the majority of web servers stop using SSLv3, POODLE will no longer be a problem. There is also a tool known as TLS_FALLBACK_SCSV that has been developed that web servers and browser programmers can implement to help. Unfortunately, that tool requires both the web server and the browser to have it. That will take awhile for everyone to implement. Only then SSLv3 will go by the wayside, as it should have a decade ago. Spread the word and make the Web a safer place to be.
Image Credits: Angry Poodle, HTTPS Vector Image via Shutterstock.