Email remains a prominent attack vector for hackers, cybercriminals, snoopers, and other online miscreants. As such, it's vital that you know how to spot an unsafe email attachment.
If you're not sure where to start, keep reading. We're going to explain several red flags that'll help you identify potentially dangerous files in your inbox.
1. Dangerous File Extensions
Unfortunately, there are several file extensions which could potentially run code on your computer and thus install malware.
As you'd expect, hackers don't make them easy to spot. Often, dangerous file extensions are concealed in ZIP files and RAR archives. If you see either of those extensions in an attachment that doesn't come from a recognized contact, you should treat it with suspicion.
The most dangerous file extension is EXE. They are Windows executable files which are particularly hazardous due to their ability to disable your antivirus app.
Other frequently used extensions to watch out for include:
- JAR: They can take advantage of Java runtime insecurities.
- BAT: Contains a list of commands that run in MS-DOS.
- PSC1: A PowerShell script with commands.
- VB and VBS: A Visual Basic script with embedded code.
- MSI: Another type of Windows installer.
- CMD: Similar to BAT files.
- REG: Windows registry files.
- WSF: A Windows Script File that permits mixed scripting languages.
You also need to keep an eye on Microsoft Office files with macros (such as DOCM, XLSM, and PPTM). Macros can be harmful but are also commonplace---especially in business documents. You'll have to exercise your own judgment.
2. Encrypted Archive Files
As we just alluded to, archive files (such as ZIP, RAR, and 7Z) can conceal malware.
The problem is especially acute for encrypted archive files---i.e., those that require a password in order to extract their contents. Because they are encrypted, your email provider's native antivirus scanner cannot see what they contain, and thus can't flag it as malware.
The counterargument is that encrypted archive files are an excellent way to send sensitive data to a recipient; they are widely used for that purpose. Again, you'll have to exercise your own judgment and make a decision about whether the file is safe.
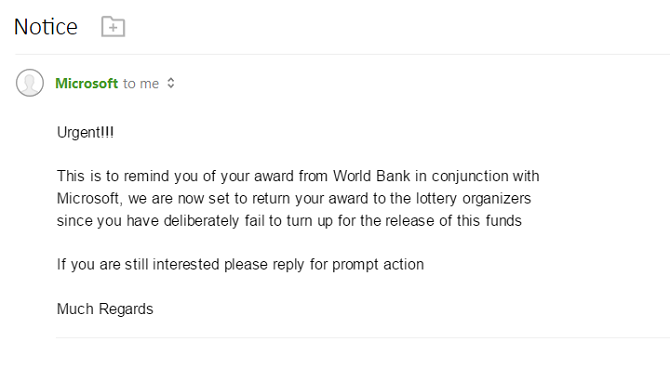
3. Who Sent the Email?
It goes without saying that an email from a nonsensical address (for example, e34vcs@hotmail.com) is almost certainly something you shouldn't open. Instead, immediately flag it as spam and remove it from your inbox.
That part is easy, but the situation can quickly become more complex.
Malicious actors are experts in making email addresses look like they are from an official source when in practice, they are phishing attacks. For instance, perhaps your bank's email address is customers@bigbank.com; a hacker might send an email from customers@bigbank.co instead. That's easy to overlook when you're scanning through your inbox in a hurry.
There's also been an uptick in email spoofing in recent years. When spoofing, an attacker tricks the email server into thinking the email came from the address being spoofed. You'll even see the person's real address and profile picture in the sender field.
In theory, you can spot spoofed emails by investigating the email's source code, but it's way beyond the abilities of most users. If you're not expecting an email from the sender and the attached file ticks some of the other boxes we're discussing, it's probably malware.
Finally, remember that an attachment could be malicious even if you know the sender and the email is not spoofed. If the sender's own machine is infected, it could send emails to their contact list without their knowledge.
4. Strange Filenames
In the same way that you should treat random email addresses with extreme distrust, so too should you be wary of attachments with filenames composed of random strings of characters.
People don't save documents with a 20-character alphanumeric code as its name, and your computer would never prompt you to do so.
Similarly, names like "freemoney" or "greatopportunity" from an unknown sender are likely to contain malware and should immediately ring alarm bells.
5. Study the Contents of the Email
The text of the email can offer some clues about whether the message---and thus any attachment---is trustworthy.
Bots write many of the spam emails, spoofed emails, and phishing emails that you receive. They often have lousy formatting and spelling errors.
There are other little giveaways, too. For example, perhaps an email that's purportedly from your best friend refers to you by your full name rather than your nickname. Or maybe it uses formal language and other syntax that you know the person in question would never use.
You should also be suspicious of an email that asks you to download and run its attachment. These emails are often made to appear as if they come from companies like FedEx and DHL; they claim that you can track your package via the download. Given that we live in an age where online shopping is routine, it's easy to be duped, especially if you're expecting deliveries.
6. Use Your Antivirus Suite
If you're caught in two minds about the potential safety of an email attachment, make sure you always run it through your desktop antivirus app before running it on your machine.
Needless to say, if your antivirus program flags the file as suspicious, stop. Delete the file from your computer and don't redownload it. The worst course of action would be to click through the various malware warnings and proceed regardless.
Remember, even though antivirus apps may not be perfect (they occasionally flag false positives), they are infinitely more trustworthy than a suspicious email which claims its attachment is safe even if it gets flagged by a scan.
(Note: We've explained how to test your antivirus app's accuracy if you would like more information.)
Always Keep a Healthy Suspicion With Emails
Unfortunately, there's not a one-size-fits-all solution for spotting unsafe email attachments. Broadly speaking, however, the higher the number of red flags the attachment ticks, the more likely it is to be a hazardous file.
If you're unsure, reach out to the sender and ask for clarification. Most businesses and individuals will be only too happy to inform you about an attachment's veracity or otherwise. Ultimately, stick to the golden rule: if in doubt, don't proceed until you're confident that it's safe to do so.
You should also consider using a secure and encrypted email client for extra security.
If you'd like to learn more about staying safe while using email, take a few moments to learn how to stop spam email in Gmail and how to spot spear phishing email scams.