URL shorteners like bit.ly, goo.gl, tinyurl, and ow.ly are great for making it easier to share links; you don't have to paste a really long, ugly URL into a chat window or an email to help someone find their way to the page you want them to get to. But a recent study showed that this convenience could come with a significant cost to your security.
The Study
Over the course of 18 months, two researchers at Cornell Tech looked at the shortened URLs created by two different services: Microsoft OneDrive and Google Maps. Both services create shortened links for sharing webpages (OneDrive uses them to share access to documents, and Google Maps uses them to share directions or locations).
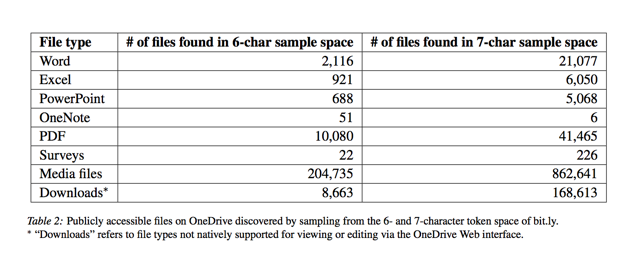
Because of the small number of characters used in these shortened links, the researchers were able to use a brute force attack to find shortened URLs that linked to actual documents. The researchers analyzed 100,000,000 bit.ly URLs with randomly chosen six-character tokens ( like "1maQ2JZ"). 42% of all of the tokens resolved to actual full URLs, and almost 19,500 of those led to OneDrive documents.
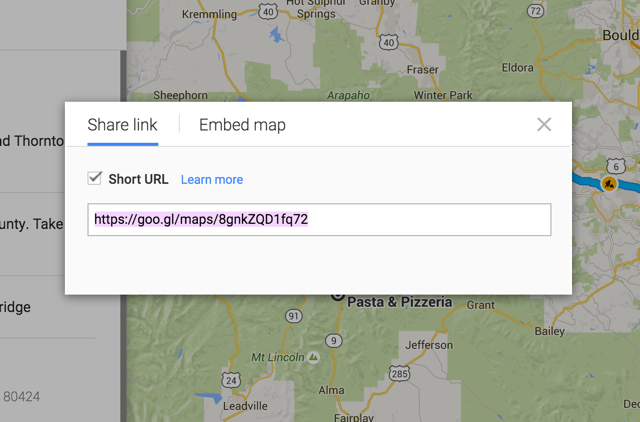
The researchers also found almost 24,000,000 live links when scanning the five-character tokens previously used by goo.gl/maps, about 10% of which were for driving directions.
Getting access to OneDrive documents and Google Maps directions is bad enough, but the researchers discovered that they could do even more with the information they recovered from those links. For example, by analyzing the standard structure of OneDrive URLs, they were able to navigate and gain access to a number of OneDrive accounts, many of which they found were actually writable, meaning they could change files or upload malware that would be automatically downloaded to the owner's computer.
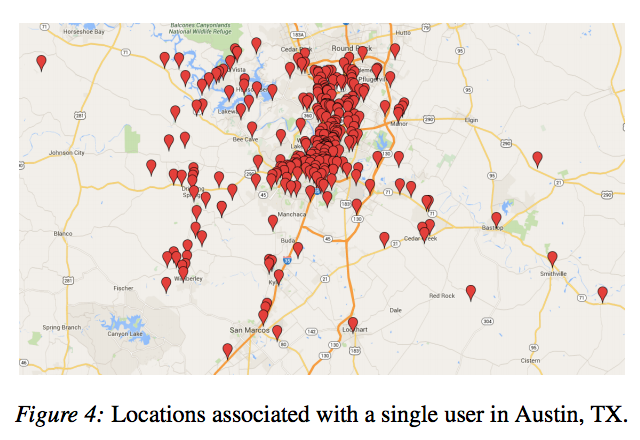
And with Google Maps, the researchers discovered a lot of information that people would probably want to keep private. By looking at residential addresses, they could make educated guesses as to which households included a person who went to specialist clinics for medical treatment, addiction treatment centers, strip clubs, and abortion providers. It's been shown that location information is very valuable in gaining identifying information for individuals, and that information combined with a sort of abbreviated travel history could be very useful to identity thieves.
If you want to see the full published article, you can check it out at arXiv, and one of the researchers also published a blog post with a useful summary.
Changes Made
The Cornell Tech researchers shared their results with Microsoft and Google, and both companies have taken steps to decrease the likelihood that their users could be compromised by shortened URLs.
URL shortening was removed from the OneDrive interface, and the method used to gain more information about the user's account no longer works (despite Microsoft's denial that their changes had anything to do with this report or that the study even revealed a security vulnerability). Old shortened links, however, remain vulnerable.
Google Maps now uses 11- and 12-character tokens instead of the five-character ones offered before, making it significantly harder to reveal them with a brute force attack. Google also made it more difficult for vast numbers of URLs to be scanned at once.
Stay Careful
Even though these two services have taken steps to mitigate the threat, the possibility of more vulnerabilities in the link-shortening process will likely be found sometime in the future (more and more powerful computers will certainly help). When I recently checked to see if popular shortening services were using small numbers of characters in their tokens, both ow.ly and tinyurl had six-character tokens, and bit.ly used seven.
While both are better than Google's previous five, it's still worrying that people could be sending access to important files or personal information this way. The Cornell Tech researchers demonstrated that a simple brute-force scan of these URLs can reveal a surprising amount of information on specific users, including a few of the most important pieces of information for identity theft.
So what should you do? To be totally safe, just don't use URL shorteners for anything that could be valuable to a hacker, identity thief, or other miscreant. Shorteners are really useful, but most of the time, a long URL will work just fine. It's big, ugly, and takes up a lot of space in an email or chat window, but it's also a lot safer.
Also, be aware that many other services offer URL shortening, and you may want to be careful with those as well. How each of those services handle permissions with shortened URLs is likely to differ, but if you accidentally gave away access to a Flickr, Google Photos, Google Drive, Twitter, Facebook, or other post, it's hard to know what will happen.
If you're given the choice to shorten a URL with a token that's longer than six or seven characters, you should take it. The researchers said in their paper that the 11- and 12-character tokens used by Google Maps are not brute-forceable (at least with current technology and a reasonable amount of effort), so aiming for at least 10 is probably a good idea.
Or just make your own URL shortener and make sure that it uses enough characters in its URL tokens!
Do You Use URL Shorteners?
Shortening services seem to be on the rise in popularity, with new services popping up regularly. Twitter's 140-character limit and the difficulty of working with long strings of text on mobile devices have likely contributed to their usefulness, and the ability to send a link in a much more viewer-friendly format is certainly appealing. There's no arguing that they're very convenient, but the convenience may not be worth the risk.
Do you use a URL shortening service? Which one do you use? Do you use it for sensitive documents, or just for publicly accessible links? Are you now worried about the security of your links? Share your thoughts below!
Image credits: Georgiev and Shmatikov via arXiv.