Security often feels like a daunting task. Who has time to spend hours locking down accounts and tightening the settings on your phone and computer?
The truth is that you shouldn't be scared of security, and can break it into manageable pieces. You can perform important checkups in a matter of minutes and your online life will be much safer because of them.
Here are several vital security checks to work into your schedule. Do these every once in a while, and you'll be more secure than the vast majority of people.
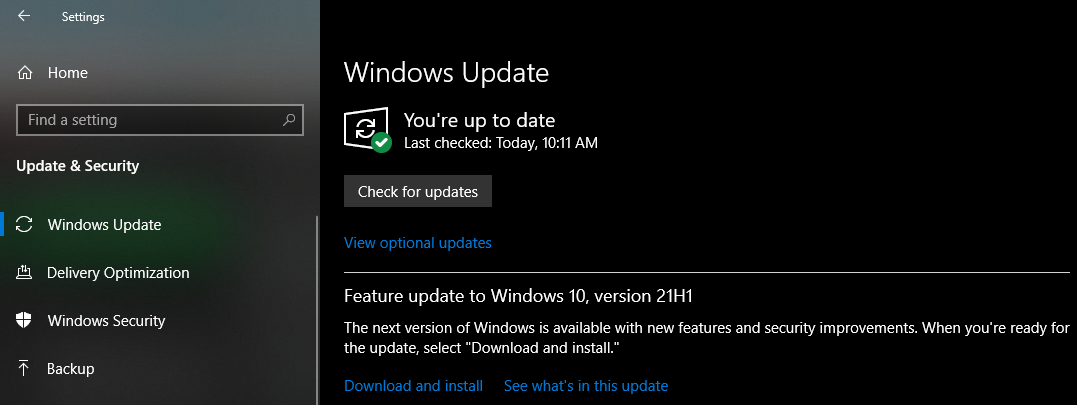
1. Apply Updates for Everything
Everyone has clicked "remind me later" when prompted about an update. But you shouldn't do this for long, since applying updates is one of the most important ways to keep your devices secure. When developers find a security flaw in their software, issuing an update is how they fix it. By ignoring these updates, you open yourself up to vulnerabilities.
Many victims of historical widespread security attacks were running outdated operating systems. Simply applying the latest patches would have protected them from these known risks. This is why most modern operating systems install updates automatically, or at least prompt you to install them regularly.
See how to update everything on Windows and our guide to updating software on your Mac to keep your desktop protected. When you open a program and see a prompt to update, do it as soon as possible. And don't forget about other devices; updating your router, Kindle, Xbox, etc. will keep you safer when using those devices as well.
2. Use a Password Manager to Change Your Weak Passwords
Using strong passwords is vital for keeping your accounts safe. Short passwords, passwords you use on multiple websites, and easily guessable passwords are all easy targets for attack. We recommend that you start using a password manager to handle this for you.
Take this a bit at a time so it's not overwhelming. Start by changing your most important passwords like your email, bank, and social media accounts. You don't need to change passwords all the time, but you should keep an eye out for major breaches.Tools like Have I Been Pwned? will check if your account details have been compromised.
This extends to your phone, too. Don't use something obvious like 1234 as your PIN.
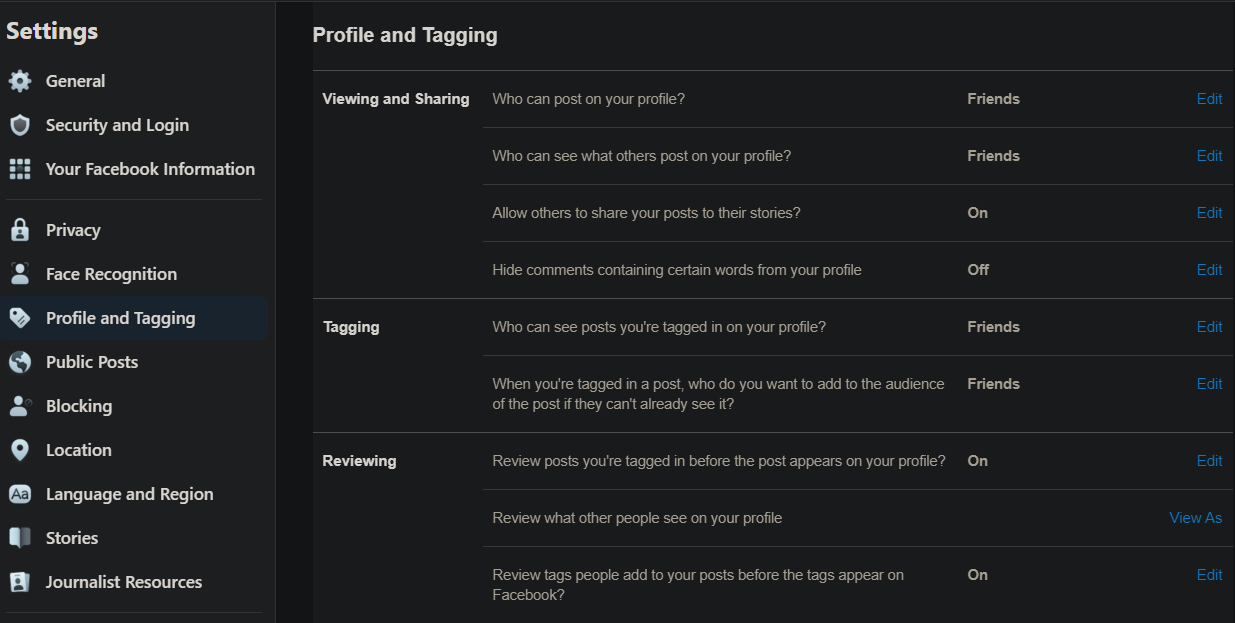
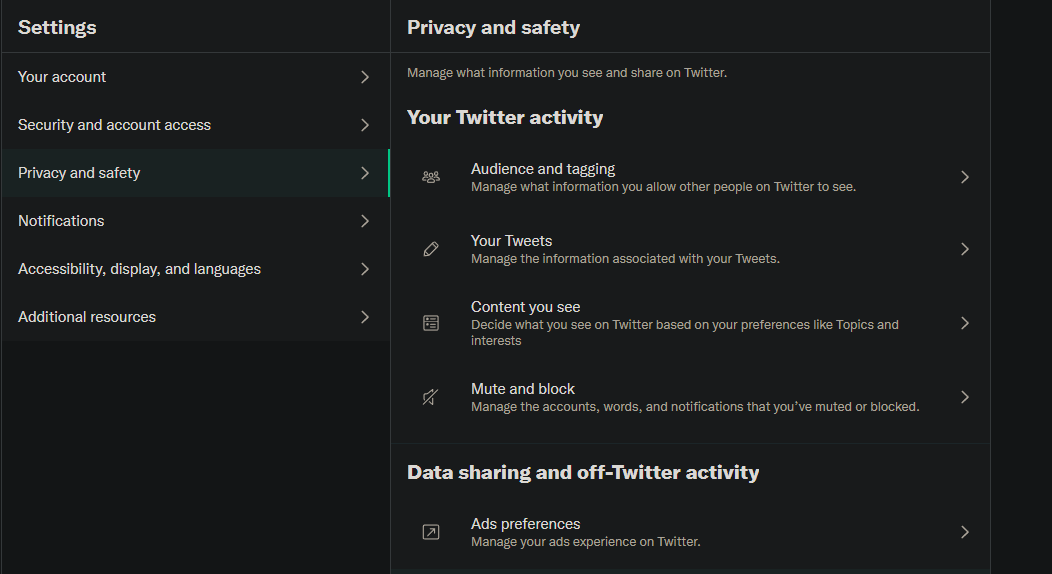
3. Review Social Media Privacy Settings
With misconfigured social media controls, you could be unknowingly sharing information with way more people than you realize. It's important to take a few moments to review who you're sharing updates with.
On Facebook, visit your Settings page and click Privacy on the left sidebar. Review the settings here to change who can see your posts, who can contact you, and who can look you up using search. You should also review the Profile and Tagging tab to change who can post on your page.
For Twitter, visit Settings and Privacy and click the Privacy and safety tab. Here you can protect your tweets so they aren't public, remove your location from tweets, disable photo tagging, and prevent others from discovering you.
4. Check App Permissions
Android and iOS both allow you to fine-tune the permissions that apps have to sensitive data like your microphone and contacts. Apps will ask you for access to these permissions as they need them, but you can grant or deny permissions at any time.
While most apps aren't malicious and need these permissions to work properly, it's worth reviewing them occasionally to make sure an app isn't taking information it doesn't need. Apps like Facebook that require an absurd amount of permissions might lead you to uninstall them completely.
See our guide to Android permissions and ways to increase privacy on iPhone for more information.
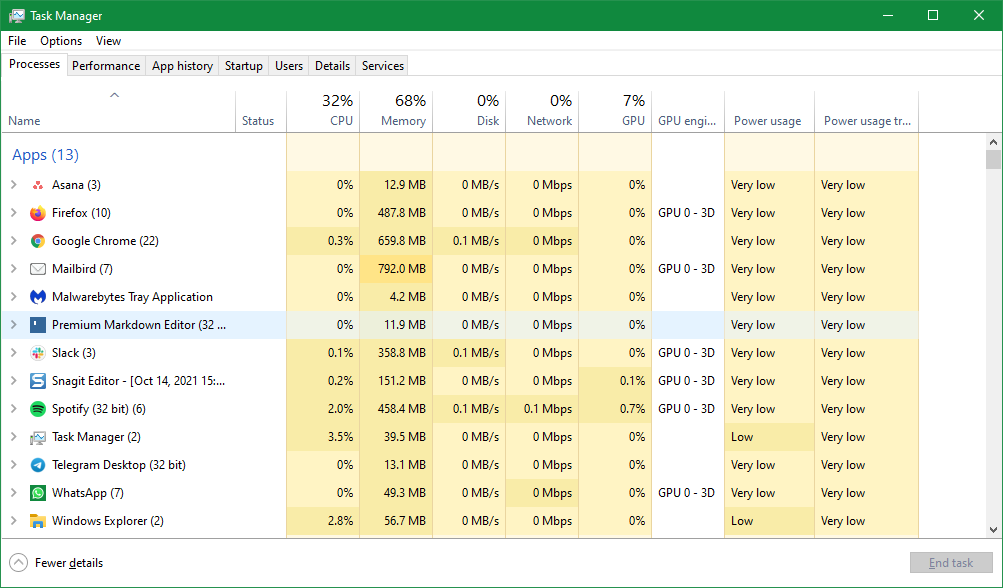
5. Review Running Processes on Your PC
While you don't need to know the exact purpose of everything that's running on your computer, it's a good idea to check which processes are active once in a while. Doing so will also help you learn more about your computer as you become more familiar with its workings.
On Windows, use the Task Manager to review and control running processes. The Processes tab contains everything running on your computer; just make sure you don't terminate any vital processes.
Mac users can see running processes with the Activity Monitor. The fastest way to open it is by pressing Cmd + Space to open Spotlight, then typing Activity Monitor and pressing Enter. Have a look through the CPU tab to see what's running on your machine.
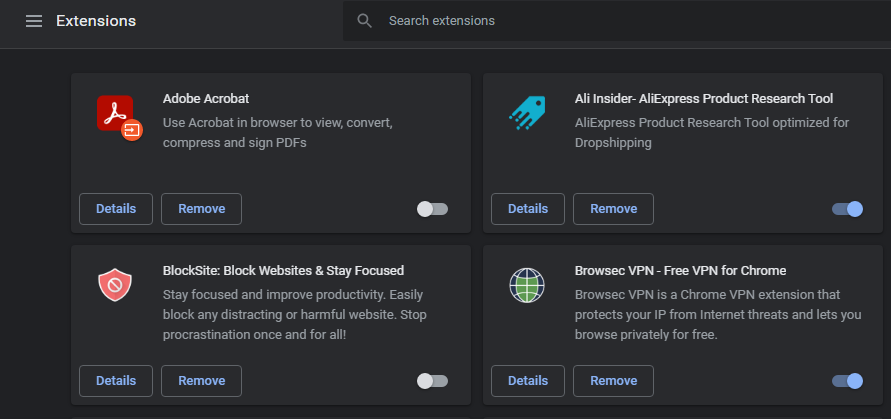
While you're at it, you should also review installed browser extensions regularly. Malicious add-ons can hijack your browsing, and even once-innocent extensions get bought out and become spyware. In Chrome, go to Menu > More tools > Extensions and disable or remove any that look suspicious. Firefox users can find this list at Menu > Add-ons and themes.
6. Scan for Malware
You might notice signs that you have malware on your PC, but in many cases, an infection can be silent. A good antivirus scanner should catch most malware infections before they can get on your system, but a second opinion from an anti-malware scanner never hurts.
On Windows, nothing beats Malwarebytes. Install the free version to scan for malware of all kinds and remove it with just a few clicks. You don't necessarily need to use an antivirus on Mac if you're careful, but there's nothing wrong with a quick Malwarebytes for Mac for peace of mind either.
7. Check Your Account Connections
Lots of websites allow you to sign in with another account's credentials; this is usually through Facebook, Google, or Apple. While this is convenient since you don't have to remember a separate login, having all those sites connected to one account is a bit worrying. That's why you should regularly review which sites and apps you have connected to your core accounts.
Check your Google apps by visiting Google's My Account page, then go to Security > Manage third-party access.
Take a close look at these, especially if you've used a Google account for a long time. You should revoke access to apps you no longer use and review the access that current apps have. Click an entry and hit the Remove Access button to delete the connection.
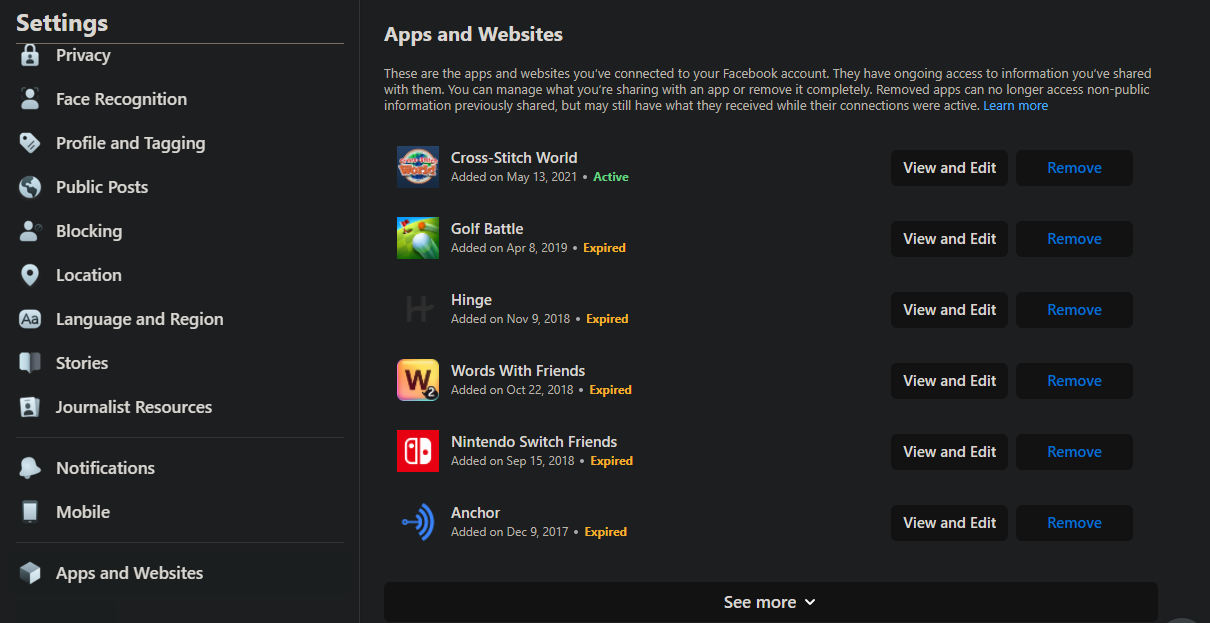
Facebook has a similar panel. Visit the Facebook Settings page and click the Apps and Websites link on the left sidebar. You'll see apps and websites that you've used your Facebook account to log into; click See more to expand the list.
Click View and Edit on an entry to see what audience the app can share to on Facebook, as well as what information the app can pull from your Facebook account. You can Remove individual permissions or the entire app integration as you see fit.
If you want to completely disable this functionality, click Turn Off next to Apps, websites, and games at the bottom of the page. You can also see apps you've revoked access for in the past by clicking View Removed Apps and Websites.
You may also want to review apps you've connected to your Twitter account at Settings > Security and account access > Apps and sessions > Connected apps. Click one, then hit Revoke app permissions to remove any that you don't use anymore.
8. Set Up Two-Factor Authentication Everywhere
Two-factor authentication (2FA) is one of the best ways to add more security to your accounts. When it's enabled, you need a code from an app or text message, in addition to your password, to log into an account. Thus, even if your password is leaked or stolen, there's another layer of protection on your account.
The process to enable 2FA differs a bit for each service. To get you on your way, see our overview of two-factor authentication, then enable 2FA on your social accounts. We recommend using Authy as your authenticator app; stay away from SMS authentication if possible, as it's less secure.
9. Review Account Activity
Another security tool that several sites offer is the option to see what devices have logged into your account recently. Some will even send you a text or email when a login happens from a new device. You can use these to know right away if someone breaks into your account.
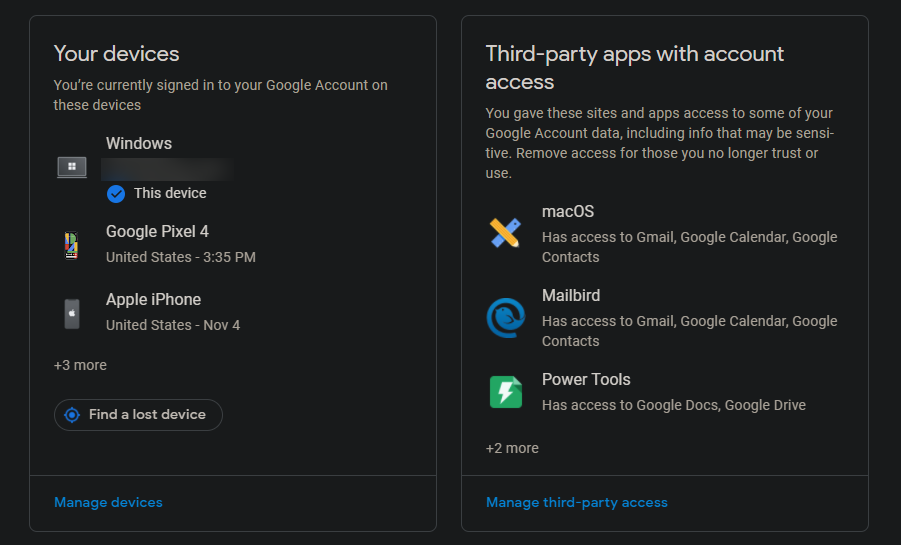
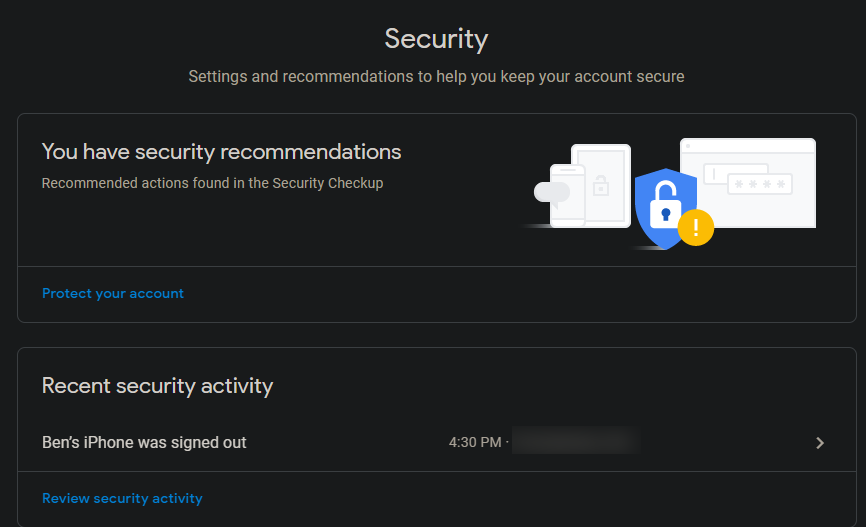
For Google, head to the same Google Account page mentioned earlier and click Security on the left side. You'll see Recent security activity showing sign-in warnings, and Your devices to show where you're currently signed into your account. Take a look at both sections and make sure you recognize all devices and activity. By default, Google will send you an email whenever a new device signs into your account.
Select an event or device to get more info on it. Choose Sign Out to revoke access from any devices that don't need it anymore. While you're here, check out any suggestions from Google at the top of the page, which will highlight potential risks on your account.
To check recent login events on Facebook, visit the Security and Login tab of your account settings. Under the top Where You're Logged In section, click See More to everywhere you're logged into Facebook. Click the three dots next to an entry to Log Out or select Not You? if you think someone else has gotten into your Facebook account.
Like Google, Facebook also has a security walkthrough you can take at the top of the page. It's a good way to quickly audit your account security.
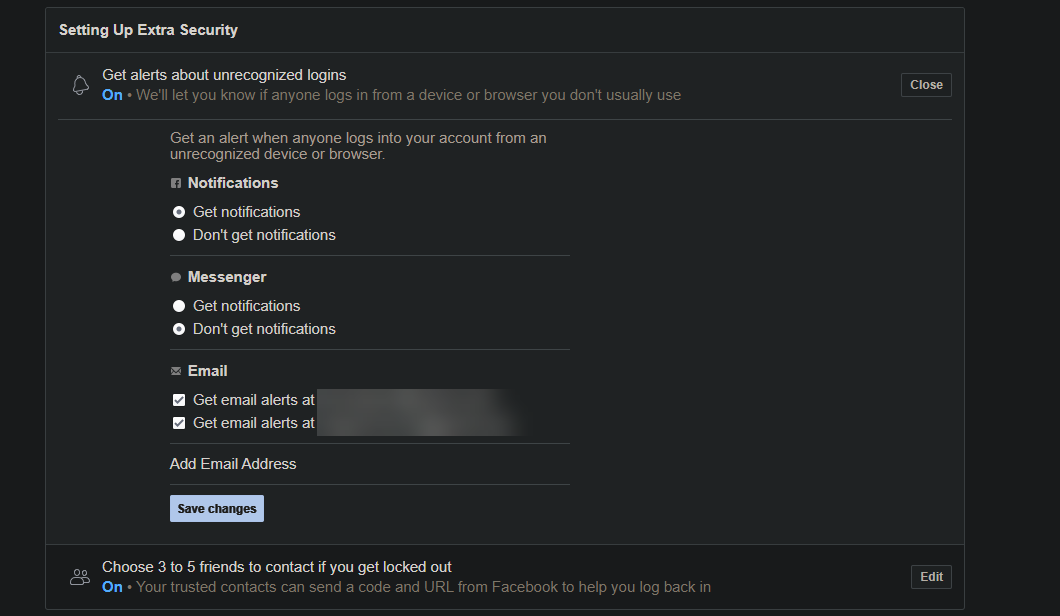
Also on this page, ensure you have Get alerts about unrecognized logins enabled. This will alert you by notification or email when an unrecognized device logs into your account.
Finally, check your Twitter active sessions at Settings > Security and account access > Apps and sessions. Check Sessions to see where you're logged in and log out if needed, as well as Logged-in devices and apps to see which devices Twitter is using for personalization.
You probably noticed that most of these tips revolve around your most email account. Your email is one of the most valuable accounts you have, because an attacker could do the most damage with it. If someone gets into your email, they can use the "forgot password" reset links on other sites to change any password that was linked to your email.
10. See Who's Using Your Wi-Fi
You certainly don't want people to snoop on your home network, and hopefully have secured your router so unauthorized people can't connect. It's worth a quick check to make sure that your neighbor didn't figure out your password, or similar.
See how to check your network for suspicious devices for assistance.
11. Uninstall Old Apps
When you're going through security audits, it's also worth checking to make sure that you don't use any old apps that are no longer supported. Even if an app is removed from the developer's website or the corresponding app store, it can still live on your device.
This can open you up to security holes, especially for once-popular software. There's also a chance that an app you once trusted will be bought up by a shady company and turned into spyware.
As a result, it's smart to check your phone and computer for "zombie apps" and only keep apps that you trust and use regularly on your devices.
Be Proactive With Regular Security Checks
These important security checks aren't fun or glamorous, but the protections they include go a long way in keeping you safe online. Now all your devices are updated, you know exactly what apps can access your accounts, and you've eliminated weak links in your security chain. It's much better to check for and resolve these issues ahead of time than to wait for a disaster to hit.
Keep in mind that even if you're secured, that isn't the same as being private or anonymous.