When it comes to internet security, everyone and their cousin has advice to offer you about the best software packages to install, dodgy sites to stay clear of, or best practices when it comes to passwords. Or perhaps you've never listened to others and have your own beliefs about internet security? In that case - this post is for you. Let's take a look at some of the most common beliefs - some might say myths - about internet security.
Note: Some of these quote results from a 2011 survey on 16,000 internet users by G Data Software. I'll be using their data for illustrative purposes only though, and we'll be addressing and somewhat debunking each myth.
My password is secure
Is it true? Not. One. Bit.
So you have a ridiculously long password full of numbers and punctuation? In fact, it's so long and uncrackable that you just use it on every site? Uh oh. All it takes it for one single site to have less than perfect security, and suddenly that password is known to all. Most sites store user passwords using a system of "hashes and salting", a process that ensures that whilst user passwords can be verified, the password cannot be retrieved at a later date by anyone - not even with direct access to database. But then some sites don't have quite the same level of security, and all it takes is one.
Sometimes, the hackers don't even need to "crack" anything - users who opt for a short or well known password - even when hashed and salted - can easily be deducted from lists of common passwords. To put it simply - comparing the result of hashing "12345" with the database will reveal all the users who had the same password. Do this many times with a list of common passwords, and you have a long list of hacked accounts, ready for resale or publishing.
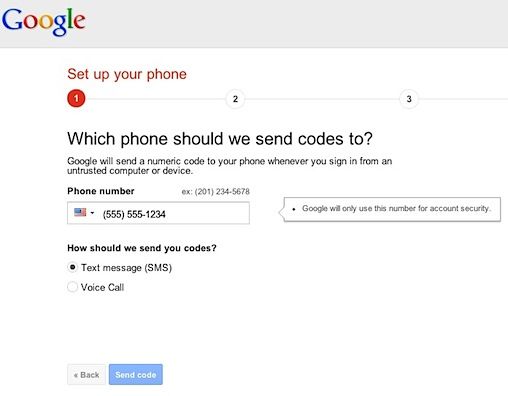
So whats the best way to secure your accounts? A long, unique but memorable password for each account is best - but even better is two factor authentication.
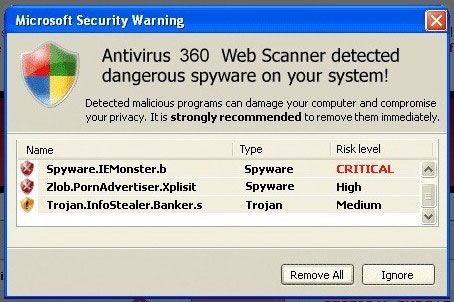
I have AV software installed, so I'm safe
Is it true? No.
Many users are lulled into a false sense of security that various software packages bring; the truth is that the biggest problem is the user. An anti-malware package or internet security suite can only do so much to protect the user - it isn't foolproof, and nothing will offer complete protection. If someone phones you up pretending to be from Microsoft, and you give them full remote access to your PC in order to fix an unknown problem, no amount of software is going to protect you.
You generally don't need security software if you follow some basic advice, learn what the threats are, and act cautiously.
You'll know when you're infected
Is it true? No - you'll be clueless.
93% of respondents assumed they would know about malware if they were infected, but this couldn't be further from the truth. Modern malware is stealthy, and hard to detect - it won't launch a million popups telling you to subcribe to something, because that would be a clear signal to the user that something is wrong. Instead, it'll quietly sit in the background, secretly giving control to a remote attacker, saving your keystrokes to listen to bank account access, or sneakily sending spam emails by the millions. Not all malware is stupidly obvious.
I'm a Mac user - nothing to worry about
Is it true? Not completely, but your chances are certainly reduced.
Though malware specifically targetting Macs is minimal, it certainly does exist; once you factor in Java and Flash as distribution vectors, the amount of possible attacks increases. Luckily, Apple has also been making headway on the issue, and now refuses to run software that isn't from a signed developer by default - though this is easy to override by the user.
Windows - specifically older versions of Windows and Internet Explorer in particular - remain the most popular target due to their sheer proliferation for potential targets and the fact that the users are likely to be somewhat less tech savvy.
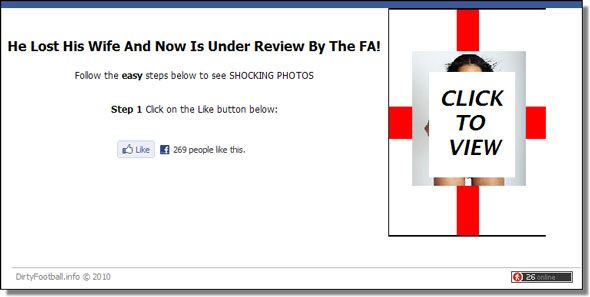
It's from a friend, so it must be safe
Is it true? Most certainly not.
Even if that email or Facebook message is from a trusted friend, the message itself cannot be trusted. This counts for instant messages and Skype too, and sometimes even SMS. The victim will install the malware, which then proceeds to systematically contact everyone in the address book or friends list.
So how to stay safe?
- Friends, don't let friends use shortened links, ever!
- Don't install random Facebook apps, despite how enticing they may be.
- Don't use third party IM tools that aren't extremely well known already.
- If you suspect something was spam and not a genuine message, just ask them.
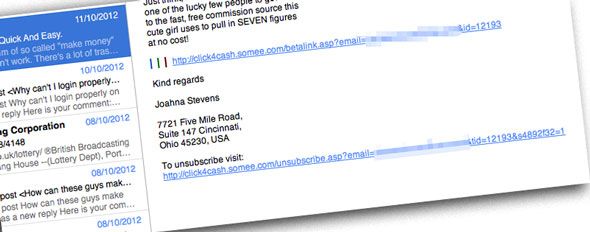
If I tell a spammer to not email me, they'll remove me from their mailing list
Is it true? No.
Quite the opposite in fact - if you either respond to the spam email or click the unsubscribe link, you're actually just verifying to the spammer that you're a real person - a legitimate address - and you'll simply be added to more target lists. Most of these emails are sent out in bulk - generated by a software package which has no idea if the email address is even real. By clicking usubscribe, you're simply signalling that the spam software was correct.
Best thing to do? Hit the spam button so that your email software or provider improves it's spam database.
Malware Comes From Email Attachments
Is it true? Not really.
54% of users thought that email is the primary distribution method for malware; but I think we all know enough to not download random email attachments nowadays. These certainly do still exist, but more common is to include an innocent looking link which sends you to a website containing the malware that will auto-download.
Of course, neither is a problem for any savvy user - Gmail and other providers filter most of them out automatically, and most will virus scan attachments for you. Any of the link-based attacks that do get through will invariably be in the form of shortened URLs or something obviously fake. Here's a tip: microsoft.someothersite.com has nothing to do with Microsoft, and login.paypalprocessing.co.cc has nothing to do with Paypal - always check the root level of the domain before clicking. If something is asking you to login for some reason, then just type the address you always use directly into the browser address bar and don't click anything in the email. No service will ever ask you to "confirm your password" or account details via email, especially not banks! And finally - shortened URLs like Bitly.com/123asdf are never trustworthy because you have no idea where they go.
Don't click on links in emails unless you're 100% sure of where they go. Simple.
Just Going To A Website Can't Infect You
Is it true? Mostly.
48% of internet users polled believed that simply visiting a site cannot infect you. This both is, and isn't true. If you use a secure browser - like Chrome - which uses a technique called "sandboxing" to place each tab into it's own virtual playground with no access to system resources, then yes, this statement generally holds true. Java is the exception to this however, and so is Flash; if you have these kind of third party plugins enabled, then they can be used to infect your PC regardless of the browser. The latest version of Firefox sandboxes Flash too, I should note.
Best advice? Uninstall Java, and disable Flash by default. You can enable it for certain sites then, or approve the plugin only when needed. If you're using an older version of Internet Explorer - stop it - and go download something more secure immediately.
Malware comes from illegal file sharing sites
Is it true: Partially
Yes, illegal file sharing sites are an easy way to distribute a virus - you can't verify the legitimacy of a game that's been pre-hacked, just as you can't know for certain that the movie you're downloading won't actually be an .exe file or have something malicious embedded. Or can you? Most filesharers on sites like PirateBay know enough to avoid anonymous uploaders or non-respected members, opting to only download those from trusted members (with a green or pink skull and crossbones next to their user). Additionally, there a little thing called comments - if the first five users are verifying that this torrent does indeed scan positive for malware, then here's a quick tip - don't download it. A 2009 study showed around 20% of torrents contained malware over a small sample of 70 downloads, though these were all from "public" torrent sites like BushTorrent and BTJunkie. The malware ratio on a private torrent tracker would be significantly smaller.
"Regular" websites are still the preferred delivery method: a more recent survey by Sophos claimed that 30,000 websites are infected daily, and that 80% of those are legitimate websites that have been hacked or injected with malicious code rather than specifically set up to host malware. Luckily for you, Google maintains a pretty comprehensive database of these sites, to which the automatic Google bot scanners add 9,500 infected sites daily.
Adult sites are more dangerous than general sites
Is it true? Yes, and no.
Adult sites - that is, paid ones - are more motivated to keep their clientele and hence not get them infected, and are generally more secure in order to protect their content. However, if you go out looking for the free stuff, then those sites are almost certainly going to contain malicious links, and fake download buttons - clicking on those results in revenue for the sites.
Don't be fooled into thinking it's only these kind of risqué sites that contain malware though; it isn't. Any site can be a victim of an attack, as criminals simply wish to infect the most users - a highly trusted site is a prime target for a hacker.
You have to open a file to get infected
Is it true? Nope.
22% of users survey believed that to be infected, the user had to specifically open a file or run it; this is just not true. Exploiting existing loopholes allow an attacker to run a file without user intervention. Most operating systems now include some kind of safeguards that ask the user before running anything, but again, many users will blindly click allow, and this isn't even neccessary if the attack uses a platform like Java to deliver it's payload.
Installing More Security Software Makes You Safer
Is it true: Unlikely
Though I'm personally of the opinion that even one bit of security software is too many, there are those users who insist on installing a plethora of system level firewalls, anti-viruses, malware scanners, plus pages worth of browser plugins. The net result? An exceedingly slow browser, severe performance issues with the computer, file lockups, delayed start up, and general frustration. And, of course, no additional protection.
If you're the kind of person that likes analogies, try this one: installing multiple security suites is like adding more locks to your door. If a thief really wants to get in, they'll break a window instead; the only real victim is you by having spent an extra 3 minutes unlocking them every time you leave the house.
Do you know of any more security myths that you're sick of hearing? Tell us in the comments!
Image Credit: Shutterstock - Password