There's no shortage of Linux operating systems available. However, many Linux distributions (distros) are niche OSes. For instance, Kali Linux is an ethical hacking and penetration testing Linux distro. There are server Linux operating systems, media center Linux distros, and more.
However, Qubes OS focuses on security. Its tagline reads: "A reasonably secure operating system." On its homepage, Qubes OS boasts testimonials from the likes of Edward Snowden. With its onus on security, and superb compartmentalization, freedom, and integrated privacy features, Qubes OS is a functional and intuitive security-oriented Linux operating system.
What Is Qubes OS?
Although Qubes OS is a security-centric Linux operating system, let's clarify how it's different. While a firewall and antivirus software are essential -- yes, even Linux needs an antivirus -- Qubes takes a different approach. Rather than relying on traditional protection measures, Qubes OS employs virtualization. Therefore it fosters security via isolation.
The isolation method focuses on limiting software and hardware interactions. Notably, Linux pre-built laptop company Purism offers an option to ship its machines with Qubes OS. Purism machines rank among the best Linux laptops and desktops you can buy.
Installation and Getting Started
Like most Debian-based Linux operating systems, the Qubes OS initial installation is fairly simple. I tried Qubes OS on an AMD A-10 HP laptop. While lightweight Linux operating systems usually function better, I found little to no perceived performance issues on the HP. Installation is fairly simple. Download the ISO file, mount it to bootable media, and install on a hard drive.
Installing virtual machine software (such as VirtualBox) might not function properly considering that all apps in Qubes OS run in virtual machines. Thus, you would create VM inception. Notably, the live USB option is not supported, though it's still available as a download.
Isolation
Unlike most traditional Linux desktop operating systems, Qubes OS employs virtualization. Various virtual machines (VMs) separate and compartmentalize its environment. By default, there a few VMs available. You can create your own as well. Virtualization manifests on two fronts: software and hardware. Therefore hardware controllers are separated into domains such as USB controller domains. But software gets segmented into domains with varying trust levels.
For example, you may have a work domain for the most trusted applications and a random domain for the least trusted domains. Each of these domains operates on a separate VM
But unlike running an operating system within a virtual machine, Qubes uses virtualization to isolate applications. For instance, your web browser remains in a different environment than your file browser. That way if a vulnerability gets exploited and executes commands on your system, the attack is contained.
Xen Hypervisor
Qubes OS uses Xen hypervisor for isolating different virtual machines. Still, there is an administrative domain, D0m0. This administrative domain features access to every piece of hardware. Moreover, Dom0 hosts such aspects as the graphical user interface (GUI) and peripherals like the keyboard and mouse. But since there is a GUI, applications appear as if they run on a single desktop. Rather, apps are isolated in virtual machines. Qubes OS employs the Application Viewer to lend an appearance that applications run on a native desktop.
Instead, Qubes simply integrates applications into one desktop environment.
Using Qubes OS
Dedicated Domains
Using Qubes OS may appear more complex than it is. That's mostly due to its security through isolation set up. Nevertheless, running applications in virtual machines isn't as difficult as it sounds. The simplicity of Qubes OS is remarkable. At first glance, Qubes appears like a standard desktop environment. In appearance, it's no more complex than a Linux operating system like Ubuntu.
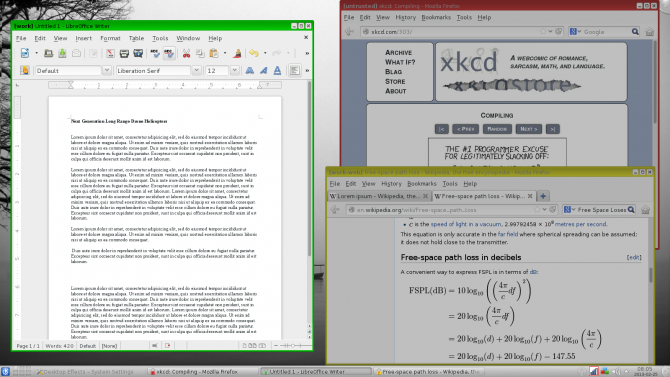
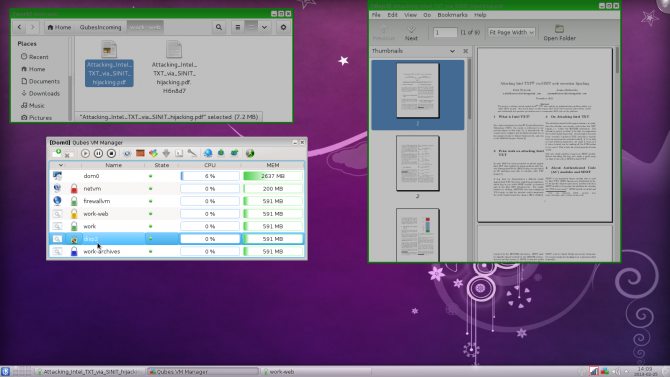
For instance, you can view two different instances of the same web browser side by side, they can run on different security domains. One may be your work browser, whereas the other is your untrusted browser. Visit the same website in both browsers running side by side, log into one, and you won't be logged in on the other browser. That's because they're in separate domains, on separate VMs.
Even file browsers remain completely separate. But using Qubes OS doesn't feel like using virtual machines. Because Qubes OS integrates all virtual machines into a single desktop environment, everything appears seamless. However, there are means to share between domains. For example, if you have a file saved in your personal domain, you can copy it to your work domain.
Even the clipboard is domain separated. If you copy text in a text document on your work domain and click into a document on a personal domain, the text is relegated to the original domain. Still, as with files, you can use Ctrl + Shift + V to copy clipboard data between domains. Different colored borders differentiate your separate domains helping you easily identify applications.
Disposable Domains
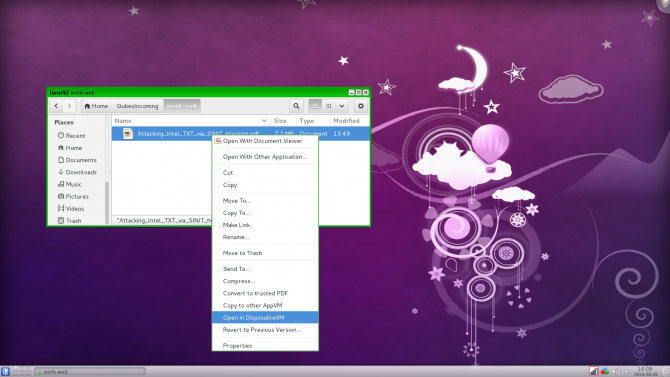
In addition to dedicated domains, you can create disposable domains. These differ from dedicated domains. Disposable domains are created for a single task, and once that's complete they're totally gone. If you open an instance of a web browser in a disposable VM, you can do whatever you want: bookmark sites, add them to your favorites, and save cookies. Once you close that browser, everything from that session is gone. Opening another web browser in that disposable VM will show nothing saved from your previous session.
From any domain, there's a right-click option to open a document in a disposable VM. Therefore, if you download a file in a work or personal domain, you can right-click and open that file in a disposable domain. Notably, this is an excellent means to avoid contaminating a domain. If you download a PDF from an untrusted source (not recommended), you can save it in your work domain and execute it in a disposable domain.
App Installs and Updates
Opening a terminal in an application domain, such as your work domain, downloads and installs software as usual. However, using a domain specific terminal limits that application to that domain. Moreover, installing an application within a specific domain doesn't save. When you restart that domain, that program is absent. To install and save an application, you must install it in the template. This is a neat touch. For example, if you want to try an application, you can try it within a specific domain. Then a VM reboot clears that application.
Appearance and Perceived Performance
Appearance and performance are where Qubes OS really shines. Using an application, you would have almost no idea that you're using an app in a domain. Pull up a work and personal web browser side by side and the only indication that they're running in separate VMs is the colored border around each and label that says the domain name. I really appreciate the simplicity of Qubes OS. While it's complex in its customization options, Qubes OS is very intuitive.
Although both Qubes OS and Container Linux by CoreOS both concentrate on virtualization, Qubes remains more user-friendly. Because Container Linux is entirely command line-centric, it's less suited to beginners. But since Qubes OS includes a GUI it's simpler to navigate. In fact, Qubes OS doesn't look or feel like anything aside from a standard desktop operating system.
Why Use Qubes OS?
Okay, now the question you're probably asking: why should you use Qubes OS? Can't you achieve all of this virtualization using the likes of VirtualBox, VMware, and Parallels?
Unfortunately, that approach is pretty cumbersome. To upgrade applications within those separate domains is pretty task-intensive. You would have to, for instance, update the web browser in each unique virtual machine.
Enter Qubes OS. What makes Qubes OS fantastic for compartmentalization is its ability to spin up VMs and run applications within separate virtual machines in one desktop environment. But Qubes integrates everything into one desktop environment. Spinning up new VMs is incredibly manageable. Within domains, you can choose which applications appear in that domain, select various templates, and work with totally isolated environments in one desktop.
Because Qubes OS is VM-centric, you'll need a pretty beefy computer. While you may be able to run Qubes OS on less powerful hardware, it's not recommended. Virtual machines remain hardware and resource intensive.
Have you tried Qubes OS? Let us know your thoughts in the comments section!