The GHOST vulnerability is a flaw in a vital part of every major Linux distro. It could, in theory, allow hackers to take control of computers without the need for a username or password.
Having said that, there are a few key points to keep in mind:
- The flaw has never been exploited in the wild – just in experiments by security researchers.
- There are patches out there, right now, for every major Linux distro.
- If you install security updates regularly, or use a rolling release distro, you've got nothing to worry about. Install the latest updates and you're covered (the updates will require a restart, but don't put it off).
- If you use an outdated release of a Linux distro, which no longer receives security updates, you're likely vulnerable to GHOST (and a variety of other exploits).
It's odd, but modern security vulnerabilities have brand names intended to raise awareness – Heartbleed is a recent example, with its striking name and red logo. The brands help make otherwise obscure bugs into news stories, helping ensure problems are patched quickly.
GHOST brings this trend to the Linux world, thanks to an effort by Qualys. They hired a PR team to publicize their role in finding the bug, and many feel it was overhyped.
We'll get to that. First, here's what this bug is, what it affects, and what it can teach us about how Linux security updates happen.
What Is GHOST?
GHOST is a flaw in glibc, a library that comes with most Linux distros and is necessary to run basically all software. GHOST itself is a flaw in the "gethostbyname*()" function of glibc, which applications use to convert a web address to an IP.
This is where GHOST got its name: GetHOSTname.
The bug creates a buffer overflow, which allows would-be hackers to run code without credentials. Qualys' proof of concept did this by sending code to an email server – other use cases might be possible.
Interestingly enough, the flaw was fixed in 2013, but wasn't identified as a security risk at the time.
If The Bug Was Fixed Years Ago, Why Is It An Issue Now?
Basically, because no one noticed the bug was a security problem – meaning the update wasn't pushed to many users.
Linux distros are a compilation of a wide variety of different packages. To the user this means software like Firefox, and desktop environments like Gnome, but that's really only the tip of the iceberg. A lot of other software and libraries, including glibc, make Linux what it is behind the scenes. These projects all have their own teams, which regularly put out their own updates.
There are a lot of Linux distros out there, and all of them have different approaches to pushing these updates to their users. Rolling release distros, for example, are pretty much constantly updated – meaning users of distros like Arch have been secure since 2013.
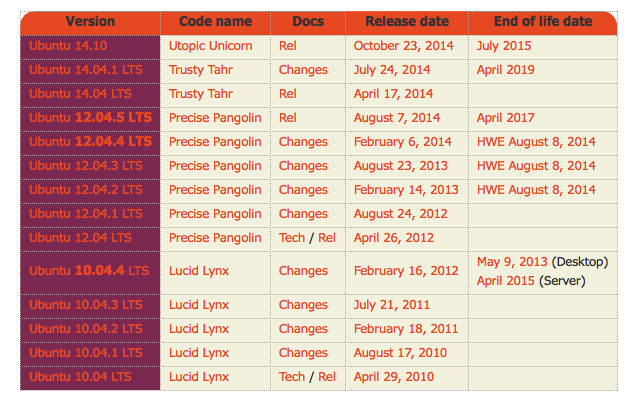
Ubuntu, to use another example, sees a new version released every six months. These releases generally update all packages, which only get security updates after that. This means versions of Ubuntu released in 2014 or later were never vulnerable to GHOST, but users of Ubuntu 12.04 LTS were (at least, until a security update patched the bug).
According to Symantec, vulnerable releases included:
- Ubuntu 12.04 LTS
- Ubuntu 10.04 LTS
- Red Hat Enterprise Linux 5
- S.u.S.E. Linux 7.1
- Debian Linux 6.0
Interestingly, ChromeOS developers noticed the flaw in early 2014, and patched it themselves for that reason. The Linux world seemingly didn't notice.
Should I Be Worried?
Probably not: updates have been pushed to all major distros, and the bug itself was overhyped according to security experts. To quote Pawan Kinger at Trend Micro:
"Taken together, the risk of actual exploits targeting GHOST is relatively small compared to other vulnerabilities like Shellshock or Heartbleed." -- Pawan Kinger
And to quote Jake Edge of LWN.net:
"While the GHOST glibc vulnerability is serious, it also seems to be fairly hard to exploit – and has been seriously overhyped." -- Jake Edge
It was certainly a vulnerability that needed patching, but it probably didn't need a brand name and a logo – and you shouldn't lose much sleep over it.
What Can Users Learn From This?
If there's a security myth that needs to die, it's that Linux users don't need to worry about their security. Every operating system has security flaws, and Linux (while quite safe) is no exception.
And on all systems, one of the best ways to protect yourself is to keep everything up-to-date. So, to summarize:
- Always install security patches.
- Ensure the version of Linux running on your personal computer, or your server, is still receiving security patches. If it's not, upgrade to a newer release.
Do these things and you should be fine.
I want to know: have you installed updates yet? If not, get to it! Come back when you're done, and we can talk about this and more in the comments below. Remember: just because you don't run Windows doesn't mean you're completely safe!