Most of us know Heartbleed as a bug that affected websites and web servers, but Android 4.1.1 also uses the vulnerable version of OpenSSL. In other words, some Android smartphone and tablets are vulnerable to Heartbleed attacks.
What's the Risk?
Heartbleed has been used to attack various web servers. In a nutshell, servers running the vulnerable version of OpenSSL have a bug in their encryption that can be exploited. By sending specially crafted packets, attackers can force the web server to respond with chunks of its working memory. This working memory can contain sensitive passwords, private encryption keys, and other important data.
Your Android device doesn't function as a web server, of course. The problem is the flaw can also work in reverse if the client -- Android, in this case -- is running vulnerable OpenSSL software. In other words, when you connect to a malicious or compromised website from your Android 4.1.1 device, the website can send specially crafted packets and force your Android phone or tablet to respond with chunks of its working memory. This memory could contain sensitive data -- for example, it could give away data belonging to an online banking app or your credit card number from an online shopping app that's saved in memory. It could give away passwords, private messages, and anything else your Android may have in memory.
If you use a vulnerable device, websites you connect to via your browser and other apps could use the Heartbleed flaw to capture the contents of your device's memory.
How Many Devices Are Vulnerable?
Google divulged this information in their Heartbleed information blog post:
"All versions of Android are immune to CVE-2014-0160 (with the limited exception of Android 4.1.1; patching information for Android 4.1.1 is being distributed to Android partners)."
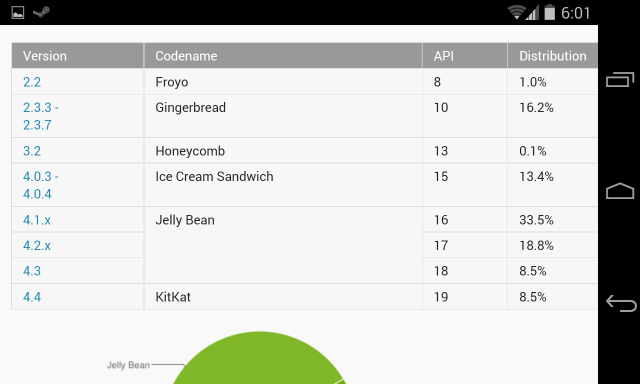
The good news is that your Android device is probably fine. The bad news is that Google's developer dashboard indicates that as many as 33.5% of devices in active use run version 4.1.x, also known as Jelly Bean. This includes devices running other versions of Android 4.1, so we don't know exactly how many devices are actually running Android 4.1.1 specifically.
Check if Your Device is Vulnerable
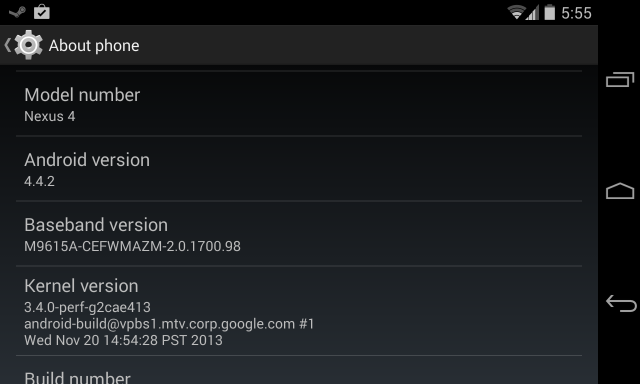
If you're not sure what Android version your devices are using, you'll want to check first. Open the Settings app, scroll down to the bottom of the screen, and tap About phone or About tablet. You'll see the version number displayed under Android version on this screen.
If you see anything but 4.1.1, you're fine. If you see 4.1.1, you may have a problem.
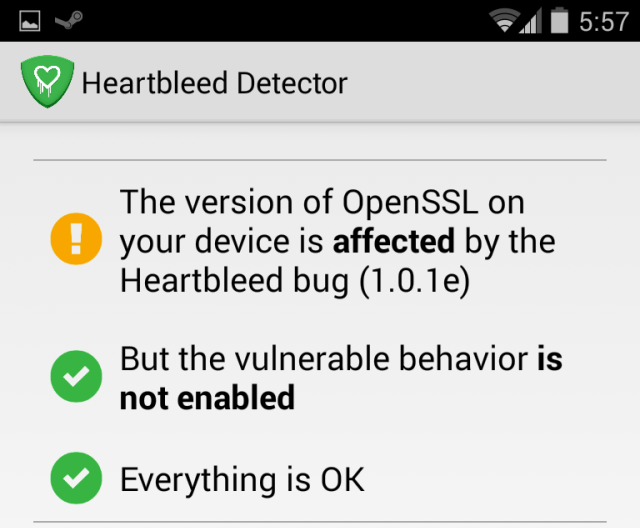
To double-check whether you're actually vulnerable, you may want to install Lookout's Heartbleed Security Scanner app. This app doesn't just check your installed version of Android. Instead, it checks to see if the version of OpenSSL on your device is vulnerable to Heartbleed. It also checks to see if the device is actually vulnerable -- if OpenSSL has been built without support for heartbeats on your device, you may actually be secure.
Here we're using a Nexus 4 with Android 4.4.2 and Heartbleed Detector says OpenSSL is vulnerable. However, the heartbeat feature is disabled on this version of Android, so we're perfectly fine. In spite of the potentially concerning warning message, we don't have to worry at all.
Update Your Device
The real solution for vulnerable devices is an update. As Google said, they're trying to help Android device manufacturers and cellular carriers patch their devices. However, we all know that the Android updating situation can be a mess. Manufacturers have many different devices to update, so they may not have issued a patch yet -- or they may not ever release a patch if the device is older. Even if a manufacturer releases a patch, cellular carriers will have to deploy it and may drag their feet or just never release the patch.
If your device is vulnerable, you should attempt to update to the latest available version of Android for your device using its built-in update feature. This will vary from device to device and carrier to carrier.
If You Can't Update
If your Android hardware is vulnerable to Heartbleed and no patches are available, hopefully you'll get one soon. To be secure, you should avoid storing sensitive data on your device -- this means uninstalling online banking apps, not entering your credit card into websites and apps, and similar things. Of course, your passwords and messages will still be exposed. You should really avoid visiting websites and using apps as much as possible if your device is a vulnerability.
The majority of Android devices out there aren't running a vulnerable version, and the majority of devices running the vulnerable versions should have updates available to fix this problem. If you're using one of the few devices that hasn't been updated, you should stop storing sensitive data on the device. You may want to contact your carrier or the device's manufacturer and see if they'll be releasing an update soon. If your device isn't receiving an update, it may be time to get a new one.
Of course, you can always install a custom ROM like CyanogenMod to replace the version of Android that comes with your device. This will give you an up-to-date version of Android that isn't vulnerable, but it's a bit more work.
Sure, there may not be any known cases of this vulnerability being exploited, but it's better to be safe than sorry. It would be very difficult to detect if an Android device was being exploited.
Heartbleed has been used to capture sensitive tax information, passwords, and other data online, so it's best to avoid using any software vulnerable to Heartbleed attacks.
Image Credit: Indi Samarajiva on Flickr