We've all heard about webcam hacking, but what about microphone hacking?
Yes, there are people out there who can hack into your operating system and take over your microphone, using it to listen in on your conversations and record personal information. In fact, as German researchers proved, it gets a whole lot more sinister than that.
So, how much of a privacy risk does your microphone represent? Do you need to start taking precautions? And how can you protect yourself?
Let's take a look.
The Secret Spy
Web camera hacking has frequently been in the headlines over the last few years, and as a result, it's now firmly in the public consciousness.
A hacked camera is reasonably easy to spot; lots of built-in laptop cameras have a light that shows when they're in use, while external USB cameras can be unplugged to nullify any threat. The threat is there, but it's "treatable".
But what about microphones? Almost all computers now have built-in microphones. How can you tell if they are being used? They don't have lights, they rarely come with on-screen notifications, and they're not as easy to cover as a webcam; some muffled speech will still get through, especially if you're a loud talker.
Why Should You Care if Your Microphone Is Listening?
It's easy to be dismissive of the potential threat. Why should you care if someone listens to you talking about a TV program with your partner, or the sports results with your best friend? What use is that information to a criminal?
The answer: massively useful.
What happens when you try and log in to an online service that you've not used in months or years?
Often, you'll have forgotten your password.
Then what happens? You go through a series of security questions. And guess the most common questions: "What is the name of your pet?", "What is your favorite sports team?", and "What is your mother's maiden name?". Exactly the types of questions whose answers you might have discussed in your home.
Suddenly, the prospect of seemingly innocent conversations being overheard feels a lot more worrisome, doesn't it?
What Are RATs?
The chances of a hacker targeting you in the above manner are admittedly slim, but there are still more serious and sinister concerns you need to be aware of.
One example is RATs. RATs is short for "Remote Access Trojans". These are pieces of malware that allow a hacker to remotely control a victim's computer. They are often delivered by zero-day vulnerabilities and so can bypass security software before running invisibly in the background.
Once operational, these RATs can capture sounds from the user and their surrounding environment and send them back to the hacker via compressed audio files or even encrypted streams.
RATs have been found in highly secure government and corporate environments, with experts now claiming confidential data is being exposed at an alarming rate. The problem has been exacerbated by the proliferation of Voice over Internet Protocol (VoIP) phones, such as Skype, which have increased the number of potential vulnerabilities by their very nature.
The bottom line is, whether you're a home user or business owner, you're at risk from audio RATs.
High-Pitched Hacking
The last vulnerability worth considering is the use of microphones as a means for transmitting and receiving data using high-frequency audio signals that are inaudible to humans.
In 2013, researchers at Germany's Fraunhofer Institute for Communication, Information Processing, and Ergonomics conducted a study. It found that "covert acoustical networking"—a technique which had been hypothesized but never proved—was indeed possible
The two researchers, Michael Hanspach and Michael Goetz, discovered that it was conceivable to transmit small packets of data between two laptops that were 20 meters apart and not connected to the internet. The signal could then be repeated, allowing hackers to quickly develop a mesh network over huge distances.
Mark Hagerott, U.S. Naval Academy cybersecurity professor, said:
"These arms races between defensive and offensive advanced technologies have been going on for [a long time], but now, with the low cost of writing code, it may get progressively more challenging to defend against."
According to Hanspach, the network could transmit data at about 20 bits per second—not enough for large files, but more than adequate for sending data from keyloggers, encryption keys, or login credentials.
How to Stay Safe From Microphone Threats
Those are very different hacking techniques, all of which utilize your computer's microphone.
And that's not even mentioning when your phone collects information for advertising.
Whether it's someone listening in to your conversations to garner personal information, a hacker who's used advanced software to remotely listen in to a business' confidential Skype conversations, or someone who is using your microphone to collate data, it all just proves just how vulnerable you can be if you're are not careful.
Can You Disable Your Microphone?
If you're not an online gamer or you don't have to take part in a lot of video calls for your job, it is possible to make a case for leaving your microphone permanently disabled. You can just enable it on odd occasions when needed.
It's not a foolproof plan—hackers could reenable it if they were already in your system in some way and they really wanted to, but at least you're minimizing your risk.
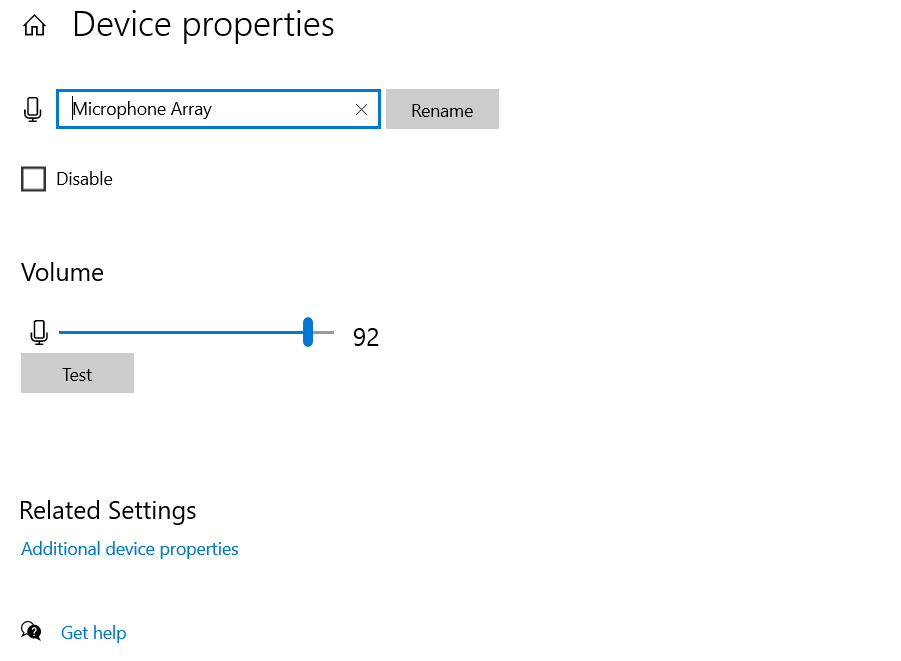
To disable your microphone on Windows, follow these step-by-step instructions:
- Open the Settings app.
- Select System from the menu.
- Click on Sound.
- Scroll down to the Input section.
- Click on Device Properties.
- Mark the checkbox next to Disable.
If you are running macOS, the process is similar, if simplified:
- Open System Preferences.
- Select Sound.
- Click on the Input tab.
- Move the slider all the way to the left.
Just remember to turn it back on again before you need to use it!
Don't Panic: Take Precautions
Taking these steps won't help if someone has deployed a RAT on your machine, but the chances of that are relatively small.
Nonetheless, the only way you can be truly safe is to use zero-day virus protection alongside your regular anti-virus software, and be extremely vigilant about which sites and apps you grant microphone access to.
Image Credit: BoBaa22/Shutterstock