Online security is something you probably know is important, but might not give it the proper attention. Unfortunately, negligence in this area can result in huge problems, and your email is one of the most sensitive areas.
Having your email account compromised will allow an intruder to break into any account you've used it to sign into. That's why you need to keep your email as secure as possible. Here are some simple yet important email security tips you should put in practice.
1. Use Separate Email Accounts
Most people have one central email account for all their personal activity. This means that all of your social media notifications, website registrations, newsletters, receipts, messages, password resets, and more get sent to the same email box.
Having everything in one place means that if that place fails, you'll lose everything associated with it. If someone breaks into it, they'd be able to access all of the above kinds of media. And remember that when you reset a password on most sites, the link to reset it goes to your email. This could allow someone to lock you out of all your own accounts.
To combat this, it's a smart idea to use separate email accounts for different purposes. This will help boost your security by limiting the damage someone could do by breaking into one account. It's even better if you use secure email services for your most important accounts.
Plus, doing so can also boost your productivity. You could consolidate all your work emails into a single work account, friends and family communication with your personal account, have a recreational account for various websites, then a throwaway account for potential spam links.
This way, if someone hacks your work account, all of your personal emails are still safe.
2. Set a Unique, Strong Password
No matter if you stick with one email account or use multiple as above, it's vital to protect each one with a strong password. Reusing the same password on multiple accounts is a major vulnerability. If an attacker breaks a password, they'll certainly try it on other accounts using your email address.
While it seems simple, many people don't follow this basic advice. The best way to improve your security in this area is to start using a password manager. These let you create strong and unique passwords for every account that you don't have to remember.
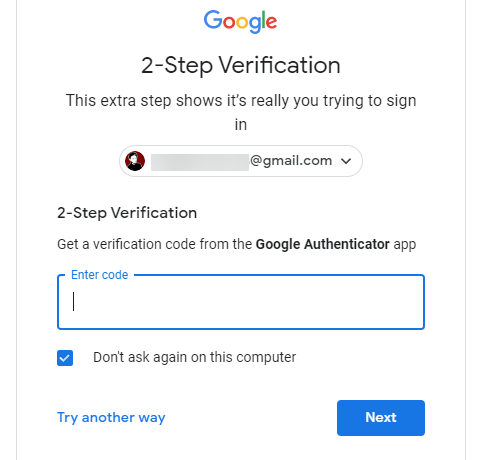
3. Enable Two-Factor Authentication
Along with a strong password, you've probably heard the advice about using two-factor authentication (2FA) before. And while using it is a little inconvenient, it drastically increases the security of your account. In addition to your password, 2FA requires a secondary code (usually from your phone) to log in.
As mentioned above, because your email is the key to every other account, you should at least use 2FA there even if you don't enable it anywhere else.
Follow our guide to setting up 2FA on major accounts for information on how to do it. For best results, we recommend using an authenticator app like Authy. This generates offline codes that you use to approve new account logins after entering your password.
4. Beware of Phishing Scams
Legitimate companies will not ask you for your password or other sensitive information over email. While you might be able to spot blatant attempts to steal your information, scammers have gotten better at creating convincing phishing messages.
Typically, phishing emails claim to come from a legitimate entity (like Amazon, Apple, PayPal, or similar) and tell you that something is wrong with your account. They prompt you to click a link that leads to a fake website. If you enter your credentials there to "confirm" the information, you're actually handing the data over to thieves.
You should know how to spot a phishing email to avoid falling for these common schemes.
5. Never Click Links In Emails
The widespread nature of phishing means that it's wise to follow a general rule: when in doubt, never click links inside emails. While you can hover your mouse over a link to preview the destination URL, this isn't foolproof. Most email fraud relies on you clicking a link that takes you to a phony website, so clicking links is always a risk.
At best, clicking a link will let the scammer know that your email is active and that you're willing to click on links. At worst, it could bring you to a site that tries to install malware on your computer or wants to steal your information.
If you get an email claiming to come from your bank or any other service that asks you to sign in, always visit the website manually to see what's going on. The only exceptions are when you're explicitly expecting a particular email, such as a forum registration link or game account activation email.
6. Don't Open Unsolicited Attachments
Most of the time, you should treat attachments in emails like links. If you're expecting something from a friend, then you're probably fine to open the attachment. However, if the email is unsolicited, you shouldn't open any of its attachments.
Even if the file looks innocent, it could be a hidden danger. It's trivial to spoof filenames and extensions to make a nasty EXE look like a JPG, for example. A lot of ransomware distributes through email attachments, so opening one could begin the encryption process on your system.
Follow our guide to spotting unsafe email attachments so you don't make a costly mistake.
7. Scan for Infections Regularly
If you read an email, open an attachment, or visit a linked website that seems suspicious in any way, it's not a bad idea to run a malware scan. Of course, not every spam email will infect your machine, and it's probably overkill to run a scan every time you open a fishy message.
It's better to be safe, though. Make sure you have a reliable antivirus suite installed (Windows Defender is fine for Windows 10) and consider installing Malwarebytes for a second opinion. If you unknowingly enabled a keylogger, you'd rather know sooner than later.
8. Be Careful on Public Networks and Computers
You probably know that public Wi-Fi isn't as secure a connection as your home network. And while you'll probably be OK checking your email on airport or cafe Wi-Fi, you should still take caution when using such networks.
Thanks to widespread use of HTTPS, your activity on most websites will be safe from prying eyes elsewhere on the network. However, if you don't own the network, you can't be certain of how it's set up. The network could be a spoofed point, or have malicious software installed to allow for man-in-the-middle attacks.
The same goes for logging into your email on public computers, like those in libraries and hotels. Someone could install a keylogger on those machines to steal your credentials, so it's best to stick with trusted devices like your phone when at all possible.
Safe Use of Email Is Essential
While the web has become more secure over time thanks to widespread use of HTTPS, stronger encryption protocols, and better automated detection from email providers, a lot of your personal security still lies with your decisions. Take some time to lock down your email accounts and your online safety will become a lot stronger because of it.
In short, don't click anything from an email that you weren't expecting, and make use of the various account security options email providers offer. Doing so will make your account much safer to use. If you're not convinced, find out what scammers could do with access to your email account.