Removing malware can be a pain. Malware removal guides ease the process, but it remains tedious. And so is dealing with the after effects of removing it.
Did your Internet stop working or were your browser settings messed up after you removed a virus from your computer? Malware can cause havoc while being active and it can put up a fight before it is finally eradicated. Many times, that malware will attempt to mess up your Internet settings so that you will not be able to access it anymore. You do not have to throw out your computer or re-install Windows because of this -- here are four things you can do to try to fix the problems.
Browser Settings: Homepage, Search Engine, Add-Ons
First off, make sure that all of the settings in your browser are at the values that they should be. This not only includes literally going through the "Settings" dialog, but it also includes making sure that the home page and default search engine are what they should be. You can follow our browser homepage guide, which details how to check and reset the homepage in five common browser.
To change your default search engine, refer to the following page for each browser: Chrome, Firefox, Internet Explorer.
Toolbars, a possibility for Internet Explorer and Firefox, may also appear after malware has touched your system. If you're using Internet Explorer, toolbars most likely need to be removed via the Windows Add/Remove Programs tool. Firefox toolbars usually appear as add-ons, and can be removed via the respective menu.
Additionally, you should check whether all of your extensions are still installed, and more importantly, remove undesired ones.
If nothing was been changed in your browser, or if you returned everything to its original values and you are still not able to normally access the Internet, the malware pulled some sneakier tricks.
Hosts File
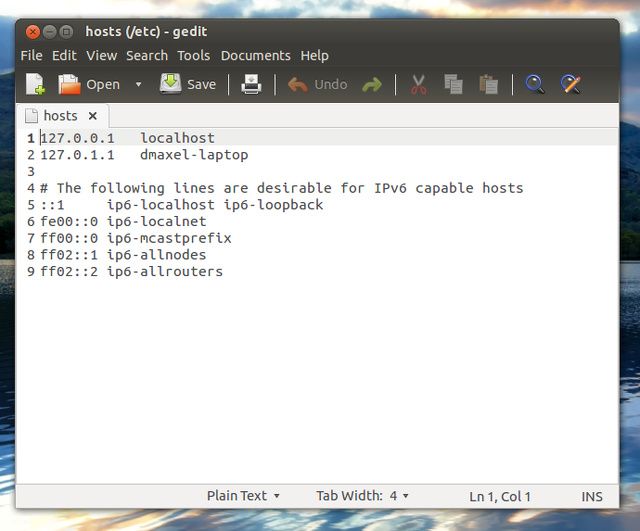
All operating systems have a hosts file which can be used to force certain address resolutions to take place (as well as some other surprising uses). This would allow the malware to take you to a phishing site when you type in a regular web address, and more widespread rules could block Internet access altogether. Check your hosts file to make sure there are no entries, which could mess with your system. You can find the hosts file in these locations:
- Windows: C:\Windows\system32\drivers\etc\hosts
- Mac OS X and Linux: /etc/hosts
Remember that you will most likely need administrative permissions in order to edit this file and save changes to it. In Windows, you can do this by finding Notepad, right clicking it, and choosing "Run as administrator". For Mac OS X and Linux, you should be able to use "sudo" in combination with your favorite text editor in a terminal.
Essentially, what you are doing is looking for any strange entries. A Windows hosts file should not have anything uncommented in it (so no lines without a # in front of it). Some resolutions for localhost and your hostname into 127.0.0.1 are acceptable, however, because those are commonly found on Unix hosts files, which is where the concept of a hosts file originated form.
DNS Settings
If the hosts file is all clear, there is one more common place to check: your DNS settings.
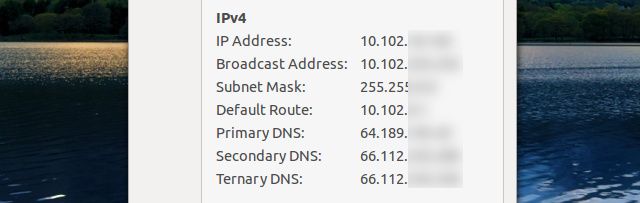
Sometimes, malware goes far enough to switch your DNS settings. A DNS server is a remote server, which can help turn web addresses such as "http://www.facebook.com" into an actual IP address, which the computer can use to access Facebook. If the malware's creator put a lot of effort into their creation, they could have potentially set up their own malicious DNS server and have the malware change infected computers' DNS settings to point to it. Also, it could have simply changed them to invalid values, leaving no DNS resolution whatsoever.
From the Windows desktop, you can check your DNS settings by right-clicking on the network tray icon in the bottom right of your screen, choosing "Open Network and Sharing Center", click on "Change adapter settings" on the left side of the window, right-click on the network adapter you're using and choose "Properties", then scroll down in the list and select "Internet Protocol Version 4 (TCP/IPv4)" and click on "Properties". At the bottom of this window you'll see your DNS settings.
Make sure that this value is the recommended value -- it is either your ISP's DNS server addresses, your router's IP address, or a custom DNS server. If you don't know what to put here, it is recommendable to set it to "Obtain DNS server address automatically" or to use Google's DNS server. The two values for their DNS servers are 8.8.8.8 and 8.8.4.4.
The Last Resort: Second Opinion & Reinstallation
If, after all of these steps, your system is still wonky or your Internet access is altered, try using a second or third antivirus or anti-malware tool. They may discover and remove malware traces that your first choice did not catch. It may also help change a few obscure Internet settings that are hard to reach, such as the amount of pipelines your browser can use at a time (the number of simultaneous requests).
If, after all this, you are still struggling, it's best to reinstall your operating system and start fresh. Make sure you have a backup of your important data and scan every single file you have backed up for malware, so that you do not reinfect your system later. While it is the most inconvenient way of getting your computer to work again, sometimes it really is the only choice you have left.
What is the nastiest malware you have had to deal with? What advice could you give to your fellow readers? Let us know in the comments!