System logs in Linux provide you with great insight into core activities on your PC or server infrastructure. They're critical for keeping your system stable and secure. System logs also provide you with an opportunity to audit various activities that have taken place in the past.
This guide introduces you to the logging system in Linux. All the major activities carried out by core system applications and services are recorded in the form of logs and at the heart of all this is a system known as Syslog.
Why are System Logs Important?
Imagine that your Linux PC has recently been experiencing startup errors or you suspect that someone has been trying to log onto your system. These events can be easily traced as your system keeps track of such activities in the form of logs.
In Linux, system logs are human-readable records of the core system activities performed by services, daemons, and system applications. Some of the important activities logged on a Linux machine include user logins and login failures, operating system booting, system failures, etc.
Linux has a dedicated service known as Syslog that is specifically responsible for creating logs via the System Logger. Syslog comprises of several components such as the Syslog Message Format, Syslog Protocol, and the Syslog Daemon: popularly known as syslogd or rsyslogd in newer versions of Linux.
The /var/log directory stores most of the logs on a Linux system. The /var directory mostly contains variable files and directories i.e data that is bound to change often. There is no standard format for logs but at the minimum, logs should contain a timestamp and the details of the activity being logged.
Listing Files Managed by syslog
All general logs on your system are stored in the /var/log/syslog file on Debian-based Linux distros. Other distributions use the /var/log/messages file for storing logs.
Note: Different Linux distros may use different files for logging specific messages. For example, on Debian-based Linux distros, the /var/log/auth.log file contains authentication logs, while RedHat systems use the /var/log/secure file to store such logs.
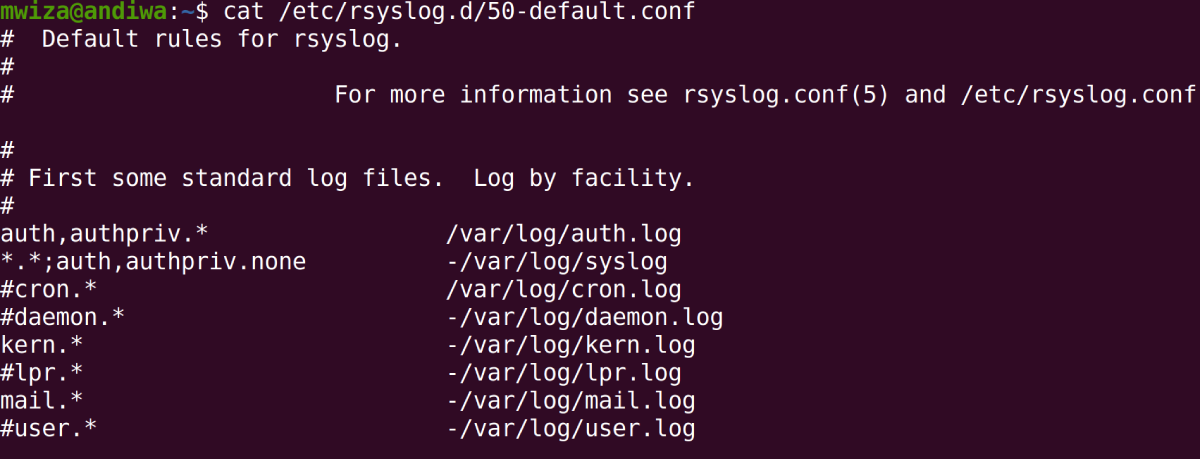
To find out more about all the files that are responsible for storing logs, you can take a look at the /etc/rsyslog.d directory, which contains important Syslog configuration files. For example, to list standard log files, you can take a look at the /etc/rsyslog.d/50-default.conf file.
cat /etc/rsyslog.d/50-default.conf
The file shows you the names of the system applications and the corresponding log files associated with them.
How to Inspect Log Files
Most log files are pretty long. As such, one of the most important commands for inspecting log files on Linux is the less command, which outputs file content in easily navigable sections.
For example, to view the contents of the /var/log/syslog file, use the less command as follows.
less /var/log/syslog
Use the F keyboard key to scroll forward and the B key to scroll backward.
The syslog file contains logs of some of the most critical activities such as system errors and service activities on your system.
If you only want to inspect the most recent logs you can use the tail command, which only lists the last 10 log messages by default.
tail /var/log/syslog
You can also specify the number of log messages that you want to view with the tail utility. The command takes the following format tail -n file-to-inspect, where n is the number of lines you want to view. For example, to view the last 7 log messages in the syslog file you can use the following command.
tail -7 /var/log/syslog
To view the most recent logs in real-time, you can use the tail command with the -f option as follows.
tail -f /var/log/syslog
Another important command for inspecting log messages is the head command. Unlike the tail command which displays the last log messages in a file, the head command shows you the first lines in a file. By default, the command will output the first 10 lines only.
head /var/log/syslog
Authentication Logs
If you want to find information about user logins on your system, you can take a look at the /var/log/auth.log file. Information related to user logins, login failures, and the authentication method used can be found here.
Kernel Logs
When your Linux system boots, important data about the kernel ring buffer is recorded in the /var/log/dmesg file. Other information about hardware drivers, kernel, and boot status is all recorded in this file.
Instead of inspecting the boot log messages with the less or cat command, you can use dmesg to view these log files.
dmesg
Note: Log messages in the /var/log/dmesg file are reset whenever the system boots.
Another important log file related to kernel issues is the /var/log/kern.log.
Logging Messages With the logger Command
Apart from just viewing log messages logged by system applications or services, the logging system in Linux also allows you to log messages manually using the logger command. A user can log messages to the /var/log/syslog file by default. For example, to log a simple message you can run the following command.
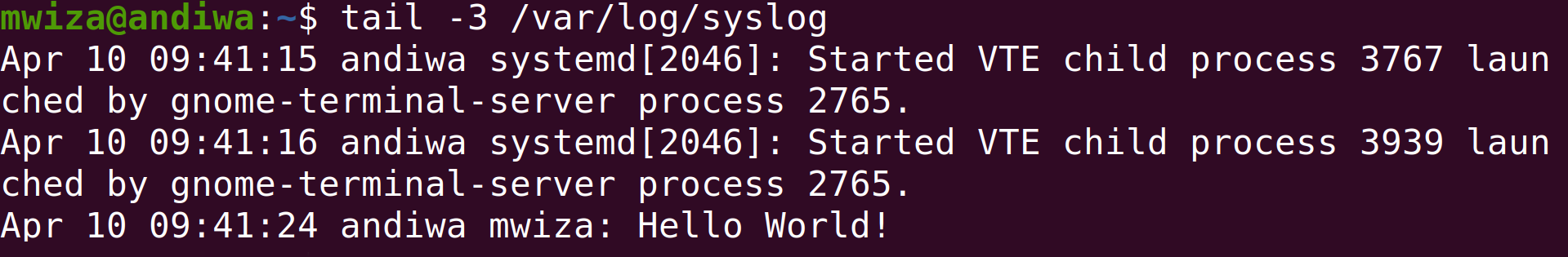
logger hello world!
You can now use the tail command to view the recently logged message.
tail -3 /var/log/syslog
You can even log the output of other commands with the logger command by enclosing the command within the back-tick (`) character.
logger `whoami`
You can also use the logger command within your scripts to log important events. Use the man pages to learn more about the logger command and its options.
man logger
Managing Log Files
As you might have noticed, there is a lot of data that gets logged on a Linux machine. Therefore, you need to have a proper system in place to manage disk space used by the log files. In addition to that, having a logging system ensures that you find the log messages that you are looking for easily. Linux's solution to this problem is the logrotate utility.
Use the logrotate utility to configure what log file to keep, how long you want to keep them for, manage the mailing of logs, and how to compress old log files, etc.
You can configure the logrotate utility with any text editor of your choice. The config file for logrotate can be found at /etc/logrotate.conf.
Keeping Your System Robust With Logs
System logs in Linux are a great way to get insight into the major activities happening on your system that can comprise security and overall stability of the system. Knowing how to view and analyze log messages on a server or PC will go a long way in helping you keep your system robust.
Sometimes, users find it hard to use certain applications on their system because of the low availability of system resources. In such situations, killing unresponsive programs can free up space on your system's main memory.