Microsoft recently explained in greater depth how the SolarWinds cyberattack took place, detailing the second phase of the attack and the malware types in use.
For an attack with as many high-profile targets as SolarWinds, there are still many questions that need answering. Microsoft's report reveals a trove of new information on the attack, covering the period after the attackers dropped the Sunburst backdoor.
Microsoft Details Second Phase of SolarWinds Cyberattack
The Microsoft Security blog provides a look into "The missing link," the period from when the Sunburst backdoor (referred to as Solorigate by Microsoft) was installed at SolarWinds to the implanting of various malware types within the victim's networks.
As we already know, SolarWinds is one of the "most sophisticated and protracted intrusion attacks of the decade," and that the attackers "are skilled campaign operators who carefully planned and executed the attack, remaining elusive while maintaining persistence."
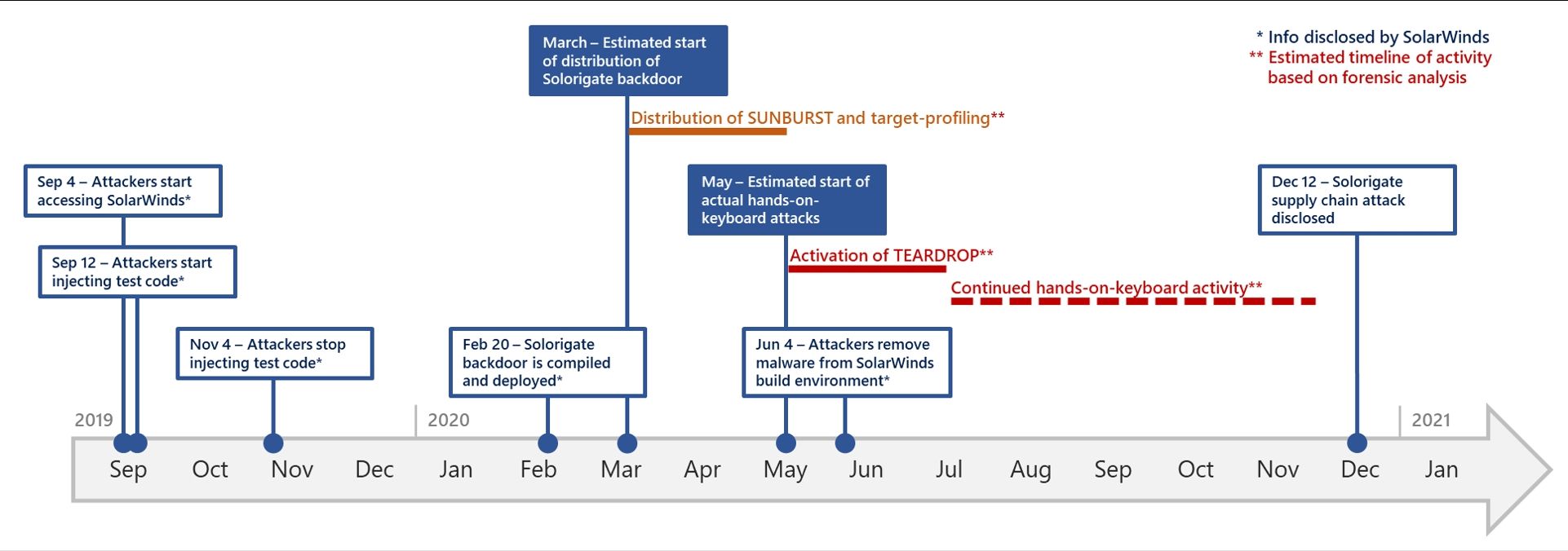
The Microsoft Security blog confirms that the original Sunburst backdoor was compiled in February 2020 and distributed in March. Then, the attackers removed the Sunburst backdoor from the SolarWinds build environment in June 2020. You can follow the full timeline in the following image.
Microsoft believes the attackers then spent time preparing and distributing custom and unique Cobalt Strike implants and command-and-control infrastructure, and the "real hands-on-keyboard activity most likely started as early as May."
The removal of the backdoor function from SolarWinds means that the attackers had moved from requiring backdoor access through the vendor to direct access to the victim's networks. Removing the backdoor from the build environment was a step towards disguising any malicious activity.
From there, the attacker went to great lengths to avoid detection and distance each part of the attack. Part of the reasoning behind this was that even if the Cobalt Strike malware implant was discovered and removed, the SolarWinds backdoor was still accessible.
The anti-detection process involved:
- Deploying unique Cobalt Strike implants on each machine
- Always disabling security services on machines before proceeding with lateral network movement
- Wiping logs and timestamps to erase footprints, and even going as far as to disable logging for a period to complete a task before switching it back on.
- Matching all file names and folder names to help camouflage malicious packages on the victim's system
- Using special firewall rules to obfuscate outgoing packets for malicious processes, then removing the rules when finished
The Microsoft Security blog explores the range of techniques in far greater detail, with an interesting section looking at some of the truly novel anti-detection methods the attackers used.
SolarWinds Is One of the Most Sophisticated Hacks Ever Seen
There is little doubt in the minds of Microsoft's response and security teams that SolarWinds is one of the most advanced attacks ever.
The combination of a complex attack chain and a protracted operation means that defensive solutions need to have comprehensive cross-domain visibility into attacker activity and provide months of historical data with powerful hunting tools to investigate as far back as necessary.
There could still be more victims to come, too. We recently reported that antimalware specialists Malwarebytes were also targeted in the cyberattack, though the attackers used a different method of entry to gain access to its network.
Given the scope between the initial realization that such an enormous cyberattack had taken place and the range of targets and victims, there could yet be more major tech companies to step forward.
Microsoft issued a series of patches aimed at reducing the risk of SolarWinds and the associated malware types in its January 2021 Patch Tuesday. The patches, which have already gone live, mitigate a zero-day vulnerability that Microsoft believes to link to the SolarWinds cyberattack and was under active exploitation in the wild.