SSH and FTP are two of the most exploited network protocols. Hackers utilize complex automated tools to guess your username and password and then break into your system.
With good security practices in place, you can mitigate most of the security risks. And with Fail2ban, you can further reduce the risk of security breaches by being proactive in securing your Linux servers or PCs.
What Is Fail2ban?
Fail2ban is a powerful open-source security software that dynamically protects your servers or PCs from suspicious activities and brute-force attacks. It continuously scans your log files for login attempts, and in case of any, it blocks the source IP address by updating your firewall rules.
Fail2ban works with most remote connection services such as SSH, FTP, SMTP, and HTTP.
Fail2ban is easy to configure and customize. You can specify for how long you want to block the IP addresses or configure it to receive automated alerts when there is suspicious activity.
To emphasize, Fail2ban alone is not enough to protect you from security breaches. You should also have other security measures in place to reduce the risk of being hacked. For example, you should always use strong passwords on your systems and restrict access as much as you can.
How to Install Fail2ban on Linux
Most of the major Linux distros including Red Hat Enterprise Linux (RHEL), Ubuntu, and Arch Linux support Fail2ban. Here’s how to install Fail2ban on your Linux distro:
On Arch Linux and its derivatives:
sudo pacman -S fail2ban
To install Fail2ban on Ubuntu and Debian:
sudo apt install fail2ban
Installing Fail2ban on Fedora and RHEL is easy:
sudo dnf install fail2ban
Next, you'll need to enable the Fail2ban service. This way the process will run in the background whenever your system boots.
sudo systemctl enable fail2ban.service
To finalize the installation, start the Fail2ban service using the following command:
sudo systemctl start fail2ban
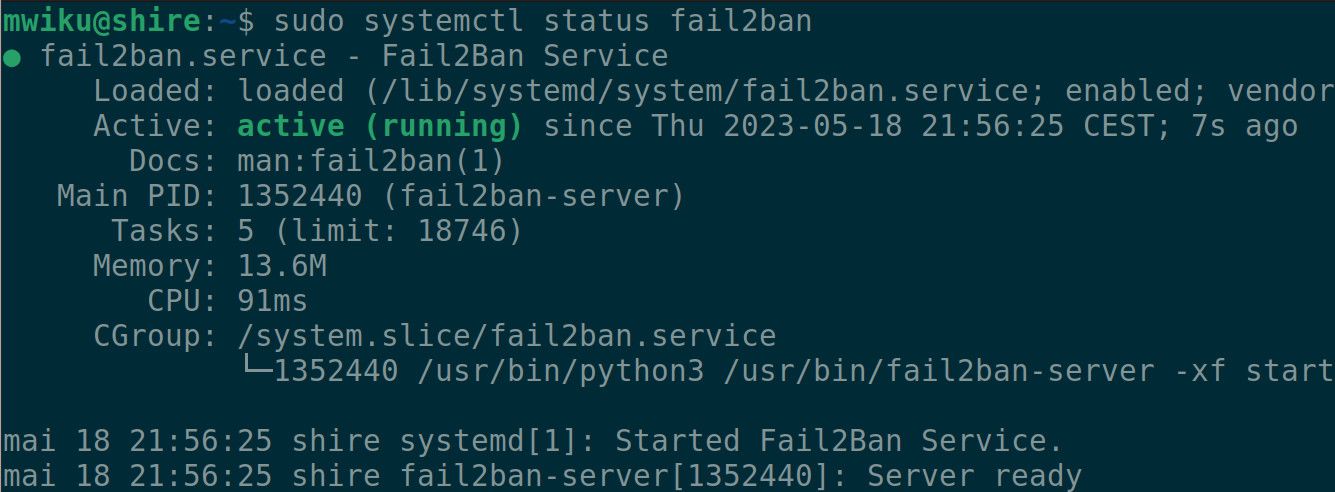
You can verify that the Fail2ban service is up and running with:
sudo systemctl status fail2ban
If everything is okay, the service should be up and active. If there are any error messages, you can look at the Fail2ban log messages using the journalctl utility:
sudo journalctl -u fail2ban
Configuring Fail2ban on Linux
Finally, you can start configuring Fail2ban to protect your system from brute-force attacks and other suspicious activities.
The /etc/fail2ban/jail.conf file stores the main Fail2ban configurations. As a best practice, avoid making changes to this particular file. Only use it as a reference.
Whenever you update Fail2ban, the jail.conf configuration file will be overwritten. To avoid losing your configuration, make a copy named jail.local within the same folder. Use the powerful cp command for this:
cd /etc/fail2ban && cp jail.conf jail.local
Next, open the jail.local file using your favorite text editor and adjust the following configurations:
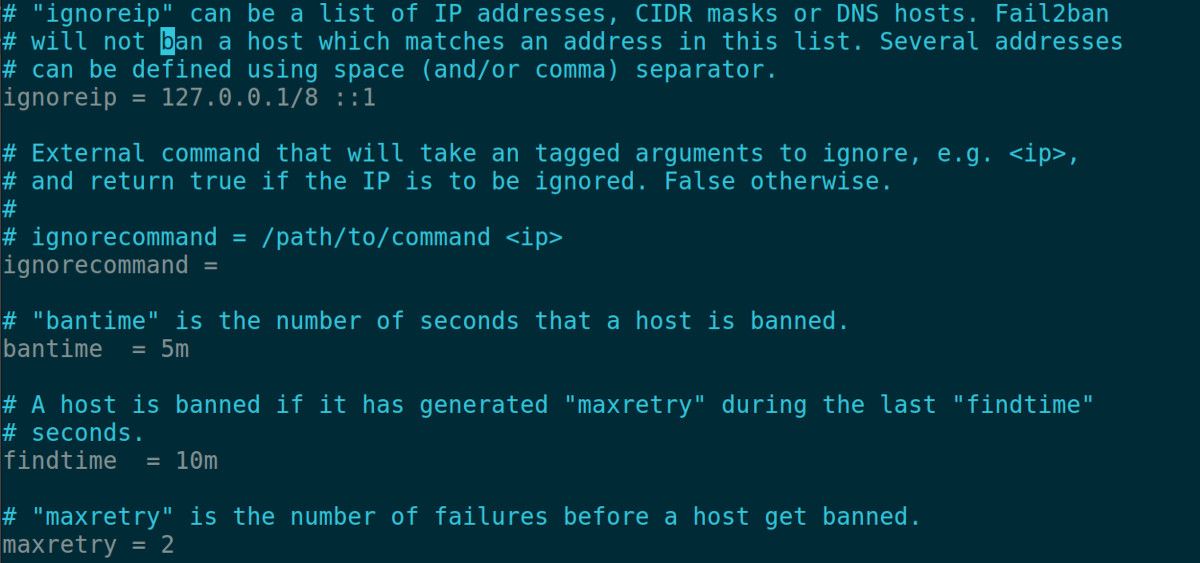
- ignoreip: Use it to specify a list of IP addresses that you want to be exempted from the Fail2ban rules.
- bantime: The bantime parameter defines a period in which an IP address should be banned. This can result from multiple failed login attempts or other suspicious activity. Set this to five minutes (5m).
- maxretry: Use this to specify the number of login failures before you can ban a host. For testing, let's set this to 2.
The configuration file is well documented, so read through it to learn more about Fail2ban and the options that it presents.
Finally, restart the fail2ban service for the changes to take effect. Use the command:
sudo systemctl restart fail2ban
Testing the Fail2ban Configuration
With the configuration set up, you can test if the maxretry configuration is working. Try to SSH login to the PC or server you have configured.
When requested for login credentials, supply the wrong password, twice. Fail2ban will kick into action and block you for five minutes, as configured.
This is just a simple use case; now proceed to configure your server to your liking, and feel free to experiment.
Add an Extra Layer of Security to Your Linux Server or PC
Fail2ban is a powerful and very configurable security tool. Use it to proactively protect your servers or PCs from brute-force attacks.
In addition to having Fail2ban, use strong passwords and configure your firewall for better security. You can also protect your home or office network by using a reputable firewall system.