Whether you're a Linux administrator or user, having a secure server or PC should be a top priority. Although Linux is a secure operating system, it is also susceptible to attacks or security breaches just like other OSes.
In this guide, you'll learn how to audit and scan for security vulnerabilities and loopholes on your Linux machine using Lynis. Lynis is an open-source tool and is available on most Unix-based operating systems such as Linux, macOS, Solaris, FreeBSD, etc.
How Does Lynis Work?
Lynis performs health and security scans on your PC or server to enhance security hardening and compliance testing.
Lynis is modular and only tests the components on your computer that it can find; for example, systems tools and their corresponding libraries.
One of the main advantages of Lynis is that it does not require you to install it in order to perform an audit. You can simply run it from a configuration folder if you wish, so your system remains in a very clean state.
All Lynis audits are custom, that is, every audit is unique depending on your system configuration, installed software, and other factors. The more components available on your system, the more extensive the audit report will be.
In addition to displaying audit information on your screen, Lynis also stores technical information in the lynis.log file. A separate file named lynis-report.dat stores suggested actions and warnings. Both of these log files are located in the /var/log/ directory.
Lynis audit reports give you much insight and knowledge on the security measures that you should take in ensuring that your system remains secure, robust, and hardened from potential security attacks.
Installing Lynis on Linux
There are several methods by which you can run or install Lynis on Linux, but to keep things simple, we'll take a look at two of the most popular methods.
1. Installing Lynis via a Package Manager
You can easily install Lynis using the default package manager on your system, depending on your Linux distro.
On Debian-based Linux distros such as Ubuntu, simply run:
sudo apt install lynis
On RHEL-based Linux distros such as Fedora and CentOS:
sudo dnf install lynis
On Arch-based Linux distros:
sudo pacman -S lynis
You can check the version of Lynis installed using the following command:
sudo lynis --version
Note: You need elevated privileges using either sudo or su to run Lynis commands.
2. Running Lynis Directly From Source
For the most minimal footprint on your PC, you can run Lynis from the tarball file without installing it.
Simply download the Lynis tarball file and extract it using the tar command. Then go into the extracted folder and run a Lynis audit as follows:
sudo ./lynis audit system
Download: Lynis
Auditing a Linux Machine With Lynis
Auditing is one of the most common use cases of Lynis among system administrators, system auditors, and other security professionals.
You can start an audit of your system by running the following command:
sudo lynis audit system
Lynis first profiles your computer system, that is, it checks what operating system you are using, the kernel, hardware, and other important parameters for conducting the audit.
How to Examine Lynis Audit Reports
Lynis audits are categorized into sections to make it easy for you to understand the outcome of the audit.
For example, some of the important categories include:
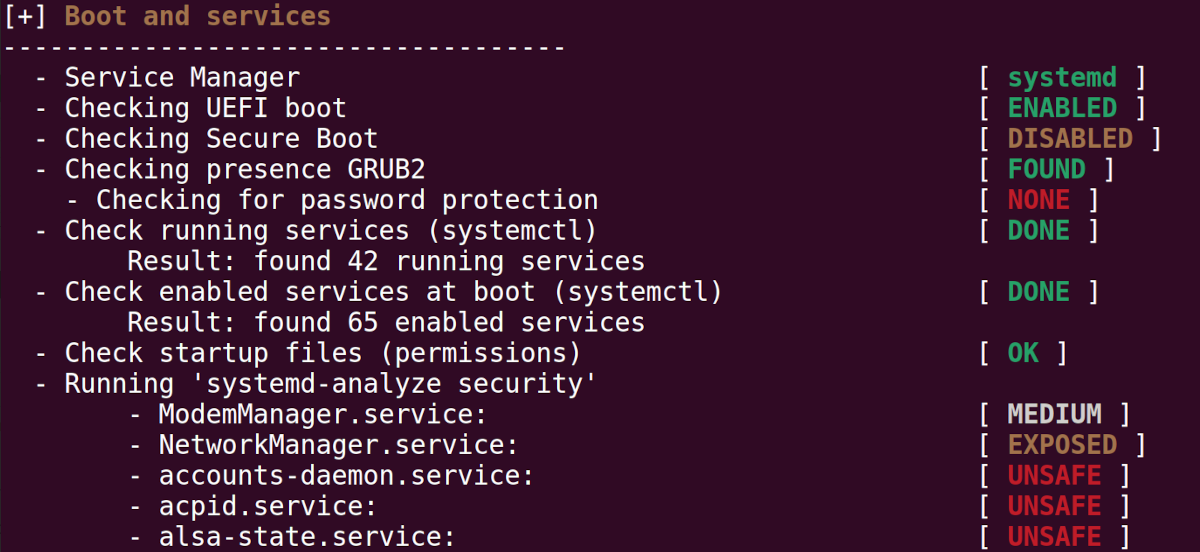
- Boot and Services: In this category, Lynis gives you an overview of the boot process and the service manager in use on your system, e.g. systemd, OpenRC, etc. Lynis will also show you how many services are currently running and the ones that are enabled at boot time. Finally, you'll be shown which services pose a security threat to your system because they are unsafe or exposed.
- Users, Groups, and Authentication: Lynis scans your user administrator accounts, checks for password strength and expiry, and also examines if important files such as /etc/passwd and PAM config have proper permissions and are secure.
- USB Devices: Checks for USB devices and authorization methods in place to protect your system.
- Ports and Packages: Here Lynis will give you an overview of unsafe and open ports that infiltrators can use to exploit your system over the network. It'll also inform you of outdated packages that can pose a security risk.
- Logging and Files: Lynis checks if the logging daemon is up and running. In addition, it checks the availability and security of important log files on your system.
Apart from these categories, Lynis also checks your network, file systems, shells, memory and processes, and other critical parts of your system.
Color Coding
Further to the categorization, Lynis uses three main color codes to show the severity of a security loophole or potential security risk.
Green shows that the scanned module or software is deemed to be ok and that you do not need to take any action. The remaining color codes, usually require your urgent attention to remedy the security loophole or some other form of action. For example, to update or upgrade software.
Orange shows that there is a suggestion that you should look at. For example, a software module or service is disabled, therefore Lynis could not conduct an audit. Or it could be that the software module was not found by Lynis.
The last color code is red. You should pay extra attention to report outputs marked in red. This indicates that you should urgently fix the marked item because it poses a huge threat to the security of your system.
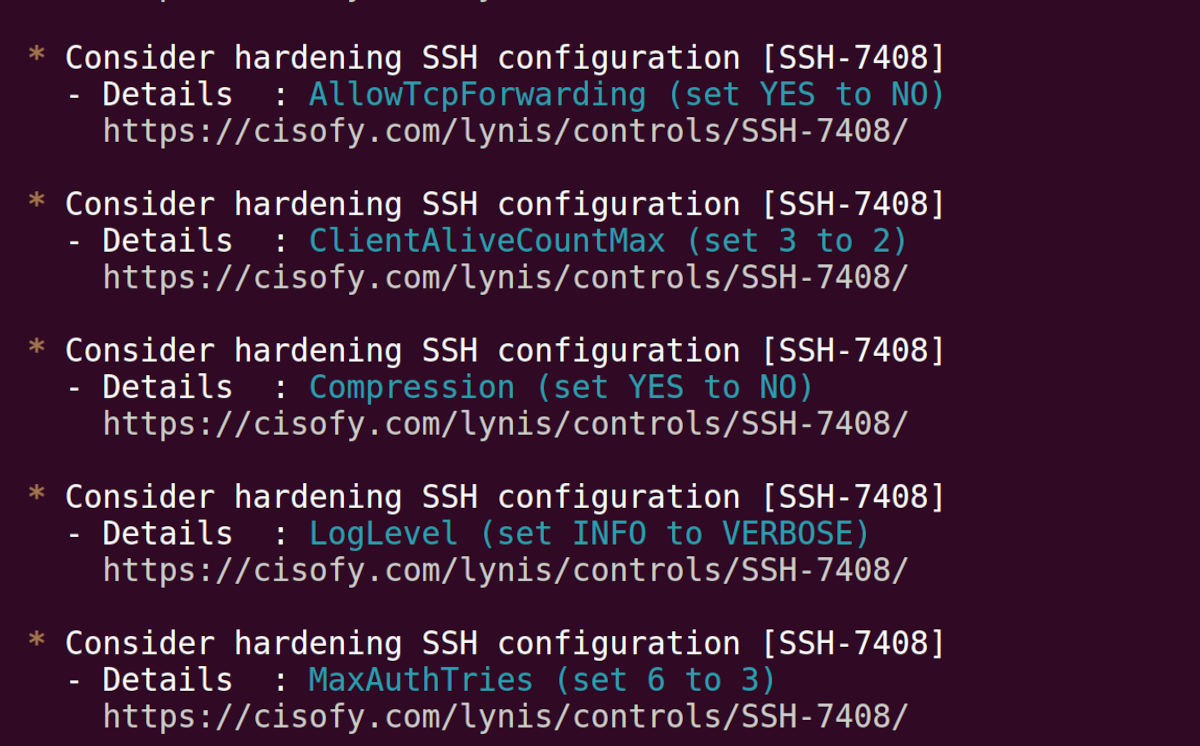
Lynis Audit Suggestions
Towards the bottom of the report, Lynis gives you suggestions with web links. Open the web links in your browser for steps or guidance on how to fulfill the suggested remedies.
Getting Help With Lynis Commands
You can learn more about Lynis and the options it provides using the following command:
sudo lynis show
You can also take a look at the man pages for more detailed info.
man lynis
Getting Started With Ethical Hacking on Linux
This guide has looked at how to audit and analyze the security of your Linux system using Lynis. Do not compromise on the security of your Linux PC or server. Always have up-to-date software and regularly audit your system.
One of the best ways to learn about systems security is by becoming an ethical hacker using Kali Linux and Raspberry Pi.