Netwalker is a strain of ransomware that targets Windows-based systems.
First discovered in August 2019, it evolved throughout the rest of 2019 and into 2020. Significant spikes in NetWalker targeted attacks were noted by the FBI during the height of the Covid-19 pandemic.
Here's what you need to know about the ransomware that has attacked major schools, healthcare systems, and government institutions throughout the US and Europe.
What is NetWalker Ransomware?
Previously called Mailto, Netwalker is a sophisticated type of ransomware that renders all critical files, applications, and databases inaccessible through encryption. The group behind it demands cryptocurrency payment in exchange for data recovery and threatens to publish the victim’s sensitive data in a "leak portal" if ransoms aren’t paid.
The group is known to launch highly targeted campaigns against large organizations, mainly using email phishing sent to entry points to infiltrate networks.
Previous samples of poisoned emails used the coronavirus pandemic as a lure to make victims click on malicious links or download infected files. Once a computer has been infected, it starts spreading and compromises all connected Windows devices.
Aside from spreading through spam emails, this ransomware can also disguise itself as a popular password management app. As soon as users run the bogus version of the app, their files will be encrypted.
Like Dharma, Sodinokibi, and other nefarious ransomware variants, NetWalker operators use the ransomware-as-a-service (RaaS) model.
What is Ransomware-As-A-Service?
Ransomware-as-a-service is the cybercrime offshoot of the popular software-as-a-service (SaaS) business model where software that’s centrally hosted on cloud infrastructure is sold or rented out to customers on a subscription basis.
In selling ransomware as a service, however, the material sold is malware that’s designed to launch nefarious attacks. Instead of customers, the developers of these ransomware seek out "affiliates" who are expected to facilitate the spread of the ransomware.
If the attack is successful, the ransom money is split between the developer of the ransomware and the affiliate who distributed the prebuilt ransomware. These affiliates normally get around 70 to 80 percent of the ransom money. It’s a relatively new and lucrative business model for criminal groups.
How NetWalker Uses the RaaS Model
The NetWalker group has been actively recruiting "affiliates" on dark web forums, offering the tools and infrastructure to cybercriminals who have previous experience infiltrating large networks. According to a report by McAfee, the group seeks out partners who are Russian-speaking and those who already have a foothold in a potential victim’s network.
They prioritize quality over quantity and only have limited slots for partners. They stop recruiting once these have been filled and will only advertise via the forums again once a slot opens up.
How Did the NetWalker Ransom Note Evolve?
Previous versions of the NetWalker ransom note, much like most other ransom notes, had a "contact us" section that used anonymous email account services. Victims would then contact the group and facilitate the payment through this.
The much more sophisticated version that the group has been using since March 2020 ditched the email and replaced it with a system using the NetWalker Tor interface.
Users are asked to download and install the Tor Browser and are given a personal code. After submitting their key through the online form, the victim will be redirected to a chat messenger to talk to NetWalker "technical support".
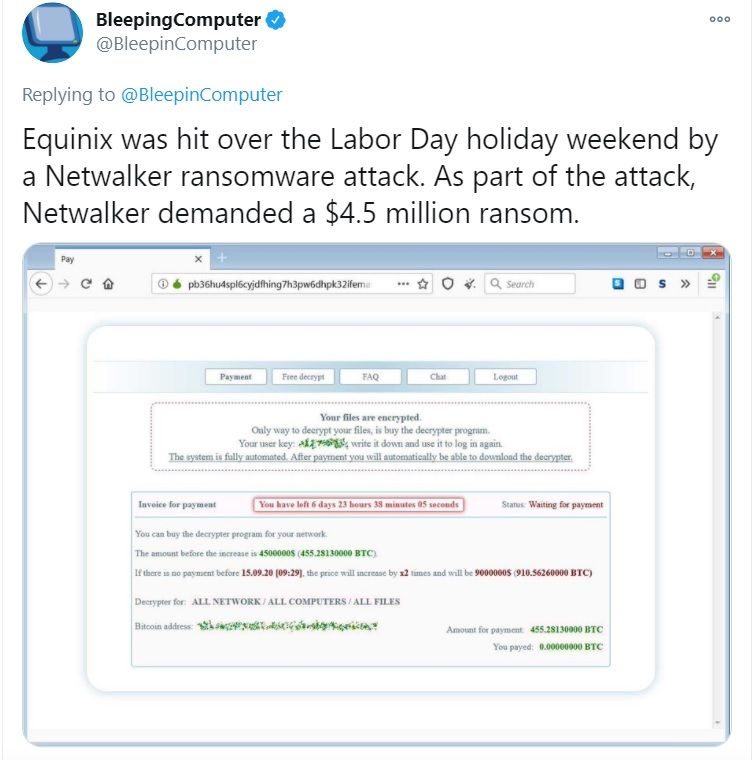
How Do You Pay NetWalker?
The NetWalker system is organized much like the companies they target. They even issue a detailed invoice that includes the status of the account i.e. "waiting for payment", the amount that needs to be settled, and the time they have left to settle.
According to reports, victims are given one week to pay, after which the price for decryption doubles—or sensitive data is leaked as a consequence of non-payment before the deadline. Once payment has been made, the victim is directed to a download page for the decryptor program.
The decryptor program appears to be unique and is designed to decrypt only the files of the specific user who made the payment. This is why each victim is given a unique key.
High-Profile NetWalker Victims
The gang behind NetWalker has been linked to a spate of attacks on different educational, government, and business organizations.
Among its high-profile victims are Michigan State University (MSU), Columbia College of Chicago, and University of California San Francisco (UCSF). The latter apparently paid a $1.14 million ransom in exchange for a tool to unlock the encrypted data.
Its other victims include the city of Weiz in Austria. During this attack, the city’s public service system was compromised. Some of their data from building inspections and applications were also leaked.
Health institutions have not been spared: the gang reportedly targeted the Champaign Urbana Public Health District (CHUPD) in Illinois, The College of Nurses of Ontario (CNO) in Canada, and the University Hospital Düsseldorf (UKD) in Germany.
The attack on the latter is believed to have caused one death after the patient was forced to go to a different hospital when emergency services at Dusseldorf were affected.
How to Protect Your Data from NetWalker Attacks
Be wary of emails and messages asking you to click on links or download files. Instead of clicking on the link right away, hover over it to examine the entire URL which should appear at the bottom of your browser. Don't click on any email links until you're definitely sure it's genuine, which might mean contacting the sender on a separate system to check.
You also need to avoid downloading fake apps.
Make sure you have reliable antivirus and anti-malware installed that’s regularly updated. These can often spot phishing links within emails. Install software patches straight away since these are designed to fix vulnerabilities cybercriminals frequently exploit.
You also need to protect your network’s access points with strong passwords and use multi-factor authentication (MFA) to protect access to the network, other computers, and services in your organization. Taking regular back-ups is also a good idea.
Should You Be Worried About NetWalker?
While it doesn’t target individual end-users yet, NetWalker can use you as a gateway to infiltrate your organization’s networks through phishing emails and malicious files or infected bogus apps.
Ransomware is a scary thing, but you can protect yourself by taking sensible precautions, staying vigilant, and