Social media phishing is a form of cyberattack using social networking sites instead of emails. Although the channel is different, the goal is the same—to trick you into giving your personal information or downloading a malicious file.
Social media is a favorite among cybercriminals because there isn’t a shortage of victims. And because of the trusted environment, there’s a goldmine of private data they can use to launch a follow-up spear-phishing attack.
Here’s how they’re doing these on some of the most popular platforms.
Facebook is the third most commonly impersonated brand for phishing attacks. With over 2.6 billion users worldwide, it’s easy to see why. The platform offers a plethora of profiles and messages teeming with personal information for phishers to exploit.
Attacks on Facebook are often targeted towards consumers and not as much on big organizations. Phishers use social engineering to lure unsuspecting victims into exposing their data.
They will pretend to be from Facebook and send emails to users about a security alert, for example. From there, users are instructed to log in to their Facebook profiles and change their password. They’re then sent to a fake Facebook login page where their credentials are harvested.
How Phishing Targets Your Friends
If they get access to your account, they can cast a wider net by victimizing your contacts. They can also use the information your friends share with you in a more targeted spear-phishing campaign.
Phishers will use your account to send out messages or post a status with a malicious link. And because your contacts trust you, there’s a bigger chance that they will click on it.
What Is Angler Phishing?
This is a type of phishing that uses social media but has a more sophisticated MO. They target users that post (mostly rants) about a service or their account. Attackers pretend to be from the service provider, then send the user a link to get in touch with a customer service representative.
But you guessed it: the link leads to a fake site to harvest information.
What used to be a selfie gallery is now a multi-million dollar business used by the world’s biggest brands and influencers.
Like phishers on Facebook, those that exploit Instagram send out emails to users warning them of a security alert. For instance, it could be a message about a login attempt from an unknown device. The email has a link that sends users to a fake site where login information is harvested.
Once they get access, they’ll have a goldmine of personal information to exploit in different ways. A sinister attack, for example, involves blackmailing you or your friends by threatening to leak photos you shared privately or through Instagram Direct Messenger (IGdm) if you don’t cave into their demands.
What Is a Copyright Infringement Scam?
If phishers get their hands on business accounts, especially verified ones, they can launch more insidious phishing campaigns through IGdm.
A verified account for a major corporation's branch in Chile, for instance, was reported by users in June 2020 for sending phishing messages.
The message alerted users of a copyright violation in a post. The rest of the message said: “If you think copyright infringement is wrong, you should provide feedback. Otherwise, your account will be closed within 24 hours.” The link for the feedback was of course a fake Instagram page collecting login information.
What Is a Blue Badge Scam?
Nothing feels as legit as having that coveted blue check. Phishers exploit this too.
One Instagram phishing scam involves sending users an email offering them a certified badge. Once the users click on the "Verify Account" button, they’re taken to a phishing page where their personal information will be harvested. Most of the time, influencers and “Insta-famous” users are targeted for this kind of attack.
Check out our guide on how to get verified on Instagram to bypass those scammers.
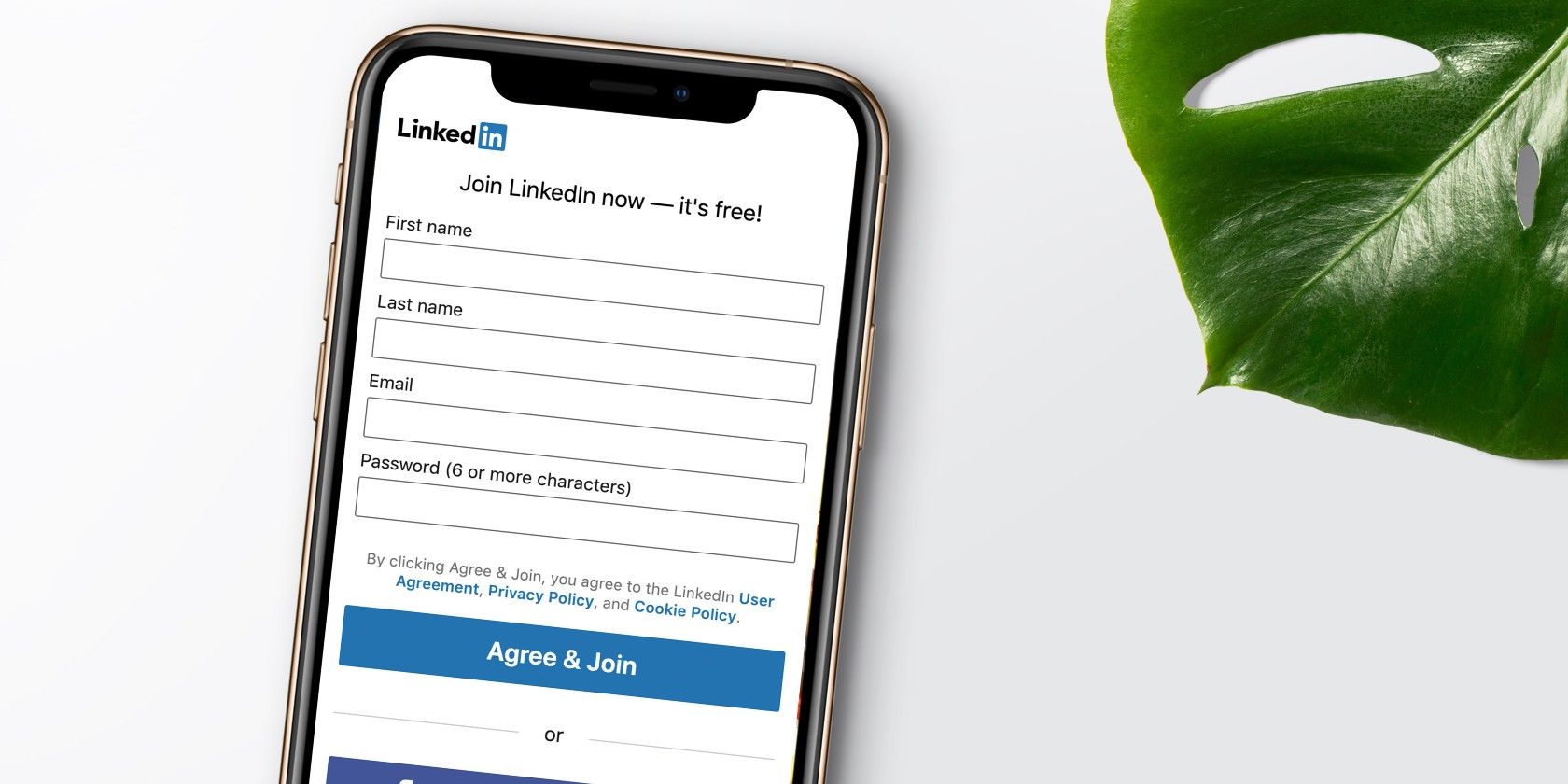
The main platform for the world's business community used by over 700 million professionals is also a favorite target of phishers.
People trust LinkedIn more than any other social networking site according to a digital trust report. Users are also more likely to post details about their jobs making them a prime target for spear phishing and whaling attacks.
How Fake Recruiters Scam LinkedIn Users
One of the cruelest social media phishing campaigns is an attack that targets job seekers on LinkedIn. Cybercriminals pose as a recruiter and reach out to users about a fake job post via LinkedIn Messaging.
Phishers lure you in by saying that your background is perfect for the role they are trying to fill. They’ll make this even more irresistible with an increased compensation package.
You’ll see a link that the phisher says has all the details about the job. Alternatively, they might send an attachment in Microsoft Word or Adobe PDF to download.
It sound exciting, especially for someone who’s looking for employment. But links lead you to a spoofed landing page and the Word file has Macros to launch malware. The latter could steal your data or open a backdoor to your system.
Have You Received Fake Contact Requests?
There are two most common fake contact requests. The first sees users receiving an email alerting them to a contact request. This comes with a link leading to a fake LinkedIn login page.
The second is more complicated: it involves creating fake accounts and sending connection requests from within LinkedIn. Once you accept the invitation, phishers have access to more information in your profile and be a step closer to all your connections.
They can then send a phishing message or use your information to launch more targeted attacks on your contacts. Being your 1st-degree contact also gives them more credibility by making their profile seem more legit.
How to Protect Yourself From Social Media Phishing
To protect yourself from these types of attacks, don’t click on links within emails and DMs. Double-check the source. Even if it seems like the message is from someone you trust, there’s a chance that their account has been compromised.
Call the person first to make sure it's real, particularly if the message contains attachments you are being asked to download.
Always check the URL of the websites you visit. Hackers produce spoofed URLs by changing one or more letters of the URL of well-known websites. They can also use symbolic letters to look like the original letters. Hover over links to examine the entire URL, which should appear at the bottom of your browser.
Remember that official correspondence from social networks and other organizations will never come from anyone using email addresses with @gmail or @yahoo domain names.
Other telltale signs to watch out for are typographical and grammatical errors or messages that rush you to take action. The latter is designed to cause fear or panic so you won’t have time to think.
Social Media Risks Your Loved Ones Too
If you expose yourself to social media phishing attacks, you risk your friends and loved ones, since hackers can use your account as a gateway to get to them too.
Fortunately, a little caution and common sense goes a long way in protecting yourself.