The parent company of password manager service, LastPass, which in late 2022 revealed that the password vaults of its entire customer base were now in the hands of criminals, has announced that encryption keys for some of its other products have been compromised too.What does this mean for its users?
What Was the 2022 LastPass Data Breach?
LastPass and its customers didn't have the best year in 2022. In August, the company announced in an understated blog post that criminals had accessed the LastPass development environment, source code, and technical information. The language was reassuring, and referred to "unusual activity" and the incident as "a development". An FAQ section reassured customers that their vaults, passwords, and master passwords were safe, while stating, "we don’t recommend any action on behalf of our users or administrators".
A month later, after an investigation in partnership with Mandiant, the original blog post was updated, to further comfort LastPass users that there was, "no evidence that this incident involved any access to customer data or encrypted password vaults", and further patronized users with the acknowledgment that, "security incidents of any sort are unsettling but [we] want to assure you that your personal data and passwords are safe in our care."
However, in late November 2022, the blog was updated yet again, in an admission that the intruders had managed to make off with, "certain elements of our customers’ information."
Finally, in a December 2022 update, LastPass owned up to the fact that criminals had managed to exfiltrate the personal data vaults of millions of customers, containing unencrypted website URLs and site names, as well as encrypted usernames and passwords, together with backup data including customer names, addresses and phone numbers, email addresses, IP addresses, and partial credit card numbers.
Again, LastPass sought to contain the reputational damage, stating that, "it would take millions of years to guess your master password using generally-available password-cracking technology."
Worse to Come for LastPass Users?
LastPass is an independent company, owned by GoTo (an SaaS provider, formerly known as LogMeIn), and while the LastPass breach has garnered the most attention, the initial penetration was of a third-party cloud storage service, which is used by both GoTo and LastPass. As LastPass was compromised, so was GoTo. Threat actors managed to exfiltrate encrypted backups from both companies.
On January 23rd 2023, GoTo released a statement on its blog stating that it has "evidence that a threat actor exfiltrated an encryption key for a portion of the encrypted backups", and additionally that Multi-Factor Authentication (MFA) settings of a small subset of their customers were impacted.
What this means is that the criminals can easily decrypt their stolen goods without needing to wait millions of years to do so.
It's uncertain whether LastPass vault encryption keys have also been exfiltrated.
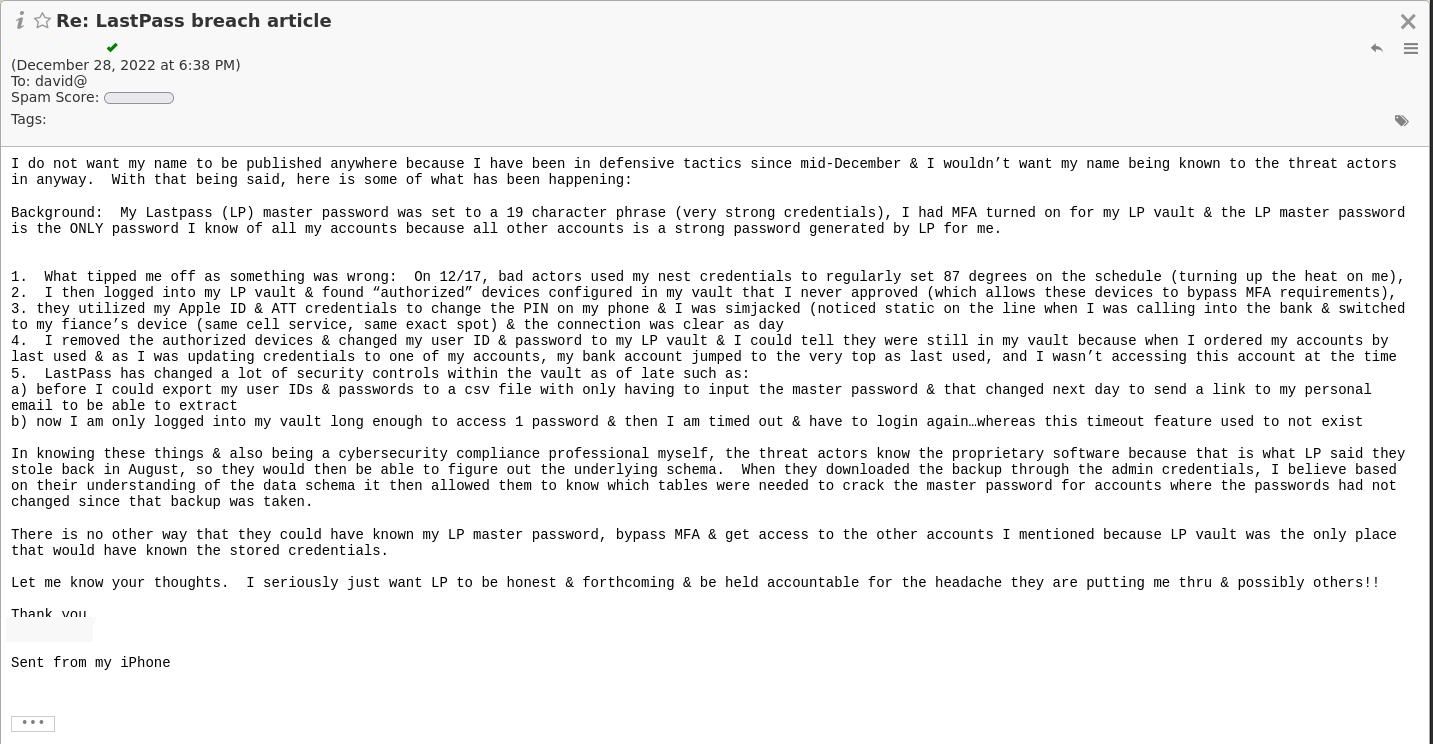
Reports of LastPass Vaults Being Compromised
Almost as soon as the December update was published, MUO was contacted by readers claiming that one-off passwords stored only in LastPass vaults were being used by criminals to access online accounts, resulting in SIM-swapping attacks.
On Twitter, users reported that crypto wallets were being attacked and drained of their contents—those seeds were reportedly stored solely in LastPass vaults.
As yet, LastPass has not addressed these rumors, nor the revelations of its parent company.
GoTo has at least started to contact affected users and all passwords have been automatically reset.
Change Your Passwords for Everything
Password management services exist to keep your passwords safe and unguessable. If criminals have the keys to that vault, then your passwords are anyone's to use as they wish.
The first thing you should do is to change your passwords for every service you've ever accessed online. Where possible, you should use a unique username and email address too.
It's never a good idea to entrust your deepest secrets for someone else to safeguard. BitWarden is a password manager you can host on your own hardware, and which will generate usernames, email aliases and passwords for each site you visit. As you run it on your own machine, you don't have to leave your passwords to the dubious care of another company.