Zoom's popularity has soared, largely thanks to the coronavirus pandemic. In December 2019, it reported 10 million users. By April 2020, that rose to 300 million. Its stock price increased by more than 500 percent over the course of the year. It has now become an essential app for businesses, groups of socially-distant friends, and even entire families.
But is Zoom safe? Stories about the app's security and privacy issues have been lurking throughout its rise. Let's take a closer look at some of the biggest Zoom security concerns you need to know about.
1. Zoom-Bombing
Yes, Zoom-bombing is a thing. Much like photo-bombing, which sees people insert themselves into unsuspecting people's snaps, Zoom-bombing refers to the practice of users logging into Zoom calls that they were not invited to.
But how is Zoom-bombing possible? Zoom uses a unique meeting ID number for every chat on its platform. The number is between nine and 11 digits long and is used to get access to a conference.
However, meeting ID numbers can be easily guessed. As a result, pranksters are joining calls and creating havoc using features such as screen sharing. At best, it's very annoying. At worst, it compromises your data, especially if you are on a confidential business call.
The solution is simple—set a password for every Zoom call you participate in. Zoom has also introduced a way to suspend participants' activities, meaning you can boot imposters out of your call.
Read our comprehensive guide to Zoom-bombing to learn more.
2. Unsecure Desktop Apps
If you want to use Zoom on a desktop machine, you have two options: the desktop app or the web app. You should always use the web browser version; this gets new security enhancements much faster than the desktop app.
And aside from the updates, the web version is still more secure. That's because it lives in a browser's sandbox, meaning it has far fewer permissions and a reduced ability to cause issues across your entire operating system.
If you'd prefer to use an app for Zoom, consider Skype for Business. It has a secure Zoom integration.
3. False End-to-End Encryption Claims
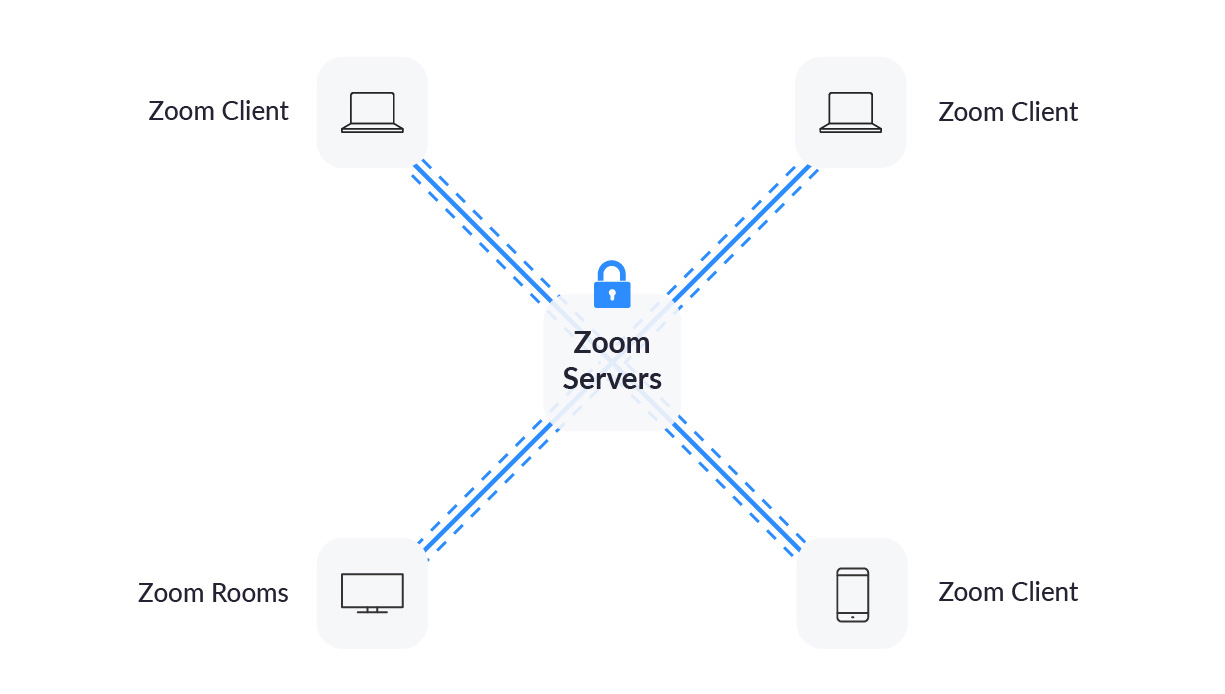
At the start of 2020, Zoom heavily advertised its end-to-end encryption as a key feature. In theory, that means that all communications between you and the other people in your chat would only be visible to those parties; nobody could decrypt them.
The claims were quickly shown to be false. Data was encrypted, but only between you and the Zoom servers.
While that means that snoopers and local hackers on your public Wi-Fi network would not be able to see your calls, Zoom employees could see everything. Therefore, if a government or law enforcement agency were to request access to your chats, they could easily get them.
In late October 2020, Zoom did finally roll out true end-to-end encryption, but the entire episode left a bad taste and showed Zoom could not be trusted as a business.
Head to Settings and toggle Allow use of end-to-end encryption to enable the feature.
4. Installers With Bundled Malware
The Zoom installer has been widely copied and redistributed. Many of those redistributions had malware bundled in with the installer in an attempt to trick unsuspecting users.
The most famous example is the cryptocurrency-mining malware that was found in Zoom installers in April 2020. If installed, it would eat through your CPU and GPU in a bid to mine Bitcoin, leaving you with little free power to do anything else on your machine.
This flaw isn't Zoom's fault. But it shows how hackers will target anything that's "hot" at a given moment and exploit it. To protect yourself, make sure you only ever download Zoom from the company's official site.
5. Leaked Passwords
When you hear the phrase "leaked passwords," you probably assume the service provider is at fault. However, in this example, Zoom is not to blame.
According to an academic paper from the University of Texas and the University of Oklahoma, people on your Zoom call could theoretically tell what you are typing by watching the movements in your arms and shoulders.
Of course, all forms of video streaming, including Skype and Twitch, are also vulnerable.
All the hacker would need to do is record your call in 1080p and then feed it through a computer program that strips the background. By monitoring your arms and shoulders relative to your head, they would be able to tell exactly what keystrokes you had made.
The lesson? Never log into your accounts while on a call. If you do need to enter a password, you should briefly disable your video feed while you type. Wearing sleeves, covering your shoulders, and touch-typing with 10 fingers also increases the difficulty of this method for hackers.
6. Endless Security Flaws
Zoom has a long list of security flaws. Many of them have now been fixed, but it raises the question of how many more undiscovered vulnerabilities are still available for hackers to exploit.
Here's a quick rundown of some of the most headline-worthy Zoom flaws and security breaches in 2020 alone:
- In June, Talos revealed that a hacker could force malware installations via the Zoom app using an animated GIF.
- In the same month, Talos learned Zoom did not scan the contents of compressed files for malware.
- In May, Trend Micro found two instances of corrupt Zoom installers that could open up backdoor access to a PC and spy on its owner. One of them involved a botnet.
- Consumer Reports said Zoom's privacy policies exposed users to all kinds of shady data collection. "[Zoom] can collect data while you're in a videoconference, combine it with information from data brokers and other sources to build consumer profiles, and potentially tap into the videos for purposes like training facial recognition systems," the report said.
- Twitter users discovered private chats on Zoom were not really private at all. Instead, "private" conversations were appended to the transcript that hosts receive at the end of a meeting.
- In April, Citizen Lab found that meeting attendees in a Zoom waiting room could still get the meeting's encryption key by using a hack.
- Also in April, Intsights discovered that 500,000 stolen Zoom passwords were up for sale on the dark web after hackers used a technique called credential stuffing.
If you need more information, check out our list of ways to make your Zoom calls more secure.
Should You Use a Zoom Alternative?
Given all the Zoom security issues, should you think about using an alternative instead? Sadly, it's not so simple.
Firstly, Zoom is far from being the only video conferencing app with security issues. Services such as Google Meet, Microsoft Teams, and Webex have all received flack from security experts over privacy concerns.
Secondly, Zoom is now the most popular video conferencing app by some distance. All the people you want to talk to will be on the platform. Much like leaving Facebook or WhatsApp, you won't be able to enjoy the same level of communication with friends and colleagues if you use a different app.