Pegasus spyware from the notorious NSO Group is used by governments and other powerful actors across the globe to spy on journalists, lawyers, business people, scientists, politicians, activists, and even their friends and relatives.
A leaked database of 50,000 phone numbers belonging to suspected victims was analyzed by Forbidden Stories and Amnesty International. Some devices examined by investigators show evidence of Pegasus attacks. The NSO group disputes the findings and claim its software is only intended for use against criminals.
So what does Pegasus spyware do? And how can you check whether it's on your iPhone?
How Does the Pegasus Spyware Infect Devices?
The spyware can attack iPhones and Android devices remotely using “zero-click” methods without users doing anything.
Pegasus can be installed via WhatsApp, iMessage, a silent SMS, missed calls, and other currently unknown methods.
What Can the Pegasus Spyware Do?
The spyware allows attackers complete access to your data and allows them to do things even you, the owner, are restricted from doing. All your messages, emails, chats, GPS data, photos, and video, and more can be silently sent from your device to whoever is interested in you.
Attackers can use your microphone to record your private conversations and use the camera to secretly film you.
How Can I Remove Pegasus Spyware?
At the moment, there is no sure way to remove Pegasus. It’s unclear if even a factory reset would work as the spyware may persist in the lower levels of a system’s code.
If your phone is infected, the best solution may be to change your device and number. Of course, a new Android or iPhone could be compromised easily as your previous one, although Apple has released the iOS 14.7.1 update which is thought to address some of the exploits involved.
Are There Serious Alternatives to iOS and Android Phones?
At the time of writing the mobile OS ecosystem suffers a serious lack of diversity and even hardened Android forks such as Graphene OS or Calyx may offer no protection. Security-through-obscurity might be applicable in this case and a device running Sailfish OS from Jolla or perhaps a Librem 5 running Pure OS are the main alternatives.
How Can I Check if My iPhone Has Been Infected With Pegasus Spyware?
Fortunately, Amnesty International released a tool called MVT that lets users check if their device has been attacked by NSO malware. Although the command line tool is designed for forensic investigators, some of the detection is automated and should provide enough information to decide if it’s worth investigating further, even if you’re not a security professional.
At the moment, iPhones seem to be the most common target and investigators have also found that the Apple devices provide the most detailed evidence of intrusions. Read on for our guide to installing and using the detection software with your iPhone.
What Do I Need to Check My iPhone for Pegasus Spyware?
To simplify the process and allow you to run the tool on macOS, Linux, or Windows, we’re going to use a Docker container specially prepared for MVT. So, first, you’re going to need to install Docker on your machine. We have instructions for installing Docker on Ubuntu and how you can boot Ubuntu on your Windows or Apple computer.
How Do I Set Up My Computer to Check My iPhone for Pegasus?
We give each command step-by-step below and multi-line commands should be typed in full before pressing the enter key.
First, open a terminal and create a folder to hold the files we’ll be using by typing this command and pressing enter:
mkdir Pegasus
Then move to the Pegasus folder by typing:
cd Pegasus
Now you need to create folders for MVT. Type:
mkdir ioc backup decrypted checked
Next, you need to get a file containing indicators of suspicious behavior. Enter:
wget https://raw.githubusercontent.com/AmnestyTech/investigations/master/2021-07-18_nso/pegasus.stix2 -O ioc/pegasus.stix2
Your next step is to retrieve the MVT Docker file. Type:
wget https://raw.githubusercontent.com/mvt-project/mvt/main/Dockerfile -O Dockerfile
Now, to set up the Docker image, type:
docker build -t mvt
How Do I Prepare My iPhone for MVT Analysis?
First, you will probably want to stop your iPhone display from switching off during the process. Tap the Settings icon, then tap Display & Brightness > Auto-Lock > Never to make sure your iPhone display stays on.
Next, plug your iOS device into your computer’s USB port. You now need to stop the USB daemon which handles connections between your computer and your iOS device. Type:
systemctl stop usbmuxd
You may have to wait a bit for this process to finish and return you to a $ command prompt. Now run the Docker container by typing this entire command:
docker run -it --privileged --rm -v /dev/bus/usb:/dev/bus/usb --net=host \
-v $PWD/ioc:/home/cases/ioc \
-v $PWD/decrypted:/home/cases/decrypted \
-v $PWD/checked:/home/cases/checked \
-v $PWD/backup:/home/cases/backup \
mvt
Press enter after mvt. You are now working inside the Docker container and your command prompt should change to something like: root@yourmachine:/home/cases# Start the USB daemon again by entering:
usbmuxd
Your iPhone should display a message asking if you want to trust the computer, so press Trust and enter your iPhone passcode if requested.
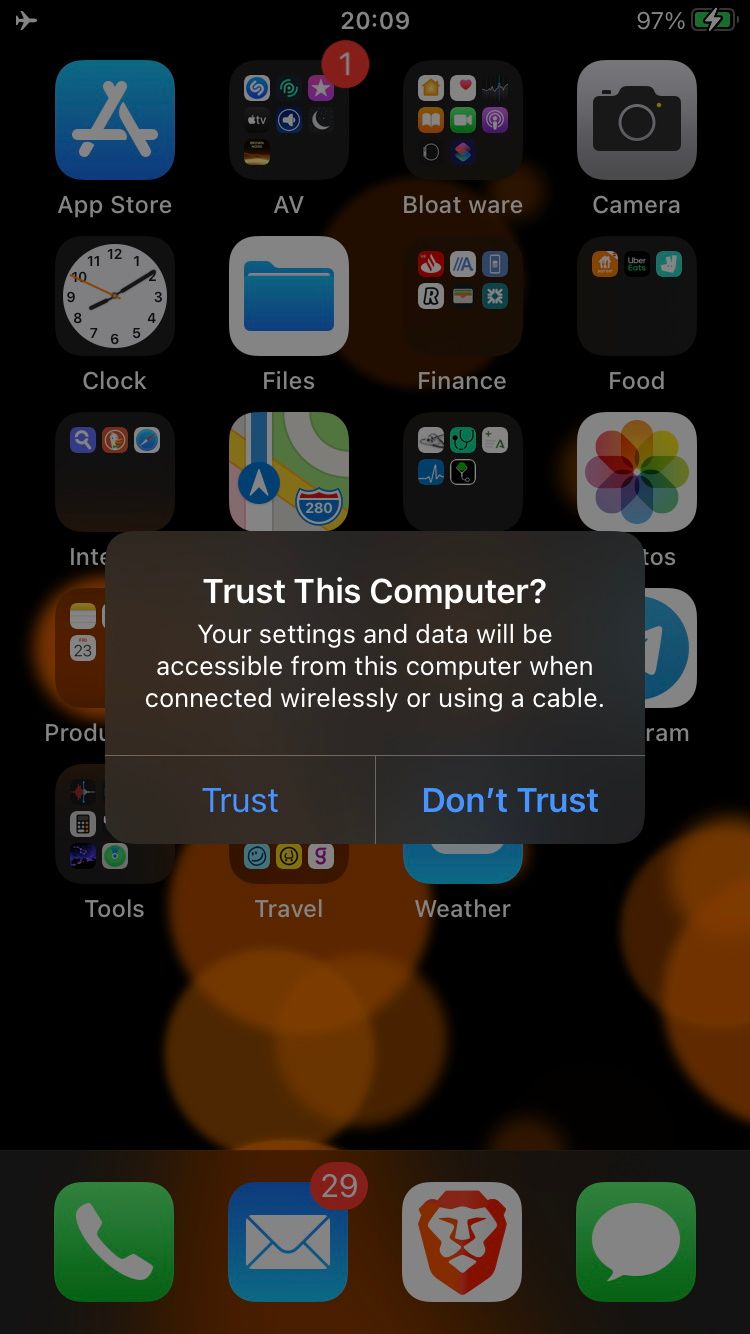
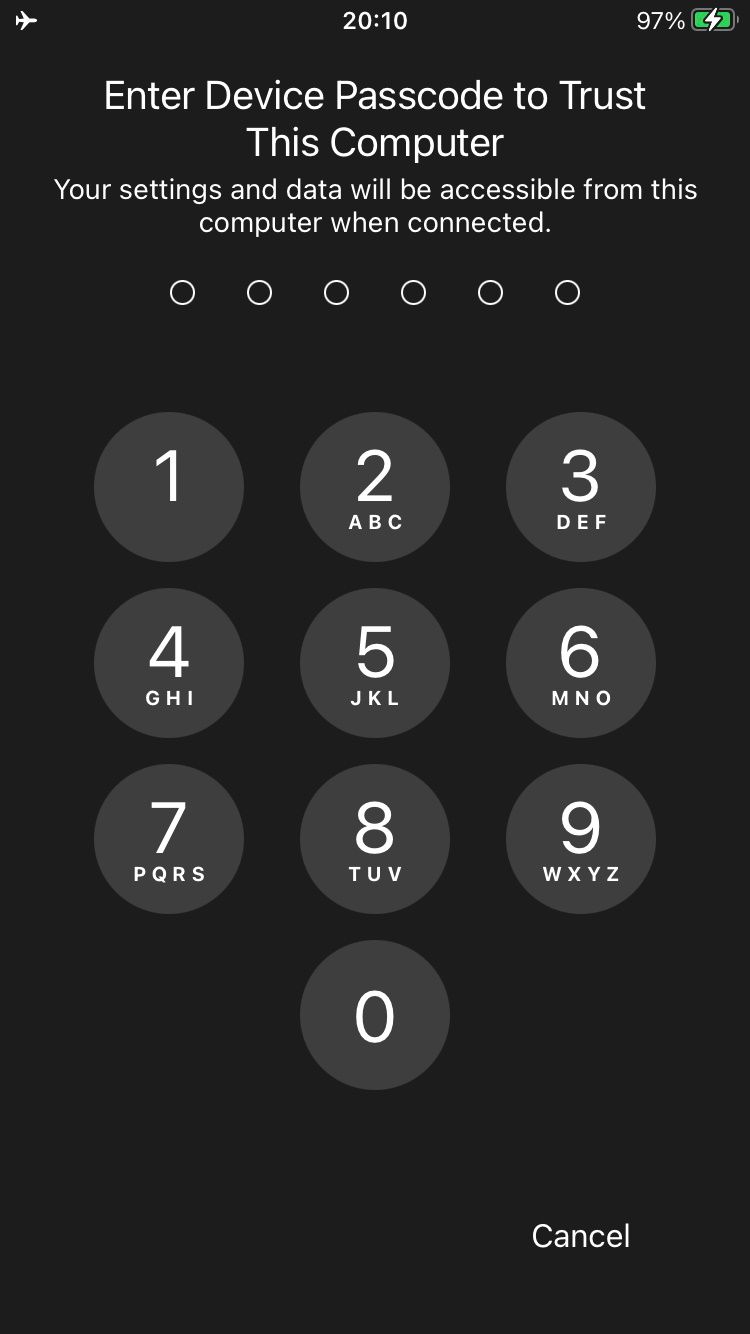
Verify that your iPhone is connected to your computer by typing:
ideviceinfo
A successful connection should spit out reams of technical data into the terminal. If you get a "device not detected" error, try restarting your iPhone and repeating the command.
You’re now ready to perform a backup to your computer. An encrypted backup allows the process to gather more information from the device, so if you do not have a password protecting your device you need to turn encryption on by typing:
idevicebackup2 backup encryption on -i
If you already have encryption enabled the terminal will tell you this. If not, choose a password and enter it when prompted. Now to run the backup, type:
idevicebackup2 backup --full backup/
Depending on how much information is on your device, this procedure could take quite a bit of time. To confirm the backup has been successful enter:
Run ls -l backup
This should give you the name of the backup which you will need for the next step. Now the backup is on your computer you can decrypt it by typing:
mvt-ios decrypt-backup -p <enter your backup password here> -d decrypted backup/<enter backup folder name here>
The command you enter should look something like this:
mvt-ios decrypt-backup -p password1234 -d decrypted backup/4ff219ees421333g65443213erf4675ty7u96y743
With the backup decrypted you can proceed to the analysis stage. To analyze the backup, the MVT tool will compare it against a stix2 file containing examples of malicious activity. To run the comparison use:
mvt-ios check-backup -o checked --iocs ioc/pegasus.stix2 decrypted
MVT will then create a series of JSON files containing the results of the comparison. You can check these results with this command:
ls l checked
Now open the folder called "checked" inside the main Pegasus folder. Look for any JSON files with _detected at the end of their filenames. If there are none, then the tool was unable to find evidence of a Pegasus infection. If _detected files exist you may want to copy the folders named backup, decrypted, and checked to a secure encrypted location for future reference.
To exit the Docker container, type:
exit
What if MVT Finds Evidence of a Pegasus Attack?
If there are some files marked _detected, then it’s probably time to contact a cybersecurity professional and change your phone and number.
You should keep your infected phone as evidence, but turn it off and keep it isolated and far from any important conversations, preferably in a Faraday cage.
You should de-authorize your phone from all online services and use another machine to change the password on all accounts accessed through the suspect device.
How Can I Protect My iPhone From Pegasus?
This spyware uses many attack methods known and unknown, but there are some steps you can take to reduce your chances of being compromised:
- It should go without saying that you need to secure your phone with a PIN or preferably a strong password.
- Update the operating system regularly.
- Uninstall apps you don’t use to minimize the attack surface. Facetime, Apple Music, Mail, and iMessage are known to be vulnerable to the Pegasus infection, but you probably use at least a couple of them.
- Reboot your phone at least once a day as this can clear the spyware from RAM and make life more difficult for it to work properly.
- Don’t click on links in any messages from unknown numbers, even if you are expecting a parcel delivery.
Pegasus: Should You Be Worried?
Pegasus is one of the worst examples of spyware we’ve seen so far. While the number of people reportedly affected so far is not huge on a global level, the fact that attackers can target one device with such zero-click methods means all devices with the same operating systems are vulnerable.
It may only be a matter of time before other groups replicate Pegasus techniques and this should be a wake-up call to everyone to take mobile security much more seriously.



