Burp Suite is a powerful vulnerability scanner developed by Portswigger used to test web application security. Burp Suite, which comes with distributions like Kali and Parrot, has a tool called Intruder, which allows you to perform automated special attacks against online applications for ethical hacking. The Intruder is a flexible and configurable tool, meaning you can use it to automate any task that comes up in testing applications.
So how does it actually work?
Using the Target in Intruder
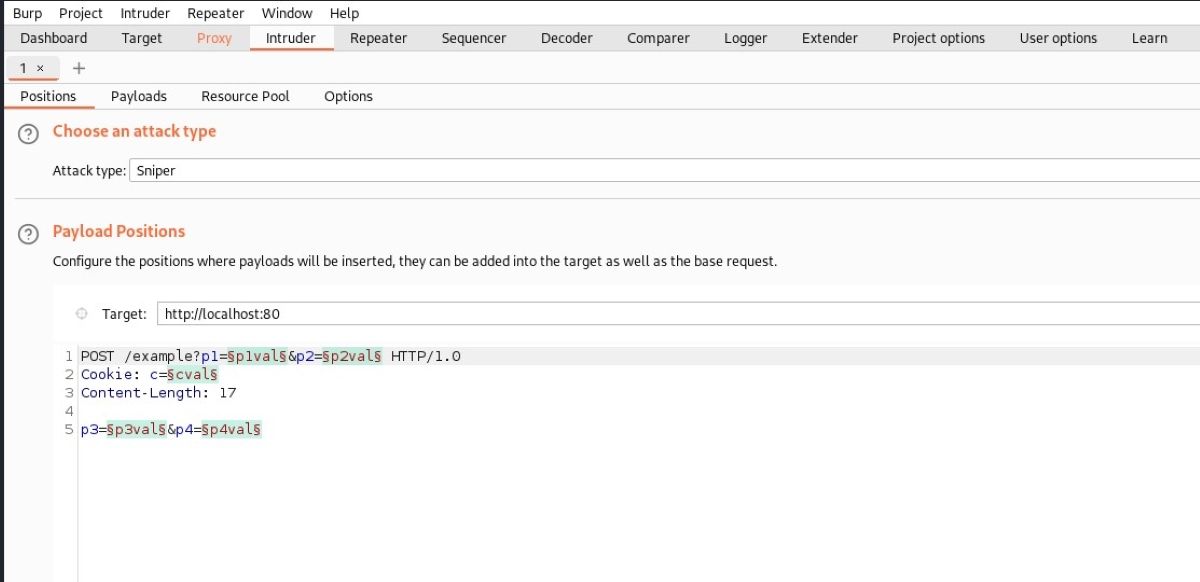
Target, which you can see when you come to the Intruder tab in Burp Suite, contains information about the target website or application you want to test. You can enter the host information and port number as the target under the "Payload Positions" section.
Using the Positions Tab in Intruder
In the Positions tab, you can see the attack types, the request template, and the parameter information to be targeted. Here are the types of attacks you can test using Burp Suite.
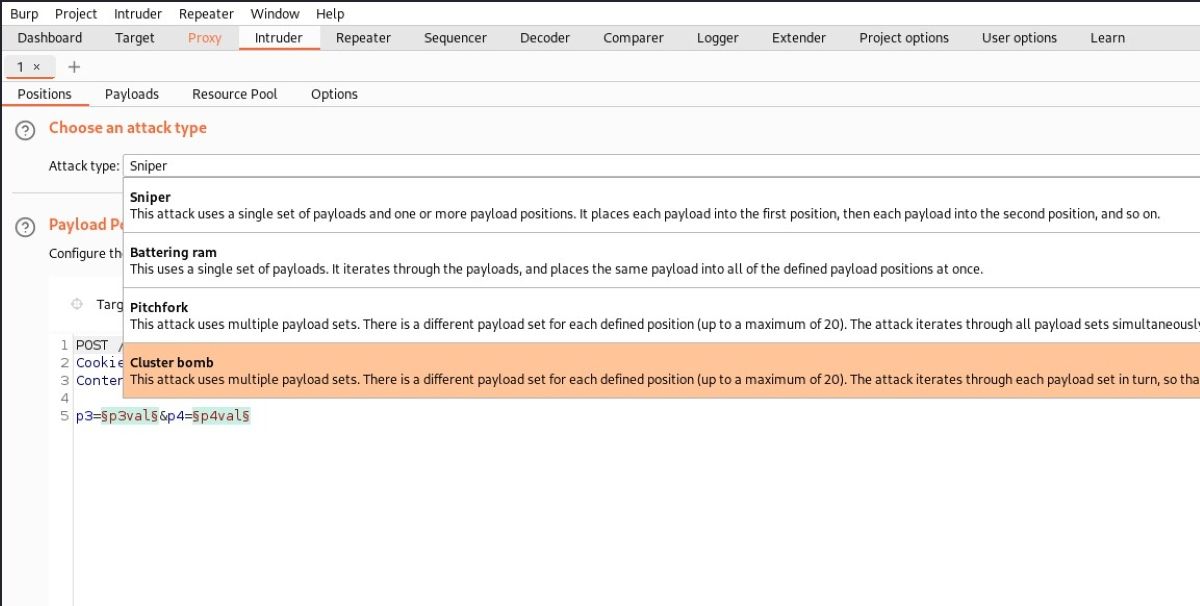
Sniper: This option uses only one parameter. Untargeted parameters are not affected in this case.
Battering ram: This option uses a single attack vector for all targeted parameters. That is, if there are three targeted parameters in the request template, it attacks all three using the same attack vectors.
Pitchfork: In this option, it is possible to use more than one attack vector for all targeted parameters. If you think that there are three targeted parameters in the request template, the first request would be to select and place the first element of the first list for the first parameter; the first element of the second list for the second parameter; and the first element of the third list for the third parameter. In the second request, the elements to be selected will be the second element of each list. You can use this attack type when placing different vectors on multiple target parameters.
Cluster bomb: You can employ more than one attack vector for all targeted parameters using this option. The difference between it and the Pitchfork option is that a cluster bomb allows you to adjust all combination distributions. It doesn't make sequential choices as Pitchfork does. Trying every possible combination of target parameters can result in a massive request load. As a result, you must exercise caution when using this option.
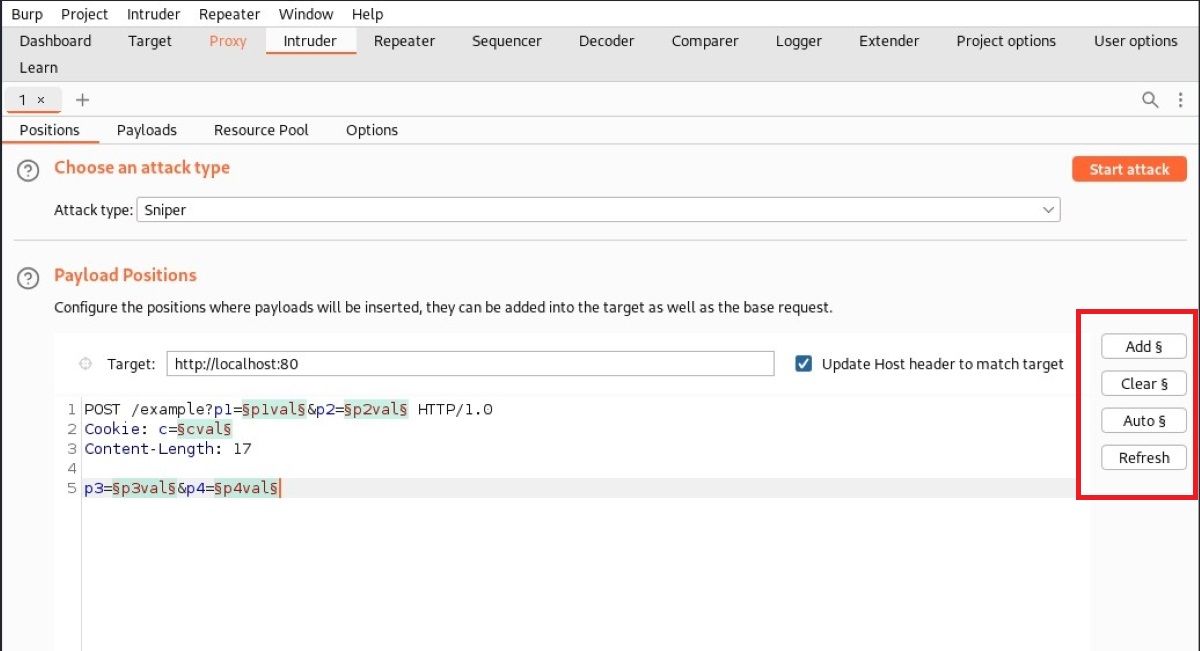
There are some other useful buttons on the Positions screen. You can remove any selected parameter with the Clear button on the right. If you want to target a new one, you can use the Add button on the right too. Use the Auto button to automatically select all fields or return to their original state.
What Is the Payloads Tabs in Burp Suite?
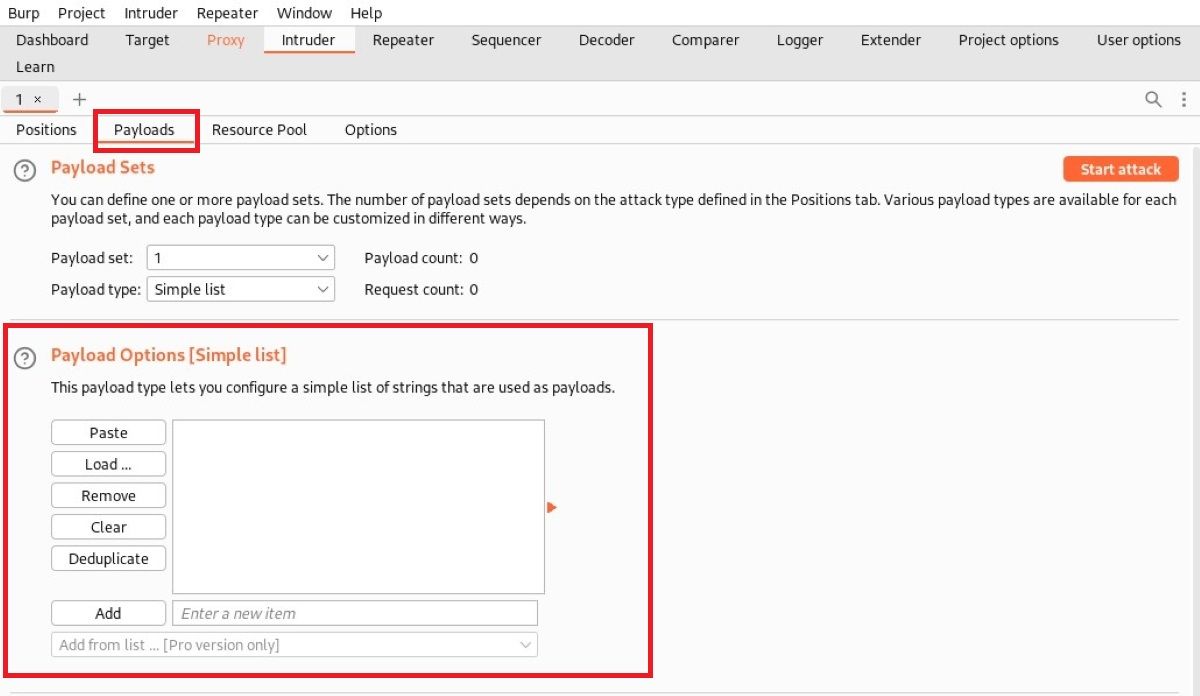
Think of payload lists like wordlists. You can use the Payloads tab to set up one or more payload lists. The number of payload sets varies depending on the attack type.
You can define a payload set in one or more ways. If you have a strong wordlist, you can import your wordlist by selecting the Load button from the "Payload Options" section.
You can also prepare separate payload sets for the targeted parameters. For instance, you can use only numeric expressions for the first target parameter, while you can use complex expressions for the second target parameter.
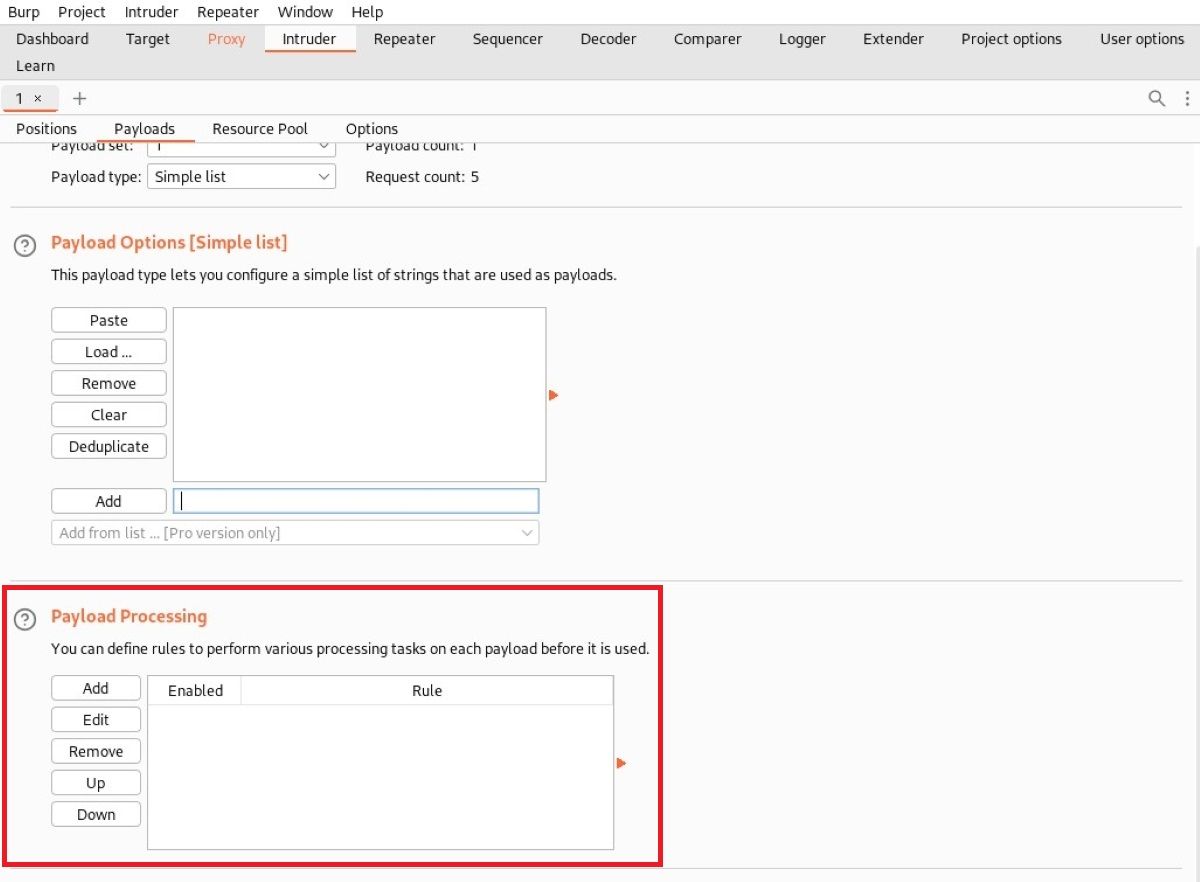
Payload Processing
You can further expand the payload sets configured via Payload Processing with rules and encodings. For example, you could prefix all payloads, have them encode and decode, or skip expressions that pass certain regexes.
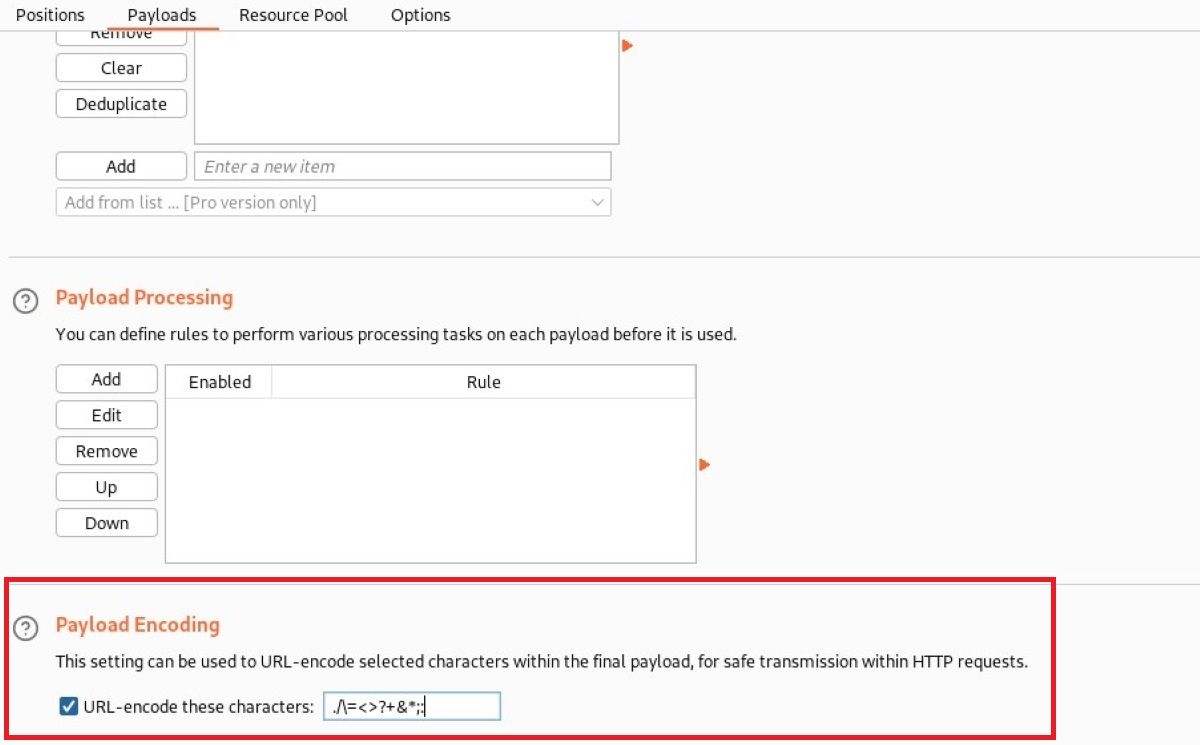
Payload Encoding
With Payload Encoding, you can specify which characters should be URL encoded in the parameters during the transmission of HTTP requests to the destination without any problems. URL encoding is a converted version of information that is likely to be confused with the address. Burp Suite sends the URL to encode equivalents of characters such as ampersands (&), asterisks (*), and semi-colons and colons (respectively, ; and :) in default settings.
What Is the Options Tab in Intruder?
The Options tab has options for request headers, attack results, grep matches, and redirects. You can change these in the Intruder interface before starting a scan.
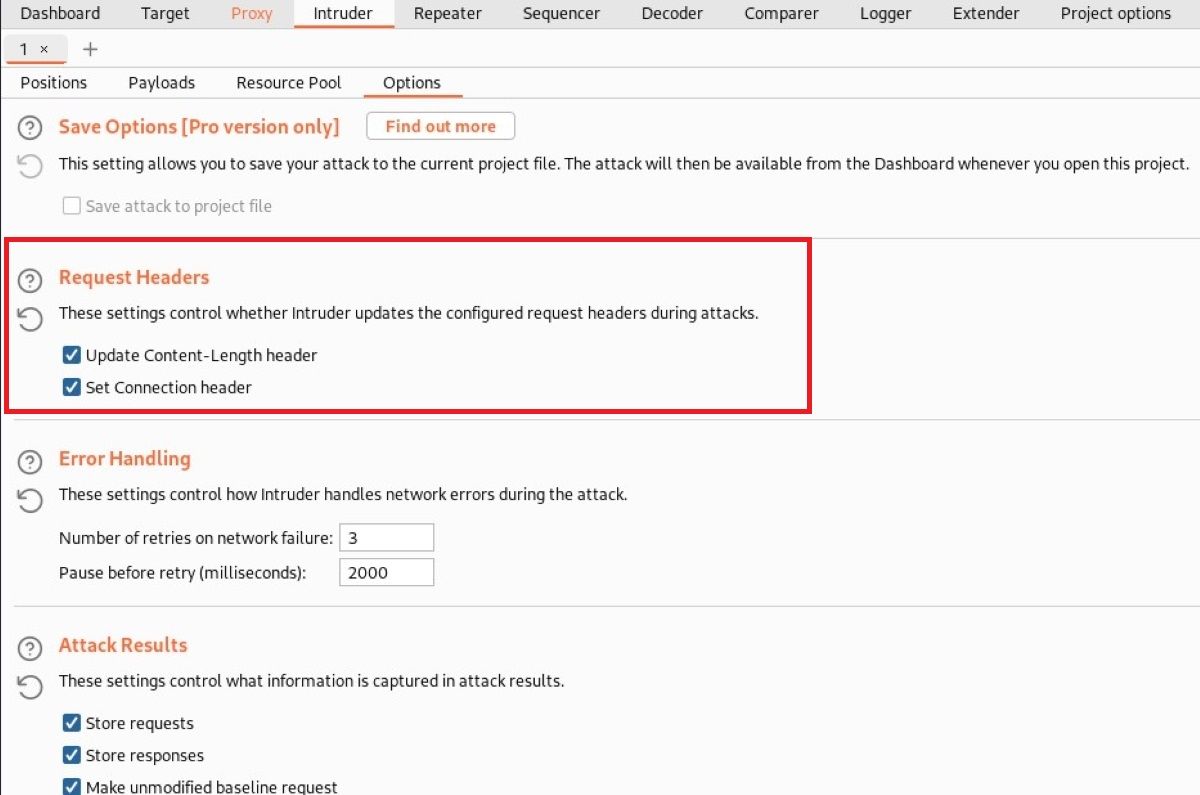
Request Headers
You can set the request headers using the settings in the "Request Headers" field. The important thing to note here is the Content-Length header: the destination address may return an error if the content is not properly updated.
If the Set-Connection information is not used, the connection may remain open, so, after activating the Set-Connection option, the connection is terminated. However, you can perform transactions somewhat faster.
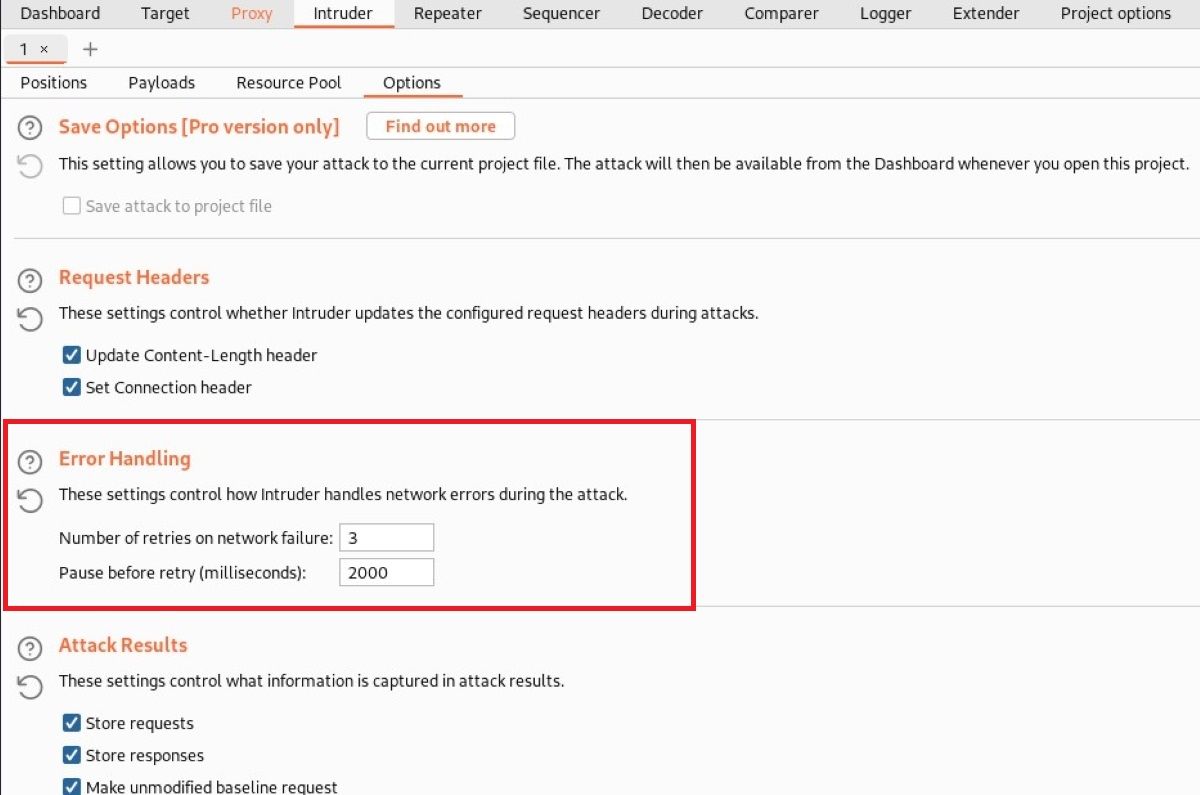
Error Handling
The settings in the "Error Handling" section control the engine used to generate HTTP requests in Intruder scans. Here, you can set parameters such as the speed, severity, and duration of the attack.
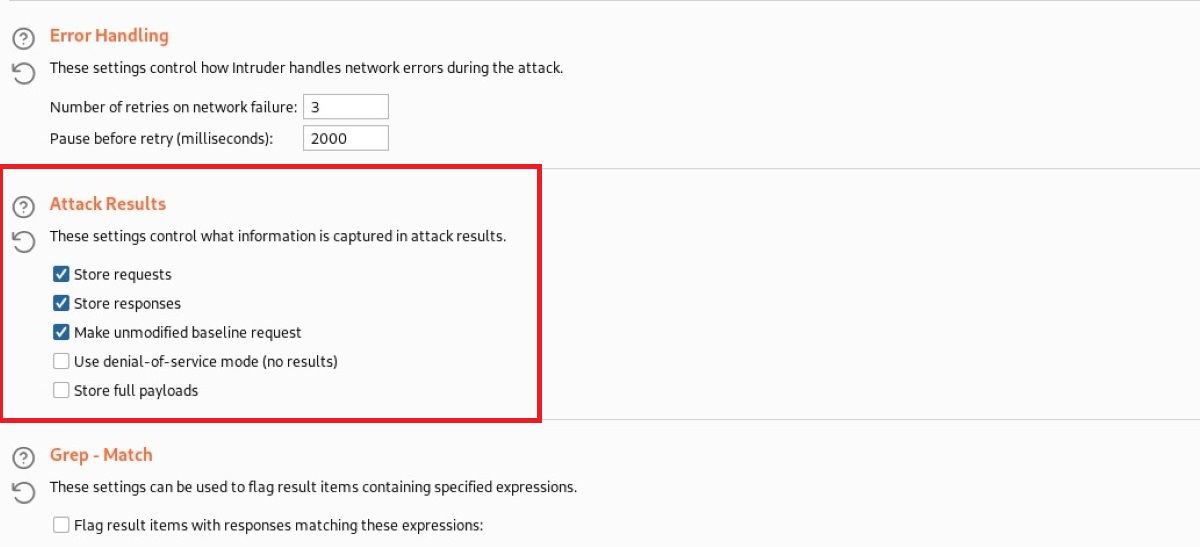
Attack Results
The "Attack Results" section lets you set what information will be in the scan results. These configuration settings have the following options:
- Store requests/responses: These two options are for specifying whether or not it should save the content of requests and responses of scans.
- Make unmodified baseline request: This contains the base values of the targeted parameters as well as the configured scan requests, so you can compare scan responses.
- Use denial-of-service mode: With this option, you can make a normal scan request. However, it may suddenly shut down before there is a response from the server because this function causes fatigue in the target server. That's why you have to use it carefully.
- Store full payloads: This allows Burp Suite to save the exact payload values for each result. If you choose this, Intruder will take up extra space.
Grep - Match, Extract, Payloads
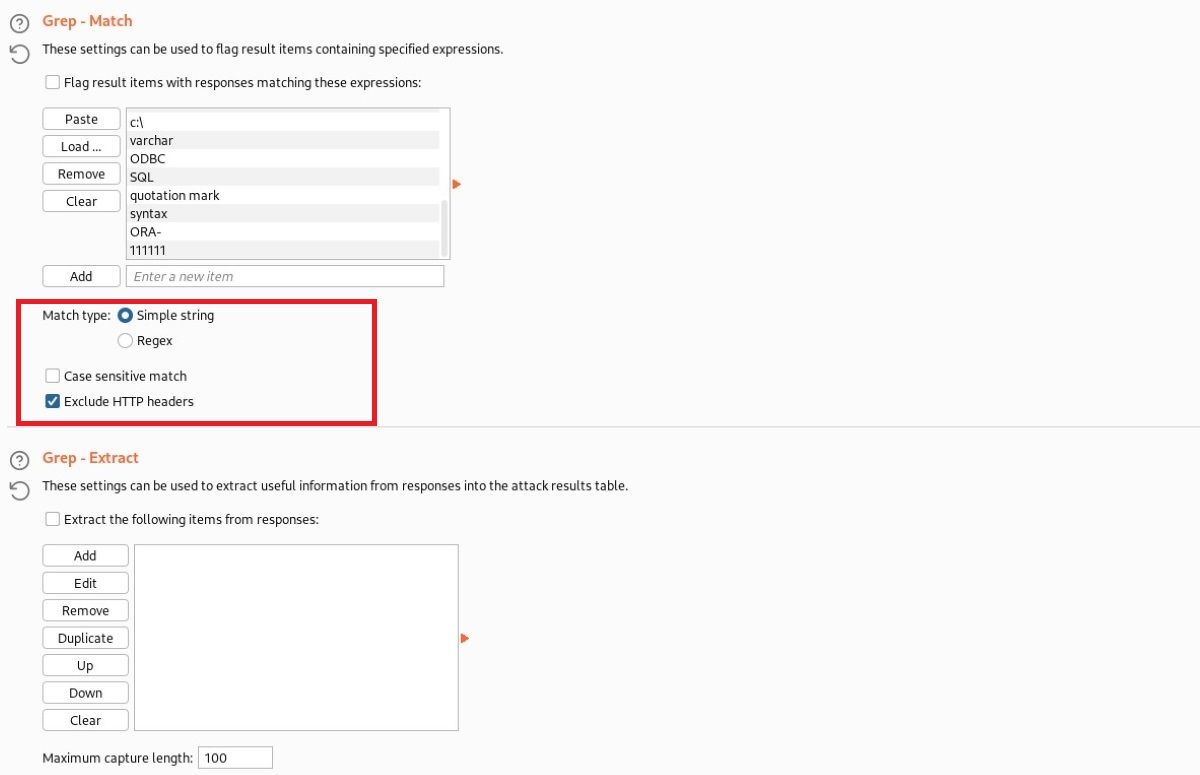
You can use the settings in the "Grep—Match", "Grep—Extract", and "Grep—Payloads" sections to mark results that contain phrases specified in scan responses. Burp Suite will add a confirmation column for each item you configure, indicating whether the item is found in the response. For example, in password attacks, you may see sentences such as "incorrect password" and "successful login". Features in the Grep-Match section include:
- Match type: This indicates whether the defined expressions are a regex (regular expression) or text expression.
- Case-sensitive match: This specifies whether to be case sensitive or not.
- Exclude HTTP header: Specify whether the header lines are exempt from this operation.
Why Is Burp Suite So Important?
Ethical hackers often use Burp Suite for bug bounty operations. Similarly, security researchers working in corporate companies and penetration testers who want to perform security tests on internet applications might rely on Burp Suite too. Of course, there are many other great tools that you can use for penetration testing; mastering other pentesting tools in addition to Burp Suite will make you stand out.