Due to the nature of Linux systems, there are many restrictions and authorization settings for files and directories in terms of security. The only user with all these privileges is the root user.
Therefore, while using the system, if we are root users, the warning before us will not be a restrictive mechanism, and in some cases, the changes we will make may cause major problems with the system. This is why knowing about Linux user authorizations is very important for every Linux user.
Actions Users Can Take Regarding Files and Directories
Each user can act within the framework of the authorizations given to him. There are three actions that users can take regarding files or directories.
- read(r): It is about being able to view the folder list and file contents.
- write(w): It is about making changes to the file or folder.
- execute(x): It is about running the target file or being able to access the folder.
If you are familiar with the chmod command and Linux file permissions, you may have heard of these three permissions before.
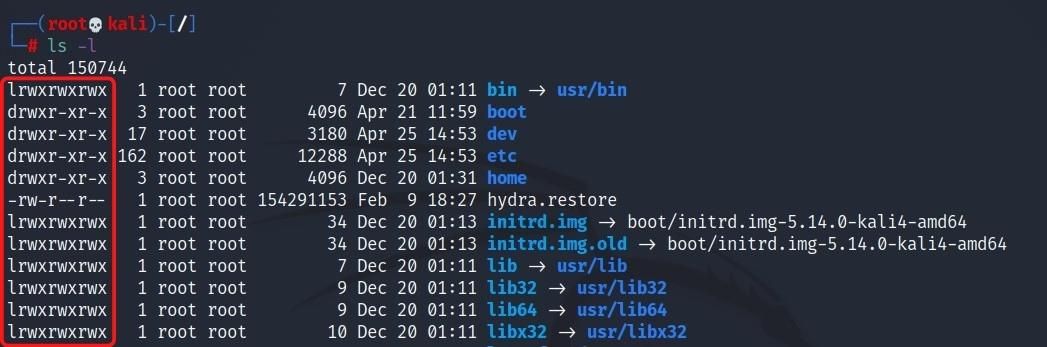
Enter the ls -l command to see what permissions your current file has.
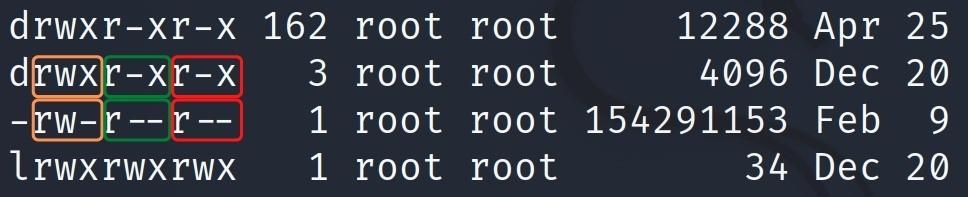
The parts we see as drwxr-xr-x and -rw-r--r-- refer to file permissions. The letter d at the beginning of some expressions indicates that that expression is a directory. If we explain the remaining parts separately, the parts separated by the - sign represent the user group with that permission.
For better understanding, divide them into groups of three, excluding the letter d.
rwxr-xr-x = rwx r-x r-x
rw-r--r-- = rw- r-- r--
The first set of letters specifies the permissions of the file owner, the second of group permissions, and the last set specifies the permissions of other users.
Accordingly, the permissions in the above files are:
- r: read privilege
- w: write privilege
- x: execute privilege
- rwx: the user who owns the file can read, write, execute
- r-x: other users can read, execute, but not write
Changing Permissions With chmod
Only root, who is the most authorized person, can change the access privilege. This change process is easily performed with the chmod command.
The parameters and meanings of the chmod command are given below.
- u: Owner of the file or directory
- g: Users in the same group as the owner of the file or directory
- o: Other users
- a: Open to all
- =: Authorization synchronization
- +: Add authorization
- -: Deletion of authorization
Now that you have seen the meanings of the parameters, you can now consider an example operation. For this, create a sample directory and follow the steps below in order.
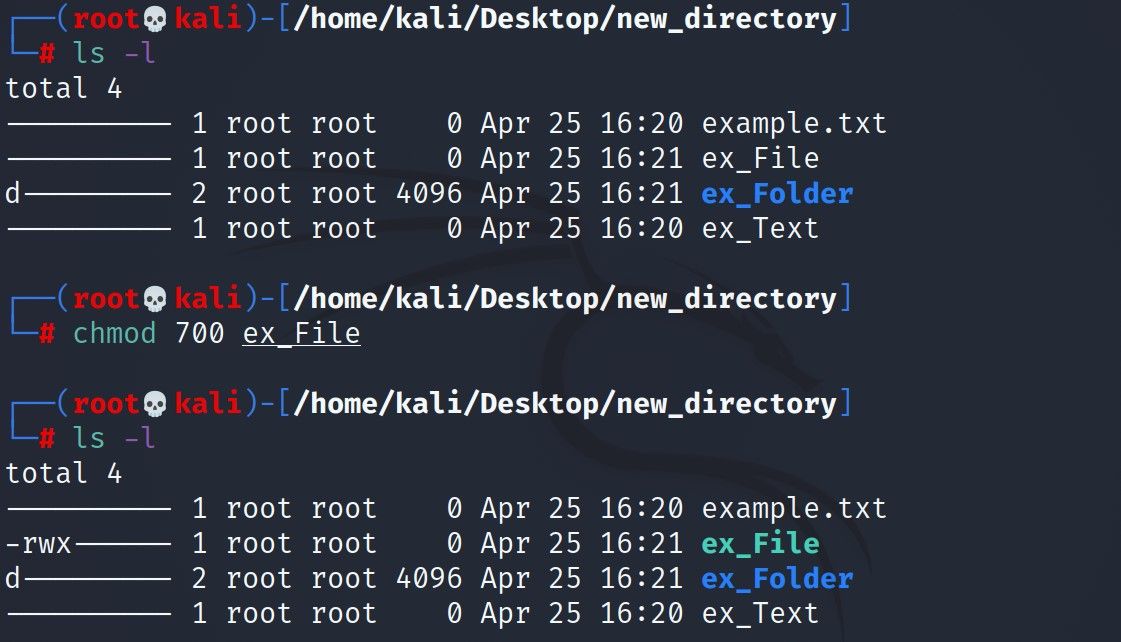
Use the ls -l command to browse the permissions of the files in the folder you created. While doing this, think that the permission structure of your files is as follows.
ls -l
total 4
---------- 1 root root 0 Apr 25 16:20 example.txt
---------- 1 root root 0 Apr 25 16:21 ex_File
d--------- 2 root root 4096 Apr 25 16:21 ex_Folder
---------- 1 root root 0 Apr 25 16:20 ex_Text
After this, access all files in the folder using * character and let write(w) become public using chmod +w * command.
chmod +w *
ls -l
total 4
--w-r-x--- 1 root root 0 Apr 25 16:20 example.txt
--w-r-x--- 1 root root 0 Apr 25 16:21 ex_File
d-w-r-x--- 2 root root 4096 Apr 25 16:21 ex_Folder
--w-r-x--- 1 root root 0 Apr 25 16:20 ex_Text
Now, try to give read-write-execute authorization (rwx) to users in the group(g), write permissions(w) to users(u), and only execute permissions(x) to other users.
chmod g+rwx,u+w,o+x *
ls -l
total 4
--w-rwx--x 1 root root 0 Apr 25 16:20 example.txt
--w-rwx--x 1 root root 0 Apr 25 16:21 ex_File
d-w-rwx--x 2 root root 4096 Apr 25 16:21 ex_Folder
--w-rwx--x 1 root root 0 Apr 25 16:20 ex_Text
And finally, you can use a command like the one below to deauthorize files in your location.
chmod a-rwx *
ls -l
total 4
---------- 1 root root 0 Apr 25 16:20 example.txt
---------- 1 root root 0 Apr 25 16:21 ex_File
d--------- 2 root root 4096 Apr 25 16:21 ex_Folder
---------- 1 root root 0 Apr 25 16:20 ex_Text
Apart from these uses, authorization processes can also be expressed in numerical terms that you have probably come across before and used without realizing it.
Numbers Are Defined for Each Authorization
|
Owner of the File |
Users in the Same Group as the Owner of the File |
Other Users |
|
|
r |
4 |
4 |
4 |
|
w |
2 |
2 |
2 |
|
x |
1 |
1 |
1 |
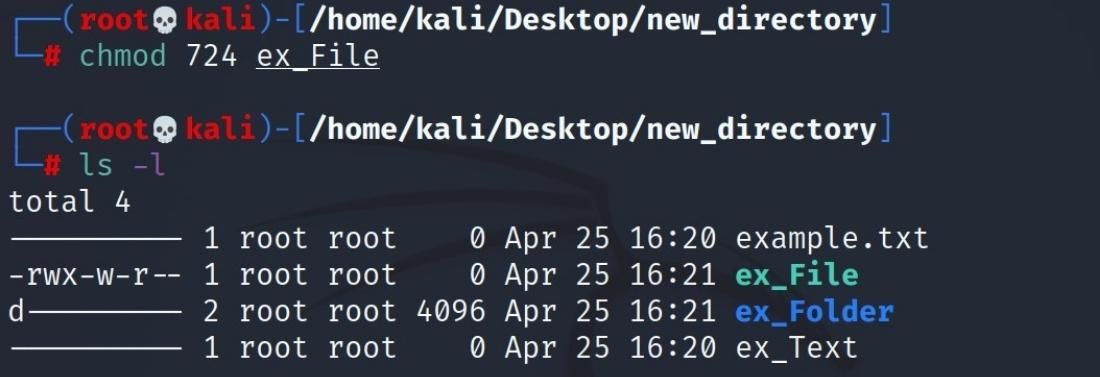
For example, imagine you want to give all permissions to only the owner of the file. For this, you must first collect the number equivalents of the authorization patterns. In other words, since you will give all the permissions, r=4 + w=2 + x=1=total number is 7.
You want to grant this permission only to the owner of the file. To do this, you can slightly modify the chmod rwx- ----- command you would normally use. If you use a command like chmod 700 file, only the owner of the file will have all privileges.
To understand this better, you can think of another example. Imagine that the owner of the file has all permissions, those in the public group have write permission, and other users have read permission.
You can use the equation r(4)+w(2)+x(1)=7 for all privileges to given to the owner of the file.
The write authorization you give for the users in the common group with the file owner will use the number 2, which is the numeric equivalent of the write(w) character. The read authorization you will give for other users will use the number 4, which is the numeric equivalent of the read(r) character.
As it can be understood from the output, the numerical equivalents must have performed the authorization you want.
Make Your Authorization Settings Valid in Subdirectories With -R
In addition, if you want the permissions you give to take effect on that directory and its subfolders, you should use your command with the -R parameter.
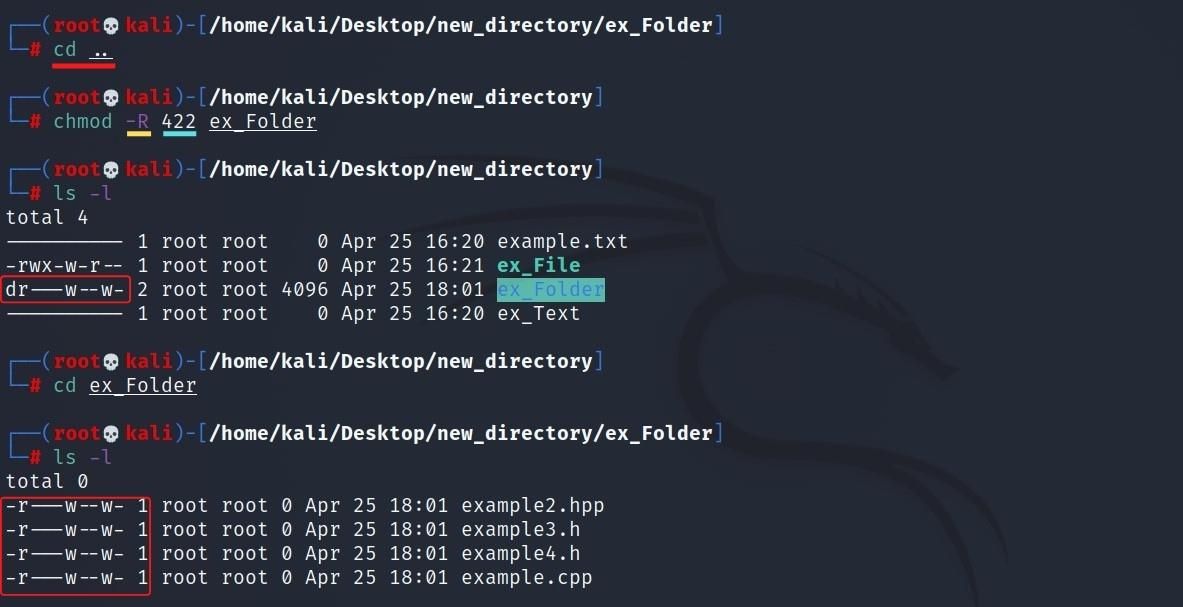
For example, list the access rights of the folder named "ex_Folder" in your location. The result will be an output stating that no entitlements were found.
ls -l
total 4
---------- 1 root root 0 Apr 25 16:20 example.txt
-rwx-w-r-- 1 root root 0 Apr 25 16:21 ex_File
d--------- 2 root root 4096 Apr 25 16:21 ex_Folder
---------- 1 root root 0 Apr 25 16:20 ex_Text
Then go inside the folder named "ex_Folder".
Then back to the parent directory. Use the -R parameter and write a command like chmod -R 422 ex_Folder so that the access permissions to added are valid for all subfiles.
As a result, all files, including all files and directories and subfolders, authorized in a way that corresponds to the 422 statement.
The Best Solution for Accidentally Deleted Files: chattr
Whatever the reason, if there are files that you consider important, it is possible to protect them before they are accidentally deleted. The command that gives this protection opportunity is the chattr command. The chattr command does not only protect against deletion, it is also used to prevent the file from being modified.
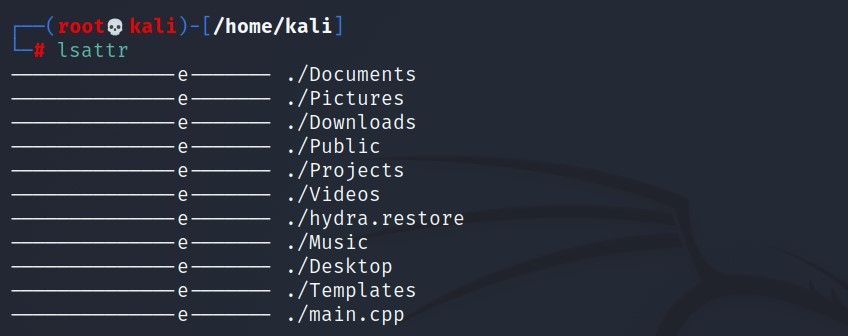
You can use your lsattr command to list such files.
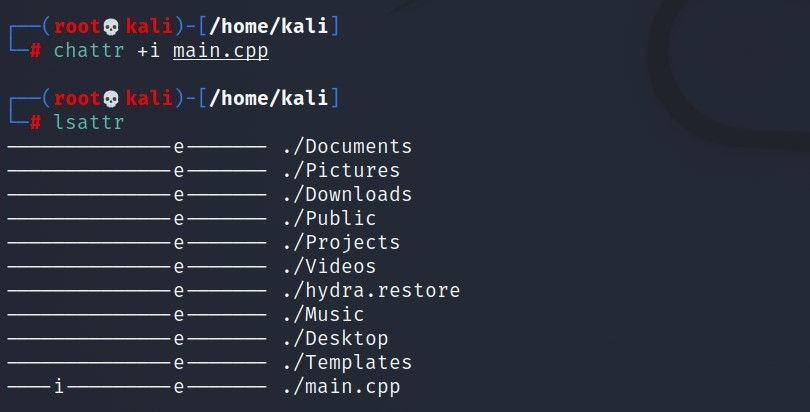
Try to protect the main.cpp file that appears here with the chattr +i main.cpp command.
As seen in the output, there is a -i statement in the permissions section. This statement is a sign that the file can no longer edited. To confirm this, you can try to delete this file with a command like rm -rf main.cpp.
rm -rf main.cpp
rm: cannot remove 'main.cpp': Operation not permitted
If you want to undo this operation and make the file editable, simply use the chattr -i main.cpp command.
Access Privileges Are Important for File System Security
Access authorization forms the backbone of Linux file system security. Thanks to the access permissions that can given to each file separately, a much more comfortable system management can be realized.
Access rights on a per-user basis can sometimes even more meaningful. Therefore, you may want to approach the projects and files on your system knowing the authorization methods described in this article.