Password encryption masks users' passwords so they become hard to guess or decode. It's an essential step in developing secure user-base software. Whether you're building one with Flask or another light Python Framework, you can't ignore that step. That's where bcrypt comes in.
We'll show you how to use bcrypt to hash your password in Python.
How bcrypt Works
Bcrypt is a language-agnostic hashing library that offers unique password encryption. While encrypting your string, it generates extra random characters (salt) by default to beef up the security of your password.
Optionally, you can also specify the number of extra characters you want to add to an incoming string.
The bcrypt library doesn't read raw strings—byte code only. So to start, you'll first encode an incoming password string before passing it to bcrypt for encrypting.
Encoding isn't the same as encrypting. It only ensures that a string becomes machine-readable before an encryption algorithm can mask it.
Encrypting a Password in Python With bcrypt
bcrypt password encryption is easy with Python. We'll focus on how to do this without using a framework. But no worries, it follows the same process in frameworks once you know how to store your users' inputs and read them from the database.
Install and Set Up bcrypt
If you haven't done so already, activate a Python virtual environment in your project root. Then install bcrypt using pip:
pip install bcrypt
Start Encrypting Passwords
Once installed, let's see how to encrypt a string using bcrypt:
import bcrypt
password = "mypasswordstring"
<strong># Encode password into a readable utf-8 byte code:</strong>
password = password.encode('utf-8')
<strong># Hash the ecoded password and generate a salt:</strong>
hashedPassword = bcrypt.hashpw(password, bcrypt.gensalt())
print(hashedPassword)
When you run the Python code above, it prints an encrypted byte string. The output, however, changes each time you execute the script. This is how bcrypt ensures each user has a uniquely encrypted password.
That's for password encryption, by the way.
How to Compare and Confirm Passwords With bcrypt
What if you want to store the hashed password and confirm later that it matches a user's provided password during authentication?
That's easy. You only need to compare the authenticating password with the one stored in the database (or in memory in this case).
And since bcrypt only reads byte strings, you'll also need to encode the authenticating password before comparing it with the one in the database. In essence, you'll cross-check an encoded authentication input with the encoded hashed password already stored in your database.
Using dummy Python inputs, let's see how this works in practice:
import bcrypt
<strong># store your password</strong>:
password = str(input("input password: "))
<strong># Encode the stored password</strong>:
password = password.encode('utf-8')
<strong># Encrypt the stored pasword</strong>:
hashed = bcrypt.hashpw(password, bcrypt.gensalt(10))
<strong># Create an authenticating password input field to check if a user enters the correct password</strong>
check = str(input("check password: "))
<strong># Encode the authenticating password as well</strong>
check = check.encode('utf-8')
<strong># Use conditions to compare the authenticating password with the stored one</strong>:
if bcrypt.checkpw(check, hashed):
print("login success")
else:
print("incorrect password")
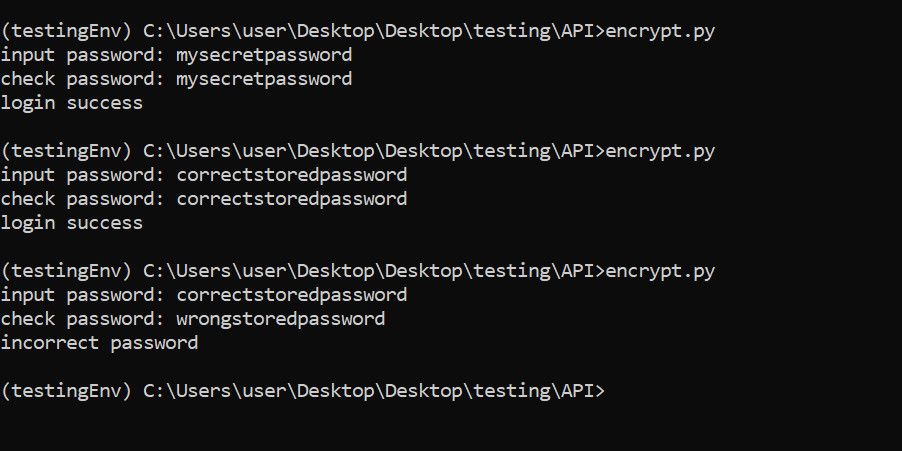
The above code asks you to input a new password when you execute it. Python stores this in memory. You'll then provide the same password (known only to you) in the authenticating field.
Python prints a success message if the compared password matches the previously stored encrypted one. Otherwise, it outputs the failed message wrapped in the else statement:
The whole concept is the same as storing a password in a database during registration and providing it later during authentication.
Scale Up Encryption With bcrypt
While we've only demonstrated how bcrypt works by storing encrypted passwords into plain Python short memory, its ultimate usage is in real-life user-base applications.
Nonetheless, this tutorial shows the fundamental ways to structure your code to achieve this, even in real-life scenarios. For instance, if you're using Flask, you can replace the inputs with separate web forms to serve the registration and authentication fields. And of course, you'll store encrypted passwords in a real-life database and read from it when comparing passwords.