Data Execution Prevention (DEP) is a memory-protection feature in Microsoft Windows that prevents malicious code exploits. It monitors certain memory regions or pages and prevents them from executing malicious codes.
DEP uses hardware and software-based mechanisms to ensure that the system memory locations are used only by Windows and other authorized applications.
When DEP detects an unwanted program executing code in these locations, it notifies the user and terminates the program.
How Does Data Execution Prevention Work?
Unlike a firewall or an antivirus suite, DEP can’t prevent malware from being installed on your computer. It’s only a security tool that monitors programs on the computer and ensures that they utilize the system memory safely.
DEP achieves this by marking one or more memory locations as non-executable. A non-executable location means that code can’t be executed from that memory region, thus reducing the threat of malicious code exploits.
In case an application attempts to execute code from one of the protected memory regions, a memory access violation occurs, and the user is notified. If the user doesn’t handle the violation, the process is terminated.
A downside of using DEP is that it may sometimes flag programs that rely on Microsoft Windows services. You’ll either have to disable DEP or create an exception for the program in your system settings to run such programs. However, this would make the program vulnerable to attacks that could then spread to other programs and files on your computer.
Before disabling DEP for a program, we recommend looking for a DEP-compatible version of the program with the software publisher.
Types of Data Execution Prevention
Data Execution Prevention can be enforced by both hardware and software to help prevent malicious code execution. Here is how the two differ:
1. Hardware-Enforced DEP
Hardware-based DEP marks all memory locations as non-executable unless a location explicitly holds the executable code. It relies on the processor hardware to distinguish memory locations where code shouldn’t be executed.
DEP's hardware-based implementation varies with processor architecture, but all processors that support "execution protection" can enforce hardware-based DEP against malicious exploits. Both AMD and Intel make processor architectures compatible with DEP.
Hardware-Enforced DEP Requirements
- The computer processor should be compatible with DEP.
- Hardware-enforced DEP should be enabled in the BIOS.
- Hardware-enforced DEP should be enabled for programs on the system.
2. Software-Enforced DEP
Software-enforced DEP is a memory protection technology designed to prevent code exploits that leverage Windows' exception handling mechanisms. Any processor capable of running Windows XP Service Pack 2 (SP2) and above can run software-enforced data execution prevention.
Software-enforced DEP alone can only protect limited system binaries. To take full advantage of the execution protection feature, you must use a processor that supports hardware-based DEP.
How to Enable DEP in Windows 10 and 11
You can enable, disable, or make specific exceptions for programs that shouldn't use DEP in Windows 10 and 11. To do so, you can use any of the following two methods.
1. Using System Settings
Using the Settings menu is the most straightforward way to enable DEP on your Windows machine. Here's what you need to do:
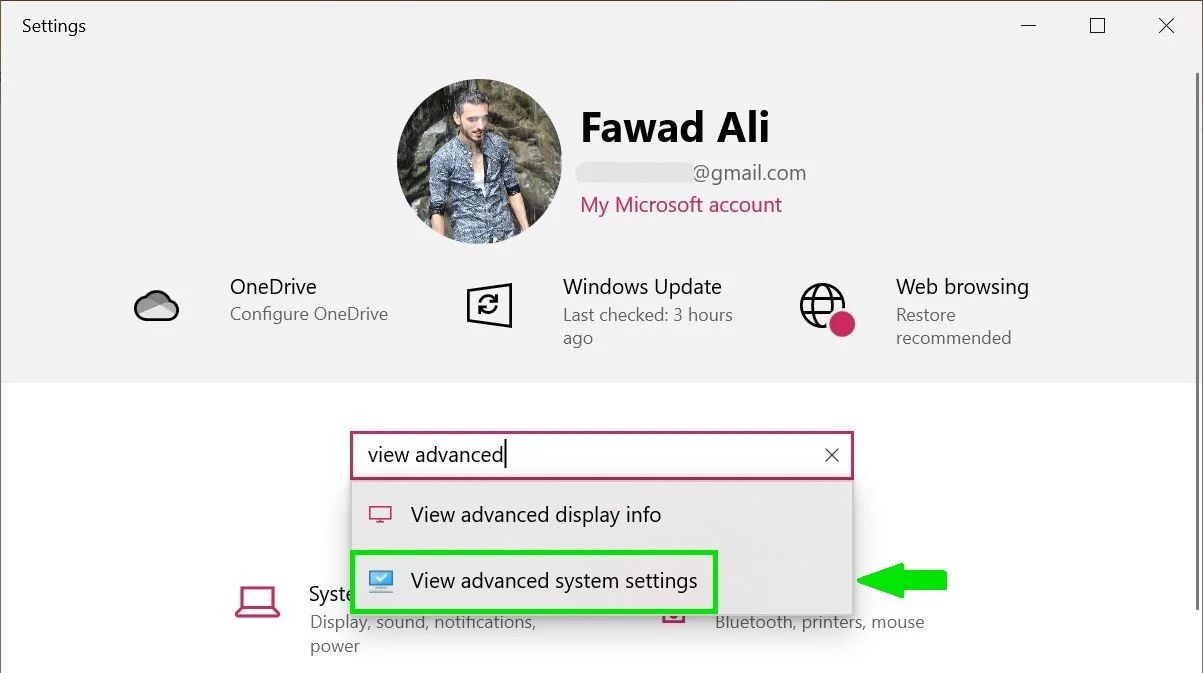
- To get started, click Start and select Settings.
- Type View Advanced System Settings and choose the same option in the drop-down menu.
-
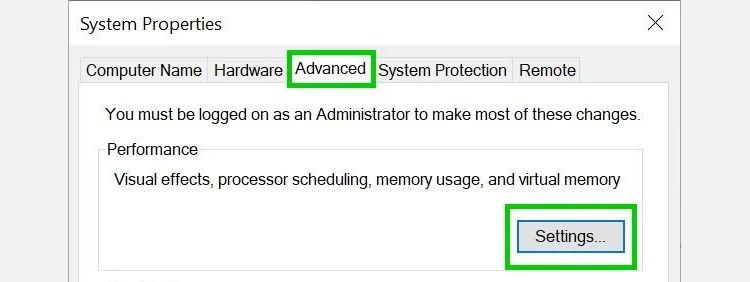
Tap on Advanced in the new window and select Settings under the Performance section.
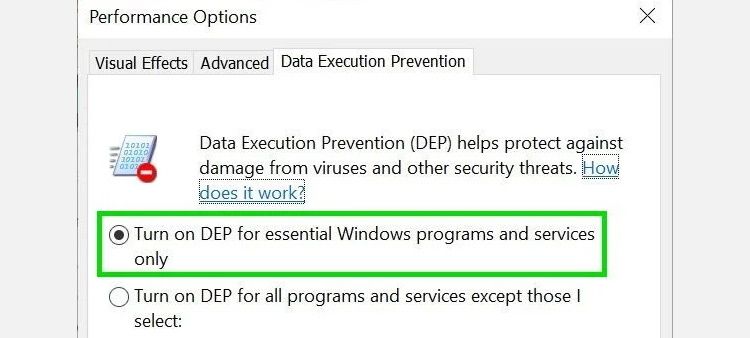
- Click on Data Execution Prevention in the menu bar and check the box against Turn on DEP for all programs and services only option.
- Apply the changes and click OK to complete the process. You may also need to restart the system for the changes to take effect.
You can also exclude certain programs from DEP protection by choosing Turn on DEP for all programs and services except those I select. As soon as you check the box against this option, you'll be able to add programs and services to the list that won't use DEP.
Additionally, the data execution prevention window also tells you whether your processor supports hardware-enforced DEP.
2. Using Command Prompt
Alternatively, you can use Command Prompt, which is actually a one-step process provided you know the command line. Follow the steps below:
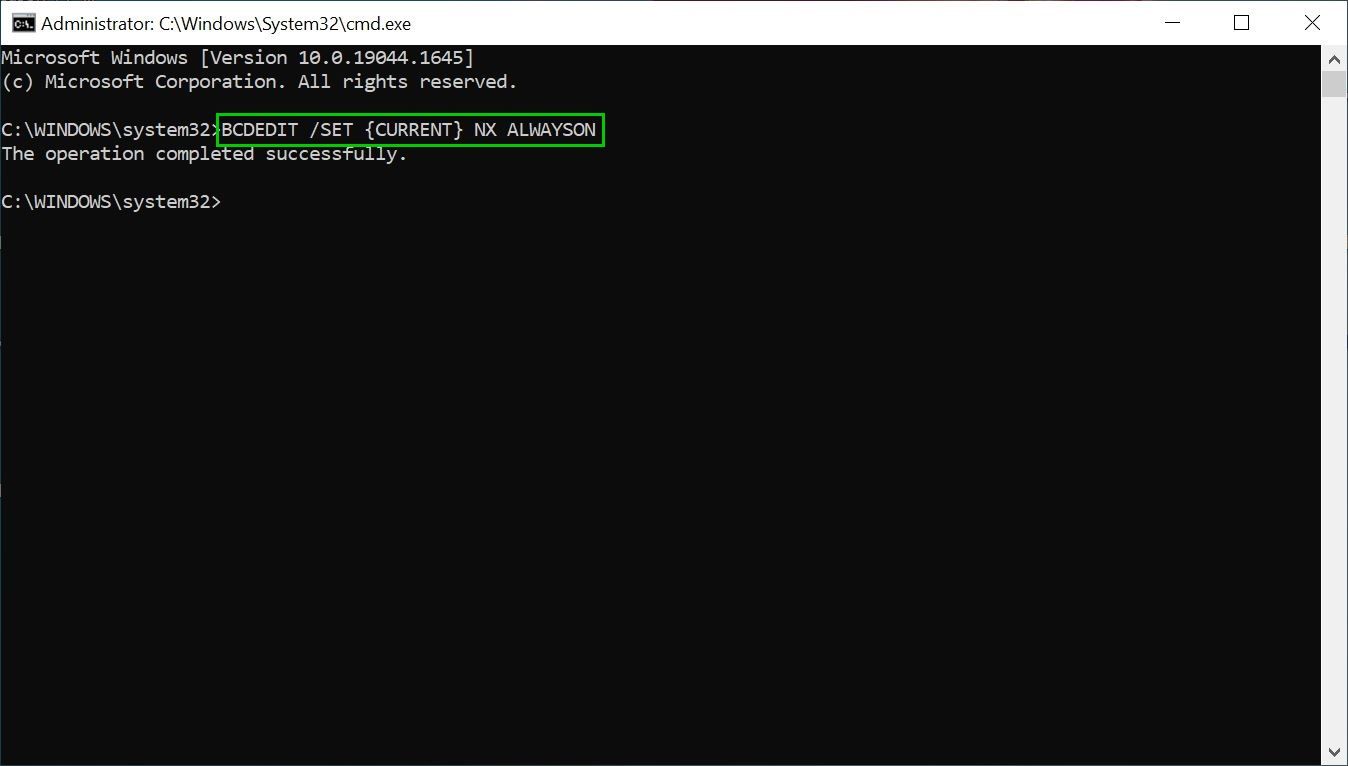
- To enable DEP through the Command Prompt, click Start and type CMD in the search box.
- Right-click on Command Prompt and select Run as administrator.
- In the Command Prompt window, type BCDEDIT /SET {CURRENT} NX ALWAYSON and press Enter.
The changes will take effect as soon as you restart your computer.
Enjoy Protection Against Code Exploits
DEP isn't a comprehensive defense against all exploits. It's a basic system protection feature, and you shouldn't use it as a replacement for firewall or antivirus software.
Windows enables DEP by default and shall remain active unless you have a valid reason to disable it for specific programs installed on your system.