SSL/TLS certificates are essential for securing your web application or server. While several reliable certificate authorities provide SSL/TLS certificates for a cost, it is also possible to generate a self-signed certificate using OpenSSL. Even though self-signed certificates lack the endorsement of a trusted authority, they can still encrypt your web traffic. So how can you use OpenSSL to generate a self-signed certificate for your website or server?
How to Install OpenSSL
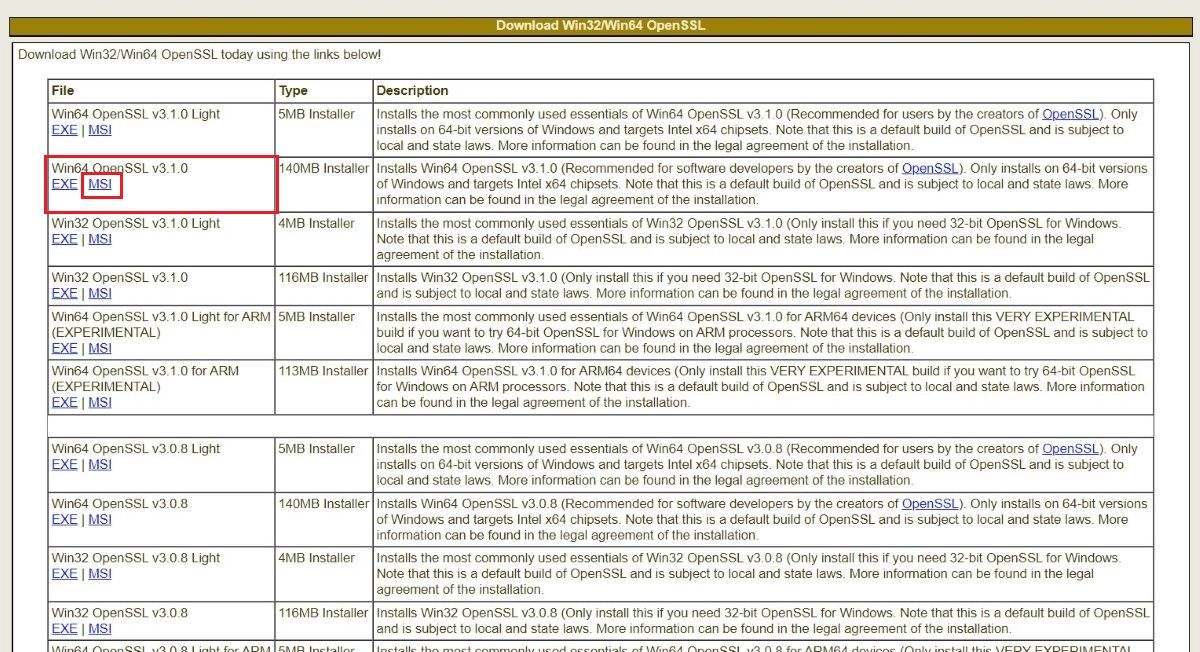
OpenSSL is open-source software. But if you don't have a programming background and are worried about build processes, it has a bit of a technical setup. To avoid this, you can download the latest version of OpenSSL's code, fully compiled and ready to install, from slproweb's site.
Here, select the MSI extension of the latest OpenSSL version suitable for your system.
As an example, consider OpenSSL at D:\OpenSSL-Win64. You can change this. If the installation is complete, open PowerShell as admin and navigate to the subfolder named bin in the folder where you installed OpenSSL. To do this, use the following command:
cd 'D:\OpenSSL-Win64\bin'
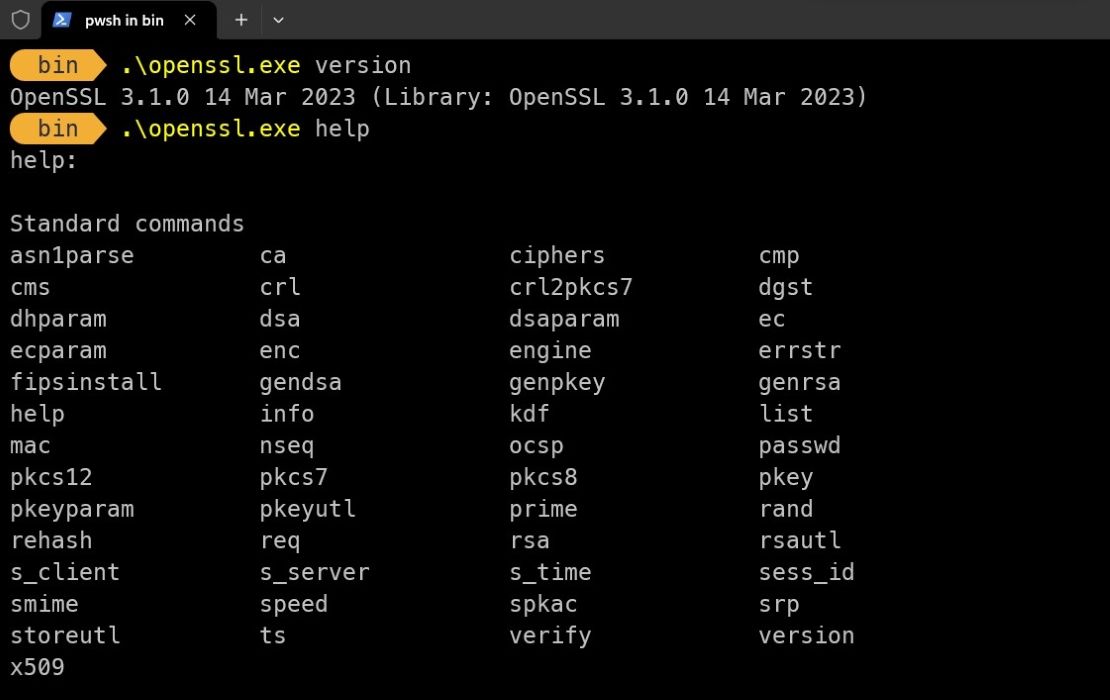
You now have access to openssl.exe and can run it however you want.
Generate Your Private Key With OpenSSL
You will need a private key to create a self-signed certificate. In the same bin folder, you can create this private key by entering the following command in PowerShell once you have opened as admin.
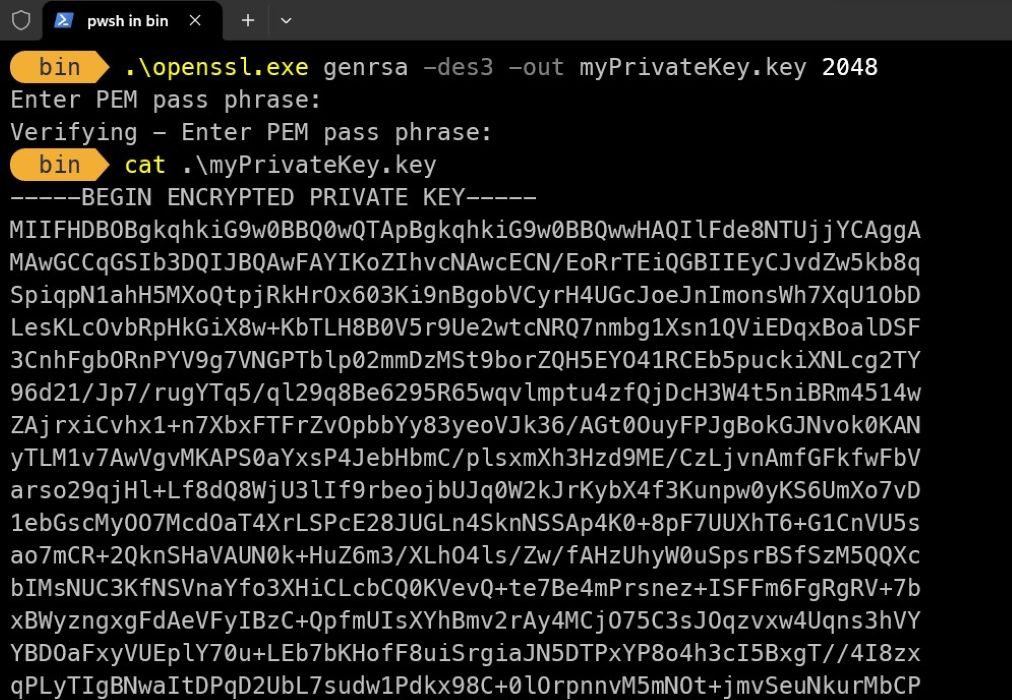
openssl.exe genrsa -des3 -out myPrivateKey.key 2048
This command will generate a 2048-bit long, 3DES-encrypted RSA private key via OpenSSL. OpenSSL will ask you to enter a password. You should use a strong and memorable password. After entering the same password twice, you will have successfully generated your RSA private key.
You can find your private RSA key with the name myPrivateKey.key.
How to Create a CSR File With OpenSSL
The private key you create will not be enough on its own. Additionally, you need a CSR file to make a self-signed certificate. To create this CSR file, you need to enter a new command in PowerShell:
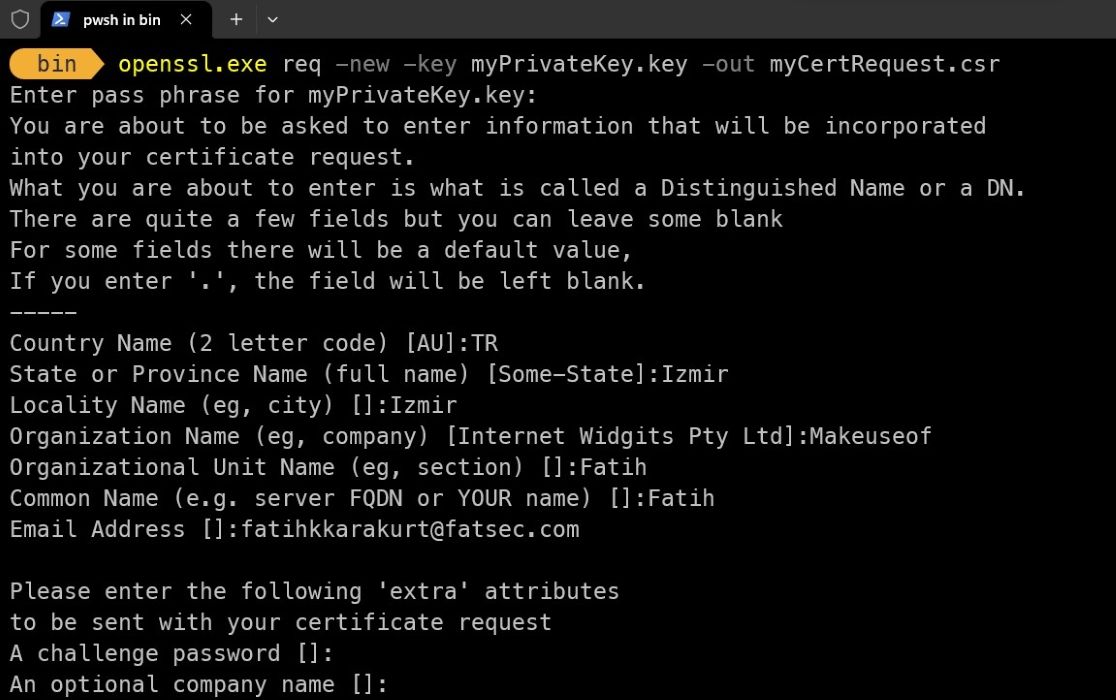
openssl.exe req -new -key myPrivateKey.key -out myCertRequest.csr
OpenSSL will also ask for the password you entered to generate the private key here. It will further request your legal and personal information. Be careful you enter this information correctly.
In addition, it is possible to do all the operations so far with a single command line. If you use the command below, you can generate both your private RSA key and the CSR file at once:
openssl.exe req -new -newkey rsa:2048 -nodes -keyout myPrivateKey2.key -out myCertRequest2.csr
You will now be able to see the file named myCertRequest.csr in the relevant directory. This CSR file you create contains some information about:
- The institution requesting the certificate.
- Common Name (i.e. domain name).
- Public Key (for encryption purposes).
The CSR files you create need to be reviewed and approved by certain authorities. For this, you need to send the CSR file directly to the certificate authority or other intermediary institutions.
These authorities and brokerage houses examine whether the information you provide is correct, depending on the nature of the certificate you want. You may also need to send some documents offline (fax, mail, etc.) to prove whether the information is right.
Preparation of Certificate by a Certification Authority
When you send the CSR file you created to a valid certificate authority, the certificate authority signs the file and sends the certificate to the requesting institution or person. In doing so, the certification authority (also known as a CA) also creates a PEM file from the CSR and RSA files. The PEM file is the last file required for a self-signed certificate. These stages ensure that SSL certificates remain organized, reliable, and secure.
You can also create PEM file yourself with OpenSSL. However, this can pose a potential risk to the security of your certificate because the authenticity or validity of the latter is not clear. Also, the fact that your certificate is unverifiable may cause it to not work in some applications and environments. So for this example of a self-signed certificate, we can use a fake PEM file, but, of course, this is not possible in real-world use.
For now, imagine a PEM file named myPemKey.pem comes from an official certificate authority. You can use the following command to create a PEM file for yourself:
openssl x509 -req -sha256 -days 365 -in myCertRequest.csr -signkey myPrivateKey.key -out myPemKey.pem
If you had such a file, the command you should use for your self-signed certificate would be:
openssl.exe x509 -req -days 365 -in myCertRequest.csr -signkey myPemKey.pem -out mySelfSignedCert.cer
This command means that the CSR file is signed with a private key named myPemKey.pem, valid for 365 days. As a result, you create a certificate file named mySelfSignedCert.cer.
Self-Signed Certificate Information
You can use the following command to check the information on the self-signed certificate you have created:
openssl.exe x509 -noout -text -in mySelfSignedCert.cer
This will show you all the information contained in the certificate. It is possible to see a lot of information such as the company or personal information, and algorithms used in the certificate.
What if Self Signed Certificates Aren't Signed by the Certification Authority?
It is essential to audit the self-signed certificates you create and confirm that these are secure. A third-party certificate provider (i.e. a CA) usually does this. If you do not have a certificate signed and approved by a third-party certificate authority, and you use this unapproved certificate, you will run into some security issues.
Hackers can use your self-signed certificate to create a fake copy of a website, for example. This allows an attacker to steal users' information. They can also get hold of your users' usernames, passwords, or other sensitive information.
To ensure the security of users, websites and other services typically need to use certificates that are actually certified by a CA. This provides an assurance that the user's data is encrypted and is connecting to the correct server.
Creating Self-Signed Certificates on Windows
As you can see, creating a self-signed certificate on Windows with OpenSSL is quite simple. But keep in mind that you will also need approval from certification authorities.
Nonetheless, making such a certificate shows you take users' security seriously, meaning they'll trust you, your site, and your overall brand more.