Conventional on-premises servers have the huge downside that they need to be managed in-house by an individual. With the adoption of the cloud and agile software development methodologies, these are becoming obsolete now that cloud data storage operational loads can be reduced because there is no server in-house. The downside is that along with the use of cloud services, information leakage accidents can occur easier than with on-premises servers.
Strong security measures must be implemented for each cloud workload to be protected. Yet, due to the differences in storage and workload architecture, different measures from conventional server security are required. That’s where Cloud Workload Protection Program (CWPP) technology comes into play.
What Is a Cloud Workload?
Cloud workloads can be anything from general services, applications, or an amount of work that consumes computing memory, known too as cloud-based resources. Typical workloads that use cloud-based resources are microservices, Hadoop nodes, databases, cloud Infrastructure as a Service (IaaS), containers, and Virtual Machines (VMs).
That’s where CWPP helps define, implement, and monitor consistent, centralized security for workloads regardless of where they reside, their form, or their lifecycle. The cloud is a huge target for cybercriminals and one of the biggest challenges is working with data that travels between environments. CWPPs were created to deal with hybrid data centers—the storage of work and personnel data on physical premises, container-based application architectures, multiple public IaaS, and VMs. In simple words, CWPP is a workload-centric security protection solution.
How to Protect Workloads Using CWPPs
There are many cloud platforms on offer, meaning CWPPs must be dynamic to be able to protect all cloud architecture systems, primarily to stop leaks and infiltrations. So how do they do this?
First, creating network segmentation through firewalls helps with traffic monitoring, visibility, and log management. CWPP also provides workload vulnerability management to monitor behavior and conduct anti-malware scanning; this is essentially Endpoint Detection and Response (EDR) and Host-based Intrusion Detection Systems (HIDS).
In a way, a CWPP could be described as antivirus and optimization software for cloud workloads.
How Are CWPPs Beneficial?
Most cloud vendors will integrate a security protocol for their product, so a CWPP would become an additional layer of protection against targeted attacks. Cloud visibility also allows you to reduce boost threat detection and response by allowing you to respond to a threat faster.
Another benefit is cloud and human performance optimization: cloud optimization because, with CWPP, you are able to collect analytics from applications, which in turn helps optimization; and human performance optimization because all cloud workloads will be integrated into one program. This signifies less of a need for personnel to be tasked with conducting updates, scans, and reports on each cloud workload.
All these benefits (fewer personnel required to manage security, cloud optimization, and a single centralized protection program) reduce operational and hardware costs while also lowering maintenance time.
Which Companies Offer These Solutions?
Dozens of well-known security software development companies offered CWPP solutions. The most well known are:
- McAfee Server Security Suite.
- Symantec Cloud Workload Protection.
- Microsoft Defender for Cloud.
- Sysdig Secure DevOps Platform.
- Trend Micro Deep Security.
What Are Other Cloud Security Tools?
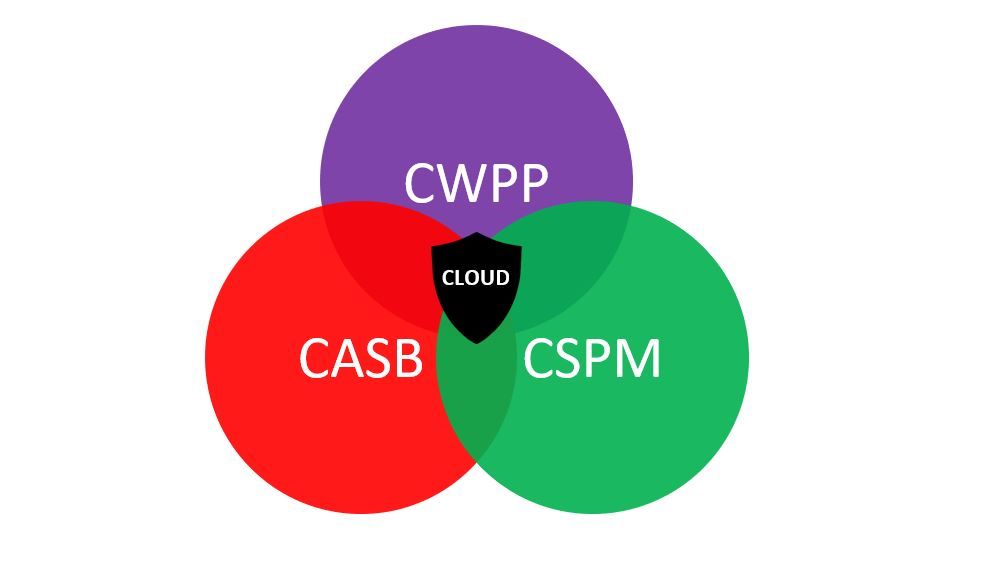
Some of these companies mentioned above will offer CWPP combined with other cloud security and optimization software, just like Cloud Security Posture Management (CSPM) and Cloud Access Security Broker (CASB). Many of these three software's features overlap yet they each specialize in a single aspect of cloud security.
CSPMs technology is used to comply with cloud security configurations by implementing security and compliance processes, while CASB is software that makes sure that traffic complies with an organization's security policies before enabling access to a network. These are sometimes used together with CWPPs to better optimize and secure cloud workloads and data.
Why Do You Need CWPP Technology?
While protecting your cloud, CWPP will enable you to perform security functions across multiple environments, reduce cloud protection complexity, and boost portability regardless of what or where a cloud workload is.
No other software offers as much protection and centralized controls as a CWPP, and for that reason, a CWPP is absolutely necessary to remain secure against today's cyber threats and data breaches.