Wi-Fi penetration tools aid cybersecurity analysis by delving deeper into the details of the security framework. Before hackers use these tools to infiltrate your system, it is a wise decision to examine your network for any such vulnerabilities.
For this purpose, many organizations are beginning to use Wi-Fi penetration testing tools to uncover the vulnerabilities on their wireless networks. Read on to know some of the potent and popular Wi-Fi penetration tools.
Wireless Password Crackers
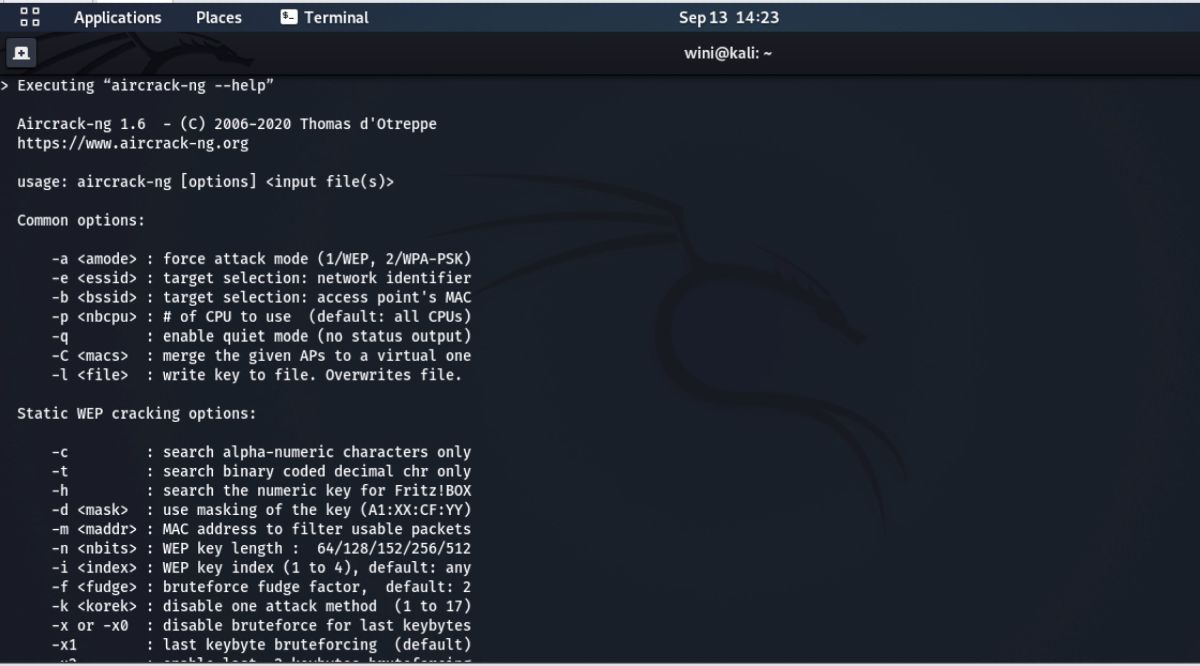
1. Aircrack-ng
Aircrack-ng is probably the most preferred choice for hackers to penetrate Wi-Fi networks and access passwords for ethical or unethical use. It is popular for people looking to crack both WEP and WPA passwords.
Aircrack's working principle is based on capturing the network packets by using a series of foolproof algorithms. The tool collects enough packets to recover the password through an optimized FMS attack. It supports most wireless adapters and promises to deliver a high success rate.
2. Reaver
Reaver is a popular open-source wireless network penetration tool topping every pen tester's toolkit list. This tool applies brute force attacks for stealing passwords on WPA and WPA2-secured wireless networks.
The Reaver source code is freely available on Google, but you need to read its usage guide before getting practical with the tool. This Wi-Fi penetration tool is still in use, even though it hasn't been updated for quite some time now.
3. Hashcat
Hashcat is the world's fastest password cracker. It's based on an in-kernel rule engine that gives you the flexibility to use it on some of the most popular operating systems.
Operating systems like Linux, Windows, and macOS support Hashcat's usage extensively. Hashcat's password candidate brain functionality continues to be one of the primary attention-grabbing USPs of this tool.
It comes with a built-in benchmark system and an internal thermal watchdog. Besides that, it supports hex-salt, hex-charset, automatic performance tuning, interactive pause/resume, distributed cracking, multi-device, and many more features.
4. Wifiphisher
Wifiphisher is yet another excellent tool for cracking passwords and creating fake access points. Penetration testers can use such fake access points for red team engagement and Wi-Fi security testing.
The tool enables you to achieve a man-in-the-middle position against Wi-Fi access clients quickly. The tool is helpful in customized web phishing attacks, infecting the stations with malware and performing automated phishing attacks based on your preference and requirement.
It is freely available and comes pre-loaded within Kali, a specialized penetration testing Linux distro. Hackers use this tool for stealing Wi-Fi passwords.
5. CoWPAtty
Joshua Wright is the owner/founder of cowPatty. It works on the principle of automated offline dictionary attacks. The tool includes an Auditor CD that makes it easy to use the tool for hacking WPA-PSK networks.
The tool is easy to use but works very slowly, which is a significant drawback. It runs on a word list containing the passwords used in attacks. As a hacker, you cannot hack the network, until and unless the password is available within the password word list.
While this process might make the whole concept secure, it is a slow tool, which tends to drop from every pentester's interest list soon enough.
Network Scanners and Wi-Fi Hackers
6. AirSnort
AirSnort ranks high, especially when it boils down to offering a suite of freely available Wi-Fi penetration tools for WEP networks. One major drawback is that it only works with WEP networks, which continues to be a bummer, considering its list of useful features.
AirSnort gathers, examines, and composes encryption keys after collecting enough network packets. It is an easy-to-use tool for both Linux and Windows operating systems. Unfortunately, just like Reaver, there has been no update on this tool for a while now.
7. Infernal-Twin
The primary purpose of developing the Infernal-Twin pentesting tool is to automate the evil twin attack by creating access points. Those access points sniff network communication and get the desired results for the users.
The attackers set up bogus Wi-Fi access points that promise to provide internet services; however, the reality is different, as it does the work of sniffing the user's traffic.
The fake access points pretend like a genuine page for network access, whereas they simply attempt to steal your network's Wi-Fi credentials and other vital data.
It comes with all the essential features required for hacking a wireless network. Whether a person is using WEP, WPA, or WPA2, rest assured Infernal-Twin will give you success.
Some features include:
- SSL Strip
- Note-taking functionality
- Network mapping
- MiTM
- WPA/WPA2/WEP hacking
- Wireless social engineering
- GUI wireless security assessment
Infernal-Twin tool is regularly updated; the author announced that the next release would give more power to gather victim's credentials and other data through TShark log file parsing. These features make it an excellent tool for getting the most out of your Wi-Fi pentesting assignments.
8. Wireshark
Wireshark is a widely used and highly trusted network protocol analyzer freely available as an open-source tool. As a pentester, you can get microscopic-level details about your network with this tool.
Wireshark works on collecting packets and further analyzes them to give the detailed security status. It offers multi-platform support on some of the most popular operating systems such as macOS, Linux, Windows, amongst others.
Its rich VoIP analysis and deep inspection of over a hundred protocols make it worthwhile for various governmental, private, and nonprofit organizations. The tools can't provide plaintext passphrases in some cases, but it is still beneficial for sniffing and capturing live data.
Furthermore, ethical or unethical hackers may use it for Bluetooth, Ethernet, USB, and other networks, besides Wi-Fi. People having little to negligible knowledge about network protocols might feel incapable of using this tool.
Finding the Best Penetration Testing Tool for Your Wi-Fi
Use each of these tools for cracking Wi-Fi passwords or to monitor your network traffic. While each tool has its own set of features, you need to decide which feature is best suited for your immediate needs.
You can also choose to switch to a penetration testing Linux distribution if you don't want to spend time installing every tool on your system.


-(1).jpg)
.jpg)
.jpg)
.jpg)