Cast your mind back to May 2017. FBI Director James Comey was fired, terrorists struck an Arianna Grande concert in Manchester, and the world fell victim to the WannaCry ransomware attack.
WannaCry infected more than 230,000 computers across 150 countries. It brought the United Kingdom's health service to a standstill, crashed cell phone networks in Spain, and caused long delays on Germany's railways. In short, it was one of the worst cyber attacks the world had ever seen.
Now, three months later, you might think the flaws that allowed the attack to spread have been fixed. You'd be wrong -- and you might still be vulnerable.
What Caused WannaCry?
Without getting too technical, WannaCry spread using EternalBlue. It's an NSA-developed exploit of the Windows Server Message Block (SMB) protocol.
Microsoft responded by pushing out patches to millions of older computers, including to "officially unsupported" operating systems such as Windows XP. Theoretically, the updates closed the EternalBlue SMB flaw.
Sadly, it seems the patches didn't work. At the annual DEF CON conference in late-July, security researchers found yet another flaw. They claimed the flaw has existed for 20 years.
Called SMBLoris, it's a remote denial-of-service attack. It can crash a computer or a server using no more than 20 lines of code.
And what was Microsoft's response? The company said it would not patch the issue. It argued SMB should be blocked automatically by the firewall.
Technically, Microsoft is right. But you shouldn't leave it to chance.
How to Protect Yourself
SMBLoris affects all forms of SMB. It means removing SMBv1 from your system is no longer sufficient. Instead, you need to block all incoming connections on ports 445 and 139.
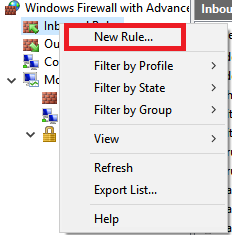
You can block ports on your router, but there's an easier way: use the Windows Firewall tool. Go to Control Panel > Windows Firewall > Advanced Settings, right-click on Inbound Rules, and select New Rule.
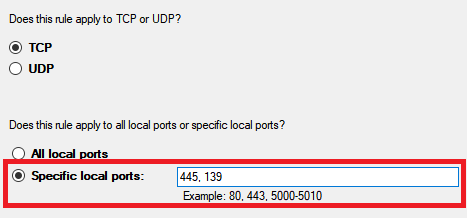
On the next screen select Port and then Next. Now you need to choose Specific Local Ports. Enter 445, 139 in the box. Again, click Next.
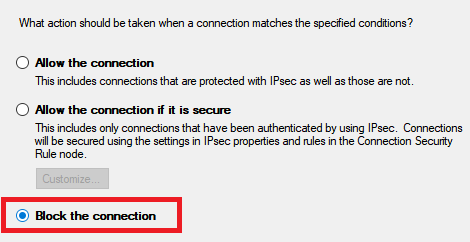
Finally, choose Block the Connection, give your new rule a name, and hit Finish.
Were you a victim of WannaCry? Will you disable SMBv1? Let us know in the comments below.